How Okta secures your Java EE Application Server (without reinventing the wheel)
Today’s post gives an overview of how Okta integrates with Java EE Application Servers to protect your Java infrastructure. This includes:
- Oracle WebLogic
- IBM WebSphere
- Red Hat JBoss
- Glassfish
I also cover improving end-user experience and security with Single Sign-On (SSO) and Adaptive Multi-Factor Authentication (MFA), and how to simplify account management with an identity store such as LDAP. All this while reducing the costs and headaches associated with hosting and maintaining additional software and infrastructure on-premises.
Tip: If you use Java on micro-services or modern micro frameworks such as Spring Boot, you can integrate your Java app directly with Okta. No Application Server configuration required (yay!).
Quick Question: What's a Java EE Application Server?
Tip: If you already know what a Java EE Application Server is, skip to the next section.
Java EE Application Servers, such as those listed above, are infrastructure components typically used on legacy Java Enterprise Edition (J2EE) deployments. They provide modular services for developers and system administrators to run, integrate, and manage Java applications with IT infrastructure such as databases, directories, HTTP Servers, etc.
Although J2EE Application Servers are not as popular as they used to be (modern Java apps are typically built using micro frameworks like Spring Boot) a lot of companies still rely on them to run legacy apps including:
- Custom services: Enterprise JavaBeans (EJB), Java Message Service (JMS), and SOA Web Services (SOAP)
- Custom web apps: Java Server Pages (JSP) and Java Server Faces (JSF)
- Oracle Fusion Middleware stack: WebCenter, BI Publisher, Fusion Apps, etc.
Using your Application Server native support for integration
Java EE Application Servers are built modularly. They rely on Java EE standard specifications (e.g., JDBC, JAAS, and JAZN) and standard IT protocols (e.g., LDAP, SAML, SQL, and HTTP) to host Java apps and integrate them with your IT infrastructure.
Okta can also leverage these IT protocols to provide SSO, MFA, and identity store to external services (lightbulb moment!)

Okta, App Server, integration options
In the next section, I'll show you three ways you can integrate your Application Server with Okta — without reinventing the wheel.
Three integration options
Okta offers a few integration patterns, such as SAML, Reverse Proxy, and the LDAP Interface, that integrate with custom and legacy apps. This gives the app owner the flexibility to choose the pattern that best addresses their business and technical limitations, such as resource constraints, product know-how, and time to market.
SAML
SAML is an XML-based standard protocol used for SSO. Okta works with SAML and can provide both SSO and Adaptive Multi-Factor Authentication to your Java Application Servers and web Apps. Using the Application Integration Wizard, you can configure SAML in Okta in minutes.
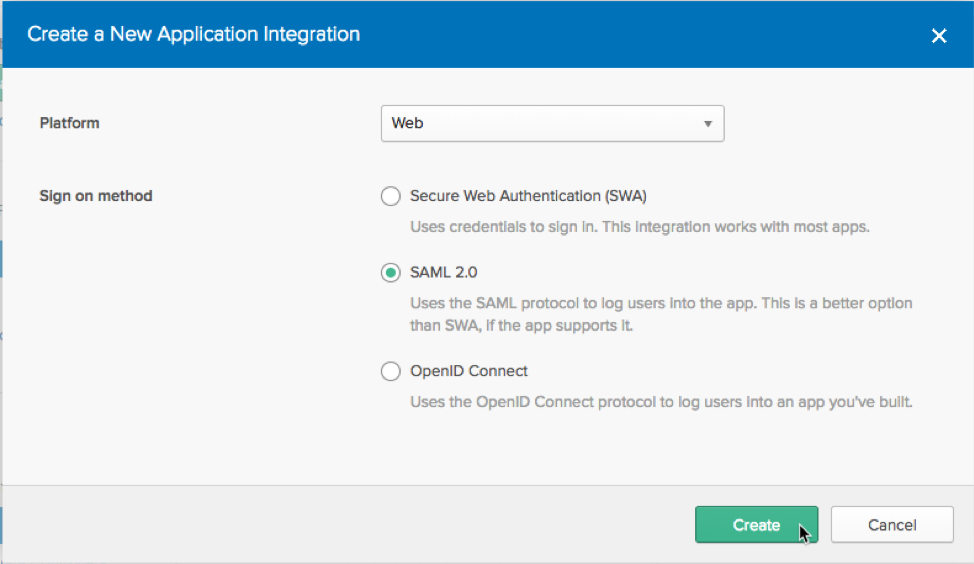
Application Integration Wizard - SAML
On the Application Server side, you can use tutorials like this one provided by Oracle or this one by RedHat or the documentation provided by your Application Server. Oracle Weblogic Server, IBM WebSphere, and RedHat JBoss all provide specific sections about SAML.
When integrating with your Application Server, you can also look for special features to simplify the process. WebLogic, for example, supports virtual users. This feature allows your application to establish user sessions from Okta without creating users in your WebLogic user store.
