Bringing Modern Access to Traditional On-Prem Apps
Modernize Access to Traditional On-Prem Apps
Large enterprises looking to securely connect their employees, contractors, partners, and customers to thousands of applications and resources face numerous challenges. In particular, mature organizations inevitably use at least some resources that were built with technologies and standards from previous generations. For example, many on-premise business systems still incorporate outdated authentication techniques which are closed, inefficient, and offer inadequate protection against today’s threat landscape.
As companies look to the cloud to modernize and reduce their data center footprint, hybrid IT has become the norm. Most enterprises maintain at least a few key on-prem web apps that are critical to their business, in concert with more and more newer apps and services from multiple cloud providers. While they’ve adopted advanced security practices to manage access to cloud services, too many IT and security teams have either ignored the risks posed to their traditional on-prem apps or continued to rely on antiquated approaches because of time and budget constraints.
Today, forward-looking organizations are recognizing the need to protect both on-prem and cloud apps from a single identity provider. Traditional on-prem applications that lack modern standard support can now be integrated into a cloud-based identity-as-a-service (IDaaS) architecture with Okta—letting you deliver a simple, yet secure user experience without changing the way those apps work.
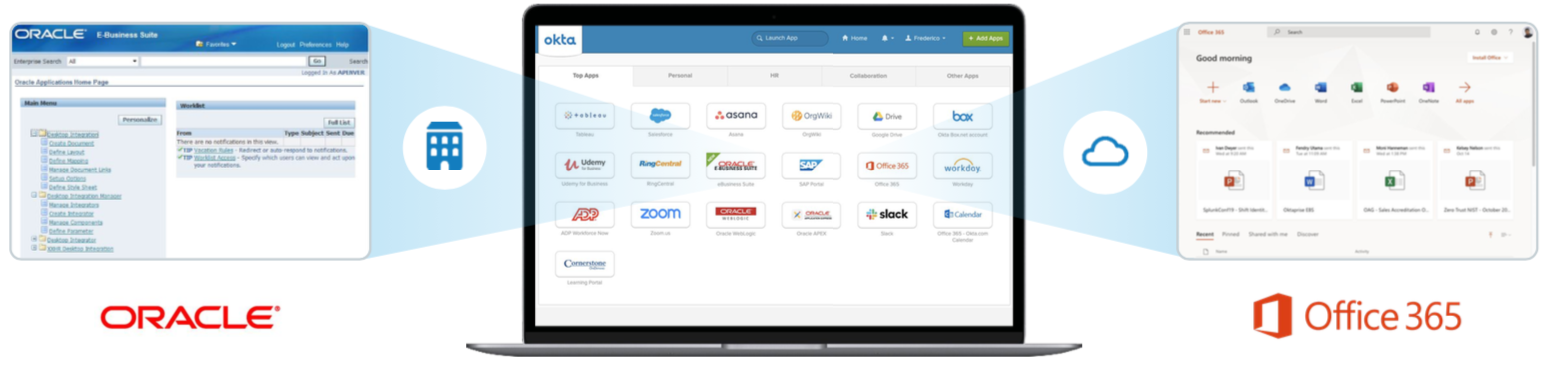
With Okta, organizations can control access to the Hybrid IT from a single solution
This guide will walk you through the drivers, considerations, solutions, phases, and best practices for modernizing identity and access management with Okta.
Drivers for identity & access modernization
There are several reasons business are looking to layer modern IDaaS onto their on-prem resources, including:
Challenges:
• Digital transformation
• Cloud journey (shifting towards building 100% cloud, mobile IT)
• Higher user expectations
• Competitive differentiation in new markets
• New security exposure (apps, cloud, speed)
• Mergers, acquisitions & divestitures
In order to support these business needs in an agile, future-proof way, organizations must deliver the following solutions:
Solutions:
• Secure omnichannel experiences
• Lower cost and complexity for IT operations
• De-risking and building a future foundation
• Modern frictionless UX
• Rapid time-to-value and adoption
And to meet the security requirements of a typical enterprise, modern identity approaches should protect access to resources regardless of their type or deployment locality, while also protecting all users—employees, contractors, partners, and customers. This requires technology capabilities such as:
Requirements:
• A common unified identity platform with adaptive digital security capabilities
• Agility to integrate quickly, securely, and without disruptions
• Integration with not only popular SaaS services, but mobile apps and mobile access, traditional on-prem web applications, and multiple cloud infrastructure providers
• New types of multi-factor authentication and passwordless access
• Continuous, contextual access controls based on information such as geolocation, IP reputation,
and device posture
• Enterprise-grade scalability, availability, and support for zero trust strategies
Limitations of common approaches
There are several reasons these business and security requirements are difficult for IT and security teams to meet. The first is that traditional on-prem apps don’t natively work with cloud solutions because they were created long before modern authentication and federation approaches – such as SAML, OpenID Connect, and OAuth – emerged. To fully understand the differences between the various methods for securing access to apps, it’s helpful to review common legacy authentication patterns used to authenticate end users.
Legacy authentication patterns
No authentication
This is also known as “anonymous access.” In this pattern, anyone can access a site without authenticating first. For web applications intended to be public, this is fine, but sometimes you require more security. In these cases, you can improve security by forcing authentication, and allowing access only to authenticated users.
