4 Ways to Simplify Authentication for Your Users
Authentication can be one of the most significant sources of friction for your application’s users. This usability barrier can impact adoption of your product, increase the burden on support operations or product administrators and, in some cases, degrade security.
At Okta, we spend a lot of time working with developers to design and build better authentication flows. We’ve found that a handful of simple patterns help your users get to what they came for more quickly, and you can implement these patterns today. Here are four ways to make authentication easier for your users.
1) Eliminate passwords with federation
While passwords aren’t the only source of friction, they cause a great deal of pain. In fact, password reset and account recovery requests top the charts at many customer service desks. A secure password can be hard to remember, especially across multiple applications. Password reuse increases vulnerability to attack, while those who resist the temptation to recycle passwords must rise to a monumental memorization challenge.
A great way to cure the password headache is federation, or outsourcing authentication to a service that the user trusts, such as a social identity provider like Facebook or an enterprise identity provider owned by the user’s organization.
Optimize Federated Login Flows
Many applications stop short of achieving a fully streamlined federation experience. Helping the user seamlessly move from their identity provider for authentication and then back to your app is the key to making federated authentication as easy as possible.
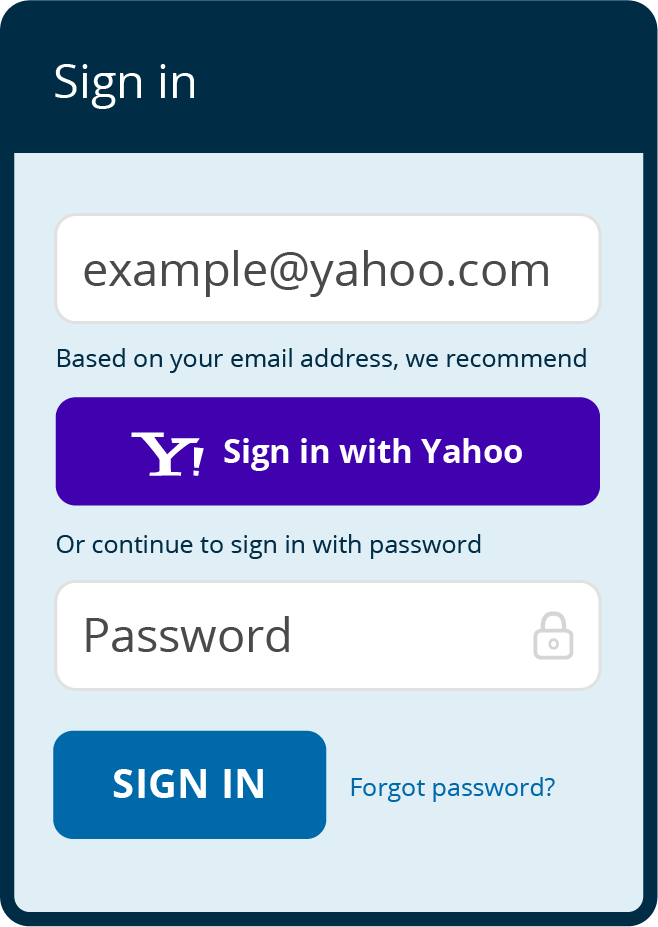
In consumer scenarios, it’s common for people to have profiles with all the social identities offered – so it’s important to help them remember the ID they used to create their account. One elegant method is to ask for the user’s email first. Once the user enters their address, they are given a hint about which identity provider they registered with or are invited to sign up for the appropriate choice based on their domain. A click on the suggested identity provider guides the user to complete login with the identity provider or – better yet – if the user already has a session with the identity provider, they are able to proceed directly into their previously-created account, or an account created on the fly.
If the user signs in with a different social identity provider than they used for registration, an account linking step can establish that the user owns both identities, allowing both to sign in and thereby mitigating the friction of forgetfulness during future sign in attempts.
Business scenarios present a similar need – the “email first” approach is helpful here as well. The user can enter her address and then get redirected to the identity provider for authentication, instead of having to enter a username and password multiple times.
Too often, we see applications that require unnecessary login steps. For example, in the browser, a common mistake is to present a “Single Sign On” button before allowing the user to enter his or her credentials. The application ought to take on the work of directing the user to the appropriate identity provider.
Consider implementing this “email first” pattern to solve many of the friction points associated with federation.
2) Connect your entire product experience with one identity
Applications are quickly modularizing, and developers are increasingly choosing to build experiences across product components: for example, Zendesk and Service Cloud for customer service, and Jive, Lithium and Salesforce Communities for online user and customer communities. In many cases, a product will comprise a set of disparate applications, each built by different teams.
Requiring users to sign in to individual components of a product means they need to remember credentials for each. Further, you’ve probably gone to great lengths to brand each component so it looks like one seamless product, so users will inevitably be confused about which part of your product they’re interacting with.
In modular scenarios, it’s also important to transmit user context consistently from element to element. Entitlements, access policy and other profile-driven context should be the same throughout your product.
Single sign-on can help unify all parts of your application into one authentication step and one session. The identity provider becomes the single source of truth for users, profile information and access rights, and this information passes to each part of your product when accessed.

3) Streamline Multi-Factor Authentication with Mobile Push
One-time passwords are perhaps the most popular form of multi-factor authentication. A user installs an application on their phone or they are issued a device with a time-based code, and they must enter this code upon sign-in within a short time window.
This experience leaves much to be desired. The user glances back and forth, shuttling digits into the login screen a few at a time, rushing to finish before time is up.
With the ubiquity of smartphones comes a compelling alternative: mobile push. Upon installation, an application can send a notification to the user’s device upon primary login. The user can then approve or deny the request with one tap on their phone or smartwatch.
4) Consider Password-less Authentication
Some applications are good candidates for a new approach: eliminating the password altogether. With password-less authentication, the user enters their identifier and then receives a one-time token via email or SMS that allows them to sign in just once before the token expires.
The design wisdom here is that instead of issuing and managing credentials, the flow simply collapses to the account recovery process (and eliminates arduous steps for setting and updating a password in the process). If your application is one that users turn to infrequently, making them more likely to forget their credentials, password-less authentication is a compelling option.
The future is bright
We hope that these ideas will help you make life better for users right away. While we’re not yet at the point where passwords can be eliminated altogether, we are excited about what the future holds. Massive adoption of mobile devices and biometric tools like TouchID creates significant opportunities for improving login UX. For example, with more context about the user’s location, behavior and biometrics, adaptive risk-based models can be developed to provide for seamless access to resources in some circumstances while requiring more involved or onerous authentication steps in others. Watch this space.

