Building Digital Experiences in Healthcare
Transcript
Details
Ally Kozel: Hi everyone. I'm Ally Kozel, and I'm excited to welcome you to our Oktane Live session, Building Digital Experiences in Healthcare. This session is in lieu of our annual healthcare lunch, which narrows in on healthcare trends and security-related initiatives while providing an opportunity to network with healthcare thought leaders and subject-matter experts who are redefining the industry. With that being said, we encourage you to join the discussion and network with other attendees via the chat window, and engage with our speakers and Okta experts throughout the session via the Q&A. Without further ado, I'd like to introduce our speaker for today's session, and a true pioneer in this space, Mike Towers, Chief Security Officer for Takeda Pharmaceuticals. Mike will share his experiences transforming workforce identity for active employees and contingent workers, plus share how he plans to build a centralized externally facing identity and access management platform to support their entire ecosystem. Take it away, Mike.
Mike Towers: Thanks Ally, and thanks everybody for taking the time to join the session. These are obviously unprecedented times, and I appreciate the flexibility for everyone joining this virtually, and I look forward to walking you through the materials and sharing my experiences on this very, very exciting topic. So with that I will jump straight into my materials. As Ally mentioned, I'm the Chief Security Officer for Takeda. I've been here for about a year and a half, but I've been doing pharmaceuticals and I've been in life sciences for about 25 years, and I've been in a senior security leadership position for about 12 of those years. So it's an exciting area. It's an area that I'm passionate about, and I've been doing a lot of work specifically in the identity space, and we'll talk about a lot of that today.
Mike Towers: So today I want to talk a little bit about shifting our focus to patients, healthcare providers, and caregivers. And that will make sense as we progress through the discussion. But, this is a shift, frankly, and we'll walk through why that is, and it presents a number of interesting challenges that a lot of historical identity platforms, and identity services, and identity initiatives maybe didn't have to think about. And we'll share what Takeda is doing in this space to prepare adequately and to really, at the end of the day, make an impact on who we are all here for, at least in the life sciences space, which is our patients.
Mike Towers: So a little bit of background on Takeda, for those of you who may not know. Takeda is now a top 10 pharmaceutical company. We recently acquired a company called Shire, which vaulted us into that position. We're one of the oldest, if not the oldest pharmaceutical company in the world. We were founded about the same week that the US Constitution was written. So there was a gentleman that was selling Chinese herbs in Osaka, Japan. His name was Takeda and that was a little under 240 years ago. And now we've grown into a pretty large enterprise, predominantly focusing on a handful of key therapeutic areas, as you can see on the slide. We are global. We're in about 110 countries. We operate primarily out of three main, I would say, regional and global headquarters. One is Tokyo, where the corporation is headquartered. A second is Boston, which is where our US headquarters is and where I sit. And then we also have a European headquarters in Zurich.
Mike Towers: We are a very, very values-driven company, and we do take patient experiences and patient benefit as the top and number one priority for the company. And that will become obvious when we talk a little bit about our extension shortly. So let's dive a little bit into some of the materials that, frankly, I'm going to transparently share with you, that we use internally to help facilitate and move forward on this journey. So, the first thing I'm showing you here is basically a slide I use with a lot of internal senior stakeholders about the concept of exposure. And I think many of us who are in the security business and have been doing security for a long time realize that security, frankly, isn't just about cool new technology (although there is a lot of that), but security is mainly in the business of mitigating risk. That, at a high level, is what we do. And in some of the areas where we need to mitigate the risk, we try to put controls in place.