Header-based authentication
With this approach, a web access management (WAM) system prompts the end user for authentication, then injects identity data into the HTTP headers in the user’s browser for consumption by the protected application. However, most WAM systems—like CA Siteminder, Oracle Access Manager and Tivoli Access Manager—are in the process of being deprecated. Migrating to a modern proxy-based architecture is a future-proof way to accommodate this pattern.
Client certificate-based authentication
This pattern utilizes a PKI certificate to authenticate the end user to an application, and is facilitated by most web servers natively.
Windows or Kerberos authentication
This pattern silently logs each user using the active Windows domain session. This requires domain permissions and only works for internal users by default. By integrating with a proxy-based architecture, you can provide remote access to these applications.
URL-based authorization
This pattern is complementary to the authentication patterns listed above. In URL authorization, a WAM system evaluates the URL (also known as realm or URI) requested by the end user against an authorization policy before granting access to the resource. The authorization policy contains rules—usually based on groups—to validate if a user should have access to the resource.
The complexity conundrum of multiple local accounts
Many organizations assume their on-prem apps’ access controls are secure enough on their own, and don’t require the added protection of an access management solution. Unfortunately, without a consolidated approach, your users have to maintain separate passwords and multi-factor authentication (MFA) factors for each of the resources they need to get their work done. This quickly leads to password fatigue and poor password hygiene, which puts your organization at risk. But if you want to address the problem through single sign-on (SSO) or MFA tools, you’ll need to configure that separately for each system.
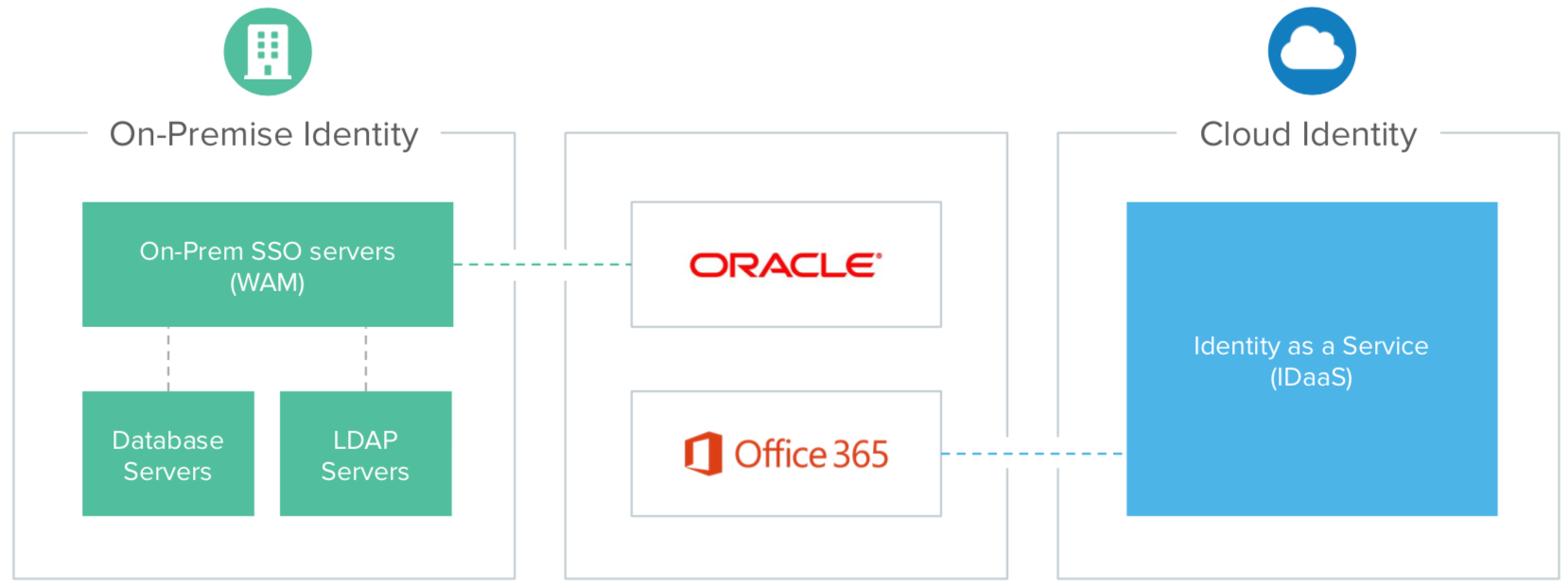
Complex deployment with separated identity stacks for on-prem and cloud apps
For example, if you use WebLogic, it has its own specific requirements for adding SSO and MFA, so a WebLogic administrator must implement and maintain the configuration. The same is true for every other traditional system or custom on-prem app in your IT environment, some of which may only support certain MFA factor types—making it a headache to keep security policies and access controls up to date. Plus, employees have to follow multiple steps to gain access to WebLogic, and those are completely different from how they log into their other apps. Too often, security teams throw up their hands at all this complexity and put off modernizing in the hopes that old-school perimeter-based security is enough to protect their older systems.
However, you should keep in mind that on-prem systems running within a corporate network are still vulnerable from data breaches caused by internal employees. Recent studies found that 87% of businesses point to human error as their biggest security threat and 59% suffered an insider attack in 2018, up from 33% the previous year.

Risk exposure from lateral movement behind the firewall
To implement a quick fix for identity and remote access to on-prem apps, many organizations rely on virtual private networks (VPNs) instead of focusing on identity. VPNs are a great tool for IT and system administrators, who need remote access to the entire network and infrastructure to do their jobs. However, many end users only require access to a few specific on-prem web applications—like your ERP, Intranet portal, or HR system. For these users, using a VPN introduces security risks in the form of lateral attacks and user experience friction.
