Off the Beaten Path: How Okta Supports MFA on LDAP in the Cloud
Okta provides an LDAP interface in the cloud (great for hybrid IT and hybrid cloud deployments). The interface does not require an agent on-premises and supports Multi-Factor Authentication (MFA) over LDAP—even though the LDAP protocol doesn't natively support MFA. In this blog post, I’ll explain why and how Okta does it.
Okta LDAP interface: awesome for hybrid cloud
LDAP (Lightweight Directory Access Protocol) is a protocol typically used by directory servers – such as Active Directory, OpenLDAP, and Oracle Internet Directory – to store user and group data on-premises.
Okta recently released the LDAP interface, a feature that allows customers to implement hybrid cloud deployments by consuming Okta via LDAP in the cloud.
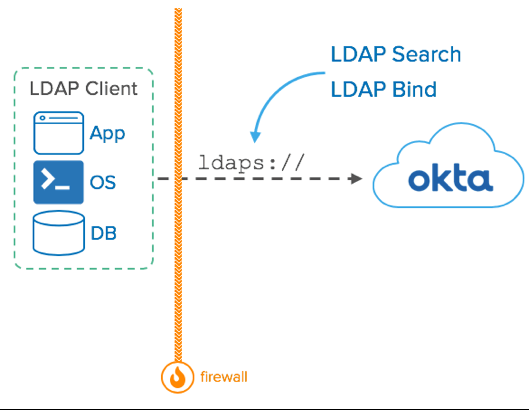
Conceptual diagram of the LDAP interface. No agents required on-premises.
Essentially, the LDAP interface supports user authentication and searches. It’s a huge hit with our customers, as it reduces the cost of integrating with systems that require an LDAP backend such as JIRA, Confluence, Cisco Meraki, JAMF, and VMWare vSphere.
Going beyond the specs: for security
Although most of our customers start using the LDAP interface to reduce their on-premises server footprint, they stay because of a secret killer feature—it supports MFA.
Yes, you read that right. MFA on LDAP!
Most people are surprised with this feature because LDAP doesn’t nativelly support this kind of authentication – LDAP supports authentication only through password and certificates:
ldapsearch -D "<USER_DN>" -H ldaps://org.com -w <PWD> "(cn=John)"
An ldap query with no place for MFA!
However, we decided to add security to LDAP beyond its spec for three reasons:
- Our LDAP interface cannot assume trust (zero-trust model).
- LDAP is a popular integration on legacy systems that adhere to regulations requiring MFA, such as PCI-DSS.
- The LDAP protocol is used on several systems that don’t provide native support for Single Sign-On, such as servers or legacy desktop apps.
The LDAP interface with MFA in action
Another cool thing about the Okta LDAP interface is that it works with any LDAP client app. For an example of how it works, I configured Okta as a LDAP server for JFrog Artifactory – an app typically used by developers to store binaries.
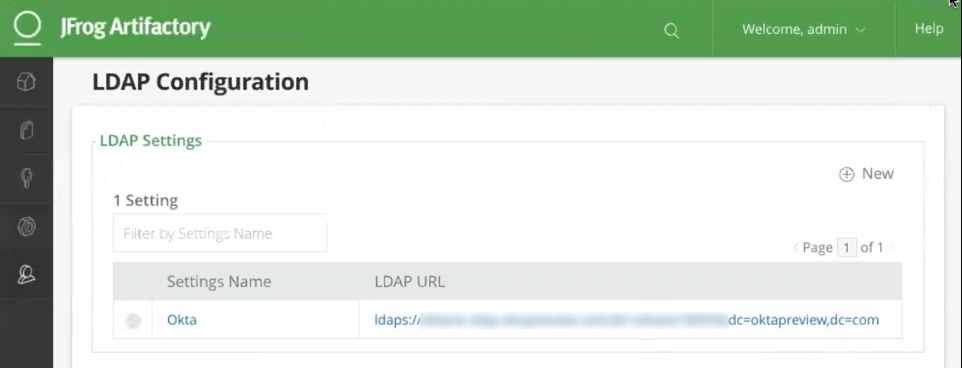
From the Artifactory side, the LDAP configuration appears like any other LDAP server such as AD, Sun One, OpenDJ, or Oracle Internet Directory.
