Managing user identities and ensuring secure access across multiple devices is crucial for organizations. With macOS Ventura, Apple introduced Platform single sign-on (Platform SSO), a framework designed to streamline user authentication by linking macOS accounts with Identity providers (IdPs). Okta, a leading provider of Identity management, has integrated with Platform SSO to extend these capabilities, allowing macOS users to authenticate directly with their Okta credentials.
This blog post will explore how macOS login authentication can be delegated to Okta using Platform SSO and the new policies introduced in macOS 15.
What is Platform SSO, and how does Okta leverage it?
Platform SSO enables developers to create an SSO extension that interacts directly with the macOS login window. This extension allows users to link their local macOS account with their Identity provider through a simple, Mac-native workflow.
Since its release in 2022, Apple has continued improving the Platform SSO framework with each new macOS release. For example, in macOS 14, the framework was extended to:
- Support Identity provider authentication at the login screen
- Support users to create on-demand local accounts by simply typing in their IdP credentials
- Support group membership backed by an IdP
Leveraging the Platform SSO framework, Okta initially released Desktop Password Sync. This feature enables users to unlock their Mac by entering their Okta credentials, and the Platform SSO framework syncs the Okta password locally.
Furthermore, using the new functionality released in macOS 14, Okta released additional functionality, including Password Sync at login and Just-in-Time Local Account Creation, extending the Platform SSO authentication to the login screen and supporting on-demand local account creation on shared devices.
To learn more about these features, visit Okta's product documentation for Okta Device Access.
Challenges and the new offerings on macOS Sequoia
When Apple first introduced the Platform SSO framework, it lacked some essential functionality. One of the main issues was that the framework didn't fully enforce IdP authentication. If the password entered was verified against the local macOS password, users would gain access, and then the framework would verify the password against the IdP in the background.
