Defining Modern Identity and Access Management
Transcript
Details
Eric Karlinsky: Thank you Ryan for that introduction. Thank you for also jinxing my demo. That'll be fun. Can't wait for that. So I'm Eric Karlinsky. I'm on the tech marketing team for our identity corp. products. And what I want to talk about today is what does modern identity and access management mean. We talk a lot about identity, but I want to actually define it to kind of set the stage for the rest of the conversations for today. Before I do that though, I think it's important to kind of talk about the definition of IT because I think it's changing. I mean how many people in the audience are on the IT team? Many. Probably most I would say. So a lot of IT professionals out there.
And I think ... I hope that you would agree that the role is changing. Because technology is taking on an ever expanding in every organization. It's touching all different parts of the business. So ... And I talk to customers about what that means for the value of IT. It's changing. IT is no longer standing up servers, managing infrastructure. At least not solely. IT is really looked at as technologists. Technology experts. I've asked directors of IT, "When you hire people for IT positions, what do you look for? What skillsets are you looking for?" And more and more often I'm getting an answer ... The answer I'm getting there's a consultative or a strategic aspect to their skillset they're looking for. So IT's really being relied on to be subject matter experts for technology in your organization.
So we tried to get to the root of this. And we dug into this. And what we came up with for a definition for modern IT is this. Modern IT is about enabling secure digital experiences. Secure digital experiences. If I asked everyone to raise their hand who was on the security team, a lot of those same hands would probably stay up. And the reason for that is because IT ... Security's all about technology. So what does it mean to enable ... Secure digital experiences. Excuse me. We see it as a problem across multiple constituencies. So let's talk first about employees.
Employees have always been the constituents of IT, right? And to summarize their needs they need seamless access, on any device, to all the technology they need to do their jobs. Right? Classic IT use case. There's also partner use cases. We talked about B to B already today. Your partners generally just want to more tightly collaborate with you. They want to do business with you faster and better. And you want that too. It's important. Strategic. Customers. A secure digital experience for your customer has really high requirements around the experience. The experience has to be delightful or your customers are going to go flee to your competitors. Right? And even if you're not a company that has a technology product per se, everyone has customers and there's a technological component about the delivery of that.
So how do you delight across all touchpoints with your customers? Make that a seamless, pleasant kind of interface between you and your customers? And the last constituency I'll mention is developers. These are like the hackers of IT. Right? If you give them the right tools, expose the right APIs, and give them access to the right data, they're going to blow your mind. They're going to innovate, they're going to create integrations you never thought possible. And developers are really ... They kind of ... We associate them with building web apps or external products, but they're turning their eye inwards and how they can accelerate the business with the technology tools. So how do you empower them to securely consume APIs?
Let's talk about some examples of some these experiences. We'll start with employees. So one example we see is employee choice. This is a use case that's very common for Okta prospects or customers and people we talk to. "How do I enable my employees to choose what device they want to work from, and what tools, technology tools, applications, resources, whatever they need to do their job? I'm IT. That's not my expertise. I don't know how to do sales," or "I don't know how to do marketing. You know what tools are best. You know how to be productive. How do I empower to make those choices for yourself?" Another use case we see is employee portals. This is a single place to go for access to everything. Right? And we think about this in terms of single sign on, but it's a single webpage or web interface you can go to to get one click access to all of your applications.
Tech autonomy. This one that a lot of our customers, we have a customer called Broadcom, which many of you may know, and they grow by acquisition. So they're buying new companies and they need to onboard those organizations. The traditional way to do that is to kind of just copy wherever those identities reside and redo all that work during onboarding. But how do you ... Broadcom's taking a different approach. They've actually empowered those businesses to be autonomous. And we've some other customers do the same thing with different business units. So marketing, and engineering, and IT, and different groups within the organization make their own tech choices, but still maintain a semblance of centralized control and visibility. So that's another use case we see for employees. And the last one, and this is really not a specific use case, but a broad use case, but you got to secure it all. Right? It's one thing for it to be seamless access, but if it's not secure, you're putting your business at risk. And we've seen the breaches tell those stories over and over again about the amount of risk you could be exposed to.
