Learn to Integrate Okta and Oracle Weblogic with the LDAP Interface
Okta integrates everything—including Oracle WebLogic Server. In this post, I'll show you how to use the LDAP interface to integrate Okta with WebLogic.
When WLS and Okta work together
Before we start: legacy app patterns
Recently, we announced Integration Patterns for Legacy Applications, an eBook describing design patterns you can use to integrate your legacy apps that remain outside the OIN catalog, with Okta.
I decided to take one of the patterns, #2 LDAP Cloud Interface, for a spin! I’ll use it to integrate Okta with Oracle WebLogic Server and show you the results.
Tip: Okta can integrate with Oracle WebLogic using other patterns like SAML and Header-Based Authentication.
Make sure that everything is A-OK on WebLogic
To begin, take some precautions on WebLogic:
- Confirm your WebLogic and Java JDK supports TLSv1.2: For security reasons, Okta uses TLSv1.2 for protocol encryption. Old versions of WebLogic and Java JDK may require you to turn TLSv1.2 on manually, using the Java argument jdk.tls.client.protocols. Since I'm using versions that already have TLSv1.2 enabled, WebLogic 12c and JDK 8, I'm good to go.
- Back up your WebLogic Server: Depending on how you use WebLogic (i.e., on Fusion Middleware and Fusion Apps) you need to back up the entire environment. If you're using only the WebLogic Server, you can limit the backup to your domain home.
Connect WebLogic to Okta
To connect Okta to WebLogic, do the following, noting that your configuration may look a bit different from what I describe below.
Access your WebLogic Admin Console as the administrator (in my case, admin: weblogic). Go to Security Realm > myrealm. Click Providers > New, then create an LDAPAuthenticator provider with Okta as the name.
The Authentication Provider page lists Okta with the other providers:
Click the Okta provider, then select the control flag as SUFFICIENT, then click Save.
Then head over to the Provider Specific tab and update the Okta configuration using the example as follows.
Tip: For this example, I have an Okta org on myorg.oktapreview.com, with the LDAP interface enabled with an admin account named [email protected].
- Host: myorg.ldap.oktapreview.com
- Port: 636
- Principal: [email protected],ou=users,dc=myorg,dc=oktapreview,dc=com
- Credential: [email protected]'s password
- Confirm Credential: repeat [email protected]'s password
- SSLEnabled: selected
- User Base DN: ou=users,dc=yourorg,dc=oktapreview,dc=com
- User From Name Filter: (uid=%u)
- Use Retrieved User Name as Principal: selected
- Group Base DN: ou=groups,dc=myorg,dc=oktapreview,dc=com
- Group From Name Filter: (cn=%g)
- Cache Enabled: deselected
After saving your settings, reorder the list of providers with Okta listed first.
Click Save, then click Activate your Settings, then restart WebLogic.
Checkpoint: WebLogic can see Okta
After restarting your server, return to WebLogic as an admin and go to Security Realm > myrealm.
Under the Users and Groups > Users tab, you will be able to see users from Okta. If needed, use the Customize this table option to filter the results.
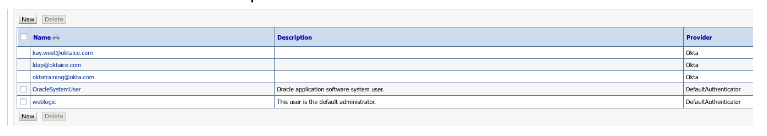
If you go to the Groups tab, you will be able to see the Okta groups:
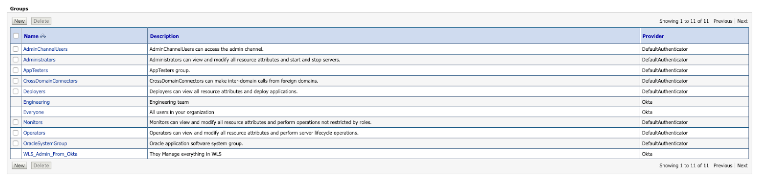
Notice that WebLogic cannot edit users and groups from Okta—and that's great! You can manage users and groups straight from Okta and use the Okta integrations with HR systems like Workday and SuccessFactors. For example, you can limit access to WebLogic based on HR Cost Center, Job Title, and Department.
Grant admin rights in WebLogic to Okta groups
In Weblogic, click Roles and Policies. Expand Global Roles > Roles, then click View Role Conditions next to Admin.
