Solution Brief: Modernize Enterprise IT
Executive Summary
Many enterprises are saddled with an IT architecture that has evolved organically over time. The realities of competing priorities, limited staffing and budgets often mean that systems and strategies remain in place far longer than originally intended. This often results in a significant burden of cost and complexity, and can compromise a business’s agility.
Recognizing this reality, many organizations have embraced modernization initiatives. Approaches vary between an incremental “two speed” model and the more ambitious “greenfield” method. Under either approach, a modern cloud-based identity management strategy is a critical catalyst in speeding the transformation process and ensuring systems and processes work together seamlessly.
Such an identity strategy helps businesses increase agility by deploying a single identity architecture, and facilitating change through automating many IT lifecycles. Businesses that embrace this change are able to decrease costs, increase efficient and accelerate growth.
The Challenge: Aging IT
If there is any constant in modern business and IT, it’s change. Mergers, acquisitions, changing priorities, new applications, services and platforms create a huge amount of flux in IT infrastructure.
Compounding reality is the fact that IT organizations are constantly being asked to do more with less. To provide value from shareholders, IT organizations push for efficiency, which often means making tough prioritization choices. When it comes time to choose between rolling out new business services and updating legacy technology, new services almost always win out.
But the long term impacts of these decisions add up over time. Maintenance creates a tax on IT. Updates and changes monopolize cycles, infrastructure to support legacy applications strains capital budgets, and staff training and retention becomes a critical priority.
The cost of aging IT
Left unchecked these impacts become a massive burden
• 71% of the IT budget for US federal civilian agencies is spent on maintaining legacy systems
• 65% of enterprise IT spend is on “run the business”
Two Approaches to Transformation
Recognizing the need to pay down this technical debt, many organizations are embracing IT modernization initiatives. Since no two businesses are the same, two distinct models for transformation are emerging, each with its own pros and cons:
1. The “two-speed” model focuses on improvements in specific areas of the IT architecture, while leaving some areas undisturbed
