
Workforce Identity Cloud
Phishing Resistance
Protect against threats with phishing resistance
Get end-to-end phishing-resistant authentication that protects your organization and supports your employees, partners, and extended workforce.
Our platform is built to empower, not impede
Our Identity-powered security offers robust protection against phishing attacks that extends across the entire user journey — from the very first time a new employee is onboarded, through every authentication and recovery process — all without disrupting productivity.

See why phishing resistance matters
Learn why more organizations are interested in going beyond MFA and pivoting to phishing-resistant authenticators.
74% of all data breaches involve the human element.*
Cybercriminals have identified end users as the weakest link in the authentication flow, helping them gain unauthorized access to organizations’ infrastructure.
Achieve defense in depth with Okta
Establish a strong security posture that adheres to Zero Trust principles.

Protect
- Reduce the attack surface with secure, phishing-resistant authentication with adaptive access policies
- Audit your security posture and get recommendations for improvements with HealthInsight
- Create a consistent, familiar user experience across platforms and devices

Detect
- Perform device security checks silently upon every app access during the course of an active session
- Enhance logging for faster detection of anomalous user activity
- Amplify security insights by synthesizing Identity threat signals across your apps and security stack

Respond
- Proactively block malicious IP addresses with ThreatInsight
- Enable self-service factor recovery in a phishing-resistant manner
- Create access policies and workflows to automate responsiveness and take quicker action against suspicious activities
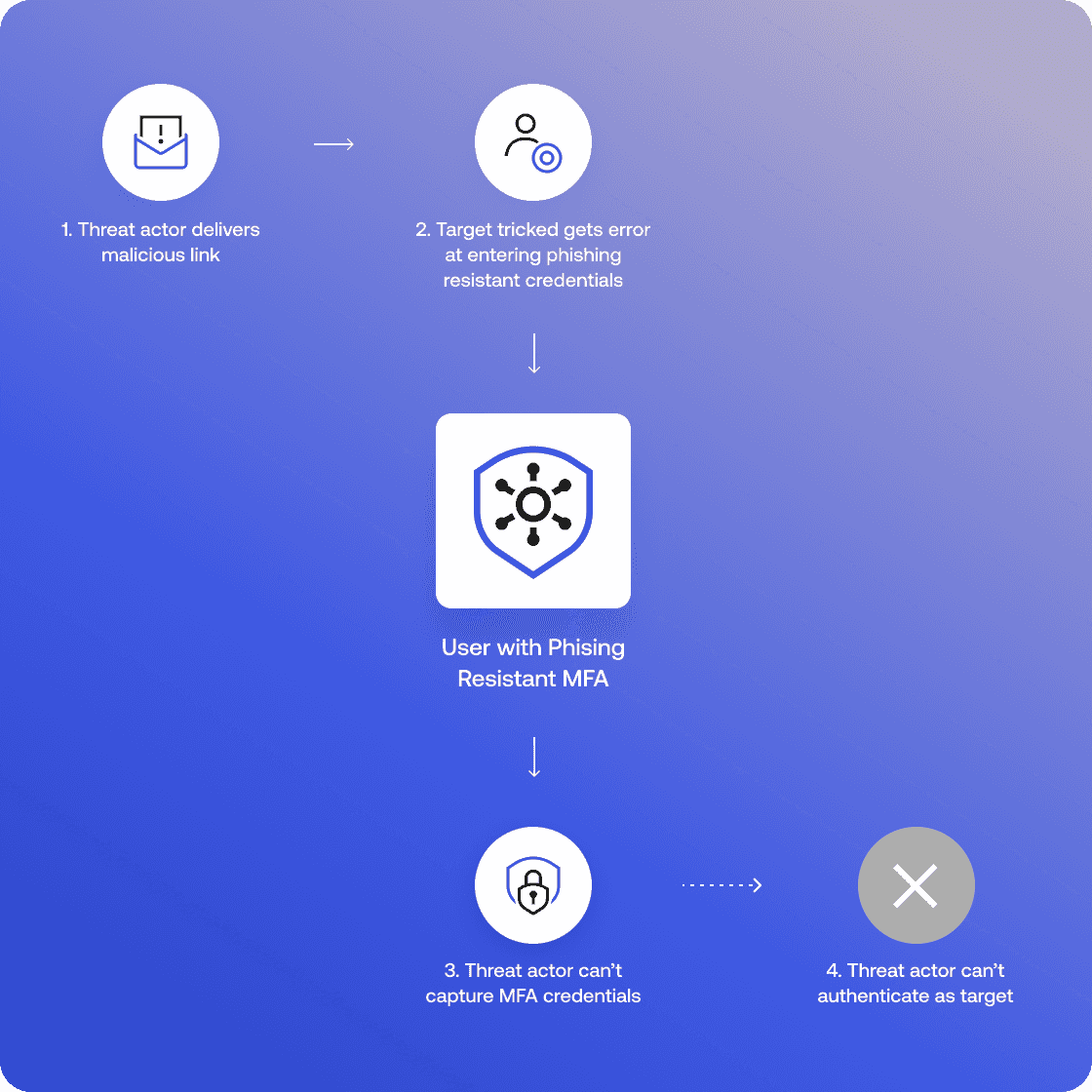
Okta FastPass
Protect against real-time credential phishing attempts on managed and unmanaged Windows, iOS, Android, and macOS devices.

This authenticator supports security keys such as YubiKey or Google Titan, and platform authentication that's cryptographically bound, and uses biometric data, such as Windows Hello or Apple Touch ID. Okta also helps make WebAuthn even more secure by allowing only hardware-protected keys in auth flows.

Our platform supports secure access to federal information systems and assures appropriate levels of security for all applicable federal applications, enabling end users to use smart cards with a x.509 compliant digital certificate.

Yubico pre-registers users and delivers YubiKeys that are ready to go. It provides the strongest level of Identity assurance and defense against phishing and man-in-the-middle attacks, while also delivering a simple and seamless onboarding experience.

When the risk level associated with a login is high, additional authentication factors will be required for low, medium, and high-security apps, enforcing phishing-resistant authenticators where possible.
Explore factor sequencing and flexible policies.





"To harden our security posture, the priority was to ensure all logins to Okta come from registered devices and use phishing-resistant MFA. Okta FastPass has enabled us to achieve that goal.”
Eric Richard
CISO and SVP of Engineering Operations, HubSpot
Okta's journey to passwordless and phishing resistance
Learn how we build best-in-class solutions by developing and testing them on our own platform, with our own employees.