9 Admin Best Practices to Keep your Org Secure
When implementing security policies across an organization, most administrators want to adhere to industry best practices. But that’s not as easy as it may seem: the threat landscape isn’t static — it’s changing day by day.
What were once considered the best practices for security configurations, including password policies and MFA requirements, have shifted as new threat vectors have emerged, and these standards will undoubtedly continue to evolve in the coming years (if not months or weeks).
That’s why today at Okta Showcase, we’re excited to announce a new feature within the Okta SecurityInsights feature family, HealthInsight. As a dashboard available for admins, HealthInsight continuously monitors an organization’s security policies and settings within Okta, and offers customized recommendations for admins on how they can make changes to enhance their security posture. Because HealthInsight recommendations are updated in response to developments within the security landscape, Okta customers can stay current with best practices as they evolve over time.
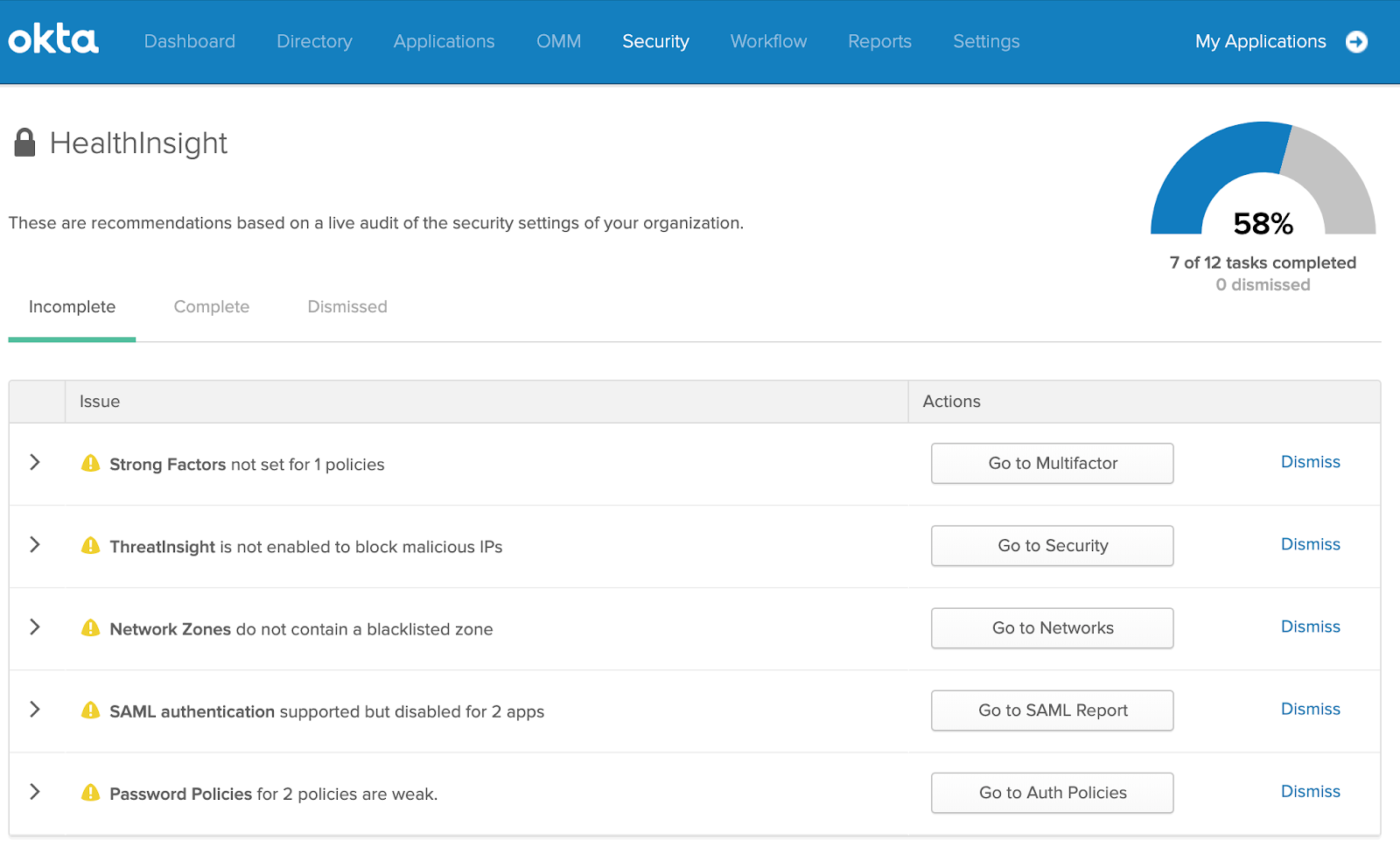
In this post, I’ll break down what these best practices are and why they are important, so anyone — not just Okta customers — can leverage them to protect their people and data.