However, as shown below, when users sign in, Okta holds the LDAP connection until they approve the MFA prompt:

And here's how it appears when a user tries to access Artifactory with the LDAP interface and MFA:
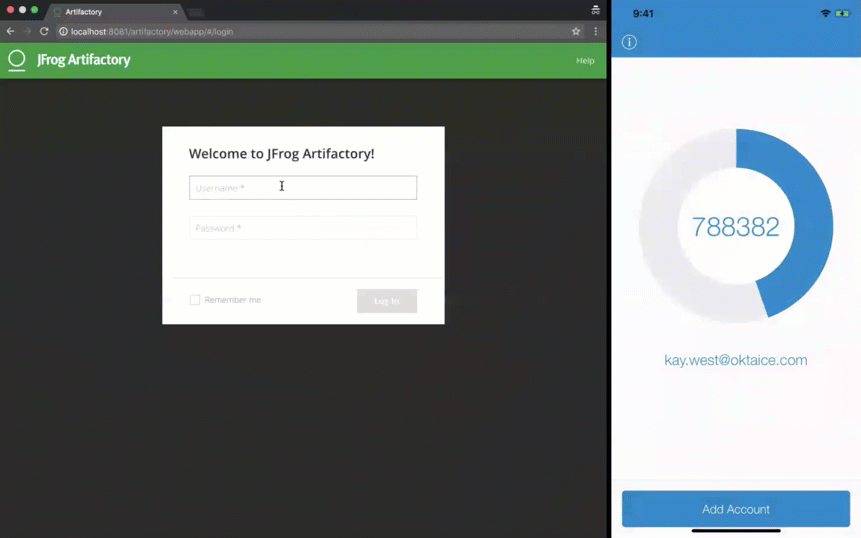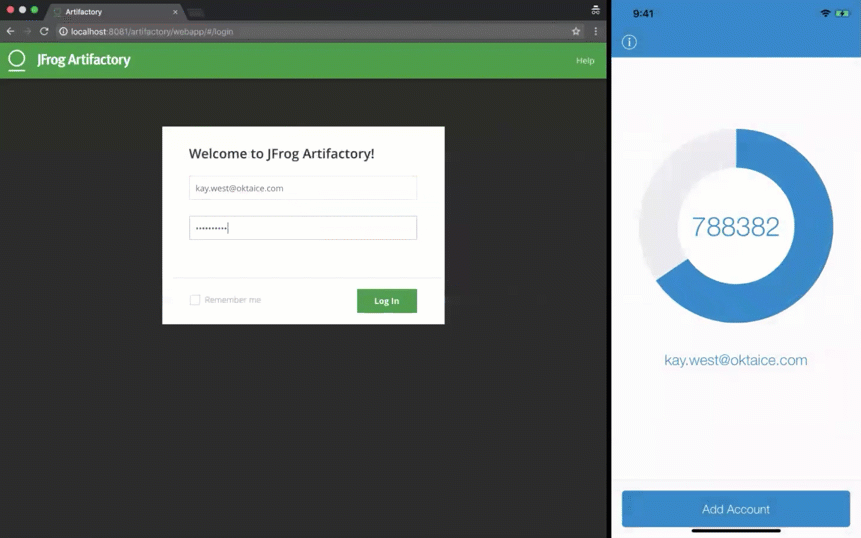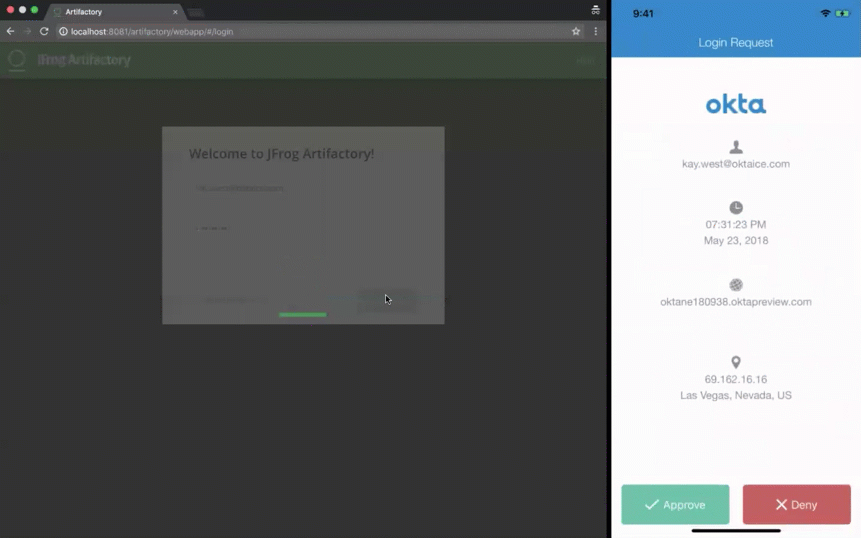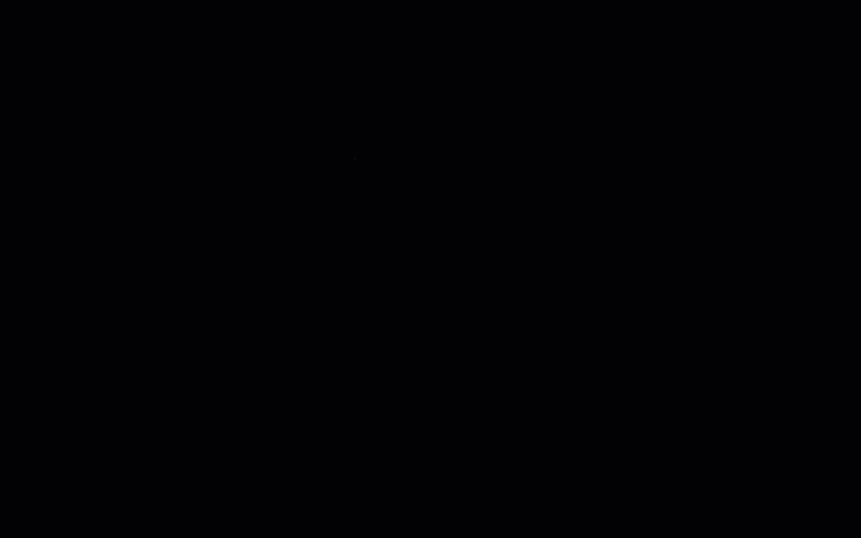
What’s unique about Artifactory is that it also supports access via CLI (command-line interface) using