Bridging the gap in browser security with Google and Okta

Browsers are today’s primary work portal. Most corporate applications and sensitive data now live behind SaaS and other cloud services, and we reach them through browsers like Chrome, Edge, and Safari.
This elevates the browser from a mere application to a critical policy enforcement point, which makes browser security a foundational element of a modern Zero Trust architecture. However, one gap continues to undermine enterprise browser security: employees using personal profiles to access corporate data.
Mixing personal and work browsing creates outsized risk, and managed browser profiles can help restore control without sacrificing user experience. Google and Okta have partnered to make managed Chrome profiles practical to scale.
Why personal profiles are a problem
BYOD and hybrid work normalized the habit of using personal devices and browser profiles for work. On corporate machines, users commonly sign in to personal Chrome or Edge profiles to sync bookmarks and passwords. But that convenience comes at a cost. Key risks for personal browser use in the workplace include:
- Credential leakage: Personal profiles make it easy to save work passwords into personal password managers and sync them beyond corporate oversight. When personal accounts or devices are compromised, attackers inherit corporate logins. Poor password hygiene compounds the risk: many employees reuse passwords between personal and work contexts or save work passwords straight into the browser.
- Insecure or unvetted extensions: Browser extensions are ubiquitous and powerful. Many request permissions to read and change site data, capture keystrokes, access cookies, and interact with local files. Employees can install anything — from helpful tools to risky adware — in a personal profile without review. That opens credible paths for data exfiltration, credential harvesting, and session hijacking. Because personal profiles sit outside your extension allowlist/denylist, they become a blind spot for prevention and forensics.
- Policy evasion and shadow IT: Web filtering, download restrictions, data loss protection (DLP), and other controls are often attached to managed browser contexts. A personal profile may sidestep those controls. Users can visit blocked sites, upload corporate files to personal drives, or use unapproved SaaS services. This activity wouldn’t show up in your SIEM, and remediation is harder because there’s no reliable audit trail.
The case for managed browser profiles
The solution is to create a clear separation: bring all work-related browsing under corporate management while leaving personal use untouched. Managed browser profiles enforce your policies, support your identity stack, and provide the visibility your security teams need while allowing employees to maintain a separate personal profile. Google’s managed Chrome profiles do precisely this and can be easily configured via the Google admin console and federated with Okta.
The control points for managed profiles are consistent and comprehensive. Identity and sign-in are anchored to a dedicated work profile and authenticated with corporate single sign-on or SSO (e.g., Okta), keeping work credentials, tokens, and cookies isolated from personal contexts. Administrators can enforce multi-factor authentication (MFA), disable password saving to personal vaults, and check device posture during authentication. Security policies like web filtering, safe browsing, DLP enforcement, certificate pinning, and VPN or SASE routing can be applied directly to the work profile and enforced uniformly across managed and unmanaged desktops. Extension control is also centralized, enabling IT teams to define allowlists, block unvetted add-ons, and auto-install trusted tools.
Managed browser profiles offer four clear benefits:
- Data isolation: Work credentials and session data stay within the managed profile, while personal browsing artifacts — like cookies, extensions, and passwords — remain separate. This limits risk if a personal account or device is compromised and prevents accidental data leaks (e.g., uploading sensitive files to personal cloud storage).
- Consistent security policies: Security controls — such as MFA, DLP, download restrictions, and password rules — follow users across devices. That helps ensure that access to SaaS apps stays protected through the managed profile, whether on corporate or personal machines.
- Reduced risk and faster response: Organizations reduce the attack surface by eliminating common threats like stored work credentials in personal profiles or unauthorized cloud uploads. Managed browser telemetry enables faster incident investigation and response.
- Improved user experience: A managed profile minimizes distractions, seamlessly enforces security, and separates work from personal browsing. Users benefit from seamless SSO with pre-approved local network access policies and tools like Okta FastPass.
In short, managed profiles strike the balance between enterprise-grade security and employee productivity. They transform the browser from an unmanaged risk surface into a more secure, policy-enforced workspace, no matter where the user logs in.
How Okta and Google simplify the rollout
Okta and Google make managed profiles practical to deploy across managed and unmanaged Windows, macOS, and Linux devices. Provisioning the work profile starts with Okta federating sign-in to Chrome so that users authenticate with their corporate credentials. On first sign-in, a managed Chrome work profile is automatically created and bound to your organization’s policies, eliminating the need for a device management solution. For step-by-step setup guidance, see Sign into Chrome with Okta, which walks through creating enterprise Chrome profiles that automatically receive your configured policies. The example below shows the end-user experience when launching the Chrome profile setup from the Okta dashboard.
- Sign in to the "Setup Chrome Profile" app in the Okta end-user dashboard.
- Sign in with FastPass.