Lateral Movement
VPNs traditionally grant access at the network level, where many resources—including servers, desktops, network components, and file systems—can be reached. The more end users you have using VPNs just to access web apps, the higher your risk that an attacker could compromise a VPN account in an attempt to reach other network components through lateral movement across your network:
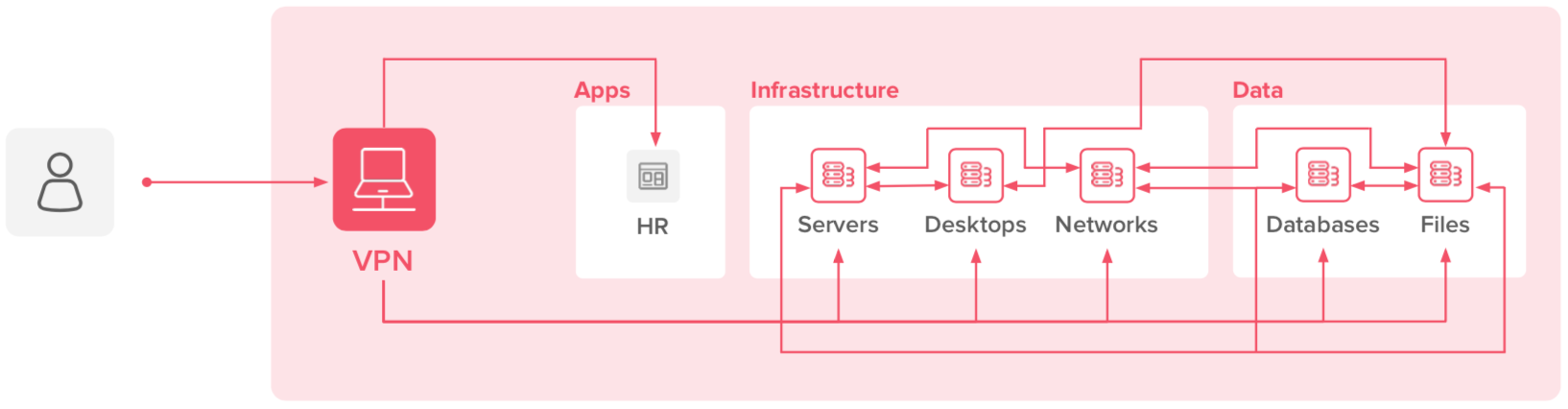
Lateral movement after a VPN account compromise
Bad actors take advantage of obsolete perimeter-centric security practices to get behind your firewall and leverage the unfettered access they gain to move laterally from one resource to the next. Ideally, users should be granted access only to the web apps they need, and access to your network and infrastructure should be limited based on least privilege policies.
User experience friction
VPNs are also cumbersome because they require many components—including complex networking and desktop client apps—and are difficult to scale to non-managed devices, the extended enterprise (like partners, contractors, temp workers), and to infrastructure-as-a-service (IaaS) environments. Users often complain of connectivity issues, lack of timely ticket resolution when they have access problems, having to still maintain multiple passwords for each app, and the inability to access daily work from devices other than their corporate laptop. All of these issues add costs for IT admins, who have to navigate multiple account recovery flows and complex network issues:
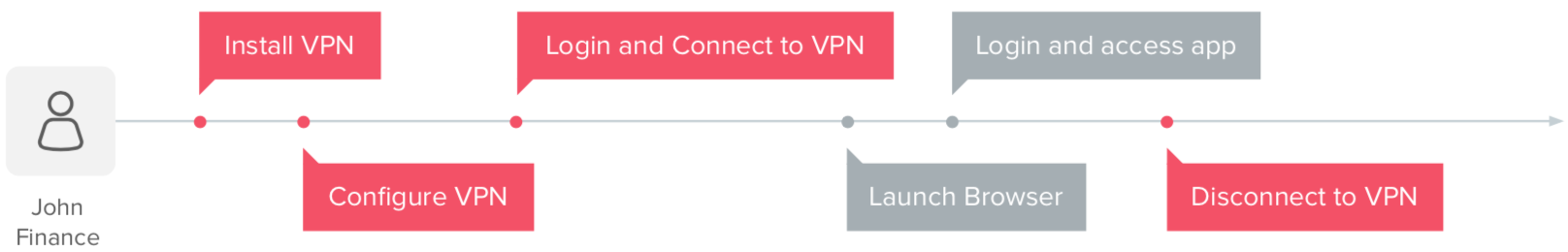
Steps for an end user to access an on-prem app on the VPN
Bringing next-gen authentication to on-prem web apps
Clearly, on-prem web apps require the same protections as other critical tools, since it’s just as important to implement cutting-edge security (or maybe even more so) for your on-prem systems as it is for cloud apps and infrastructure. If you’ve already taken steps in this direction with a legacy SSO or WAM solution, be aware that your provider is likely in the process of deprecating its on-prem WAM offering, and visit our WAM migration guide to learn more about how you can prepare.

Many traditional and custom applications have to be modified in order to natively support the modern authentication standards we mentioned above, like SAML or OIDC. These token-based approaches can eliminate the need for direct communications between identity platforms and service providers, avoiding complicated networking changes or proxy requirements. While all of that sounds great in theory, modernizing these applications probably competes with your enterprise’s other priorities, so it’s rarely going to happen immediately or completely. The reality is that without a next-gen identity and access management platform like Okta, you’ll be dealing with a disjointed architecture made up of new applications (that support modern standards), and older applications that do not, for some time.