Users would receive an optional prompt to sync their password if the IdP rejects the password. This behavior opened up the risk of allowing users to access a machine using out-of-sync and non-IdP passwords that were only verified locally.
Another limitation was the lack of support for FileVault authentication. Users had to unlock FileVault with their local password before being able to authenticate with and sync their Identity provider password.
These issues meant that local authentication remained a key factor, with the IdP taking a secondary role. New Unlock, Login, and FileVault policies introduced for Platform SSO in macOS Sequoia addressed these issues..
The new policies expanded the Platform SSO authentication to FileVault and offered the ability to enforce IdP authentication by setting the “requireAuthentication” flag, while providing an offline grace period to handle connectivity issues. This update supports authentication being delegated to the IdP.
Delegating authentication to Okta
To fully delegate macOS login authentication to Okta, administrators can set the “requireAuthentication” or “attemptAuthentication” flag on the Unlock, Login, and FileVault (if applicable) while using Okta Desktop Password Sync. This enables Okta to validate password-based login before granting access.
Only Platform SSO registered users can log in to the device, and they need to use their Okta credentials to do so. In addition, Okta reviews if the user is active and confirms that the login originates from a cryptographically verified device, adding extra protection to the authentication process.
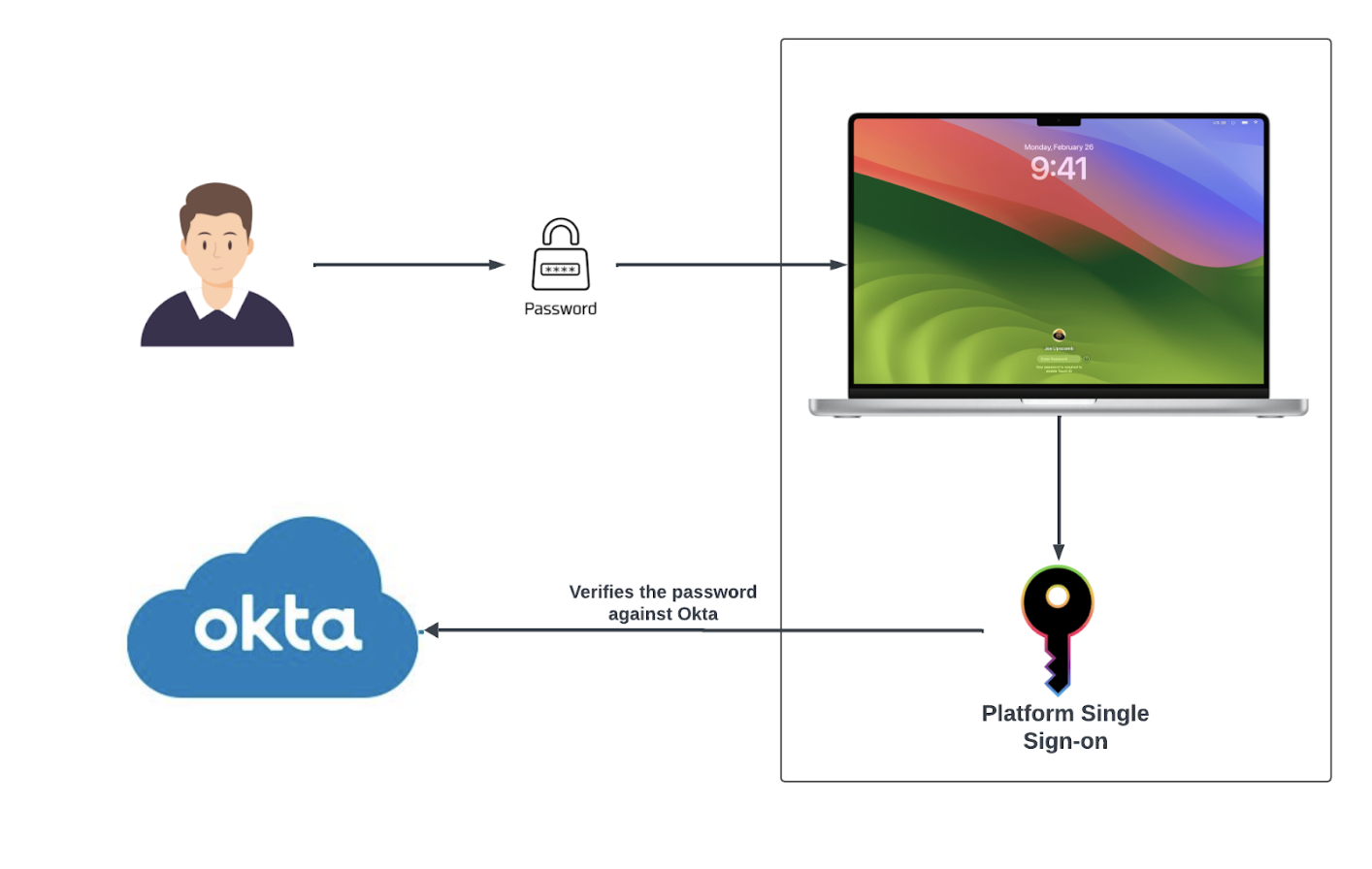
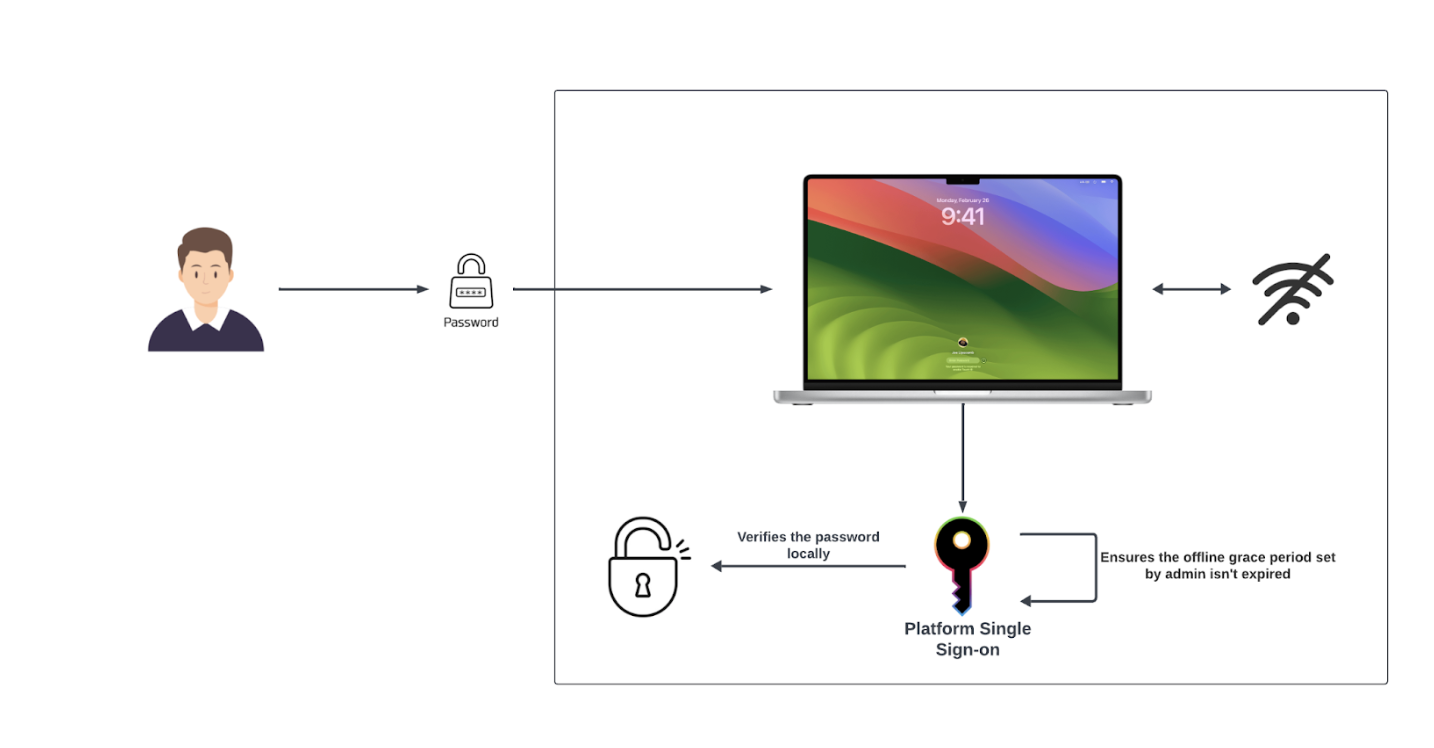
However, this can create challenges for users who travel frequently or face internet connectivity issues. If their device can't reach the Okta server, they might be blocked from logging in. To avoid this, admins can set the “AllowOfflineGracePeriod” policy. This allows users to log in while offline for a set amount of time based on their last successful Okta authentication. This feature supports users’ ability to log in during network outages, but once the grace period expires, they'll need to reconnect to the internet.