So that's on the employee side. What about partners? Nobody works in a box, right? Everyone, every organization depends on some other organization to do business. So how do you make that a better experience? Well some use cases we see there are just generally B to B collaboration. Right? "How do I expose my internal resources to my partners in a seamless way." Similarly to employee portals, we see a lot of partner portals. Same idea. You got one page to go to, maybe it's like a SharePoint page. Maybe it's a custom web application. Maybe it's an Okta dashboard. But that's one the place that partners go to to get access to everything they need to do business with you. Sales support is another one we see a lot. And Okta actually embodies this experience. Excuse me. Because we have distributors, resellers, partners that will sell Okta and they will do implementations, and they will do support, and that's really valuable to Okta as a business.
But we have to empower them to do that by sharing resources and giving them the context they need and also the assets and resources, and give them access to applications in some cases. So supporting ... Post sales support. And then the last one I'll talk about, and you can kind of go on and on about partner experiences, but the last one I'll talk about today is contractor management. Many of us are outsourcing a lot of what IT does today. Right? In different pockets, in different areas of the organization. We're either outsourcing it to save cost, or we're outsourcing to those that are better at certain areas of expertise than our company. Outsourcing things that are not our core business. And you have to manage those users that you're actually interacting with. These contractors. And they have a different life cycle.
They're time bound, and they're not necessarily going to go in your active directory because you don't have that level of trust. There's not the same vetting procedures. So you need to manage them differently when they're contractors. So that's another use case we see a lot. And the last category use case I'll talk about is the customer experience. I think these are really interesting again because the standard for the quality or the delightfulness of the experience are much higher with customers. It's very competitive. So one use case we see here is customer support. Again, even if you don't have the technology product, you have to support your customers in some way, right? So how do you do that? And there's usually a technological component. Mobile banking is a great, specific example. Banking is about managing money. It's not a technology industry. That said, it requires technology to get that service into their customers hands through mobile apps and web applications. So mobile banking is a great example of a technological use case for a non-technical industry.
Citizen services. We have a customer ... FCC is a customer, and small constrained budget organization. They have internal use cases around Okta. But then on the other side they have external use cases. And when they expose a service to their customers, that's 300 million citizens that they need to expose that to. How do you scale? Right? You're a small organization. You have 300 million constituents out there. How do provide that scalable experience and high quality experience at that? And the last one I'll talk about here, and Freddy actually already alluded to it in his talk ... We have a customer called MGM that embodies this. And it's a loyalty program. Right? So you have multiple properties and you want a cohesive experience to kind of manage that customer's, and understand how that customer's interacting with different aspects of your business. So having that cohesive view.
So these are all a bunch of examples of use cases that IT has really been called to task to help out with because they all have technological components. And I'll steal Sandeep's analogy here, because I think there's a single common thread that ties all these together. And I would argue that it's identity. So my point here is that identity connects all these experiences. If you're looking for something that's common ground across all these experiences, I'd wager it's identity. Or at least that's a component of it. That's what we believe at Okta and that's why we provide an identity and access management service. So Freddy talked about our products. And I'm not going to go into them in detail here, but we provide a suite ... A cohesive, comprehensive suite of identity and access management products meant to address just these use cases and just these needs with customers.
So it includes a directory. Our universal directory. Single sign on for a seamless experience. Life cycle management to manage different user types, contractors, employees, partners, customers. Adaptive [inaudible 00:09:51] to improve security. Mobility management to extend that experience to any device. And API access management to empower your developers. And on top of that, it's all powered by our OAN, which is a catalog of over 5,000 applications that you integrate into Okta. No one logs into Okta just to sit there and look at it. Right? You're logging in to get access to whatever Okta's protecting. It's all about the applications and the integrations, and that's the power of the OAN.
So we offer a complete integrated solution. I'm going to get to the demo in a second. But before I do, I want to talk about kind of what you're going to see today. There's going to be several demos and I kind of want to walk you through what you're going to ... We're going to kind of cover all of these products. The first demo that I'm going to do is really a high level intro to Okta. And it looks like this. It's managing users and groups in Okta. I'm pulling in users from a directory that already exists because a vast majority of our customers already had some kind of directory. And I'm enabling access to web applications, or SAAS based applications. So with that I'm going to jump over to the computer and go to the demo.