Okta Identity Platform: Overview
This chapter provides an introduction to Okta’s identity platform, including how it addresses the limitations discussed above to deliver security to cloud, mobile, and enterprise applications from a single pane of glass. With access controls consolidated into a unified platform, IT and security administrators only have to write access policies once, and can rest assured that the appropriate users will have safe access to the systems they need. Employees and other end users benefit from more advanced, consistent experiences and gain one central way to access all of their critical apps—whether those apps reside in the public cloud, on-prem, or on private cloud infrastructure—from any device or network.
Overview
Okta is an IDaaS platform that provides solutions for authentication, adaptive MFA, SSO, a unified directory, account provisioning, and API authorization. Okta is:
• Provided as a cloud service
• Globally available, 100% multitenant, stateless, and redundant
• Regularly updated with security enhancements and new features
• Built with a zero planned downtime architecture (the service is updated live, without scheduled downtime)
Okta’s identity and access management solution supports both modern and traditional enterprise applications. For modern applications, we provide the Okta Integration Network, a catalog of 6,500+ out-of-the-box integrations. We offer extensive support for open patterns that securely connect your users to any technology while avoiding vendor lock-in. For integrating with on-prem enterprise apps, we provide the functionality of multiple legacy identity solutions combined—i.e., WAM, LDAP, RADIUS, SSO, MFA, and provisioning—while mitigating infrastructure dependencies.
Secure access to on-prem web apps with Okta Access Gateway
In a typical hybrid IT environment, organizations often use different identity solutions to protect their cloud apps, hosted cloud services, and on-prem web apps. Using Okta Access Gateway, you can now protect all your different resources with a single identity solution. Our platform includes native integrations for the most popular and complex on-prem web apps—including Oracle E-Business Suite, PeopleSoft, JD Edwards, and SharePoint—as well as support for traditional authentication patterns—such as Kerberos, IWA, and reverse proxy header-based authentication—so you don’t have to make any changes to your existing on-prem apps to take advantage of the modern security benefits we offer.
How Okta works
Our platform brings Okta’s access management controls (such as SSO and adaptive MFA) from the cloud to your on-prem apps for a more robust zero trust security approach using the following architecture:
