CISO Guide: Secure Cloud and Mobile Data with Okta
This guide will explain how Okta helps you meet your security goals through detection of phishing, account-takeover and Man-in-the-Middle attacks, comprehensive log analytics, and field-level data encryption.
Executive Summary
As a CISO today, you face new and complex challenges to safeguarding your organization’s data. The days when all your applications and file servers sat safely behind a firewall, only being accessed from corporate-owned devices are gone.
Hackers are getting more resourceful and taking advantage of the shift of company apps to the cloud, where employees connect to them from all types of personal devices like smartphones, tablets, and Macs. To prevent data breaches, security teams must adapt.
The good news: By adopting secure cloud solutions, not compromising on user experience, and using contextual data about users and devices, you can more effectively detect hacks and improve the security of your cloud and mobile data.
Okta helps you meet your security goals through phishing and account-takeover detection, comprehensive log analytics, and field-level data encryption.
Detect Attacks and Protect the Organization
Phishing
Phishing attacks are a sneaky and effective way to steal data. Hackers simply have to trick a user into clicking on a fraudulent email link or installing a malware app on a mobile phone. When the unsuspecting user logs in, the hacker secretly makes away with the credentials.
In the battle against phishing attacks, multi-factor authentication (MFA) is key because it forces hackers to spoof an additional piece of information, such as a one-time passcode, or biometric data like a fingerprint.
Okta Adaptive MFA takes strong authentication one step further by using contextual data about users, their devices, and when and how they access applications, to build rich profiles of user behavior. This helps keep false positives low and improves your security by rolling out strong authentication to more applications.
Man-in-the-Middle Attacks
Man-in-the-middle attacks compromise the transport layer between a user and a cloud service. Hackers modify or steal messages by intercepting communication as it travels between endpoints.
Okta uses SSL pinning to ensure the integrity of communication between users and our service. MITM attacks be gone.
Field-Level Encryption and Secure Infrastructure
Your cloud and mobile data is distributed across many networks, applications, and devices, making it virtually impossible for on-prem monitoring tools to provide a complete record of activity across your organization. Even single cloud service providers are limited to the records on their own systems.
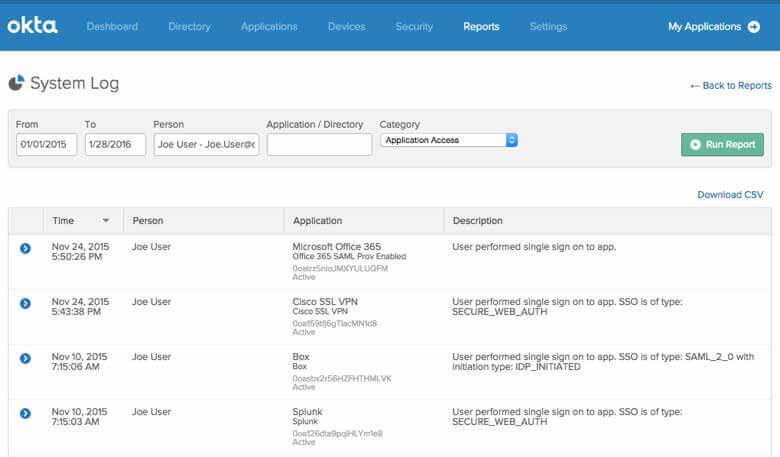
Okta offers a unified identity and access layer for your organization’s entire cloud and on-prem application ecosystem, making comprehensive log analytics possible once again. When a user’s credentials are stolen, you can quickly pull up a detailed record of all the applications accessed since the event. Your security team can run a simple trace from the Okta admin console, and quickly get a handle on the potential breadth of the breach, as well as a chronology of events leading up to the compromise.
If a service provider is hacked, Okta makes it easy to identify everyone in your company who was potentially affected, and all the applications they’ve accessed since. You can easily reset user credentials to immediately mitigate risk from service provider breaches.
Comprehensive Log Analytics
Encrypting disks and databases is no longer enough. Okta individually encrypts fields in its Universal Directory to protect customer data. Even if a hacker were able to steal Okta’s database, he would be unable to view individual user data. Custom attributes containing personally identifiable information, such as social security numbers, credit card data, or other confidential information—is all encrypted.
Okta’s infrastructure is designed to be both secure and highly available. We use SOC 2, Type I and Type II processes, formerly known as SAS 70, to successfully audit the operational and security processes of our service and our company. Okta meets US/EU and US/Swiss Safe Harbor requirements and we’ve published our controls in the Cloud Security Alliance Security, Trust & Assurance Registry (CSA STAR). We offer a HIPAA-compliant solution for organizations that require it, and are in the process of obtaining our FedRAMP compliance certification.
Conclusion
To secure the data on today’s cloud and mobile applications, CISOs must go beyond yesterday’s tools and look to the next generation of cloud-based security solutions. Okta can help you detect attacks, improve security, and make sure the sensitive data in your cloud applications stays where it belongs.
Even in today’s distributed cloud environment, you can mitigate the risk of phishing and account take-over attacks; access comprehensive application records quickly; and offer bullet-proof encryption of client data.
So go ahead—define your access policies. With Okta, you have a partner in protecting your cloud and mobile data.