The Checklist
Okta has thousands of customers across every industry, in countries all over the world, ranging from small businesses to enterprises with hundreds of thousands of employees. Our experience working with these organizations — and the insights gathered from that work — informed the development of our security best practices that define this checklist. Like the threat landscape itself, HealthInsight is dynamic, and will evolve to keep pace with the needs of our customers.
Listed in order of security impact, here are the best practices that our customers will see in HealthInsight.
1. Require MFA for Okta Administration access
It’s critical to enforce multi-factor authentication (MFA) policies for administrative accounts, which have privileged access to high-impact resources. A 2017 study from Forrester estimates that 80% of security breaches involve privileged credentials, which often belong to the IT admins who administer the organization’s systems, databases, and networks. Thus, maintaining strong MFA policies for these powerful accounts is essential.
2. Limit the number of Super Admins
Speaking of admins, the Super Admin role has the highest permissions of all the admins within Okta. Super Admins can create other admins, assign or remove permissions, and perform all other admin activities. By limiting the number of administrators who have this level of permissions, organizations reduce the odds of a bad actor gaining access to one of these highly privileged accounts and wreaking havoc from within.
3. Use ThreatInsight to block suspicious IPs
At the network level, Okta ThreatInsight is a powerful way to identify and automatically block login attempts from suspicious IP addresses. Monitoring all authentications across Okta’s vast network of customers, ThreatInsight collects and analyzes metadata and behavioral signals to reveal risks from suspicious IP addresses that could otherwise go unnoticed. When Okta sees large-scale identity attacks like DDoS, password spraying, high rate of login failure, etc., the responsible IPs are added to the ThreatInsight list, and customers can choose to block access from those IP addresses.

Across our customers with ThreatInsight enabled in audit or block mode, password spray attacks made up 80% of suspicious login attempts flagged by the tool over the past three months. We hope that HealthInsight will encourage even more customers to enable this feature, so they can monitor for similar credential-based attacks.
4. Use strong factors in factor enrollment policies
While MFA is a “no-brainer” way to add an additional layer of security and defend against credential-based attacks, not all factors are created equal. Traditionally popular factors like Security Questions and SMS have proven to be problematic. Bad actors can easily find the answers to security questions online, and SMS can leave users vulnerable to phishing and SIM jacking attacks. To stay current, administrators should require users to authenticate via strong factors, like WebAuthn, push notifications, and security keys.
So, how are our customers doing? Our customer base has grown significantly over the past two years, and over that period, our customers have gotten much smarter about MFA. We took a look at the percentages of our customer base using various factors, and found that a decreasing percentage of our customers with MFA are leveraging insecure factors like SMS and Security Questions, while stronger factors are on the rise.
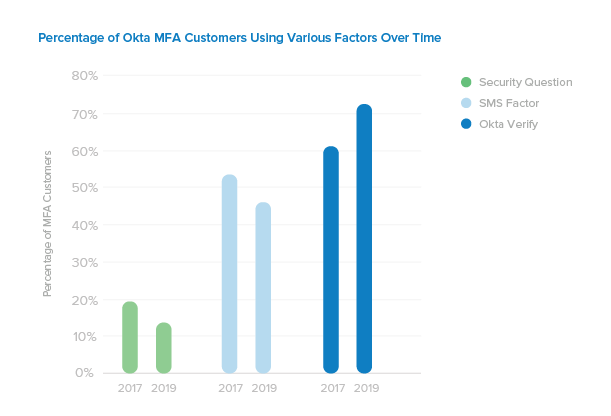
When comparing data from September 2017 to September 2019, we found that the percentage of organizations leveraging Security Questions and SMS as a factor has shifted downward by as much as 8%. This suggests that more and more of Okta’s new customers know better than to rely on these weaker factors for added protection. In contrast, we are encouraged to see the percentage of customers adopting a more secure alternative, Okta Verify, shift upward by 11% over the same period.