![Fastpass sign-in screen]()
- Complete setup in Chrome
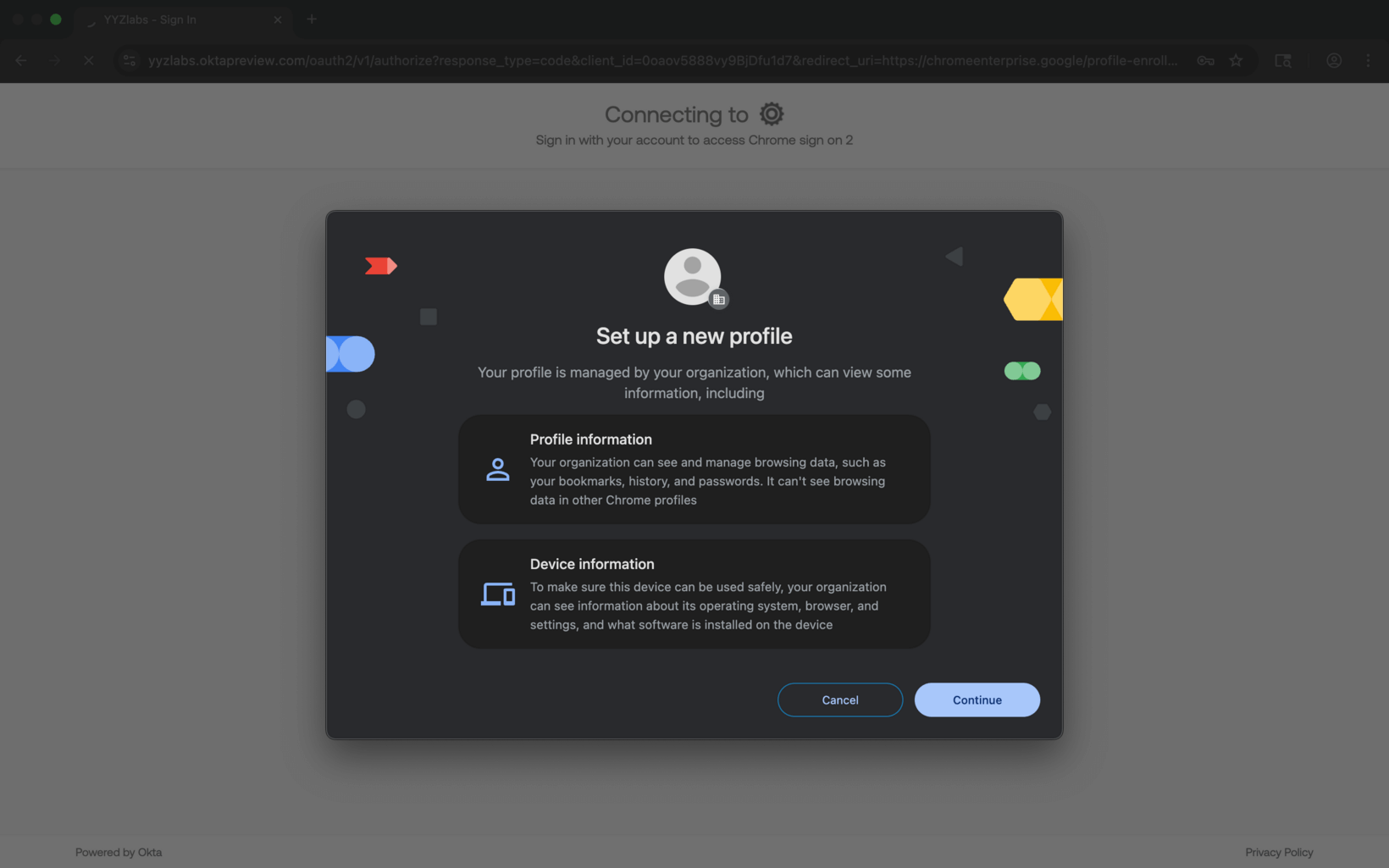
How to deliver a seamless, secure user experience
Through Chrome Device Trust Connector for Okta, admins can enforce device assurance policies such as password restrictions, safe browsing, and site isolation, which are applied before the user accesses any corporate resources.
For many organizations, delivering a smooth, passwordless sign-in experience is as important as enforcing strong security policies. Features like Okta FastPass help achieve both by enabling phishing-resistant authentication with minimal user disruption. However, Chrome’s new Local Network Access (LNA) prompt can interrupt these flows if not pre-configured.
To support FastPass and other authentication flows that rely on a local loopback server, administrators can configure the LocalNetworkAccessAllowedForUrls policy for their Okta sign-in domains, suppressing Chrome’s network access prompt and maintaining a seamless sign-in experience. This should be paired with LocalNetworkAccessRestrictionsEnabled to ensure consistency in enforcement. Once users sign in to the managed Chrome profile with Okta, they receive single-click access to their work apps, with all policies and approved extensions applying automatically, while personal browsing remains untouched. See Configure Chrome to Suppress the Local Network Access Prompt for Okta FastPass to learn more.
Secure browsers make a secure organization
It’s no longer enough to think of the enterprise endpoint as just the device — it's also the browser session. Treating that session as a managed, secure workspace is one of the most effective ways to protect identity, data, and access.
Managed browser profiles, or secure enterprise browsers, offer clean separation between work and personal use, consistent policy enforcement across desktops, improved observability for security teams, and a smoother, less disruptive user experience.
With Okta and Chrome Enterprise, you can roll this out pragmatically. To make the browser your most defended app and bootstrap managed Chrome profiles with Okta, look at the documentation mentioned above. Learn more about Okta’s Chrome integrations and device assurance policies by visiting the Adaptive MFA webpage.
These materials and any recommendations within are not legal, privacy, security, compliance, or business advice. These materials are intended for general informational purposes only and may not reflect the most current security, privacy, and legal developments nor all relevant issues. You are responsible for obtaining legal, security, privacy, compliance, or business advice from your own lawyer or other professional advisor and should not rely on the recommendations herein. Okta is not liable to you for any loss or damages that may result from your implementation of any recommendations in these materials. Okta makes no representations, warranties, or other assurances regarding the content of these materials. Information regarding Okta's contractual assurances to its customers can be found at okta.com/agreements.


