Solution Brief: Building a 100% Cloud and Mobile IT Infrastructure
Executive Summary
Organizations wishing to adopt a 100% cloud and mobile strategy aren’t exactly sure what that looks like or how to get there. They may have some on-premises resources and are considering migrating off Active Directory. They may need to support a bring-your-own-device (BYOD) environment.
A new breed of fast growing SMBs that were “born in the cloud” and grew up with services like Google and Slack are also seeing challenges in staying 100% in the cloud as they continue to scale.
Growing organizations need to deploy new applications and services to employees across distributed geographies—who use a variety of mobile and endpoint devices. When external contractors and business partners need access to corporate applications and data, IT security becomes more complex. Organizations moving to cloud and mobile need a single source of truth for identity. This helps IT automate onboarding and offboarding of employees and partners to applications, and provides visibility into who has access to what resources. Okta enables organizations move to cloud and mobile with efficiency, accelerated growth and enhanced security.
More organizations are adopting a cloud-first strategy
Research shows the movement towards cloud is pervasive:
• 40% of surveyed orgs are looking to adopt a cloud-first strategy in next 24 months
• 60% of applications used in typical SMB org are cloud
• 30% of our customers don’t have an on-premises Active Directory or LDAP directory
Why Cloud and Mobile?
Organizations are adopting a cloud-first strategy for three main reasons:
1. They want to scale faster, deploy and adopt apps as rapidly as their company grows, and meet workforce demand for apps and data.
2. They want to reduce IT costs: by cutting the initial and ongoing investment in deploying applications on servers hosted on-premises. They want to empower employees to spend less time on help desk calls with tools like automated password reset.
3. They want to increase security. Cloud- and Mobilefirst organizations understand that their software and platforms are always up-to-date.
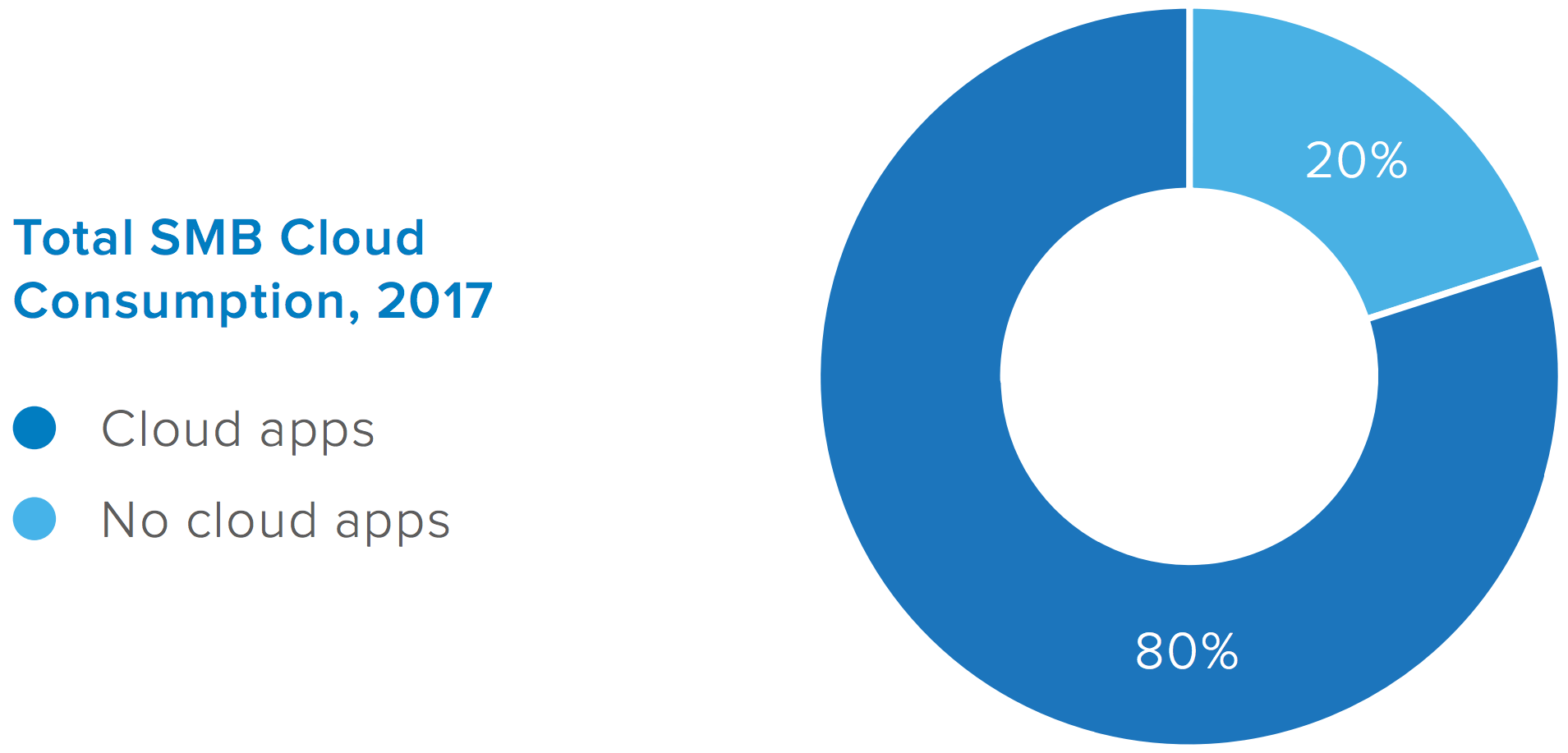
Cloud Adoption
A vision of pure cloud and mobile IT
When an organization commits to 100% cloud and mobile, what will their end-state look like?