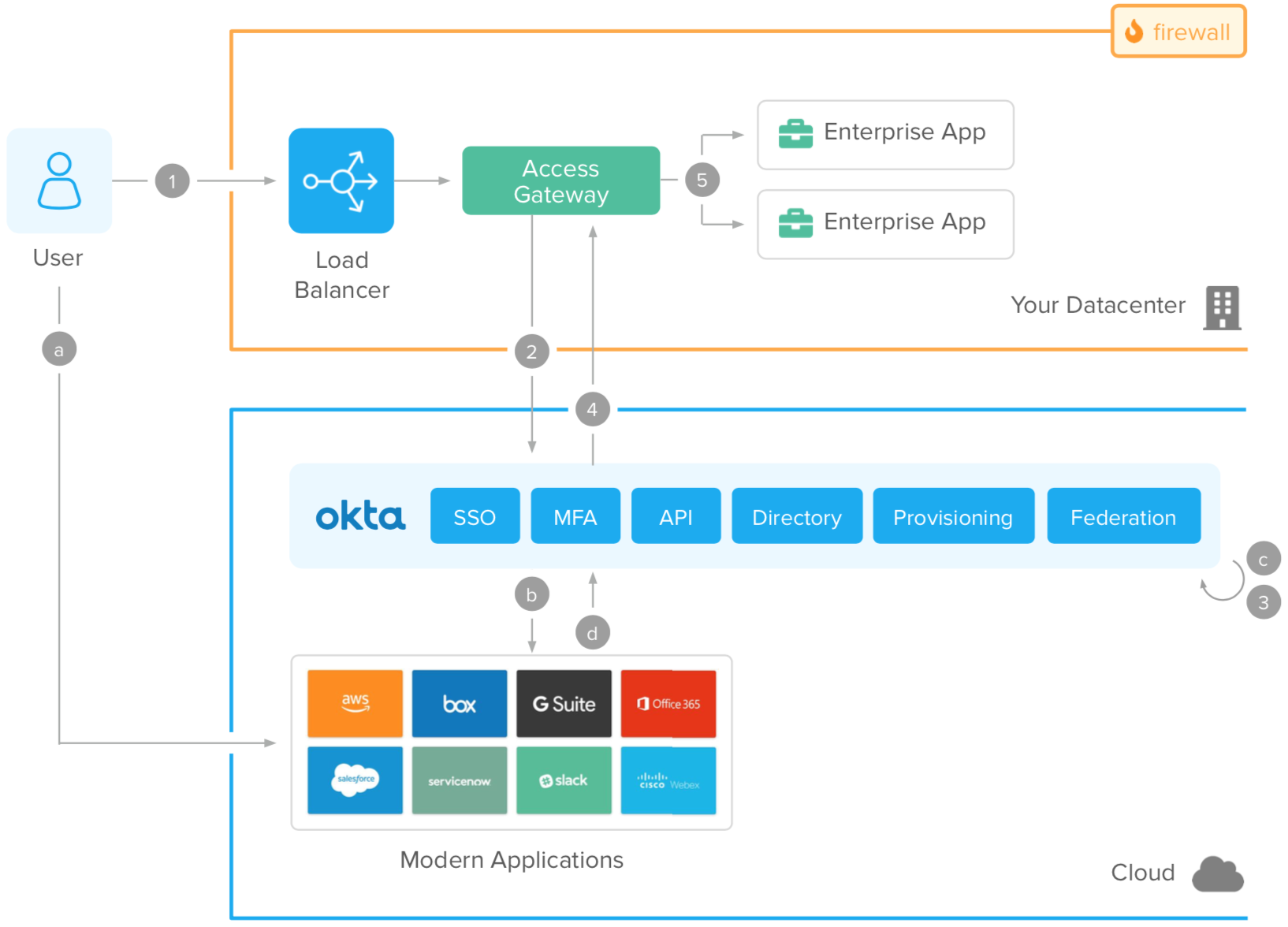
Modern (cloud and mobile) application flow
A. User accesses a cloud or mobile application.
B. The app validates the session. If there’s no session, it redirects the user for federated authentication in
Okta.
C. Okta authenticates the user using its native identity functions: SSO, user directory store, adaptive MFA, and federation.
D. Upon access approval, the user is redirected back to the cloud or mobile app. The app completes the federation process, establishes the user session, and responds to the user request.
Traditional (on-prem) application flow
1. User accesses a web application via HTTPS.
2. Okta Access Gateway intercepts the user request. If the session is invalid, it redirects the user for a
federated authentication on Okta.
3. Okta authenticates the user. All identity functions (SSO, user directory store, adaptive MFA, and federation) are built natively into the identity platform.
4. Upon access approval, the user is redirected back to the Access Gateway, which completes the federation. Because the gateway is capable of working with different kinds of applications, it doesn’t require native integration.
5. The enterprise app captures the user information, processes it, and responds to the request
Primary components of hybrid access
• Okta
Okta provides SSO, adaptive MFA, API authorization, user directory, account provisioning, and federation in the cloud for modern apps (via native standards-based integrations) and traditional enterprise apps (via Okta Access Gateway).
• Cloud and mobile applications
Modern applications with direct access to the internet (also known as service providers).
• Access Gateway
This is a lightweight appliance that bridges the gap between our core identity platform and your enterprise applications. It leverages federated authentication for SSO and adaptive MFA and connects to on-prem apps using a variety of authentication patterns and standards, so it doesn’t require native integration or any changes to how those apps work today.
• Firewalls
Network solutions used for segmenting traffic between components. Network segmentation is required to avoid unauthorized access to enterprise apps and to avoid traffic sniffing or spoofing.
• Traditional enterprise applications
On-prem web applications protected by the gateway. These apps receive traffic via HTTP servers with user information on HTTP headers.
Advanced Okta capabilities
Okta delivers sophisticated security features that go beyond individual application controls, VPNs, or even WAM solutions. With these capabilities, you can bring robust identity and access management to new use cases, improve your security posture, and boost return on investment.
Here are some examples of how Okta can bring modern access to a variety of identity projects:
• Provide access and SSO to all users—employees, contractors, partners, and customers—from a single identity solution.
• Accelerate Office 365 adoption and avoid PowerShell complexity with Okta SSO, MFA, and Lifecycle Management.
• Automate user onboarding and offboarding to applications and AD/LDAP directories with Okta Lifecycle Management and HR integrations.
• Consolidate AD domains and reduce your AD footprint with Okta Universal Directory.
• Meet compliance and secure access to VPNs, virtual desktops, and network applications with Okta MFA.
• Reduce password-reset costs with Okta’s self-service password reset for cloud applications, AD, and LDAP.
• Secure access to your custom APIs with Okta API Access Management and Okta’s OAuth and OpenID Connect APIs and SDKs.
• Secure access to cloud and on-prem servers by implementing Okta provisioning, SSO, and MFA workflows to Linux and Windows servers over SSH and RDP.
Modernization Strategy & Phases
Based on our experiences across thousands of customers, we recommend adopting a modernization strategy in incremental phases, so you can retire outdated approaches and transition to a new identity stack at your own pace. Once you’ve completed your initial IDaaS implementation, with all of your primary applications and cloud resources (SaaS, PaaS, and IaaS) integrated into Okta, you’ll want to rethink the methods you use to integrate and protect access for any new additions to your digital ecosystem.
