Okta’s enhanced smart card auth helps keep gov resources safe
Nearly two decades ago, the U.S. Homeland Security Presidential Directive 12 (HSPD-12) established a new identity policy for federal employees and contractors. Its goal was a strong, government-wide approach to secure both physical and logical access. Today, the Personal Identity Verification (PIV) and Common Access Card (CAC) standards are prevalent throughout the U.S. government because they provide strong, phishing-resistant authentication that meets the requirements under the Federal Zero Trust Strategy. And Okta supports both.
PIV/CAC cards can be cumbersome for end users, who must insert them into card readers during authentication. Our customers in the U.S. government seek the same rigorous security combined with the seamless user experience they’ve come to expect from Okta. To that end, we're thrilled to announce that Okta now supports Smart Cards as an authenticator, now Generally Available (GA).
Introducing the Okta Smart Card Authenticator
This highly anticipated feature allows customers to use PIV/CAC cards as an authenticator. It provides customers the flexibility to use PIV/CAC cards to safeguard their most critical assets and to accept less stringent authenticators for other resources — minimizing friction to their end users. Specifically, admins can now:
- Require PIV/CAC cards as an MFA authenticator for sensitive apps, while allowing lower assurance authenticators for less sensitive ones.
- Enforce PIV/CAC cards for specific user group(s) while providing non-PIV/CAC card holders, such as military families or international mission partners and contractors, access via alternative authenticators. This prevents shadow IT and information-sharing workarounds.
- Determine PIV/CAC card requirements based on risk level or contextual factors such as new geo-location, new IP address, and new devices, minimizing user friction while maintaining a strong security posture.
- Use PIV/CAC cards as an authenticator to satisfy possession factor, knowledge factor, and hardware-protected requirements for authentication policies, depending on the security characteristics of the card.
- Easily configured to use only PIV/CAC cards or any phishing-resistant authenticator as an added security measure.
See how it works
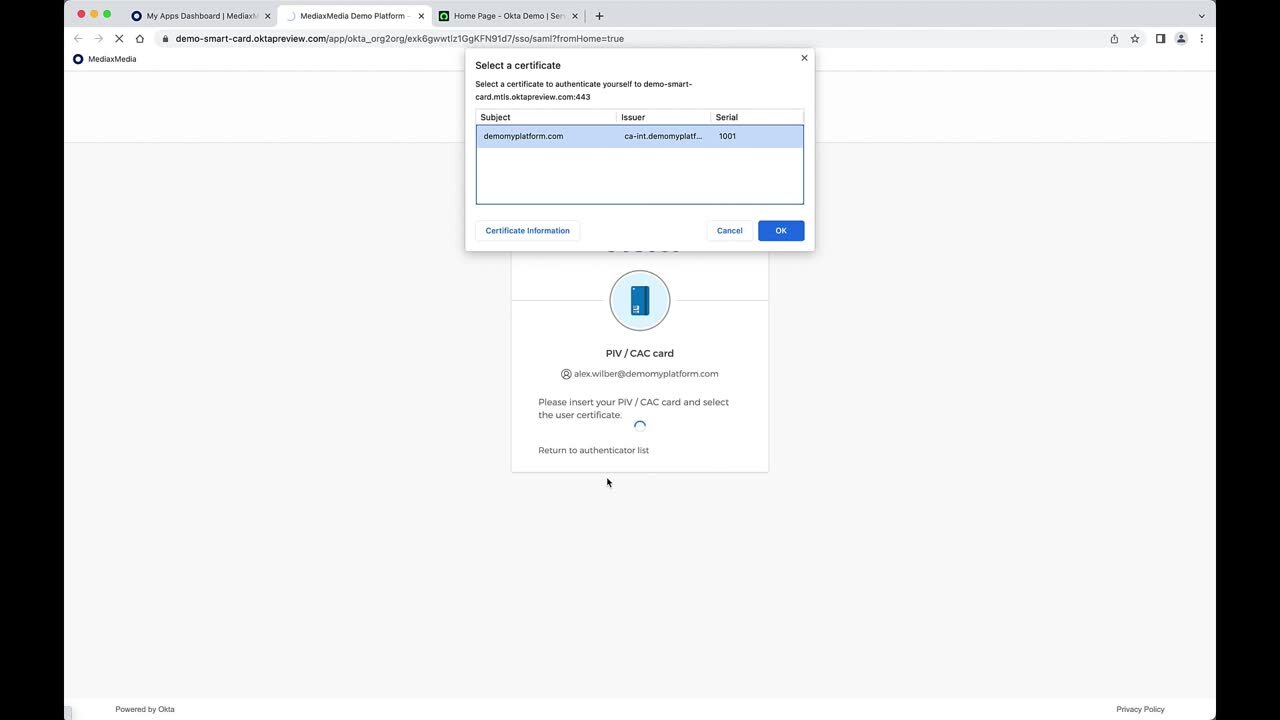
Experience how effortlessly end user Alex Wilber logs in to Salesforce for the first time using his PIV/CAC card. His Okta admin has created a sign-on policy for the Salesforce app that requires PIV/CAC cards for an extra level of security.
Availability
The Smart Card Authenticator is available in the Okta Identity Engine (OIE) for the following customers
- Okta for Government Moderate
- Okta for Government High
- Okta for US Military
Please note that the Smart Card Authenticator feature requires existing licenses for Single Sign-On (SSO) and Multi-Factor Authentication (MFA)/Adaptive MFA.
Start exploring the Smart Card Authenticator feature today! To enable the feature, simply reach out to your Customer Success representative. For more information, check out our product documentation here.