ThreatInsights Demo
Details
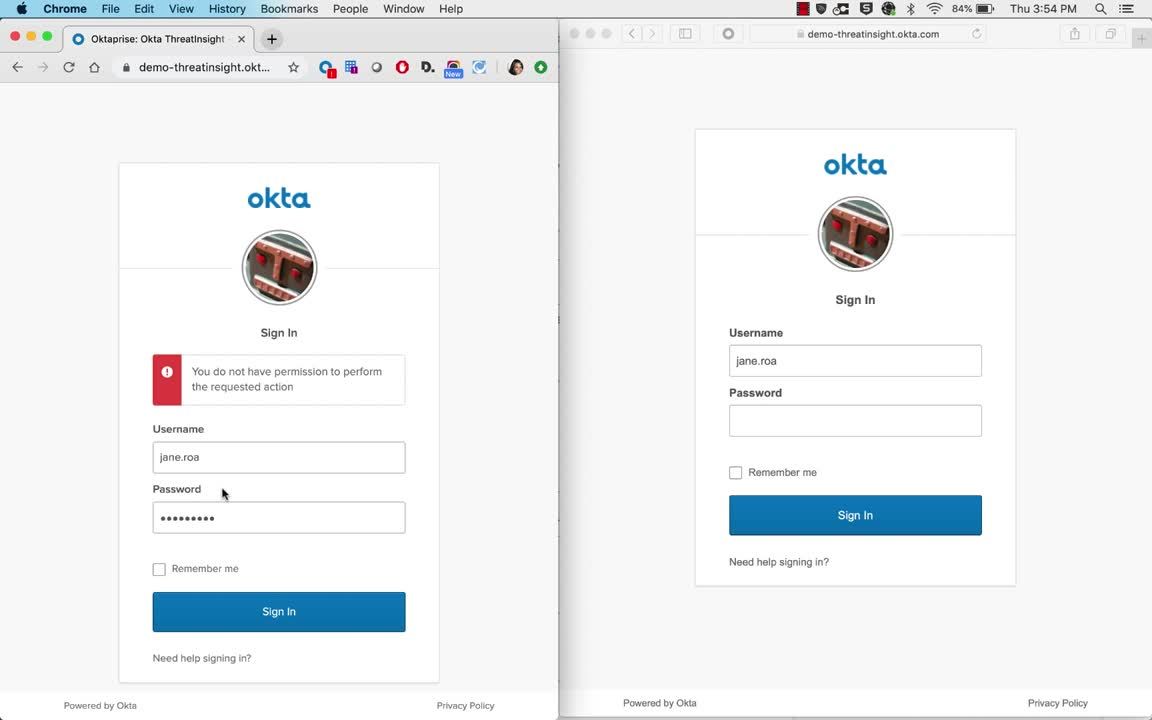
The detection of a threat takes place prior to authentication evaluation. Requests that are blocked by ThreatInsight prevent user lockouts from suspicious IP addresses. Admins can audit sign-in requests to identify malicious activity by referring to the system log and choose to block IP addresses identified as malicious.
Watch the demo to learn more.