As you look to enable modern access to on-prem web apps, there are four primary steps to consider:
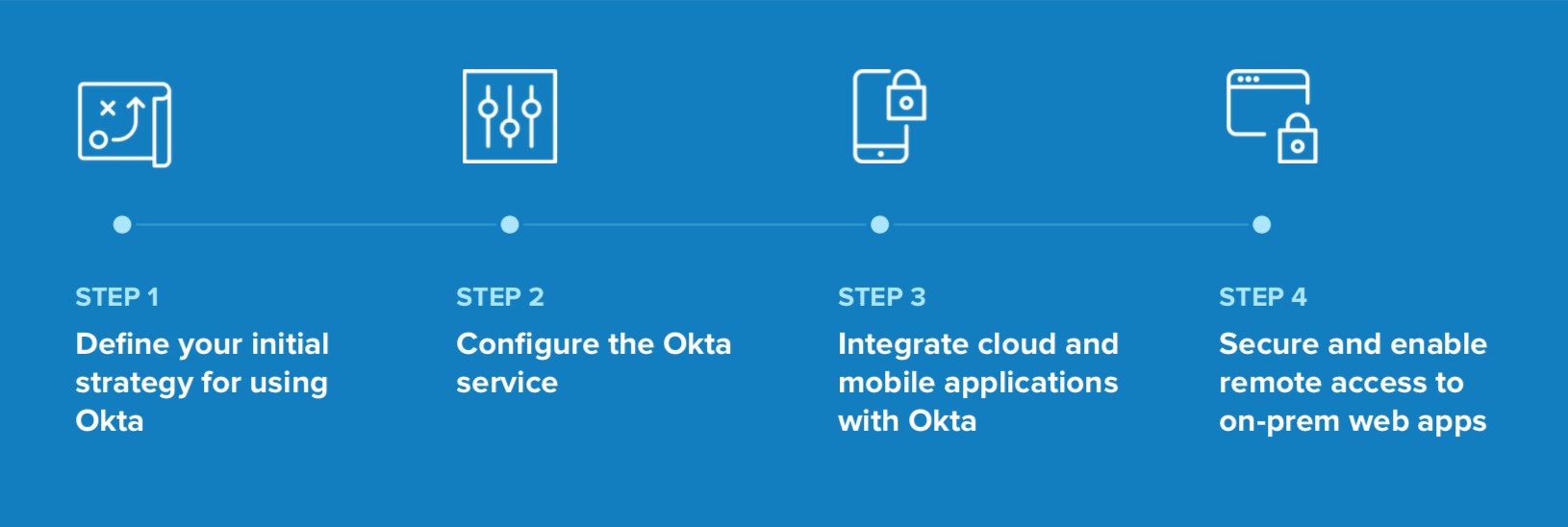
Step 1. Define your initial strategy for using Okta
In this step, first list the requirements for your identity solution. Examples include:
• What users—i.e. employees, partners, customers, contractors—will use Okta?
• Which systems—i.e. HR, AD, LDAP, or Okta—will act as the source of truth (or master) for each type of user?
• What are your authentication policies and account recovery requirements?
• What systems store and validate user passwords?
• Which apps support modern authentication standards vs. legacy patterns?
• What MFA factors will you use?
• What applications will you integrate with Okta SSO?
• What applications will have accounts provisioned by Okta?
These details will help you scope which services and settings to configure in your Okta tenant. In particular, when thinking about how to best protect various applications, it’s important to classify both cloud and on-prem apps. Determine whether each app in your environment supports a modern standard such as SAML or OpenID Connect. Most enterprise web apps have a built-in SAML capability, but it may need to be enabled, and sometimes requires an add-on purchase. Once that’s set up in the app, you’ll be able to use pre-built SAML, WS-Fed, or OpenID Connect integrations from the Okta Integration Network to connect the application rapidly with Okta SSO.
If for some reason an integration you need is not available, you can create your own using the WS-Fed template, or the SAML and OpenID Connect Application Integration Wizard from Okta. In addition, be sure to identify which web apps use legacy standards and will be integrated using Okta Access Gateway.
Step 2. Configure the Okta service
During the configuration step, you’ll start defining your policies and settings in Okta. In order to protect traditional apps with the Okta platform, you’ll first need to get an Okta tenant, which is available straight from the cloud and is fast to implement. Next, install Okta Access Gateway, which is offered as an appliance and connects seamlessly to Okta in the cloud. Install and load your Okta Access Gateway onto each data center or private cloud infrastructure where you run on-prem apps.
Step 3. Integrate cloud and mobile applications with Okta
