- Home
- Single Sign-On
- SharePoint (On-Premise)
Overview
This app integration supports Single Sign-On. See Capabilities for more details.
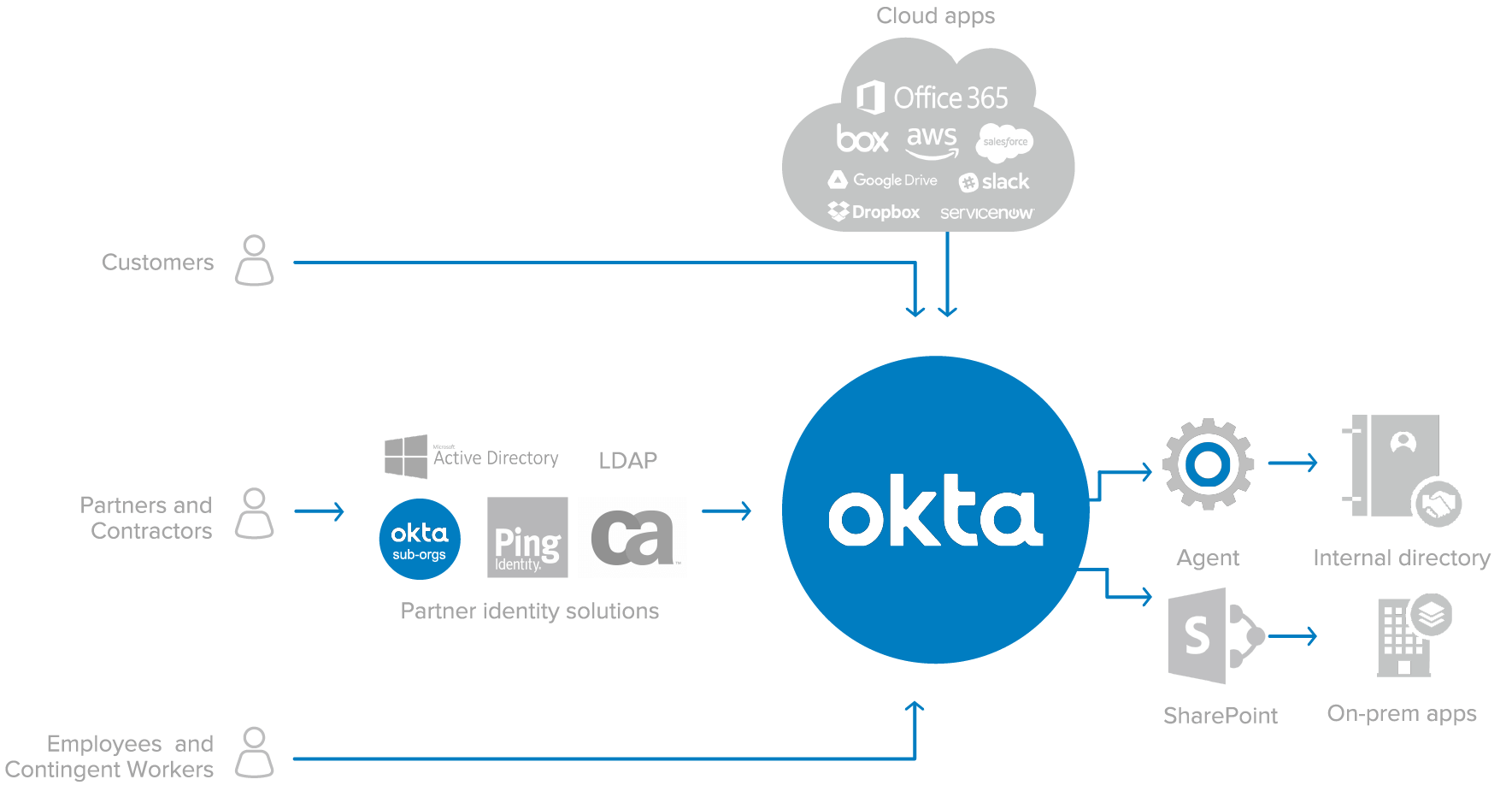
Okta provides complete authentication and user management for on-premises Microsoft SharePoint servers. Combining Okta with SharePoint allows enterprises to collaborate more seamlessly and securely with their employees, customers, and partners.