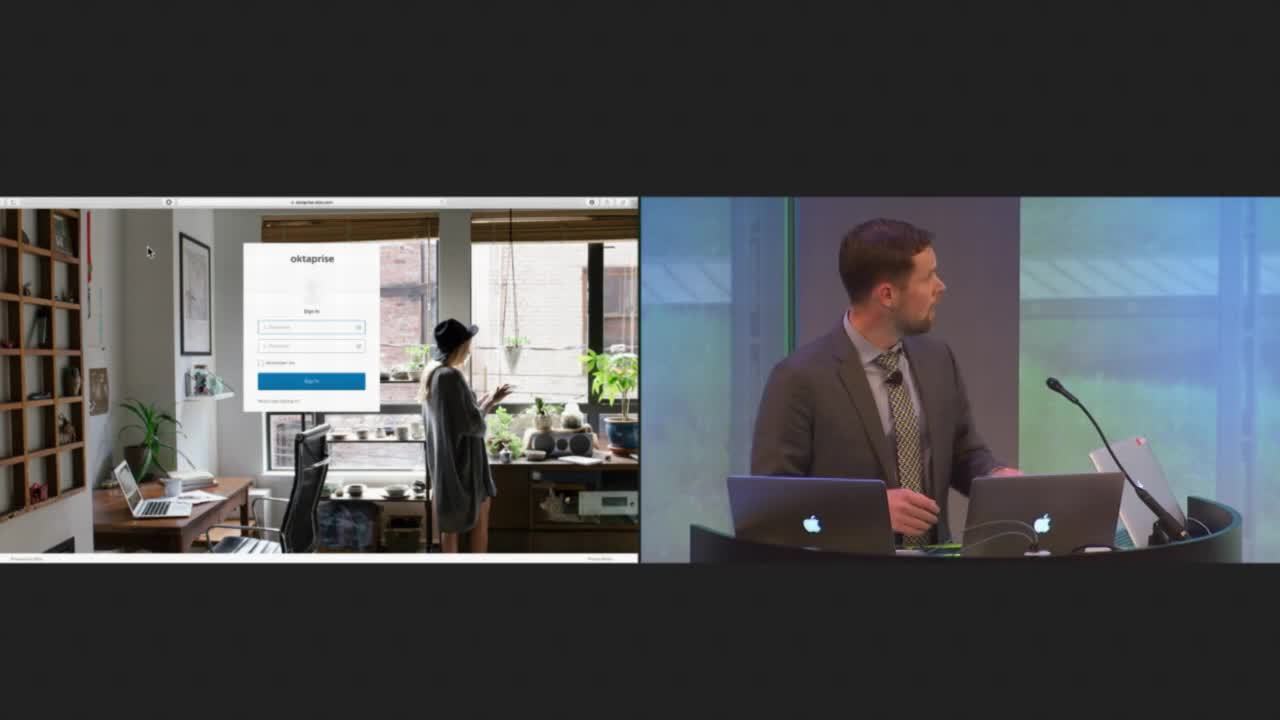
All right. So I'm logging into Okta. I enter my username password. I login to Okta and I have access. Mind blowing, right? I logged into a webpage. Okay, but there's a lot more going on here. So I'll try ... This is a simple experience, but I want to call out some details that we've invested in. First what does this do? It gives me access to applications that are integrated here. Single sign on, seamless access. So let me click on a couple of these just so you can get a sense of how this works. Click on this one as well. So I click on Box. It logged me into Box. I'm logged into my user account. I never typed in any password. Not only that, there isn't a password. It's a based on a standard called SAML, and it does essentially PKI based authentication on the user's behalf.
This is I'm logging into AWS. I have two roles here. I'm just choosing which one I'm going to log into. But again, single sign on access. Granular access, but also no password, right? Same concept. And this is actually an on premises application. It's hosted in AWS. It's a custom application. Little cheesy maybe, but this just shows how a custom application can leverage the same standards. I'm logged in as my account and here's some information about my session. So that's what this portal does. Very simple form the end user perspective. And really this is about 90% of the end user's interaction with Okta. Most of the magic is what happens behind the curtains, which we'll get to.