Mike Towers: Most of you probably are aware of this, and I know I'm probably preaching to the converted, but in essence we take risks every day. We take risks when we get in the car and we drive somewhere. We take risks when we cross a busy street, but there are controls that are in place to help us manage and mitigate that risk, whether it's a seatbelt in the car, whether it's a light at a crosswalk, and the same applies for a massive corporation like Takeda. And we define exposure as where we think we have the most significant risk and potentially where our controls, we don't believe, are suitable enough or adequate enough to really mitigate that risk. So as you can see, again, sharing transparently where we believe we have most of our exposure, and some of our biggest areas of exposure, and for a large life sciences company and pharmaceutical company, this likely is very unique when you think about our manufacturing plants, our third parties, et cetera. But I want to point some attention to our externally facing presence for a minute, because that one will resonate.
Mike Towers: But externally facing presence, in essence, is what we define as how we look outside the company. So that could be internet presence, it could be our presence to all of our external stakeholders, and again, the primary stakeholders in the world of healthcare are, quite simply, the patients and the healthcare practitioners that take care of them. And you move down a little bit and basically again, from a macro process perspective, you can almost argue that those boxes in the middle are the security machine, if you will. That's basically the machine of my department. And in essence we have three fundamental inputs to that machine. One is the exposure that I mentioned, that's basically just a current or a somewhat recent picture of how the company is currently constituted. And then in essence, again, the spirit of this diagram is to be somewhat simple.
Mike Towers: Beyond what the company is doing and what the company looks like right now, we have two other inputs. We have the external threats and, as we all know, they change multiple times a day and move very, very rapidly in this space. And then we have what we want to do from a business-growth perspective. So those three inputs collectively go into the security machine, and you see some areas that, frankly, we probably ... Well, I'm pretty confident we all do similar things, we may call them different things, but we have a handful of elements that we use to manage how we mitigate those risks and how we protect the company. And again, I'll call specific attention now to the identity pillar. We believe identity is an important enough area that it warrants its own pillar.
Mike Towers: And I think we would all agree that some of the other areas and elements that we historically would use to make decisions about security, things like your device, things like where you are in the network, things like what type of network you're on, all of those are becoming very, very difficult, if not impossible to predict, and they're highly variable. So they're really, really difficult to make decisions on. They're really difficult to establish patterns for. So identity, in essence, is becoming one of the fundamental cornerstones for how you make decisions, because no matter where you are, what you do, how you connect, the one constant is that you are an individual, you have an identity, you have the ability to prove who you are, and you likely have a role in that relationship. So that, in essence, becomes one of the fundamental backbones of how you can make security decisions: your identity, which is fundamental to what we're going to talk about here.
Mike Towers: So, I'm going to walk you through some of the journey a little bit here, and then some of the transitional elements that I talked about. So, first and foremost, I believe that anybody who's in a security-practitioner or an identity-practitioner role should start with the basics. And by the basics, identity again, and identity access management overall, is a large enough and, in some respects, a complex enough area that I would recommend, especially for large companies, that you publish and agree on a taxonomy, and you publish and agree on your definitions. They don't have to be exactly the same, I think we all may have our own opinions on what they are, but it's important that you speak the same language internally. Make sure, for example, that your stakeholders understand the difference between identity and account. Make sure your stakeholders understand the difference between authentication and entitlements, so that when you speak to these, and again, identity being important enough that these terms, frankly, should apply and be referenceable so people know what you mean when you speak to them.
Mike Towers: And it's important, again, the wider the stakeholder group is, the more important it is to make sure you have a common set of definitions. So this may sound basic. I tease a lot of people, a lot of people that know me know that I used to be a journalist, I used to be a writer, so I get hung up on words. But it is important, in my opinion, to set a baseline, and start simple and know what your common taxonomy and some of the definitions of the terms are. So these are the ones that we use internally.