Now that you’ve installed and configured Okta, it's time to integrate apps. You can start with your most important cloud apps using the Okta Integration Network, and gradually integrate others. Okta provides prescriptive integration guides for 6,500+ applications to support both net new and existing subscriptions. For your existing apps, Okta helps you to easily import and match user records, as shown in this example with Salesforce.com:
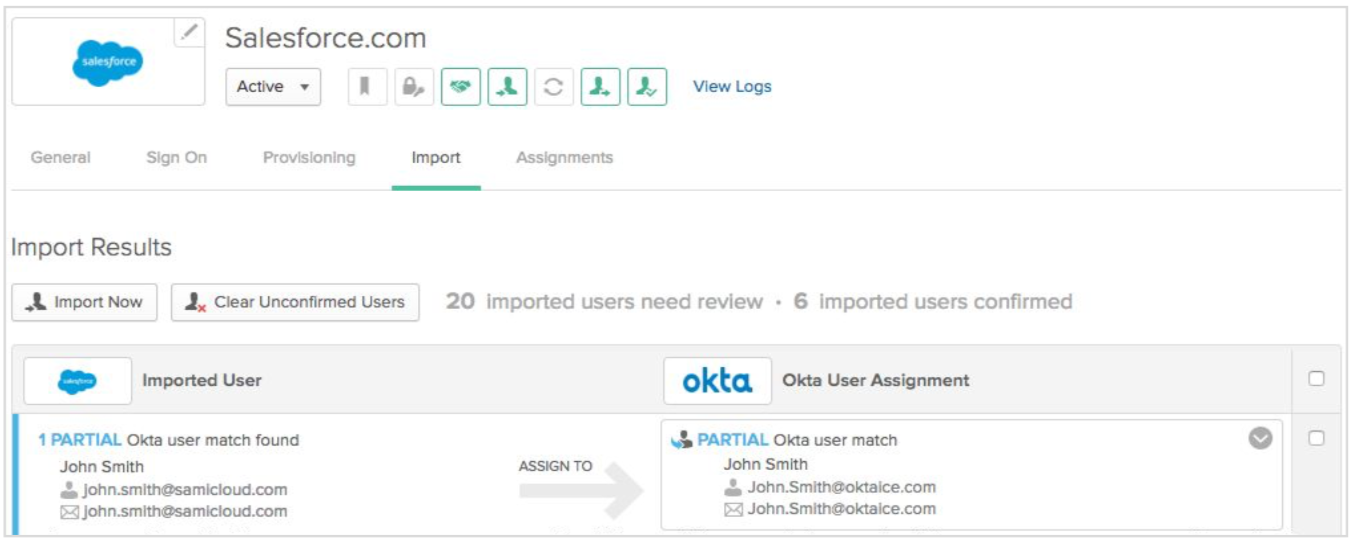
Screenshot - Okta Integration Network: Onboarding systems with pre-existing users
A typical Okta deployment starts with 10-15 applications and scales to hundreds of applications fast. Depending on your environment, key tasks during this phase might include:
• Installing an LDAP or AD Agent to sync users and groups with Okta
• Configuring an initial authentication and password reset policy
• Configuring a policy for MFA enrollment and enforcement
Because Okta is delivered as a cloud service, all of this can be completed quickly. Deployments usually take anywhere from just 6 weeks to 4 months for larger scale and scope projects. By the end of this process, your users will be set up to access the apps you’ve designated via Okta credentials. Since Okta is a flexible subscription-based platform, you can always expand your deployment over time. Connecting additional resources to Okta or turning on more features like adaptive MFA are trivial tasks that won’t require installations or manual integrations to existing modules.
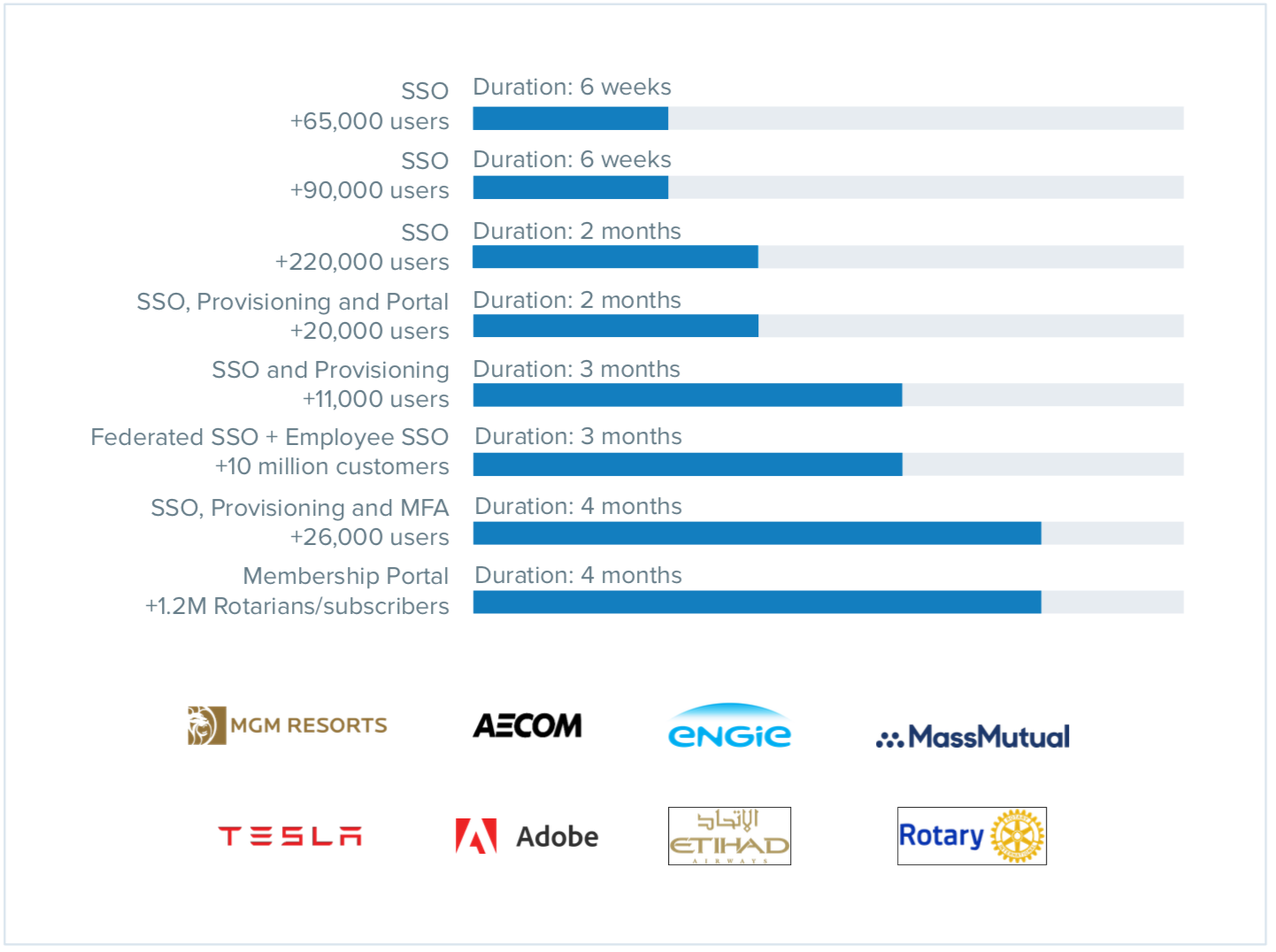
Examples of time to deploy and rollout Okta SSO, MFA, and Provisioning across different companies and industries
Step 4. Secure and enable remote access to on-prem web apps
The last step is to bring your entire hybrid environment together by adding on-prem web applications to Okta via Access Gateway. We recommend that you start with bringing in low-risk applications that share the same type of integration (e.g. header-based apps), and grow from there. For each on-prem web app, this simply entails:
• Integrating the app with Okta Access Gateway using Okta’s app template
• Following Okta’s simple step-by-step wizard to connect each app with your gateway
• Enabling access via the Okta dashboard
As you connect each traditional app with Okta, your users will start seeing these apps on their dashboard alongside SaaS apps, and will benefit from full SSO and MFA protection with a single login. They’ll enjoy simple, direct access to all of their apps from one place, without VPN clients, connections, or risk of allowing lateral movements.