We early invested in this experience because end users are not necessarily technologically savvy. So we did things like ... Some of our customers have hundreds of applications here. So even though you can customize these, drag them around, create your own tabs, even add your personal applications, it can really start to be a lot of applications here. So you can actually search. So if I know I want to access Box, I can just launch it really quickly from there. We also have the Okta plugin which you can launch from anywhere you're browsing on Safari, or Chrome, or Firefox. Even IE. Whatever the newest version of IE is. I guess Edge. And you can launch that from anywhere you are in the internet. So really quick access to your applications. And you see here I have a VPN. So we integrate with networking infrastructure too.
Point here is really simple end user experience. When I saw all those hands go up I asked who's in the IT team. So I know you got some questions. The questions are probably in this vein, "How do I make this work for me?" I think we can all agree that this would have some value in any organization, or your employees can go somewhere and get seamless access. "But how do I get it done?" And that's the magic of Okta. So two questions I want to talk about is, "How do I get my users, or anyone's users, from my directory into Okta?" You're not going to have to recreate everything from scratch. You want to leverage what you have. The next question, the second question is, "How do I get my apps on there? How do I integrate the apps that I care about, and that I've subscribed to?" So I'll show both.
One more point I wanted to make actually. I logged in as Cameron. Cameron, in this case, is an engineer. And that's why you're seeing these specific applications. [Sesplunk and Jeera 00:14:04]. There are some common applications, and there are special applications that are assigned to a specific group of users. She got these applications because she's an engineer. She also happens to be a contractor, which will be important later.
But to show you the admin UI, actually I have to logout here. So I'm going to login as my admin persona, and things are going to look a little bit different. So the first thing is I have different applications. I have more applications as an IT. I have access to a lot of stuff. There also organized differently because this is a different user account. I've just set things up differently. I have different personal applications here as well. I also have this admin button. And that flips me over to the admin UI. Now I hope that you notice this, because we're proud of it, but we invest a lot in the admin UI too. And this is a little bit, maybe different than some technologies that you've used before.
Admins are tech savvy. You don't necessarily need to hold their hand. So often technologies won't invest in the admin user interface. But at Okta we firmly believe that A, identity management in the modern world is a problem technology is well suited to solve, and B, that technology should help the admin solve that specific problem in those use cases. And the way that you do that is with a really great user experience and UI. You have to make some compromises. You have to take a stance on how to solve those problems because you're not just going to give them a box to type some code into. But we think it yields a better experience and makes customers more successful.
Okay, so this is just the dashboard, but I promised I'd show you how to integrate a directory. The way you do that is go to the directory integrations tab. You see here everything you do in Okta is in this one admin UI. To add a directory, you see I already have two here. Two LDAPs, and an AD. And to add one is very simple. I'm going to pretend to add another active directory here. Before I go on, I want to pause here because this architecture actually shows a lot of the secret sauce of how Okta works with AD. We knew that our customers had ... Most of them had AD as the primary source of identity, or authoritative source, and identification. So we invested a lot in this and making it super lightweight. You don't want to have to deploy a bunch of new infrastructure just to get access to your own infrastructure that you're looking at SAAS applications to help you get off it. Right? It's kind of a conflict of interest there. So we wanted a lightweight way to do it. And we do that with our Okta agent.
This agent does provisioning, which creates accounts either in AD or imports users from AD into Okta, or both. And authentication. So you're actually using ... Your end user is using your AD password to login to Okta. And it communicates to Okta only over port 443, HTTPS outbound traffic only. What that means is you really don't have to make any firewall changes. You can browse the internet from the server you install this on, you're good to go. And our customers sing this feature's praises a lot because negotiating with the networking and security team to get that done can take a lot of time, and there's a lot of finagling. So this saves a lot of time. The last thing I want to mention about this, it's a small download, it's only two megabytes. Again it's really lightweight. But they automatically load balanced too.
So when you're thinking about load balancing, when you're talking about [inaudible 00:17:10] infrastructure, thoughts are going through your head. "How do I invest in the hardware to have this? I need a [inaudible 00:17:15] active, passive standby. I need the whole set of infrastructure to make sure if one things goes I have continuity of service." These do all that automatically. The way it works is you employ an agent, you deploy a second agent, and they just take commands greedily. So if one of them's busy, the next one's going to pick up the slack.