Reverse Proxy (or header-based authentication)
Reverse Proxy is a deployment architecture used by legacy SSO solutions such as CA Siteminder, Tivoli Access Manager, and Oracle Access Manager (OAM). This architecture, also known as header-based authentication, leverages network segmentation, plus a load balancer or HTTP server, to evaluate the user log in before allowing access to the Application Server and its apps:
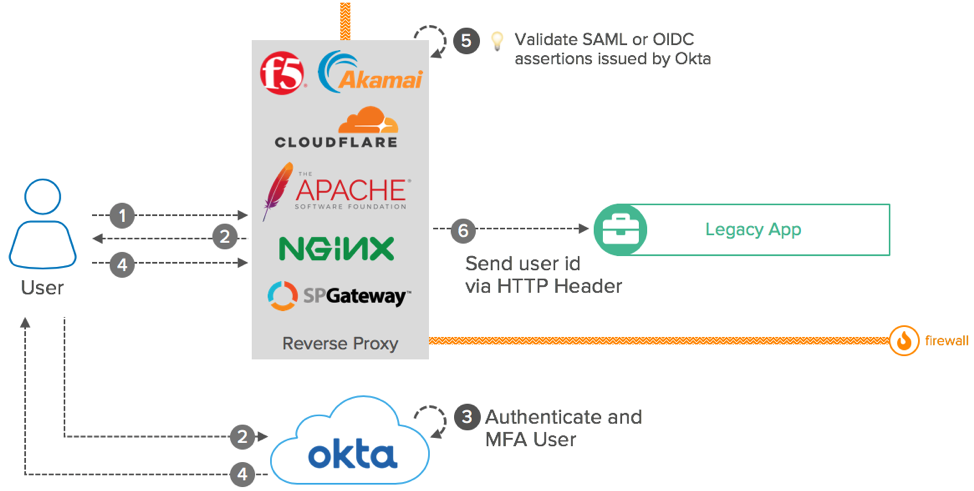
Diagram with Reverse Proxy
Okta supports integrating with HTTP servers such as Apache or NGINX, and load balancers such as Akamai, Cisco, and Big-IP F5 using SAML and OpenID Connect. You can use these types of integrations to implement reverse proxies.
The reverse proxy integration is a last-resort option if you already use this architecture and want to replace your legacy SSO with Okta SSO and MFA. However, it is not considered a best practice by security experts. Its dependency on network segmentation requires this approach to be thoroughly reviewed. A more modern option would be an approach like Zero Trust.
LDAP Interface
LDAP is, by far, the most popular integration used by Java EE Application Servers for storing and authenticating users and groups. To give a sense of its popularity, WebLogic Server comes by default with an LDAP server embedded for development purposes.
Okta provides an LDAP interface with identity store, authentication, and MFA straight from the cloud — no agents or client required. The LDAP interface can integrate directly with your Java EE Application Servers.
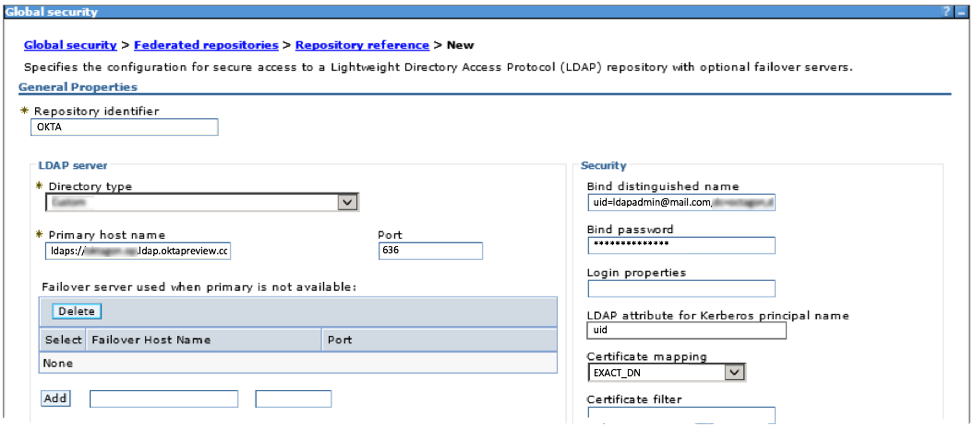
Setting an LDAP connection on WebSphere
The LDAP interface is a great integration option if you don't want to configure SAML in your Application Server. You can use LDAP to control access for end-users, as well as the Application Server administrative interfaces.
What will work best for me?
Each integration option provides capabilities that are best for specific scenarios:
- SAML is great for providing SSO and Adaptive MFA, especially if you're already familiar with your Application Server support for this protocol and your Application Server supports additional features such as virtual users and Just in Time provisioning. However, some Application Servers offer scant SAML documentation and a poor configuration experience.
- Reverse Proxy is a last-resort option when you just want to replace your current SSO solution with Okta. However, this type of architecture (even with your current SSO solution) is considered risky, since it relies solely on network segmentation for security controls. This is a legacy approach that is no longer aligned with modern security best practices such as Zero Trust.
- LDAP Interface is an outstanding option if you want to quickly integrate with your Application Server without worrying about SAML configuration. Even though LDAP doesn't support SSO, the Okta LDAP interface supports login and MFA for both the end-user access (via web app) and the admin access to the Application Server administrative consoles.
If you are an existing Okta customer, check your Application Server, pick an option and integrate with us. You can use our new Help Center in case you have questions. If you're new to Okta, reach out to us so we can help you!