Okta dashboard with access to cloud and on-prem apps
Benefits of Modernization
By following these steps to modernize identity with Okta, your IT, user, and business stakeholders will each realize significant business value, including:

Each app you integrate with Okta will instantly benefit from our powerful SSO and MFA capabilities, as well as our weekly security and feature improvements. Your users will gain the ability to directly reset their passwords as needed using self-service. Additionally, with the full spectrum of business apps (both cloud-based and on-prem web apps) displayed on Okta’s mobile- and desktop-friendly dashboard, they will experience increased productivity on any device they prefer. When it comes to accessing on-prem web apps through Okta Access Gateway, your users will no longer require a VPN client or have to log in multiple times, since sessions are established directly on the application. Furthermore, newly unified access policies will help your organization mitigate password attacks across its entire universe of hybrid IT.
 Consistent, unified, seamless protection for hybrid IT
Consistent, unified, seamless protection for hybrid IT
As your single identity provider, Okta can protect access to every hybrid IT resource, whether it exists in the cloud or on-prem. Since we enable administrators to manage all identity and access needs from one central console, they’ll no longer have to write and audit security policies, users, groups, and MFA policies across multiple systems. This saves significant administration time and effort, while enabling you to easily and seamlessly deliver a consistent, frictionless sign-on experience for all your users.
With a consolidated platform for all your apps, infrastructure, and APIs (from cloud to ground), you can eliminate identity silos and protect each type of user. What’s more, your employees will enjoy public cloud access to both on-prem and SaaS apps through Okta SSO and MFA (without even having to know where their apps are hosted). They simply authenticate through their Okta portal once and can seamlessly connect to everything they need, without jumping through different interfaces. End users also benefit from modern functionality—such as passwordless access with touch ID—that helps them safely log in from any device or network.
 Stronger security posture
Stronger security posture
Okta strengthens overall security by consistently employing modern identity management measures across your hybrid IT resources. For instance, our platform makes it easier to standardize security policies, automatically deprovision accounts when needed, and roll out adaptive MFA to not just employees, but external users as well. Since Okta requires identical effort to deploy MFA for five on-prem apps as it does for a single app, you’ll be able to roll out new capabilities and controls more quickly. Plus, the policies you set for MFA will apply to every user, no matter which resource they’re logging in to.
This approach eliminates the security gaps that often result from inconsistently applying policies between different access management systems, and empowers organizations to advance beyond all-or-nothing perimeter-based security. As a result, you’ll avoid the lateral movement that happens when hackers get behind your firewall. With fine-grained, per-app security controls and access to the latest advancements in the industry, it’s possible to move towards a true zero trust posture. Our platform also lets you take advantage of security intelligence and insights across the vast Okta customer base to better protect your on-prem apps from large scale threats and attacks. This is key, since modern, mature IAM solutions reduce the likelihood of an attack by 50% and experience, on average, $5 million less in financial damages per breach.
 Lower cost of ownership and faster time-to-value
Lower cost of ownership and faster time-to-value
As a cloud service, Okta’s simple deployment model drastically reduces the licenses, updates, patches, middleware, database services, physical hardware, or other operational burden and maintenance costs that most legacy access management approaches require. In particular, by minimizing VPN usage for regular users, you’ll reduce your organization’s attack surface while avoiding all the effort of managing client VPNs and reducing your managed device costs.
Okta also does away with VPN-related hassles that negatively impact users who only need access to web apps. Instead, we provide users seamless and secure access to internal web apps and cloud apps through standard browsers and allow them to use self-service to reset passwords and customize their preferred MFA factors, which in turn reduces IT help desk costs. What’s more, when a user completes a password reset, it automatically applies to all of the Okta-protected resources in your hybrid IT environment.
To learn more about how to modernize your identity with Okta, reach us at okta.com/contact-sales.
About Okta
Okta is the leading provider of identity for the enterprise. The Okta Identity Cloud connects and protects employees of many of the world’s largest enterprises. It also securely connects enterprises to their partners, suppliers and customers. With deep integrations to over 6,000 applications, the Okta Identity Cloud enables simple and secure access from any device. Thousands of customers, including Experian, 20th Century Fox, LinkedIn, Flex, News Corp, Dish Networks and Adobe trust Okta to work faster, boost revenue and stay secure. Okta helps customers fulfill their missions faster by making it safe and easy to use the technologies they need to do their most significant work. For more information, visit us at www.okta.com or follow us on www.okta.com/blog.