Okta and beyond: Building a robust defense against web attacks
In the realm of cybersecurity, understanding and implementing a multi-layered defense strategy is crucial. Okta offers protection against a broad spectrum of web threats. However, as the digital threat landscape evolves, augmenting Okta's capabilities with specialized services adds critical protection.
Okta's frontline defense: Understanding ThreatInsight
At Okta's front gate is ThreatInsight, a powerful tool designed to protect against credential-based attacks. Here's a closer look at how it operates:
- Edge/infrastructure layer: proactively blocks known malicious IPs at this layer, safeguarding its tenants from broad threats
- Okta ThreatInsight functionality: detects suspicious activities from IPs that are not definitively malicious but exhibit potential threat characteristics and adds suspicious IPs to its database based on their behavior across Okta's customer base, blocking or logging their activities as configured
- Pre-authentication policies: includes geolocation and network-based policies evaluated before credential verification, reducing false positives and improving user experience
- Authentication and post-authentication: involves credential verification and enforcing app-specific policies and secure access and data handling
Despite these measures, it's important to recognize that ThreatInsight focuses on credential-based attacks. Supplementing with other attack protection services ensures a full-coverage approach.
Enhancing Okta with specialized security services
Okta recommends integrating its services with additional, specialized security solutions.
Web application firewalls (WAFs)
While Okta secures Identity and Access Management (IAM), integrating WAFs brings an essential layer of security for comprehensive web traffic monitoring and filtering.
This collaboration effectively aims to block malicious requests and protects against sophisticated attacks like SQL injection and cross-site scripting. WAFs strengthen Okta's IAM and ensure enhanced data security without compromising user experience. This dual-layered approach is vital in today’s digital landscape, where web-based threats are constantly evolving.
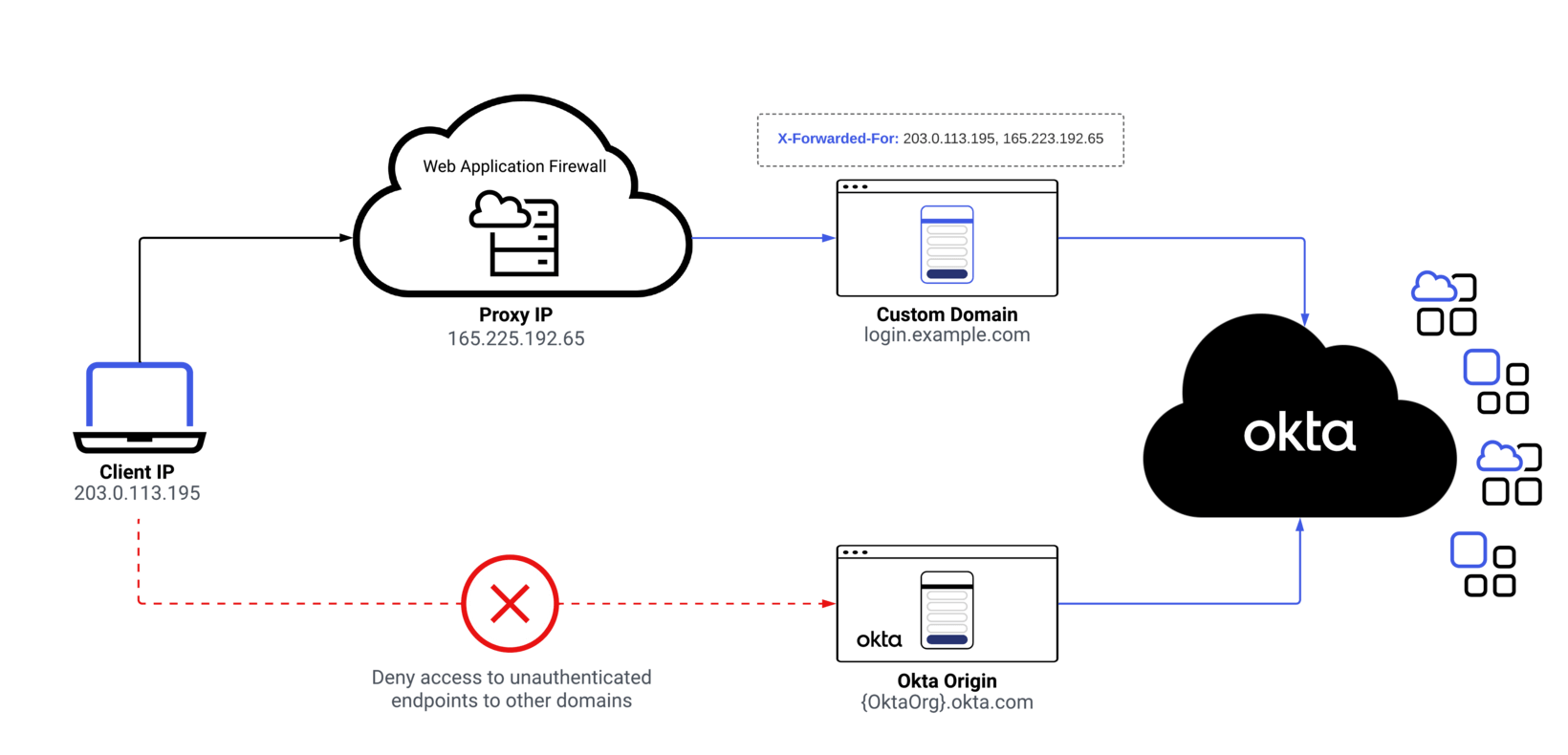
Figure 1: Use of custom domains, WAF / HTTP proxies and the X-Forwarded-For.
