Okta + Yubico
Accelerating passwordless together with simple, quick, and secure authentication at your fingertips.
The Challenge
The Solution
Creating phishing-resistant users who can go passwordless effortlessly with fast, out-of-the-box FIDO activation
Advance from phishing-resistant authentication to creating phishing-resistant users with security that seamlessly follows them across devices, services, and business scenarios. Yubico’s YubiKeys enable organizations to easily register hardware security keys for end users, securing every stage of the account lifecycle—from onboarding to authentication and recovery—while eliminating the risk of account hijacking.
With Yubico Enrollment Suite with Okta, organizations can select their path to stronger security, and easily enroll YubiKeys on behalf of users leveraging either Yubico FIDO Pre-reg or YubiEnroll.
Yubico FIDO Pre-reg
Yubico FIDO Pre-reg offers a turnkey service that delivers pre-enrolled YubiKeys to users, no matter where they are, in corporate or residential locations, and empowers them to go passwordless from day one.
Available exclusively through YubiKey as a Service, Yubico FIDO Pre-reg is ideal for organizations with over 500 users, with Yubico handling all of the key delivery logistics door-to-door, and reducing burden for both IT staff and end users.
YubiEnroll
YubiEnroll
YubiEnroll enables organizations of all sizes to easily enroll YubiKeys on behalf of end users, or do so through partners, making going passwordless a snap.
With YubiEnroll, organizations can empower their IT team to enroll YubiKeys on short notice, or do so in certain geographies that cannot easily accommodate turnkey delivery services. With YubiEnroll, organizations that purchase YubiKeys can gain access to a client application that allows IT to enroll YubiKeys for the user and deliver them directly to the user.

Secure Access
Okta Desktop MFA for macOS supports all FIDO2 YubiKey models (i.e., YubiKey 5 Series and Security Key Series by Yubico) for authenticating into Apple computers with online access, making the passwordless experience part of the secure access flow.
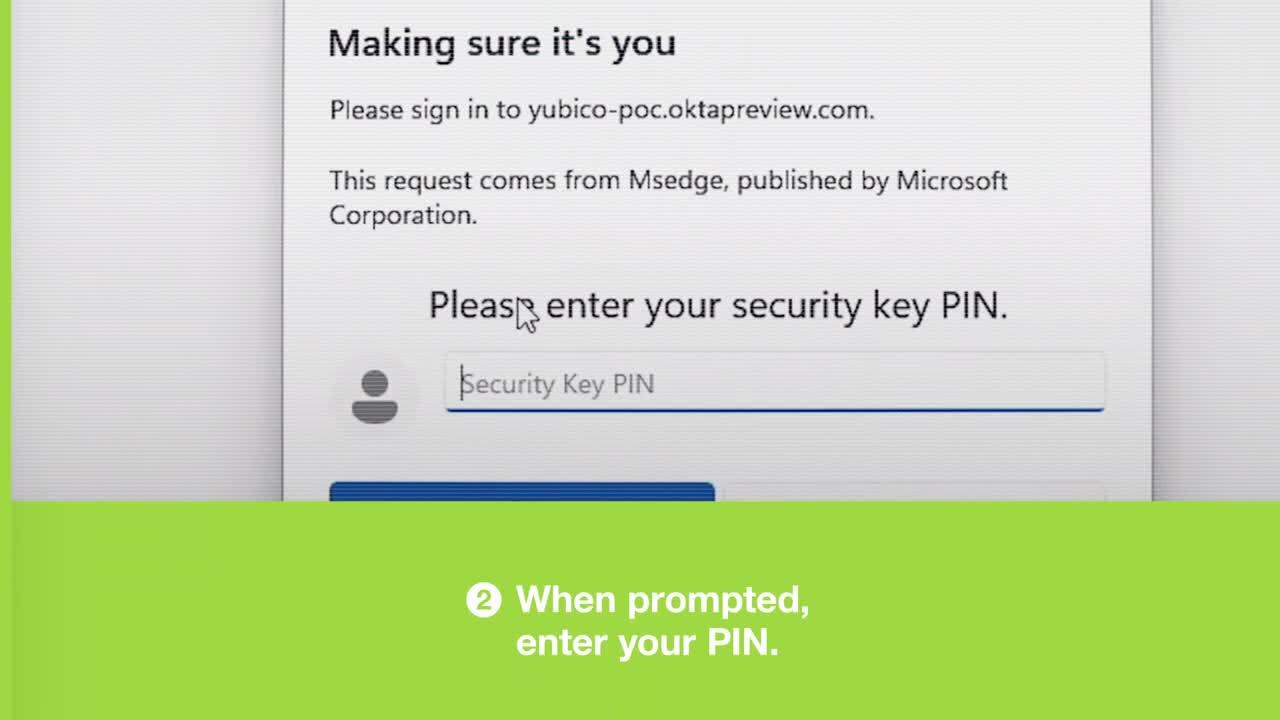

How Okta + Yubico work together:
The YubiKey and Okta Adaptive MFA deliver top-tier identity assurance, protecting against phishing and man-in-the-middle attacks while ensuring a seamless, user-friendly experience with a simple touch. As a cornerstone of Zero Trust security, YubiKeys enable strong, phishing-resistant, passwordless authentication, making it easy for users to securely access apps and services.
Together, Yubico and Okta empower enterprises, government agencies, and consumers to prevent account takeovers and streamline passwordless workflows. This robust partnership ensures reliable, modern authentication across any device or context, overcoming the common barrier of user adoption by providing security without compromising usability.



