Tactical Identity Bridge Appliance: How the U.S. Government can extend Okta to the tactical edge
Many federal organizations are meeting cloud computing strategies for persistent access to information by leveraging software-as-a-service (SaaS) technology for their enterprise mission use cases. For the U.S. Department of Defense (DoD), enabling cloud innovation must support data to and from various environments. DoD’s mission capabilities are increasingly influenced and dependent on software, to the extent that they’re actively working to extend cloud access points to the tactical edge: environments with limited bandwidth, sporadic connectivity, or no connection to the internet.
Tactical edge examples we’ve seen at Okta include military operations in remote or isolated areas, U.S.-led humanitarian efforts where hurricane-force winds knock over power lines, and critical infrastructure organizations planning for complete and total internet access disruption. In a tactical edge scenario, user experience (UX) and services may be limited due to those environmental conditions, but at Okta, we believe that Identity, Credential, and Access Management (ICAM) decisions should continue to operate securely and without friction.
ICAM beyond the realities of the enterprise
Okta has partnered with SelecTech to field the Tactical Identity Bridge Appliance (TIBA) to support ICAM requirements while disconnected and, once communications allow, seamlessly re-integrate users and their data into the enterprise. The TIBA is tailored for secure deployment at the tactical edge. It adheres to stringent Federal Government and DoD security requirements without reducing access to cloud-based, industry-leading SaaS capabilities.
How it works
TIBA is a dynamic collection of microservices deployable on customer-owned hardware. Administrators can turn microservices on or off to meet low-resource usage targets with a small infrastructure footprint (e.g., a backpack of equipment in a military operation). Admins can also scale out the microservices in a multitenant fashion in cases of higher resource demand and greater infrastructure availability. TIBA provides the following benefits to tactical edge environments:
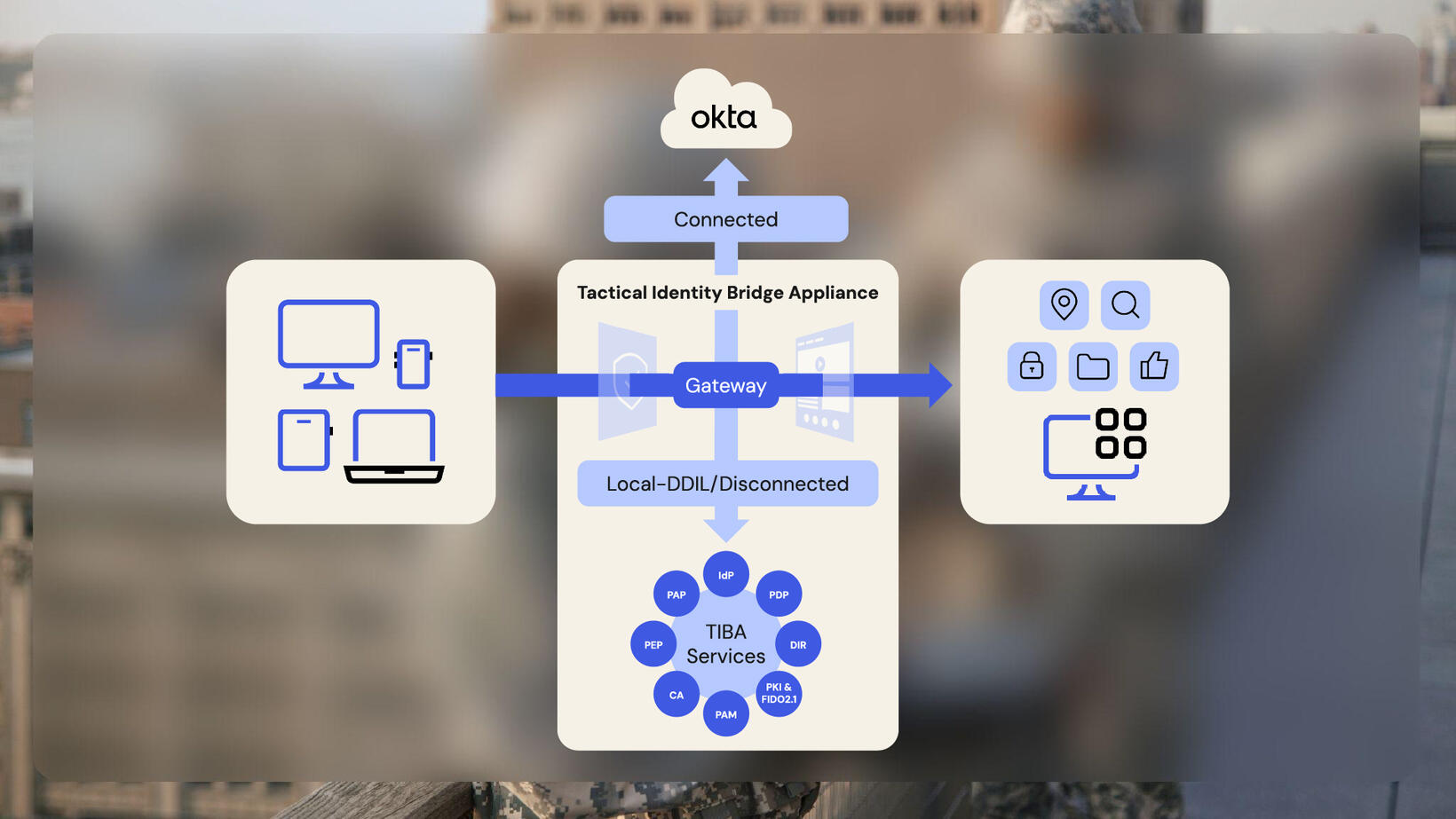
- Identity-aware network monitoring and routing: When connected to the internet, the TIBA recognizes network changes and passes all authentication and authorization back to Okta as the primary Identity provider (IdP) via the Okta Tactical Edge Connector. This solution also enables Okta to federate to a greater enterprise ICAM solution for authentication, as needed. Additionally, the TIBA can take advantage of Okta’s product features, Security Operations Center (SOC) / Network Operations Center (NOC) integrations, and AI/ML solutions. When disconnected from the internet, the TIBA gateway brokers all tactical edge applications, identities, and non-person entities to its local Identity service with a seamless UX— without reconfiguring relying parties.