2. The “greenfield” model seeks to make broad, sweeping changes across the IT architecture
The two-speed model is often appealing to organizations that wish to minimize disruption and operational risks. It identifies a prioritized set of focused projects and changes, and can be useful where budget constraints might preclude larger efforts. To be successful, the two-speed model also assumes there are no issues with existing integrations and that current architectural complexity is manageable.
By contrast, the greenfield model seeks to make broad, sweeping change to maximize the return on investment of the modernization initiative. It takes a longer term view on budget, recognizing that sweeping change will take time, and that business benefits will accrue over the following years. At times, this model is chosen out of necessity, when an overly complex, “spaghetti” architecture is hindering business growth.
Identity Management is Key to IT Modernization
Under either approach, one of the biggest roadblocks to transformation is identity. 74% of enterprise executives surveyed believe IAM is critical or very important to digital business initiatives.
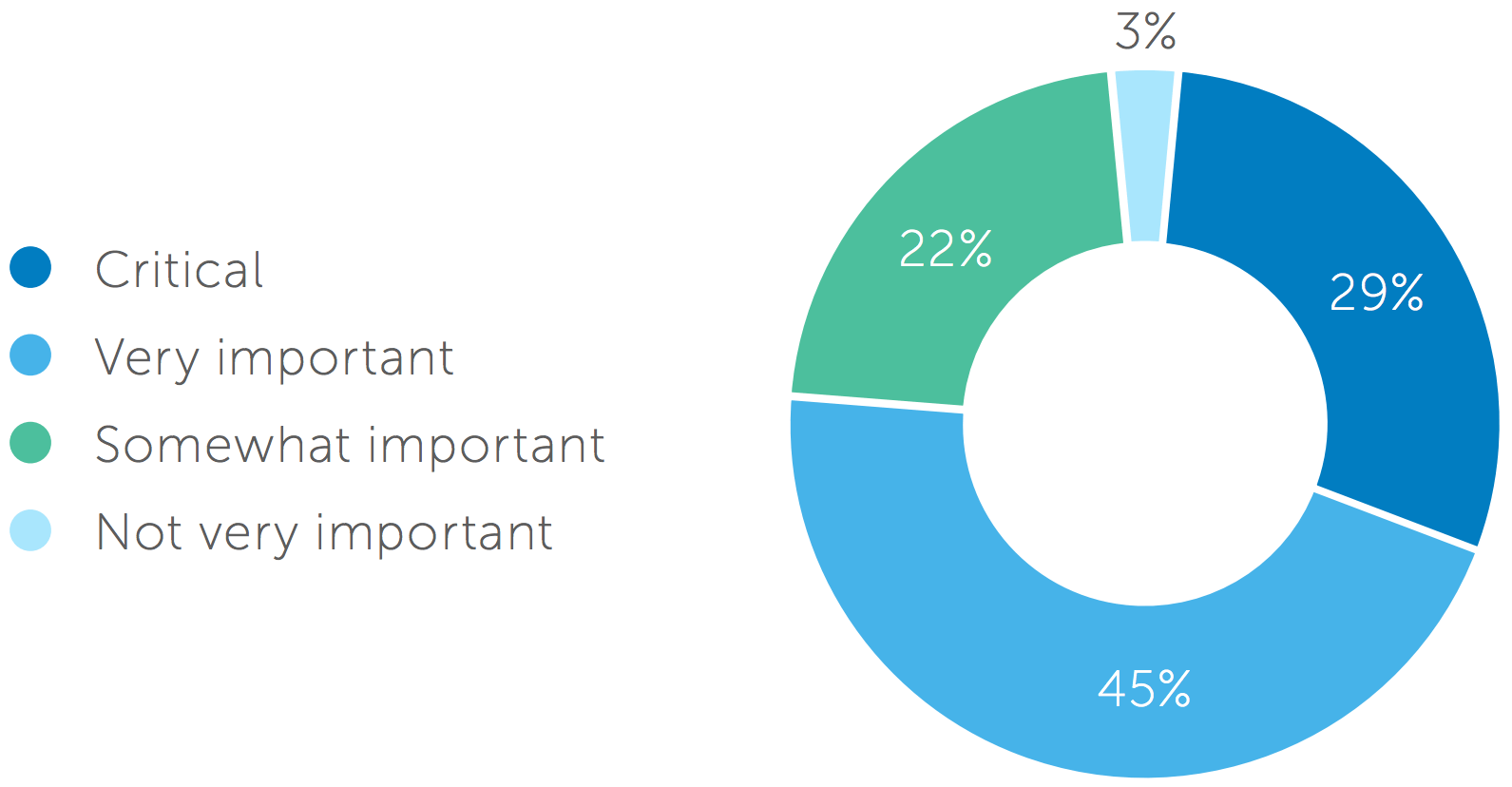
Importance of IAM in Relation to Digital Business Initiatives
The reasons become clear when you examine several examples of the role identify plays in modernization projects:
• Migrating an enterprise application to the cloud. As seen in the massive adoption of Office 365, businesses are embracing cloud-based technology for agility and simplicity. But with the proliferation of services, integration with Active Directory can be complex, causing delays and frustration.
• Moving an HR Information System (HRIS) to the cloud. Cloud-based HRIS offers myriad advantages, and integration with IAM can drive efficiency by streamlining the onboarding, offboarding and change processes.
• Building a web or mobile app. Digital offering present a tremendous opportunity to provide value to customers, but if the user experience is poor, adoption suffers. Being able to support the latest identify protocols can be a critical usability differentiator.
• Opening developer access to business systems. Interoperability and integration is key to modern business, but can open access errors. A modern identity strategy can help businesses facilitate access while remaining secure.
An Identity Strategy to Support Either Transformation Mode
Identity and Access Management strategies should be flexible enough to support either transformation mode, or a combination of the two.