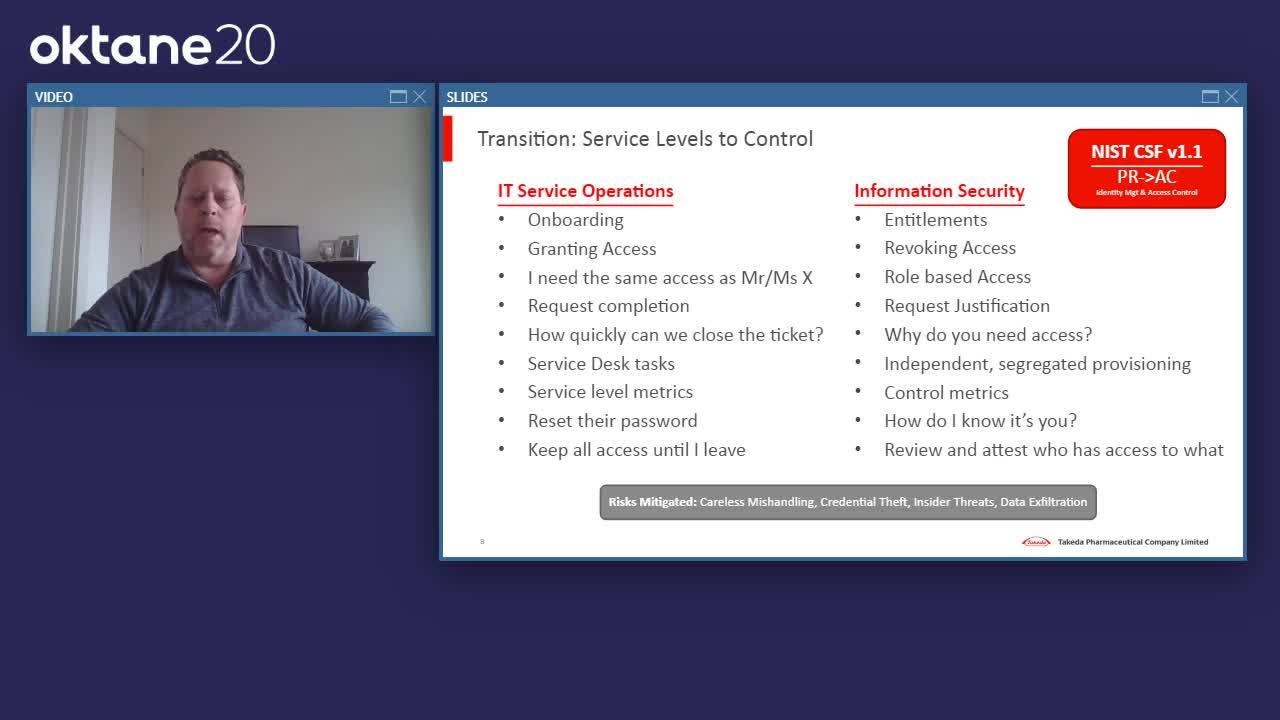
Mike Towers: And then the other element here I'll talk through is: How is identity managed and/or provisioned within your organization? So what has, frankly, become quite a popular, and sometimes contentious, decision within many companies, large or small, is: What is identity management? Is it a service or is it a control? Now, at the end of the day, if you do it well, it should be both. However, there are some fundamental decisions, and I think fundamental mindset differences, that have to come into account when you think about what the best way is to provision and manage identity- and access-management capabilities within your organizations. I'm going to build this side [of the slide] a little bit to strengthen my point. So what I'm saying here, bottom line, is that if you run identity as an IT service, in my opinion, you're not doing it optimally. Most companies can, and some, frankly, have made this transition, but for those who haven't, I strongly encourage you to do so.
Mike Towers: Identity and access management is a security control, fundamentally speaking. It's not an IT service. These are not servers, they're not networks. It's not your help desk. Of course, it's important that we do this quickly, efficiently, cost-effectively, consistently, but the fundamental motivation for identity and access management should not be surface levels, it should be control. And the reason why I point this out is that there are many, many mistakes, and sometimes many inefficiencies that happen, and, frankly, could lead to breaches where you'll have legal responsibility to disclose or manage them with those that are impacted, because people who are motivated by service levels are making control decisions. It's not a criticism, they both have their place, but the fundamental mindset of IT service operations and the fundamental mindset of a good security group are very different.