Okta benefits
Using Okta for identity and access management of on-premises SharePoint offers several advantages:
- Cloud single sign-on to on-premises SharePoint, and any on-premises web apps hosted on SharePoint
- Automated user registration and provisioning to apps hosted on SharePoint
- Flexible API integrations that can be used with a SharePoint custom registration form to support self-service registration and provisioning to applications hosted behind the firewall
Supported versions
Okta currently supports SharePoint Foundation and SharePoint Server 2010, SharePoint Foundation and SharePoint Server 2013, and SharePoint Server 2016.
Integrations
When customers use on-premises SharePoint as an entry point to other applications, Okta’s support for SharePoint 2016 with People Picker enables selecting native Okta users, groups, and claims, when a site, list, or library owner assigns permissions in Microsoft SharePoint.
SharePoint administrators can manage permissions for native Okta users and groups in SharePoint using the Okta Create API. For example, administrators can grant access to users who match a certain email address or who are part of an Active Directory or Okta group.
Access for customers and partners
Okta can integrate to SharePoint for customer and partner SSO via federation. To use certain SharePoint modules, such as SharePoint business intelligence features, users need a Kerberos token. Okta partners with F5 BIG-IP APM to enable exchange of SAML assertions for Kerberos Tokens.
Beyond SharePoint
Okta manages identity, provisioning, and security for thousands of pre-integrated applications in the Okta Integration Network, providing the broadest and deepest identity and access management solution for Cloud and on-premises applications.
Functionality
Add this integration to enable authentication and provisioning capabilities.
Authentication (SSO)
-
API
-
Cross App Access
-
Entitlement Management
-
Event Hooks
-
Identity Security Posture Management Identity Security Posture Management helps to harden the identity attack surface proactively, by identifying vulnerabilities, prioritizing risks, and streamlining remediation.
-
Inbound Federation
-
Inline Hooks
-
Outbound Federation
-
Partial Universal Logout
-
Privileged Access Management
-
RADIUS
-
Secure Identity Integrations - Advanced Supports 4 of the following integration types for the 65+ business-critical applications: SSO, SCIM, entitlements, universal logout, workflows, and ISPM
-
Secure Identity Integrations - Fundamental Supports 3 of the following integration types for the 65+ business-critical applications: SSO, SCIM, entitlements, universal logout, workflows, and ISPM
-
Secure Identity Integrations - Strategic Supports 5+ of the following integration types for the 65+ business-critical applications: SSO, SCIM, entitlements, universal logout, workflows, and ISPM
-
Universal Logout
-
Workflow Templates
-
Workflows Connectors
-
SAML Security Assertion Markup Language is an open standard for exchanging authentication and authorization data between an identity provider (IdP) and a service provider (SP) that does not require credentials to be passed to the service provider.
-
SWA Secure Web Authentication is a Single Sign On (SSO) system developed by Okta to provide SSO for apps that don't support proprietary federated sign-on methods, SAML or OIDC.
-
WS-Federation
-
OIDC OpenID Connect is an extension to the OAuth standard that provides for exchanging Authentication data between an identity provider (IdP) and a service provider (SP) and does not require credentials to be passed from the Identity Provider to the application.
Provisioning
-
Create Creates or links a user in the application when assigning the app to a user in Okta.
-
Attribute Sourcing The application can be defined as the source of truth for a full user profile or as the source of truth for specific attributes on a user profile.
-
Update Okta updates a user's attributes in the app when the app is assigned. Future attribute changes made to the Okta user profile will automatically overwrite the corresponding attribute value in the app.
-
Deactivate Deactivates a user's account in the app when it is unassigned in Okta or their Okta account is deactivated. Accounts can be reactivated if the app is reassigned to a user in Okta.
-
Sync Password Push either the users Okta password or a randomly generated password to the app. This feature is not required for all federated applications as user authentication takes place in Okta, however some apps still require a password.
-
Group Push Push existing Okta groups and their memberships to the application. Groups can then be managed in Okta and changes are reflected in the application.
-
Group Linking Link Okta groups to existing groups in the application. Simplifies onboarding an app for Okta provisioning where the app already has groups configured.
-
Schema Discovery Import the user attribute schema from the application and reflect it in the Okta app user profile. Allows Okta to use custom attributes you have configured in the application that were not included in the basic app schema.
-
Attribute Writeback When the application is used as a profile master it is possible to define specific attributes to be sourced from another location and written back to the app. For example the user profile may come from Active Directory with phone number sourced from another app and written back to Active Directory.
Documentation
Here is a section all about documentation, integration, and implementation.