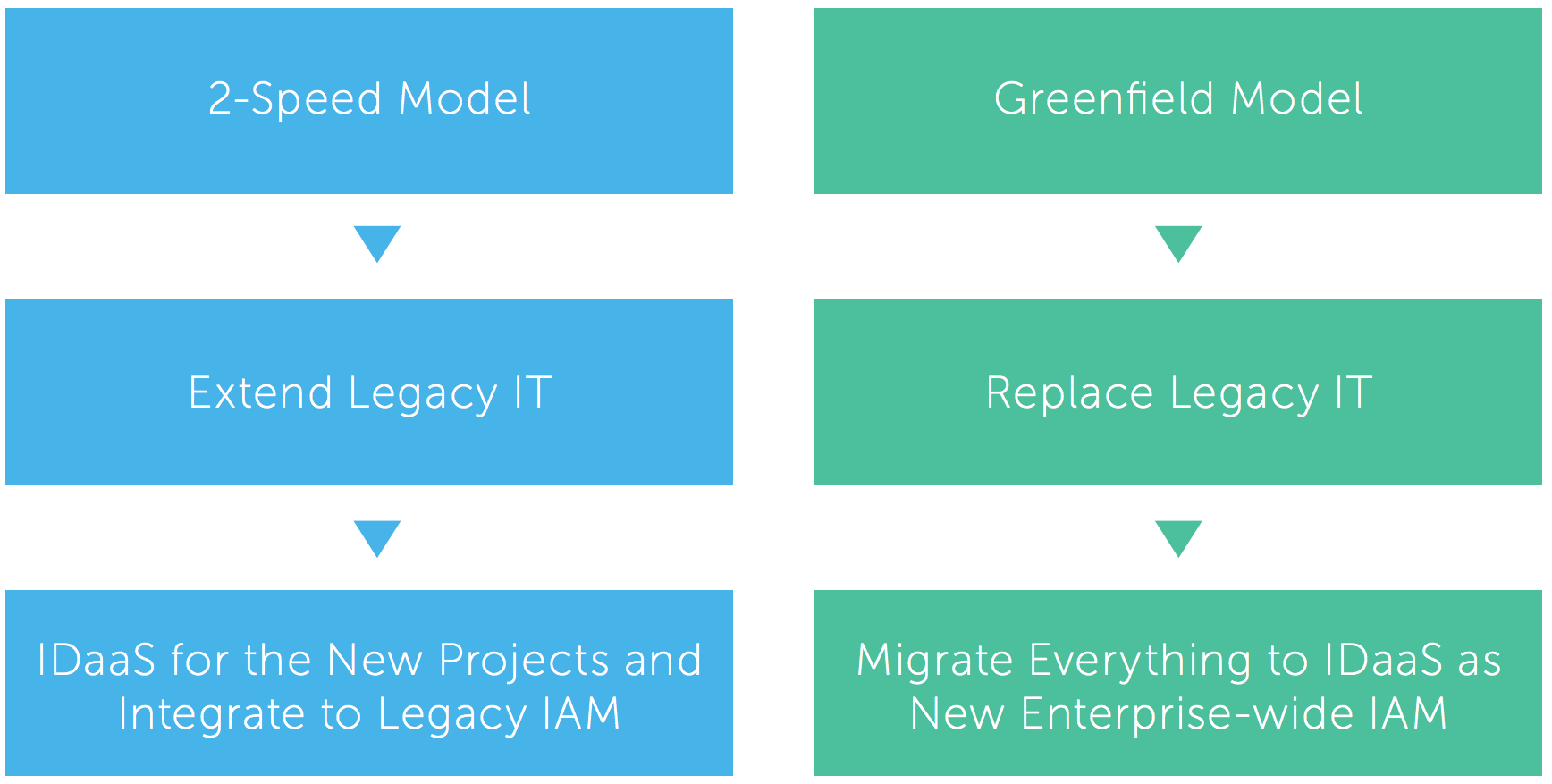
Identity as a core component of either type of modernization
Under a two speed model, the goal is often to extend legacy IT. Mission critical projects that are reserved for future change need to continue to work with legacy IAM solutions. New projects, and other projects slated for immediate change, present an opportunity to work with a modern, more flexible IAM solution. In this case, cloud-based identity as a service (IDaaS) can act as a single management console—interfacing directly with some services and through legacy IAM solutions for others.
Under a greenfield model, replacing as much legacy IT as possible is the goal. This represents the chance to treat IAM as one of those legacy applications, migrating everything to a new, cloud-based IDaaS solution. The benefits of a single interface of identity remain, without the burden of having to support legacy IAM solutions.
Under either approach, businesses will experience enhanced value across three key pillars:
1. Decreased cost and enhanced efficiency
2. Enhanced agility to add and change IT services
3. Increased ability to deliver business value
Why Okta?
Okta’s modern approach to identity management is uniquely positioned to help businesses take control of identity to modernize IT across the three pillars of value.
Decreased costs and enhanced efficiency
• A single solution for identity as a service. A single architecture and point of access means less cost and complexity architecture
• Cloud delivery means no hardware or on-premise software to maintain
• A simple administrative interface that makes administrators self-sufficient, and not reliant on customization
• Easy maintenance and automatic updates
• High availability deployment means a resilient infrastructure less prone to costly disruption
Enhanced IT Agility
• Library of preconfigured integrations means faster changes and updates
• Simple integration to a directory (e.g., multiple domains) makes it easier to maintain a complex environment
• Easily integrate with existing and future on-premise, cloud and mobile applications, as well as new services
• Integrated multi-factor authentication eases the burden of delivering enhanced security
Delivering enhanced business value
• Deploy web/mobile applications more quickly to provide enhanced customer value
• Programmatically federate with partners, or self-service registration for contractors, partners and customers to build stickier experiences
• Broad developer platform (e.g., APIs, SDKs) makes integration and for richer business context
• Faster change management lets business respond to needs in near real time
Roadmap to Success
To recap, a modern, automated approach to identity helps take control of credentials to drastically reduce the risk of a data breach. Where should organizations start?