Using HealthInsight, our customers are encouraged to continue moving in the right direction by requiring more secure ones during factor enrollment and deprecating weaker ones.
5. Enforce a limited session lifetime
Session lifetime determines the maximum idle time of an end user's sign-on session to Okta. By enforcing a limited session lifetime for users, admins reduce the window of time wherein a malicious third party could attempt to access a user's applications from an active session.
This is especially important considering the workforce is no longer strictly confined to within the walls of an office. This functionality is a must for any organization with employees, contractors, and partners that work from home or other remote locations like coffee shops and airports.
6. Enable user notifications for new sign-ons, new factor enrollment, and factor resets
Signing in from a new client, enrolling a new MFA factor, and resetting a factor are fairly uncommon actions for a user, and can sometimes indicate foul play by a bad actor. To address this risk, our customers can and should enable user notifications for each of these instances.
Thanks to UserInsight, another feature in the SecurityInsights family, should one of these anomalous events occur, the user will receive an email alert through which they can report the activity to their admin if they don’t recognize it, thus turning targets into first responders.
7. Use SAML authentication for app access
According to Verizon’s 2017 Data Breach Investigations Report, 81% of hacking-related breaches were a result of weak, stolen, or reused passwords. One way to counter credential-based threats is to reduce the use of passwords as much as possible.
For many applications, this can be achieved by implementing SAML-based authentication. While not all apps support SAML, for the ones that do, admins should require that users login via SAML-based authentication rather than with separate credentials. This reduces the need for passwords, resulting in reduced risk of a breach via threat vectors like phishing, password spraying, and credential stuffing.
Customers that use SAML-supported apps but haven’t enabled the SAML-based authentication functionality will receive alerts within the HealthInsight dashboard to let them know about this opportunity for improved security.
8. Blocklist network zones to deny access to an Okta tenant
To supplement ThreatInsight, our customers can take an even more proactive approach to defending against malicious IPs and geographies. Perhaps there are locations or IPs from which an administrator knows they never want to grant a user access to their Okta client. Examples might include a competitor’s location, an area of the globe where the organization never conducts business but that has a reputation for launching cyberattacks, Tor anonymizer proxies, or an IP address that has launched an attack against the organization in the past.
To address these instances, we recommend blocklisting network zones to deny access to the Okta client in specific situations. Customers can do so by restricting access from IP zones, which contain a list of IP addresses, or Dynamic Zones, which contain a list of locations, ASNs, or IP types. The result? Any attempts to access the Okta client from these obvious sources are stopped in their tracks.
9. Use Strong Password Policies
For many organizations, the password remains the first line of defense protecting organizational data access from bad actors. To ensure that it’s a strong one, define password policies that specify requirements for:
- Lockout: The maximum number of invalid password attempts before locking the user's account.
- Password history: The number of distinct passwords users must create before reusing a password. This prevents users from reusing a previous password when resetting their password, which reduces the likelihood of credentials that have been compromised in a data breach being reinstated.
- Password age: The minimum time interval required between password changes. This setting restricts users from bypassing the password history requirement by preventing them from rapidly cycling through password changes in succession and re-selecting an old password.
- Minimum length: The minimum password length required. Greater lengths encourage the use of passphrases, which provide greater protection against brute force attacks.
Conclusion
We hope that by leveraging these best practices developed from 10 years of working with forward-thinking security leaders, our customers will not only improve their security posture to defend against today’s threats, but be positioned to continually adapt in the face of a dynamic threat landscape with agility and ease.
HealthInsight is currently in Early Access, and is available via the Feature Manager. Learn about the other elements of Okta’s SecurityInsights feature family here, or contact us for more information.