Mike Towers: And the way identity is moving, I have a reference there, as you can see, to NIST (the National Institute of Standards & Technology), the Cybersecurity Framework, just as a reference point, frankly, and corroboration that it is identified within the cybersecurity framework and many others as a critical security control, and I recommend that you operate it as such. Again, we're walking through a journey here about some of the basics, and some of you probably already do so, but you'll start to see a couple of these examples on this slide of why it's so different. What are those types of things that an IT person thinks of? And what are the types of discussions they have? One of the common traps is that people call the help desk or call the service desk and say, "I want the same access as the person sitting next to me." Or you may be really, really angry or upset because something doesn't work. So you talk, and you, in some respects, bully that IT service person into giving you that access. And they're so motivated historically, and, frankly, appropriately, they're so motivated by service levels, turnaround time, and granting access that they don't think about the control elements.
Mike Towers: Moving into the security group or security function, and, frankly, I don't care where it is organizationally, it just has to be different from your IT service group. And they are thinking differently: not about how badly you are yelling about it, but about whether or not you need it. What's your justification, what role are you in, et cetera? So, regarding all of these questions, I think differently. The fundamental point of this slide is that IT service is motivated by service levels, security is motivated by mitigating risk, and the provisioning and management of identity belongs on the right-hand side.
Mike Towers: Then you get into some conceptual architecture, and we're starting here, specifically and initially, on what it means to do identity for the workforce. And by workforce, I mean your employees and your contingent ... almost like employees. Now there are legal reasons why your contingent workers shouldn't be treated like employees, but we all have contractors that sit with our employees and work very, very similarly. And what you see in the architecture here, and what you see are some concepts that we've developed; and again, none of this should be a surprise to many people, some of the key components and how they fit together. Again, this is what we've used. You may want to do something slightly differently, but I think some of the key principles should apply, and I recommend you make sure that they are appropriately reflected somewhere in your model.
Mike Towers: So identity governance: translating who you are as an individual into the digital accounts that you need. And then how many accounts do you have? Again, it's important to understand the difference between identity and an account. Behind the scenes, each individual may have 10, 20, 30, 50 accounts across the various systems or platforms that need it. And then you get into a lot of the pillars that identity is working on, on a day-to-day basis, and that your IAM team is likely focused on. Access control. Accounts and credentials. What are the target systems that folks need access to? Are there external directors they need to federate to? And then, all of that is built on a platform that requires audit and ongoing review. So these are some fundamental principles that we've applied. Again, this is just sharing what I've done and what we've done within Takeda to help manage this.
Mike Towers: And again, on the right [side of the slide], you see some principles that we've applied. I won't read them all to you, but a couple of highlights. HR should own the system of record of employees. It's not something IT or security should own; you should depend on HR for that. And I believe that you should have a one-stop shop for application and access provisioning. It should be separated from other groups, so you have that segregation and that additional extra focus. And I believe that a lot of this should be cloud-based so that you can extend and can be consistent between your workforce and your external ecosystem, and we'll talk about that more in a few minutes.
Mike Towers: Okay. So when we think about the identity and access management platform, the first area, as we mentioned, is your workforce. And I define the workforce as your employees and your contingent workers. Contingent workers aren't officially employees, but they're contractors. Some folks call them contractors. They're folks that basically come in and work like an employee, maybe they sit in an office or a cubicle nearby, but they're legally different. But in many respects, they get the same accounts, so they should be treated as similarly as employees as possible from an identity perspective, even though they do have a legal requirement to be treated differently. I'm a big proponent of a centralized identity management group and a function that handles everything from account governance, to authentication, to use provisioning. I also believe that the cloud should be used as best as possible, given the scalability and speed requirements, and the flexibility requirements.