So it's really easy to integrate with active directory, and it's a very robust integration. So if I click setup active directory, I'm not going to be able to do this here because I'm on this computer and not on a server. But if I click download the agent, and I go through these two more steps, and then I'm done. I download the agent. Install it. I configure it to talk to Okta using an API token, and then I configure some basic settings like OU I'm logging in from, and what attributes I want to pull in for the user profile. And when that's done it looks like this. This active directory, these are all the people that I've imported from this active directory. Here's where I set up my settings and filter my OUs. Here's an agent that's down, and tow of them are healthy just waiting for commands. And this is how I import users. Very simple. Seamless. Easy to integrate with AD.
So the next question that we want to talk about was the applications, right? How do I get my applications here? So you saw what applications I already had assigned. To add a new one, that's where the power of the OAN really comes in to the forefront. So to add an application here, it starts with this OAN interface. So first thing I'll call out is that we have some categories here so you can filter down on these applications. You can see here we have 5,250 applications. I always have to read that number because it's constantly changing. There's no way for me to memorize it. And I guess technically it's always going up. I haven't seen it go down. But it's growing. Growing catalog. But the point is a lot of applications. Everything that your business might care about is probably here. If it's not here you can create a new application.
But let's just say that I'm using a SAAS application. And I'm going to choose one for a particular reason called Envoy. So Envoy's a SAAS application which basically allows you to check in guests that are coming to your office. And you can see here that it's a port SAML which is that seamless and secure single sign on standard I mentioned, an provisioning which means I can automatically create those accounts in that application. To add an application I click add, and again four step process. Simple wizard. Admin learns how to use Okta, these things become easier and easier to repeat. So I'm just going to leave this as a general name. I'm going to click next. This step I choose how to sign on.
We support password vaulting, so if it doesn't support a standard like SAML we can still get you in. But we prefer SAML, and this application supports it, so I'm going to choose that. We'll click on view setup instructions. These are in product instructions that tell you exactly how to configure SAML for Envoy. Now these are not just instructions though, these are custom instructions specifically for this tenet of Okta. So I literally just have to copy this and paste this in Envoy, and then I'm done with authentication. Very simple instructions. The next step is to turn on provisioning. Again, same interface, right? This is a four step wizard. To enable provisioning features I'm going to need an API token. I don't have a tenet for him, Envoy, so I'm not goin got be able to set that up. But I just enter the token here. Test it. And then I can granully control about what I'm doing. Am I creating users downstream in the application? Am I just updating attributes?
I probably want to enable this last one which is deactivating users. So if someone leaves the organization, I'm going to automatically delete that account. So once I'm out of this application, I'll be automatically managing users if I enable this. I'm going to disable it because I can't complete that without the API token. But you get the idea. And now the next step here ... Oh. One thing I want to mention here, the reason that I chose Envoy as an application is because Okta didn't build this integration. Envoy did.
So one thing we've been investing in over the past 12 to 18 months or so is a way to empower our partners' independent software vendors out there to build their own integrations of Okta. And deep ones too. Not just authentication, but also provisioning. So Envoy built this. They actually authored the instructions, the configuration guide. They host it on their server, on their site, so it's always up to date. Interesting point there. We're hoping that that's going to lead to more and more ITs doing this and it's going to create this kind of flywheel network effect where that OAN keeps growing at an ever faster rates.
So last step here. This is where the magic happens. This is the assignment step. And I think it's a simple name, but what we're doing here is powerful. I can assign this to everybody. Right? But how often do you actually want to assign an application to everybody? There are some birthright applications, but there's some applications that are specific to a business like Salesforce. Right? So I can search ... If I choose group here, I can search by group. Search for like a sales group. You can see I have a bunch of them here that I can choose from. I can search for a contractor's group, and assign it only to contractors. I can choose any of those. I'll choose this one. There are a couple contractors in there. I select them all. Assign it. And next time they login they see this [inaudible 00:22:06] dashboard. We call them chiclets. The icon.
That's how you add an application to Okta if it's an OAN. Really simple, straightforward process but there's a lot of power in that integration. And what we've done is we've taken all the kind of complexity and abstracted it out, so you're only entering the specific ... The data that's specific to your tenet. I'm going to cancel that because I don't want to create this. Just a demo. Yes I want to cancel. Okay. So that's it. So you're going to see a lot more demos, and we're going to go into a lot more detail about a lot of these things. But that's kind of an intro to Okta. But there's one more thing I wanted to show, and I mentioned that Cameron is a contractor. So we manage that life cycle differently. And one of the value propositions of Okta is ... If I go and find Cameron, and go to her profile, you see she's active right now.