- Identity and attribute synchronization: When connected to the internet, the TIBA synchronizes its local directory service with Okta’s Universal Directory (UD) in real time. Because Okta can source identities and attributes from anywhere (i.e. HR systems, databases, REST APIs, and other IdPs) the TIBA can receive real-time Identity and attribute updates from the enterprise, mission partner environments, or various databases maintained throughout the government. No longer is the tactical edge an island with outdated or hand-jammed user information.
- Operational rigor in disconnected environments: When disconnected, the TIBA can:
- Maintain a local directory service of identities, roles, and attributes
- Authenticate and authorize users into local applications
- Use phishing-resistant multi-factor authentication (MFA), including Common Access Cards (CAC) and Personal Identity Verification (PIV) cards
- Collect biometrics during in-person Identity verification
- Provision new users and add or modify access management policies
- Generate cryptographic credentials, including FIDO or PIV, at the tactical edge
- Authoritative “System of Record” updates when reconnected: Once reconnected to the internet, the TIBA syncs with Okta and receives important, authoritative enterprise Identity updates in real time. Often, tactical-edge environments are rife with outdated information about personnel (e.g., roles, ranks, pay grades, training records, etc.). With the automatic reconnection sync between Okta and the TIBA, the tactical edge stays as up to date as possible, synchronized with an enterprise’s system of record.
Benefits of Okta and TIBA
Okta’s robust collaboration with the TIBA supports modern and resilient ICAM infrastructure across all domains and priorities to remain available to the federal workforce. Let’s look at a few scenarios the solution meets.
Mission turnaround time
In the DoD, a great example of improving mission turnaround time involves forward-deployed military operations, like Cyber Protection Teams that employ a tactical-edge environment often referred to as a “flyaway kit.” Currently, when a kit returns home from its mission, it‘s manually wiped clean and reconfigured for the next mission.
Imagine a world where all of the identities, attributes, and appropriate application access policies for the next mission have been pre-configured and pre-staged within Okta’s UD. When the kit returns home, its Identity audit logs can be stored, wiped clean, plugged back into the network, and automatically provisioned into the kit’s TIBA for the next mission.
Disaster planning and mission partner environments
In other areas of the Federal Government, where agencies send field teams to disaster sites with limited or no internet connectivity, organizations can leverage their Okta instance to pre-configure a TIBA while relying on standalone Identity operations in the field.
These organizations can also use the TIBA to federate with mission-partner agencies who require access to their local disaster resource planning and assistance apps, enabling them to use their credentials to log in to emergency service apps. Commercial organizations like financial services and healthcare sectors could benefit from this integration by using the TIBA as their failover mechanism in extreme disasters where internet connectivity is severed.
Phishing-resistant credentials at the edge
Phishing-resistant credentials are critical for highly secure government operations. Unfortunately, and commonly at the tactical edge, broadly issued credentials such as CAC/PIV are not authorized. This typically means admins at the edge who are trying to accomplish their missions end up breaking security best practices in environments where they should preserve operational effectiveness.
In other situations, foreign mission partners arrive onsite at the tactical edge and can’t access U.S. Government phishing-resistant authenticators. They often receive a less secure username and password.
TIBA’s native credential management service addresses these problems. Admins can verify a person’s identity, provision them with strong cryptographic credentials (e.g., apply a certificate to a Yubikey or print a PIV card on site), and create fine-grained access policies for them.
Cloud forward cross-domain operations
For some U.S. Government agencies, certain tactical environments, like air-gapped or classified networks, will never touch the internet. In these extreme circumstances, an Okta plus TIBA strategy provides enterprise unclassified environments with the full benefit of cloud-native SaaS technology. These are the types of environments where nation-state attackers and cyber criminals live and have threat vectors they can try to exploit. That’s why Okta’s pre-built integrations with network, endpoint, data, SIEM, and SOAR technologies are crucial. However, leveraging the TIBA on air-gapped or classified networks provides a robust Identity and Access Management experience in a complete offline mode, making prebuilt SOC/NOC integrations less relevant. Moreover, the ability to source and transfer identities and attributes from a flat file in Okta and the TIBA makes this a holistic approach to ICAM across network fabrics in complex Federal Government environments.
To learn more about the TIBA capabilities, use cases, and operation modes, visit okta.com/resources/datasheet-how-okta-supports-missions-at-the-tactical-edge/, and when you’re ready to take the next step, schedule a TIBA demo with us at [email protected].