Mike Towers: Synchronizing attributes is very, very important, and you'd be amazed how many people respond or react if they think their title is different, or the department's wrong, or maybe their location is wrong. When that gets synchronized around the various platforms and people notice it, they react. So it's important that you have a good data synchronization between the various components. Centralizing a workforce and a workflow for requesting access, and doing major changes like lifecycle changes, moving, onboarding, replication, et cetera, I propose centralizing that as best as possible, even in a larger organization. Having one group that thinks about this day-in and day-out is a strong discipline.
Mike Towers: And then I would propose making sure that the various directories and the various, frankly, components are in their appropriate place. For example, Active Directory. (I'm sure all of us run Active Directory, or many of us do.) Active Directory is a resource directory. It basically only exists because the Microsoft environment requires it, in my experience, and I would downgrade it to a resource directory. If you have a tool like Okta, or something like Okta that's above it and manages your identities overall, your identity platform should be different, and should master your AD environment.
Mike Towers: And then last, but certainly not least, I would recommend out-of-the-box connectors wherever possible. A lot of experience here, with both peers and my own personal experience, that the more you customize this stuff, the more trouble you'll get into. Things will break. Someone has to look after it. I know those are pretty principled things, but in identity, it's a really, really critical component to understand, that out-of-the-box connectors are important, basically because the environment changes so frequently that you have to make sure that those connections are still stable when you do make those changes.
Mike Towers: So here's where we made the pivot and the transition. We've talked a lot about the workforce. So what we want to do now, and what Takeda is doing looking forward, is that we're building a centralized externally facing platform to support the entire ecosystem, not just the workforce. And when I say “entire ecosystem,” what do I mean? In life sciences, I mean, quite simply, the lifeblood of our industry, frankly, and the important part of our industry: patients and our healthcare practitioners. So how do we do that? A lot of it's going to be based on external federation and authorization based on trust. You're going to have to focus quite a bit on leveraging industry partners. It doesn't make any sense for a company to do their own identity proofing, for example, for each and every type and part of the ecosystem. There are companies and there are services better suited to do that. You want to potentially leverage third-party credentialing where you can, and focus your own effort on what you think is differentiating for your company, whether it's authorization, which is primarily a big one; but let the more commodity stuff be done by third parties.
Mike Towers: And last, but certainly not least, is that this whole external ecosystem has to be built for scale. So most of us that do some type of business where you have an external component, the scale of external is likely going to be much, much larger than your internal... Let's take Takeda's example: 70,000 internal workers. That's a large number, and of course they're important, but are they as important as the millions of patients that we serve, or the roughly 2 million HCPs (healthcare professionals) that we serve? I think, at a macro level, probably not. But, historically, we've spent so much time making sure that our internal workers are happy, and of course they are, but we have to challenge ourselves to think bigger.
Mike Towers: What you see on this slide are some references to some partners that we've worked with, and some other pharmaceutical companies that are leading the way here. But what this basically means is that you want to focus on trust: you want to make trust-based decisions. And then you also want to think about the different categories and roles that comprise the ecosystem, and leverage third parties, and leverage industry standards. In our area, that would be things like SAFE-BioPharma. Exostar is a very good resource in this space to leverage, to help with clinical trials. But look at the table on the right and you start to think about the various personas that may exist. Healthcare practitioner, in essence, is a doctor, or maybe a certified nurse, but they can behave in multiple personas. They can prescribe medicine, they can be a clinician or an investigator, they can be a key opinion leader, they can be some sort of treatment specialist. So all of these various personas need to be reflected in your ecosystem.
Mike Towers: Then I've highlighted a few principles, considerations, there to consider. I mean, obviously, we're all used to training our workforce. You can't really train in the external world as much as you'd like, or that we all used to. I mentioned federation already. A trusted digital experience is important, so you want to make sure you have as consistent and as single an identity as you can. And I think the other area that I would point out that's a key one is: try not to be an IT service provider for your partners. Most of us are working with large-scale partners (whether it's the Big Four, whether it's a large outsourcing partner), and I'm pretty sure they have their own email system, and their own laptops, and their own Office environments. Why do we continue to provide that to our third parties when they can leverage their own? So, focusing on federation and interfacing is an important element to keep in mind.
