Okta + the NCCoE are Ready to Rock Zero Trust Security

What do a security strategy, a government agency, and a rocker all have in common? No, this isn't a silly joke; it’s the way I’m thinking about how large organizations can approach new paradigms. A way that can be music to our collective ears.
If you’ve been watching the latest season of Stranger Things, Volume 4 (Don’t worry, no spoilers), you’ll be aware of my favorite character, Eddie Munson. If not, let me introduce you: Eddie is a rocker. And if there’s anyone reading this who knew me back in the day, you’ll know why I love the Eddie character so much. Eddie is me…. 40 years ago. A D&D playing, rockin’, long-haired “nerd” who pretty much sums up my high school existence. The one piece of me that is missing from Eddie is/was my love of technology.
I see technology as an enabler. It helps us collaborate securely and become more productive. Though my “rock star” dream never came true, another one did come to life: a passion for connecting people through technology. I help people maximize the value of their technology investments and to build in security—from the beginning. It's that harmony of security and capability that's music to every practitioner's ears.
This is why I’m so excited about Okta’s collaboration with the fine folks over at the NIST National Cybersecurity Center of Excellence (NCCoE). Alongside some of our great technology partners, we’re working to provide answers to the many challenges around successfully adopting and deploying a Zero Trust security model. It’s been one year after the announcement of Okta’s participation in July 2021. Now, a testament to our deep collaborative efforts, the working group is releasing its first practice guide, Implementing a Zero Trust Architecture, for the first Zero Trust enterprise build.
You've heard it many times: Zero Trust isn't a product. It’s a “mindset shift", a “lifestyle choice” that requires organizations to think differently about where, when and how they DO security in their organization. Security is the cross-domain orchestration of policy, people, process, and technology. In Zero Trust, they span the five pillars defined by CISA (an adaptation of the original Extended Ecosystem proposed by Forrester in 2010) to help solve for these particular aspects of this new, “enlightened” philosophy of a modern security model.
It’s no accident that “identity” is the first pillar in a Zero Trust journey. Nothing happens until someone on some device requests access to data delivered by an app, and it’s an area Okta knows well. As a modern identity cloud, Okta’s mission is to connect “anyone, from anywhere, to anything”, providing access and simplifying identity—all while delivering the friction-free security we need today.
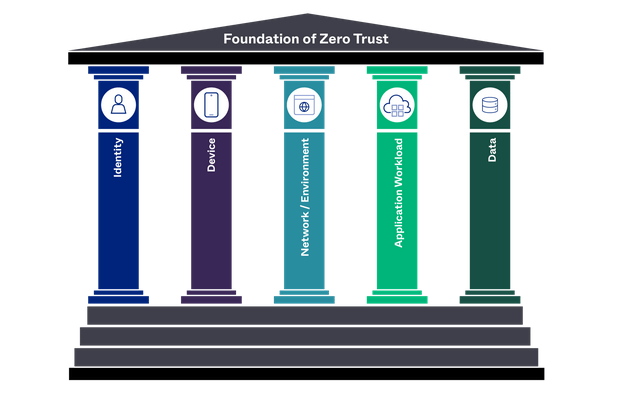
This is why NCCoE's work is so important, and why Okta is thrilled to contribute its time, talent, and technology to its success. The NCCoE is guiding government agencies, as well as commercial organizations, on how to adopt this Zero Trust security approach. They also identify the technologies that can be used to satisfy the Zero Trust pillars in your organization. The beauty here is that, most likely, you’ve already implemented some of these technologies or capabilities in your current environment. You can leverage them alongside a few new components that can really bring your shift to Zero Trust mindset to life.
If I think back to my good old days in the band, our musical collaboration would never have sparked if my bandmates and I couldn’t work together to deliver a great show for our audience. How does this translate into a Zero Trust project? The Okta and NCCoE working group release of this first guide was the band coming together. We’re working to make sweet harmony between security, access and all of your options, and delivering on the promise of Zero Trust in our technology future.
Still confused about Zero Trust for government? Learn more at okta.com/fedzerotrust.
While the example implementation uses certain products, NIST and the NCCoE do not endorse these products. The guide presents the characteristics and capabilities of those products, which an organization’s security experts can use to identify similar standards-based products that will fit with their organization’s existing tools and infrastructure.