We recommend you focus on these key milestones:
1. Deploying a cloud-based identity platform with high availability and user store
2. Achieving simple integration as new access requirements are introduced
3. Ability to deploy multi-factor authentication
4. The capability to federate with partners, or self-service registration for contractors, partners and customers
We are Here to Help
Okta provides an end-to-end suite for modern identity management. We connect with complex service infrastructures, enrich context by providing threat intelligence to deploy single sign-on, multi-factor authentication and automate lifecycle management. We do all of that by working with your existing security infrastructure to provide value.
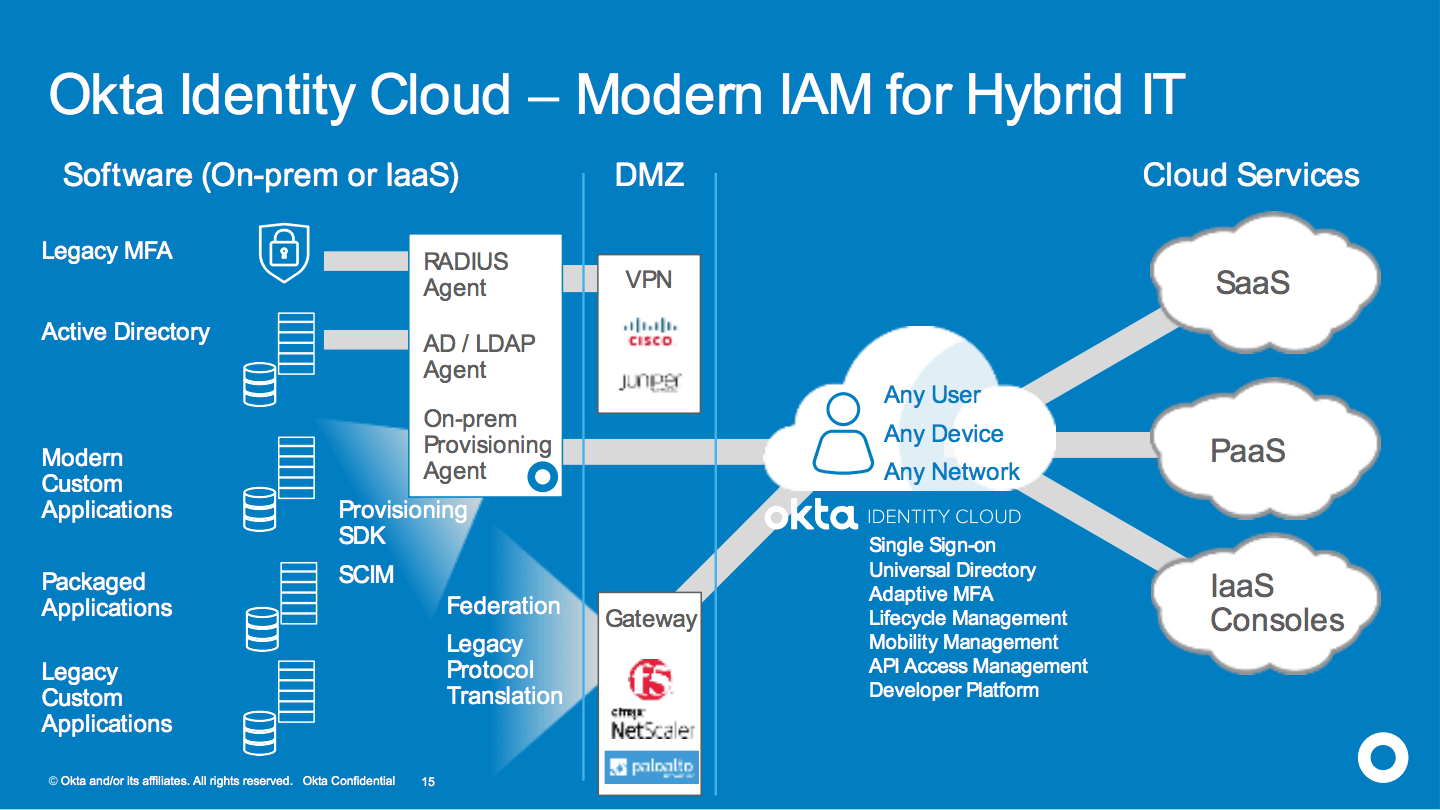
The Okta Identity Cloud Security Platform