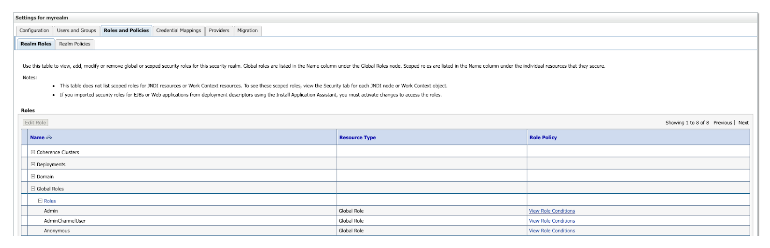
Now, just click the Add Condition button to create a group condition with a name that matches a group name in Okta. In my example, I have a group in Okta with the name WLS_Admin_From_Okta.
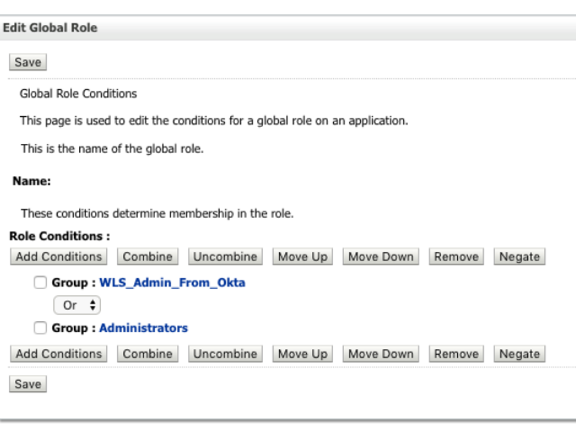
Click Save and log out.
Okta + LDAP Interface + Oracle WebLogic in action
After tying up Okta groups to administrative access in WebLogic, you can test a login. Because I have MFA enabled in Okta, I'll get prompted for an Okta Verify Push during sign in (lightbulb moment!!).

As you can see, Okta users can access WebLogic as an administrator, but only if they are members of a specific group in Okta, and if they can authenticate through MFA.
The same integration works for WebLogic as well as any app that uses the WebLogic Security Realm, such as JAAS, and JAZN compliant apps built in JSP, Java Servers Faces, etc.
The WebLogic config file
To conclude, I'll leave you with my WebLogic config.xml after the configuration, which might be useful if you prefer to edit these files directly:
<sec:authentication-provider xsi:type="wls:ldap-authenticatorType"> <sec:name>Okta</sec:name> <sec:control-flag>SUFFICIENT</sec:control-flag> <wls:host>myorg.ldap.oktapreview.com</wls:host> <wls:port>636</wls:port> <wls:ssl-enabled>true</wls:ssl-enabled> <wls:principal>[email protected],ou=users,dc=myorg,dc=oktapreview,dc=com</wls:principal> <wls:user-base-dn>ou=users,dc=myorg,dc=oktapreview,dc=com</wls:user-base-dn> <wls:credential-encrypted>{AES}123123123=</wls:credential-encrypted <wls:user-search-scope>onelevel</wls:user-search-scope> <wls:cache-enabled>false</wls:cache-enabled> <wls:user-from-name-filter>(uid=%u)</wls:user-from-name-filter> <wls:group-base-dn>ou=groups,dc=myorg,dc=oktapreview,dc=com</wls:group-base-dn> <wls:group-from-name-filter>(cn=%g)</wls:group-from-name-filter> <wls:static-group-dns-from-member-dn-filter>(uniquemember=%M)</wls:static-group-dns-from-member-dn-filter> <wls:use-retrieved-user-name-as-principal>true</wls:use-retrieved-user-name-as-principal> <wls:ignore-duplicate-membership>true</wls:ignore-duplicate-membership> </sec:authentication-provider>
Wrapping up
As you can see, Okta can integrate with WebLogic using the integration patterns for legacy apps. For this post, I used LDAP, but WebLogic also supports SAML and the Reverse Proxy integrations.
If you're already an Okta customer and using Universal Directory, check out our new feature video and start using our LDAP interface.
If you're not an Okta customer yet, talk to us. Let us show you how Okta can help you implement a hybrid cloud or hybrid IT strategy while improving your security posture on cloud and on-premises solutions.