Mike Towers: Little bit of levity here, but I often say that the one big word here that I like to focus on, is what somebody like Jimi Hendrix and Marriott have in common. And the bottom line here, the common denominator across these two seemingly very different things, is the experience. The trusted digital experience that Marriott is trying to provide their customers, for example, across their hotel chains is very, very similar, conceptually, to the type of visual experience that healthcare and life sciences are trying to manage and to build. So, I know it may not be the same level of social impact, when you're talking about hotels and hospitality versus healthcare, but there are a lot of lessons to be learned.
Mike Towers: Pharmaceuticals and life sciences, historically, rarely, if ever, dealt directly with patients. They always just dealt with doctors. Well, now we're moving into a world where the entire industry is more health-management based. Ongoing management of people's disease conditions, their symptoms. How are they feeling? How is it changing? Having direct access between the patients and the entity that makes the treatments is becoming really, really important. And that's all based on an experience-type of element that, historically, we may not have thought about.
Mike Towers: So, I mentioned Takeda is a very, very values-driven company. And our first three words in our value credo, and the order is important, are patient, trust, and reputation. So trust and reputation are huge components in determining what your overall experience is. So what's our goal here? Our goal is to build a trusted digital relationship between Takeda and our doctors and our patients. We want to make sure that that's trusted, so people can feel comfortable coming to us and engaging with us. Sometimes trusted and secure are used interchangeably, but I think, from a personal impact perspective, that they're slightly different; but it's important that we focus and make sure that this is a trusted experience.
Mike Towers: In a company the size of Takeda, it's important to note that this has probably been something that's been tried by many business units or many functions. There's probably 10, 20, 50, 100, depending on the size of your company, external websites that are potentially going after the same people. We actually had some pretty relevant, and interesting, and pointed feedbacks from some of our patients and some of our doctors who look after different therapeutic areas and who were very frustrated by what looked like a very disjointed experience. So, we want to make sure that it's not only trusted, but it's also consistent. And that's our goal: to build a consistent digital identity that, in some respects, may mimic some of the stuff that our patients are used to in the consumer world, and we want to make sure that we bring that type of experience into their healthcare experiences as well.
Mike Towers: So in order to do that, you have to leverage a lot of the consumer IAM principles, and there's obviously some diagrams here that walk through how we've built it. I won't spend a lot of time on it here, but I think it's important to note that, in the consumer world, there are a lot of lessons that we can learn when we're dealing with patients. And from a development-focused perspective, you're likely going to start thinking about things like APIs and microservices, some of the stuff that historically you didn't build, or you may not have needed to build when you're thinking about patients and HCPs. So it all links together with some of the identity principles that we're building as well.
Mike Towers: And it's not just about reaching out to patients directly, although it's very important. The doctors and the physicians are an important element of this as well. And one example of that is in the clinical trial space. So clinical trials: you have multiple systems, you have multiple companies, but you only have a finite number of doctors and clinicians who are doing this type of testing. There's a really, really famous picture that used to go around of a clinical investigator who would walk through an airport with 12 laptops, one of which he got from some of the major pharmaceutical companies to do his or her clinical testing. And that's just something that, frankly, can't apply anymore. We have to do a better job of working at this on an industry level. So, again, it's something else, that externally facing and ecosystem-focused thinking for identity is really, really important. And again, it's not an endorsement of a specific company. Exostar is very, very key here, but there are others.
Mike Towers: But it's just an essence of trying to get companies to focus where they should, i.e. authorization, and let someone else focus on the identity and the proofing as necessary that we can all rally around and using standards to sell. This is a direct screenshot from some of the presentations we've used internally about how this looks. So, we are building a complete new technology backbone for how we're dealing with the digital world, and that could be devices, it could be mobile apps, it could be complementary therapeutics, it could be wearables that we're using to get real-time and real-world evidence from our patients directly. All of that needs to be consistent from a backend perspective, but may require some flexibility on the front end. So, just as important as, say, who your cloud partner is, or how you store the data, or how you do API security, it's just as equally as important as how you manage the identities. And we've built this platform to make the identity environment one of the critical parts of the ecosystem.