Once these policies are in place, every macOS account must have its password validated by Okta, whether the account is registered or not. While this improves security, it can cause problems during rollout when unregistered accounts may be locked out.
To prevent this, admins can enable the “AllowAuthenticationGracePeriod” policy, giving temporary access to unregistered accounts through local authentication. This grace period provides a smooth transition without locking users out during the rollout process.
Administrators often use service accounts for maintenance purposes. To avoid locking these accounts out, they can be added to the “NonPlatformSSOAccounts” policy. This policy excludes certain local accounts from the new authentication rules, which no longer requires them to register with Platform SSO while allowing important maintenance tasks to continue without interruption.
Benefits of using Okta and Platform SSO on macOS 15
Adopting Platform SSO and Okta Device Access to delegate macOS authentication offers several key advantages:
- Enhanced security: Security is a top priority for every organization, and with the correct policies set, Platform SSO registered devices can only be accessed after the password is successfully authenticated against Okta. This minimizes unauthorized access as only Platform SSO-registered users can log in to the device with a valid Okta password. Additionally, organizations can leverage Okta Desktop MFA feature, available with Okta Device Access, to enforce multi-factor verifications for users logging into their devices.
- Improved user experience: Platform SSO links the Okta account to the device and syncs the local password with the Okta password, meaning a user only needs their Okta username and password to access their machine. This eases the cognitive load of managing multiple passwords. Furthermore, policies can be set to allow Apple biometrics to unlock, enabling a smooth user experience without compromising security.
- Strong password policies: “Abcd1234,” “password,” and ”qwerty” are the nightmares of IT and security departments. A 2021 survey found that over 80% of confirmed breaches are related to stolen, weak, or reused passwords. Thus, it’s crucial to strengthen passwords by enforcing policies like minimum password length, blocking commonly known and breached passwords, inclusion of special characters, etc. Okta's password policy configurator makes this possible, and since the Okta password is used to access the device (and synced thereafter), the same security rules are enforced for the device password.
- Simplified account management: Creating device accounts for new employees and revoking device access for departing ones can be time-consuming if done manually. These processes can be simplified by using Okta Device Access. For example, using the Just-in-Time Local Account Creation feature, employees can simply type in their Okta username and password on a Platform SSO registered device and a new macOS account with configured privileges will be provisioned for them. Furthermore, if the login authentication policy is set to “requireAuthentication”, deactivating or deleting a user in Okta will revoke their access to the machine.
- Compliance and auditing: Compliance is a critical focus for organizations bound by regulatory requirements. Every delegated authentication to Okta is logged, and customers can leverage Okta's comprehensive system logs to get detailed insights on which user accessed the device from which location and IP address. The logs provide visibility over access events and help organizations develop compliance reports and show regulatory adherence.
Delegating macOS login authentication to Okta through Apple's Platform SSO framework offers a streamlined, more secure, and efficient method of managing user access. By enhancing security protocols, centralizing Identity management, and simplifying onboarding and offboarding, organizations can better protect their macOS devices while providing a seamless user experience.
As Apple continues improving the Platform SSO framework, the integration with Okta remains a powerful solution for businesses looking to enhance their authentication processes across macOS devices.
To explore how Platform SSO and Okta can further strengthen your macOS authentication processes, you can learn more at https://help.okta.com/oie/en-us/content/topics/oda/macos-pw-sync/update-password-sync-for-mac-15.htm
These materials are intended for general informational purposes only and are not intended to be legal, privacy, security, compliance, or business advice. This posting does not necessarily represent Okta's position, strategies, or opinion.