• SaaS. Older on-premises apps have been modernized to support newer authentication protocols like SAML 2.0 and OpenID Connect, or replaced with SaaS applications. SaaS offers more flexibility, higher availability, and security than in-house applications.
• Distributed IT. Business units can choose the best tools to meet their needs. IT plays an advisory role to ensure security standards.
• Distributed Workplace. Employees in 100% cloud and mobile organizations can work from anywhere, using all the tools, applications, and data they need to be productive. These organizations also have a growing number of external contractors and partners who need access to internal resources and they don’t want to use rigid tools like a VPN.
• Security is Focused on Applications and Data. Security is no longer focused on devices and networks, but on securing access and authorization to apps and data, regardless of where or how they are being accessed. Multi-factor authentication (MFA) becomes an important security tool in these organizations.
• Mixed Mac and Windows. In a cloud and mobile world, on-premises directory limitations no longer restrict type f end point device employees use—so more IT organizations are providing Macs to their employees.
• Bring Your Own Device (BYOD). With focus now on protecting access to apps and data rather than the device, IT is comfortable with lighter management of devices in favor of more control for the end user. This is especially important for collaborating with outside contractors and partners who have their own devices.
• Automation. As the number of users, apps, and devices increase, 100% cloud and mobile IT orgs use tools to automate management of these users and apps to stay compliant, keep their environment secure, and generally make their job easier. IT is no longer the bottleneck for things like provisioning and deprovisioning users or resetting passwords.
Challenges:
While this vision paints a very concrete picture of what 100% cloud and mobile IT looks like, organizations may find some challenges in getting there.
• Insecure access to applications: Even new SaaS apps can be cumbersome to integrate and slow to deploy if end users are frustrated with managing multiple login credentials and portals. They may re-use passwords across apps, or store passwords insecurely, increasing risk of data breach.
• IT lacks centralized visibility and control of applications and users:
• IT admins have difficulty managing and securing access across all applications. Because there is no single source of truth for identity, IT lacks visibility into who has access to which applications. Granting internal credentials to external contractors and partners exacerbates the issue, and puts compliance at risk.
•Time-consuming and error-prone manual provisioning processes overwhelm IT, putting an organization at risk if terminated employees still retain access to applications and data.
• BYOD can put the organization at risk when corporate data is stored on unsecured personal devices with unknown device security posture.
Identity & Access Management is the solution
A modern, cloud-based approach to identity and access management can transform businesses to 100% cloud and mobile. Okta’s solution solves the challenges organizations face with:
Secure app access
Okta secures access to applications through integrated access management, with single sign-on to over 5,000 pre-integrated applications and Secure Web Authentication to custom apps. Okta leverages partners’ existing identity solutions to give contractors and partners secure access to apps and internal data.
Centralized visibility and control over end users and applications
Admins can manage and view application access, stats and policy from a central console. A flexible policy engine gives admins very specific control over how they manage access and authorization to resources, and enforce additional security measures like Multi-Factor Authentication.
Automation
Okta simplifies creating and removing accounts in apps through out-of-box workflows, group rules for role-based access. Integration with HR systems enables immediate deactivation of accounts when HR terminates an employee. Automated self-service eliminates password reset calls, and enables onboarding of new devices for new users.
A pure cloud and mobile environment untethers users from specific locations and specific devices. Employees want easy access to applications and data no matter where they are. Securing data with Okta means you can setup adaptive, risk-based MFA based on contextual data from the user, provide a consistent SSO experience using the Okta mobile app for iOS and Android devices, and administer users, devices and applications from a central console.
Roadmap to Success
Ready to get started? We recommend these key success criteria to help you achieve 100% cloud and mobile IT using Okta.
1. Begin by providing your users with secure and easy access to SaaS applications through single sign-on.
2. Expand this further by connecting to existing identity sources like Active Directory and other identity providers.
3. Automate provisioning to manage users’ access on Day 1 and revoke access when they leave.
4. Automate user account management and reduce the amount of ongoing IT effort and time in managing a user’s lifecycle.
5. Enable secure BYOD by repeating the same consistent and secure experience on mobile devices.
We are Here to Help
Okta delivers a modern suite of identity and access management solutions that help businesses get maximum value as they move towards a 100% cloud and mobile environment. We have helped businesses of all sizes speed up the process, empowering users with enhanced productivity and driving down security risk.
We do it by connecting everything. We help progressive organizations adopt a modern approach to identity and access that helps employees, customers and partners, of acquirers and acquires access systems more quickly efficiently and safely.