Mike Towers: Okay, so this slide outlines how we believe, and we've built, Takeda ID, and what we're branding Takeda Digital ID to be a fundamental part of our technology backbone. As important as the data, as important as the APIs, as important as our microservices, identity being a critical enough component that can be shared across a number of parts of our business value chain, whether it's R&D, whether it's how we deal with our HCPs from a commercial prescription perspective, whether it's the payers, whether it's how we use IOT for wearables and getting direct access to data from patients, all of that can fundamentally rely and depend on a common ID that can be shared across multiple parts of this, and across multiple geographies, multiple business units. And people don't have to worry about designing or having their own separate identity system, because it's built into the backbone. We can assure our various application developers and the various parts of our business that we have the ID and the identity piece taken care of. And again, the goal being to give every patient and every doctor one single ID to be leveraged across multiple functions.
Mike Towers: And as you can see in the top right, scale is a very, very big challenge here. It has to support a lot of users, it has to be very performant, and support many, many more users than we're probably used to supporting in our workforce environments. A little bit getting more to the future here is: What do we think the next steps are? Well, the next steps for us are, we believe strongly, that identity is one of those areas where we can improve security and improve the user experience. Oftentimes, the security practitioners were in a balance of trying to figure out where on that range things should be. If it's really, really easy to do, likely it's not very secure. Or vice versa. If we want to make it really, really secure, sometimes it's viewed as very, very difficult. So this is an area where we think that we can do both: we can have a better user experience and improve security. How do we do that? We do that with models and math.
Mike Towers: So this, in essence, is a series of representations that we're using to get into a concept of risk-based authentication. Some folks may call this behavioral authentication, but making sure that we have and can take multiple factors in, whether there's a number of partners that are working on this, a number of smallish companies that are working on some great technology here. We know Okta, being standards-based, will support them, and we've experimented with some of them already, but having, and gathering, and doing analytics on various parts of the authentication experience, building a picture of normalcy, and therefore only prompting or asking for new credentials or updated credentials when folks go outside some range of normalcy. So, it improves the experience and allows us to move on to the next generation of authentication capabilities within the same platform. And as I mentioned before, because we're building it on one platform, we can make these improvements consistently.
Mike Towers: And last but certainly not least, why are we doing this? Because again, we have a pretty important social responsibility to help the patient experience as best as we can, and the HCP experience. Those of us who have family or friends that have been dealing with a challenging medical situation, and everything, obviously, that we're going through now with COVID, I'm sure we can relate to that, the last thing you want to worry about is whether or not you have to worry about some various passwords or multiple passwords. We want to make sure that trusted digital experiences are there that people can depend on, frankly, without thinking about them too much, and they can focus on getting their condition treated, and their loved ones are taken care of within our industry. So with that, I'm going to hand back over to Ally, who will take us into a close and transition to the next session.
Ally Kozel: Thanks Mike for sharing your story with us. We encourage you all to continue the conversation via the chat and Q&A windows, but also don't forget to stick around for the rest of Oktane Live day two. We have a jam-packed agenda and some awesome sessions coming up later today, including two Okta-led roadmap sessions, and our jam-packed closing keynote with Okta's Chief Product Officer, Diya Jolly, and two guest speakers: former secretary of state Colin Powell and Amy Poehler. Thank you for joining.
Historically, biopharmaceutical companies have had little to no direct interaction with patients. With industry trends demanding more ongoing health management, optimizing the patient’s digital experience is fast becoming a fundamental requirement. Identity is a core backbone upon which to build and enable these digital experiences, and Takeda’s values of patient, trust and reputation make this a critically important pillar of our strategy.