Bot management services
In the battle against automated threats, Okta's integration with bot management services plays a crucial role. While Okta manages authentication and access controls, it also offers CAPTCHA integration capabilities, enhancing its security against bots.
These tools are crucial in distinguishing between legitimate users and automated bots, adding an extra layer of verification. This integration plays a key role in safeguarding against automated attacks like credential stuffing and account takeovers. It reinforces Okta's defenses, making sure that only legitimate users are granted access.
Security alert management services
Enhance your security alert management with Okta’s Syslog API and Log Streaming features. These tools provide deeper monitoring and faster response to security threats.
- Syslog API: Get real-time access to security and system logs. This API integrates seamlessly with SIEM systems, allowing for customized monitoring and alerts based on user activity and potential security threats.
- Log streaming: Offers continuous, real-time export of system log data, essential for proactive threat detection and analysis. It’s compatible with various cloud-based data platforms, enhancing your ability to manage and analyze large volumes of log data efficiently. Together, these features form a robust approach to threat detection and response, ensuring your security infrastructure is resilient and responsive.
DDoS Mitigation Services
DDoS Mitigation Services are designed to safeguard against the debilitating effects of large-scale DDoS attacks, which can cripple network infrastructure and disrupt business operations. Integrating DDoS Mitigation Services with Okta establishes a robust defense, fortifying your resources against the high-volume traffic typical of these attacks and maintaining resilience even under extreme conditions.

This proactive approach is a key component in Okta's strategy to protect against the rising tide of DDoS threats, ensuring continuous operation and security at the edge of your network.
Let's explore Okta’s strategies to counteract DDoS threats.
Okta's approach to DDoS protection
Okta employs advanced techniques to mitigate DDoS attacks.
- AWS Shield Advanced integration: Okta utilizes AWS Shield Advanced for comprehensive DDoS detection and protection, covering infrastructure and application layer attacks, including HTTP floods.
- AWS WAF for enhanced filtering: Okta employs AWS WAF for automatic filtering based on IP addresses, geographic blocking, and HTTP header information.
- Multi-layered customer protection: Okta implements various protective measures at the cell/customer org level, including:
- Separate Okta cells, limiting the impact of DDoS attacks
- Filtering of inbound URL requests at the web proxy level
- Rate limiting to prevent DoS through resource utilization
- Lockout detection caused by unknown devices
Best practices for implementing specialized security services
When integrating Okta with other security services, consider the following best practices.
Assess your unique threat landscape: each organization's needs differ. Assess your specific threat landscape to determine the most appropriate integrations.
Implement Zero Trust principles: Embrace a Zero Trust security model, which operates on the principle of "never trust, always verify." This includes strict access controls and continuous authentication of users and devices accessing the network.
Continuous monitoring and evaluation: Regularly monitor and evaluate your security posture to adapt to new threats and integrate emerging security solutions.
Standards-based systems: Opt for security solutions that adhere to established industry standards. This approach ensures compatibility, reliability, and easier integration with existing and future systems, providing a more robust and scalable security framework.
For the latest in Okta's comprehensive approach to security, please visit Okta Security.
You don’t have to go it alone
We understand this is a lot to chew on. Fortunately, Okta has a team in place to ensure your security posture is at the cutting edge. Expert Assist leverages Okta’s comprehensive Identity expertise to identify vulnerabilities and provide you with best practices for fighting ever-evolving security threats. Get your assessment with Expert Assist.
These materials and any recommendations within are not legal, privacy, security, compliance, or business advice. These materials are intended for general informational purposes only and may not reflect the most current security, privacy, and legal developments nor all relevant issues. You are responsible for obtaining legal, security, privacy, compliance, or business advice from your own lawyer or other professional advisor and should not rely on the recommendations herein. Okta is not liable to you for any loss or damages that may result from your implementation of any recommendations in these materials. Okta makes no representations, warranties, or other assurances regarding the content of these materials. Information regarding Okta's contractual assurances to its customers can be found at okta.com/agreements.