But let's say she's a contractor that's contract expires. I want to terminate access immediately. All I do is I click suspend. Okay. She's suspended, she can't login. She's still assigned all her applications. This account actually still exists downstream, but she can't login to Okta or anything else that's connected to Okta. Let say she comes back a couple days later, who's ever had that happen? Contract magically got renewed. Just two days too late. I unsuspend her, she's active. But now I actually know for a fact that she's gone. So I'm going to deactivate this user. See a big red button here. This is not reversible. What's going to happen is I click this, deactivates the user, not only can she not login, but all those applications are gone. We're deprovisioning those accounts from all those connected applications.
So that automates that business process, closes that loop so that when Cameron leaves the organization either of her own free will or not, she's not going to be able to login and get access. So that concludes my demo. And I want to kind of take a few minutes to tee up the rest of the demos. Because like I said, this is just the beginning. So I showed you how to manage groups in Okta. End user groups in Okta. How to import from AD and how to connect to your applications including web applications, even [inaudible 00:24:10]. But once you've mastered identity access management, once you have your arms around it, you're affording a lot of opportunities to do a lot of different things. One of them, which [Salmi's 00:24:18] going to demo next, is adding security on top that. Everyone authenticates through Okta, so why not turn on NFA? You want to turn on NFA for your whole organization? Do it one fell swoop. Also, this gives you the ability to have visibility access all across your organization.
Who's doing what [inaudible 00:24:35]? What apps are they using? Once you master identity access management, you can also then extend that to maybe your custom applications, your developers that are building against APIs. How do you control access to the APIs and the scopes behind that so they get access only to the right data, but in a seamless way so they don't have to send a bunch of people a bunch of emails? So Keith is going to do a demonstration of how you do that with Okta API access management. Another you can do is go deeper with life cycle management. Maybe you don't use AD. Maybe you just want to import users from your HR system so you only have to create them once, and then they can be propagated everywhere else. Okta supports that. And Raphael's going to do a demo of how you can use HR as that master source, and also do more granular control around the life cycle.
More granular life cycle state, and support for different types of users. And the last thing you can do, or one of the ... The last thing you're going to see today that you can do is around devices. So once you've mastered identity and access management, you can then extend that experience to any device. And the goal here is a device agnostic experience. You as IT shouldn't care what the user's using. They should have a seamless experience. They should be able to do their work and get access to everything they need. And Mike's going to do a demo later showing you how you can use OMM to extend that experience not only to mobile devices, but also to mobile applications as well.
So we hope you enjoy these demos. Definitely want to chat with you guys in the cocktail reception afterwards. A lot more to come obviously. We crammed a lot into this afternoon. And that's all I have. Anyone has any questions I got a couple minutes here. Any questions? Mike's coming around.
Male Audience: So you spoke really quickly about how you use an agent basically to kind of be the mediatory from outside into a SAAS product. Whatever. Is there any way that you could high level talk about like OPCs and OnPrem stuff, and what the difference is, and what the handshake now that you're behind the firewall rather than coming out from the outside?
Eric Kralinsky: Absolutely. So the handshake is secured using TLS. It's just like browsing internet how you establish a secure session with any website as a user. So that our agent use the same thing, we actually ping the certificates so they can do mutual authentication to the Okta service. That lives not in the DMZ, but actually on your local network and it just communicates over port 443. And the way that ... We use a process called long poling, which essentially it pings Okta every 60 seconds or so for new instructions. And it tears down that TLS channel and sets them back up. So it keeps us secure, keeps it lightweight, and allows it to support any command that we want to send it. And we do have agents not only for AD but for other integrations as well like provisioning to all OnPrems's applications and things like that. So good question. And we can go into a lot more detail too if you want.
Any other questions? All right. Well thank you guys so much. If you have questions find me at the cocktail reception. I'll see you there.
Today’s world is increasingly cloud-powered, leading forward-thinking CIOs to digital transformation as the edge their organization is looking for. Traditional identity management solutions struggle to securely and efficiently accommodate this new paradigm and provide a best in breed approach. Join this discussion to learn how a modern identity management solution is the key to thriving in the new IT landscape.
