The Dogfooding Chronicles: UserInsight — Keep it Secret, Keep it Safe
In this edition of The Dogfooding Chronicles, we’re going to discuss both sides of the same security coin: 1. How your end-users can serve as the first line of defence against credential-based attacks, and 2. how your IT department can automate tactical defence actions by using Okta’s new Workflows automation and UserInsight tools.
Frodo! I swore to protect you
Just as Samwise Gamgee swore to protect Frodo, IT and Security teams are on the hook to protect their organizations. IT departments use a wide range of tools to protect them from malicious attacks. These protections range from beefing up the security on edge devices such as firewalls, installing endpoint security software on employee laptops, or securing the workforce with Identity and Access Management solutions like Okta.
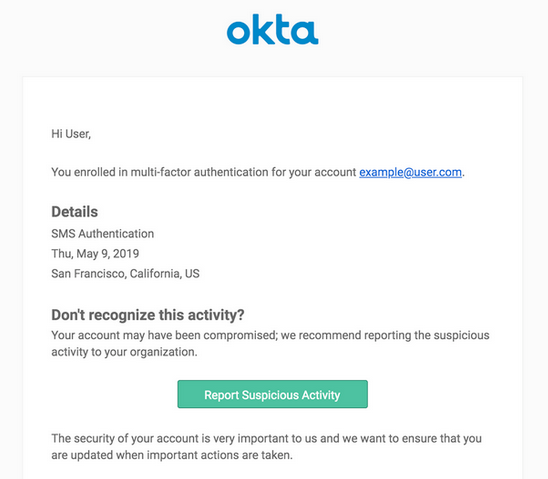
But with people as the new perimeter, who better to serve as your dynamic monitoring tool than your own employees!? After all, Frodo saved Sam once or twice too! Similar to how the TSA encourages people to "If You See Something, Say Something”, through the click of a button, Okta UserInsight allows your users to share in the responsibility of protecting your organization. UserInsight’s suspicious activity reporting alerts users to anomalous activity within their account, including logins from new devices, and the enrollment or resetting of multi-factor authentication (MFA).
If the beacons of Gondor are lit, Rohan must be ready for war!
In Lord of the Rings, the warning beacons of Gondor were the alarm system for the realm. And while I wish we had the ability to simply light a bonfire to alert security issues, the Okta IT team requires a more modern approach. When an employee reports suspicious activity, there should be automated workflows in place to handle the event. This is where Okta Workflows has been a huge asset to the Okta on Okta team. If you’re not familiar with Okta Workflows, it's an event-driven automation tool that handles complex, identity-centric processes—no code required. For details on how to use this in your own organization, refer to our detailed Okta Workflows documentation.
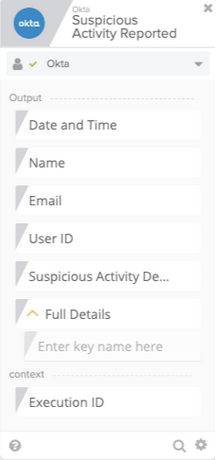
As stated earlier, the event that drives security automation is when a user has reported some suspicious activity. Here’s what the event Workflow card looks like.
These details are then used to clear the Okta user’s session, reset their password, and create an incident in PagerDuty. The actions taken on the Okta employee’s account give our IT team time to respond to the PagerDuty alert. They can assess the situation and reach out to the impacted user to determine if this was indeed a bad actor attempting to take over their account. But it could also note a false positive, where the user has legitimately signed into a new device, but is unaware that an email alert was generated.
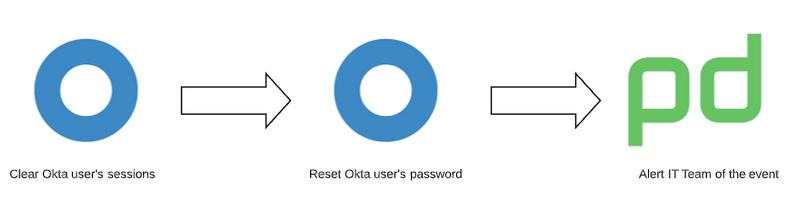
If our IT team determines that the user has been compromised, the security team is engaged to perform in-depth forensics of the situation. While this situation is not ideal, simply putting your head in the sand and hoping these situations never happen is not the solution. You must have a plan in place for if and when security incidents occur.
Fool of a took!
While some IT departments have no issues with enabling new features the day they are released, it would be foolish if you and your IT team did not have a plan in place before enabling UserInsight. I have mentioned the tenet of always planning before enabling in previous posts but I want to keep reiterating this point. If you want to successfully deploy organization-wide changes, it is imperative that you include, not just the teams that are involved with the operational support aspect, but also the impacted end-users. When deploying UserInsight, there are key details your employees should be made aware of.
Security notification emails
Any time a user signs into Okta from a new device or enrolls/resets their MFA, that user receives an email alerting them of the event. If your employees are unaware of these emails, it’s likely they'll report false positive events. While we want our employees to be security minded, we don’t want to waste IT department cycles.
Employees should also be familiar with the actions that are taken once they click the Report Suspicious Activity button. This not only helps their understanding of the new feature, but also decreases the number of reported false positives.
Your time will come. You will face the same evil, and defeat it.
If you have the mentality of, it's not if, but when a malicious actor attacks one of your users, you're already on the path to protecting your organization from outsider threats. And UserInsight is just one of the three elements of Okta’s Security Insights that can protect your organization from attacks. HealthInsight analyzes your Okta org and makes configuration suggestions that are inline with defined best practices, and ThreatInsight ensures that login attempts from malicious IP addresses are automagically blocked!
As Samwise once said, “It’s the job that’s never started that takes longest to finish.” Do yourself a favor and protect your company with UserInsight.
We've been at this for a while now, so don't ever skip a meal—read them all!
Introducing… The Dogfooding Chronicles
Dogfooding Chronicles: How Okta uses Okta
The Dogfooding Chronicles: Group Therapy—Getting All You Can From Okta Groups
The Dogfooding Chronicles: WebAuthN—The Path to Passwordless