commands such as mvn, gradle, npm, and wget. To prove that the LDAP interface works, I tried the same flow using the wget command to Artifactory:
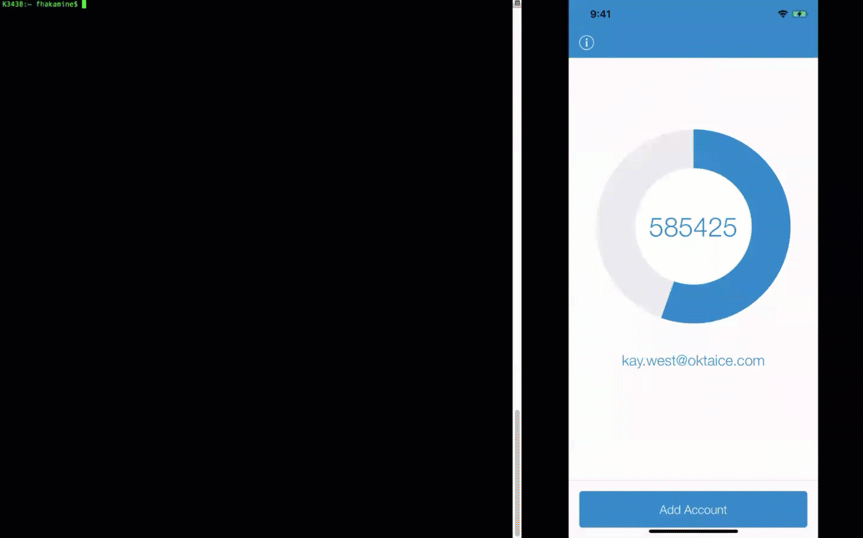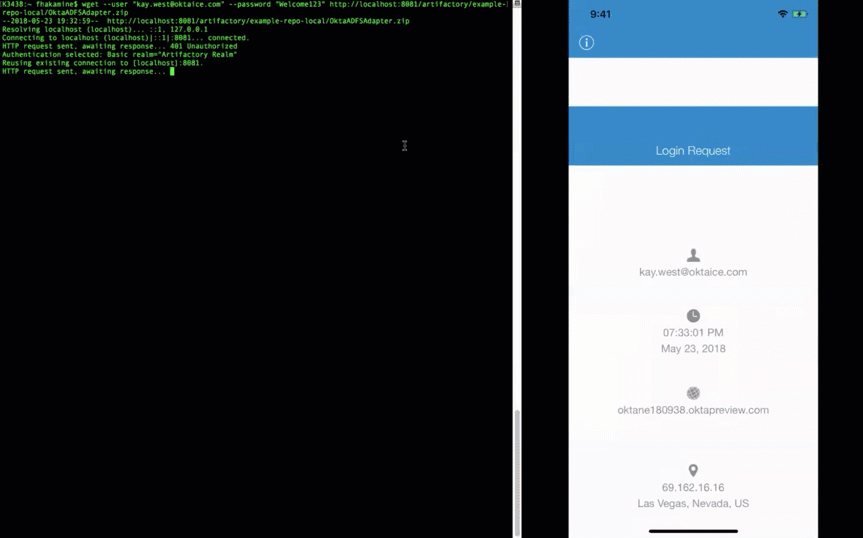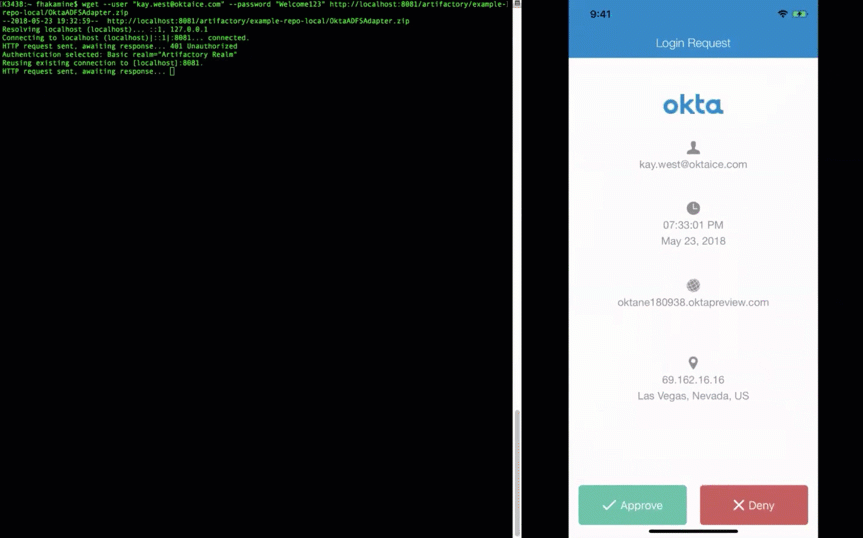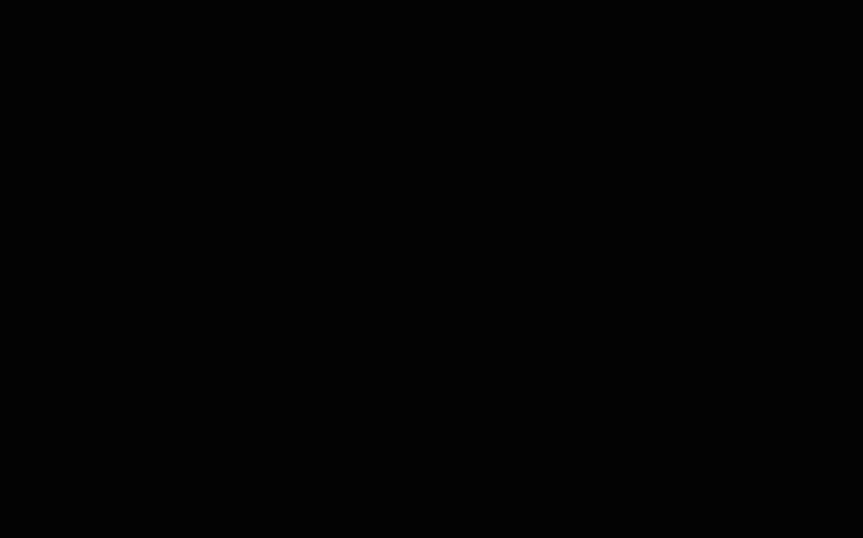
The integration works the same way any other app that uses LDAP for authentication (lightbulb moment…!).
Is MFA the only security measure on Okta's LDAP interface?
No. Okta implements additional security mechanisms on the LDAP interface,including
- Read-only access for admins
- Admins never read passwords—not even hashed values
- Use of TLSv1.2 for encryption
Excited? Let's use the LDAP interface!
If you're already an Okta customer and using Universal Directory, check out our new feature video and start using it.
If you're not an Okta customer yet, talk to us. We can show you how the LDAP interface can help you deploy a hybrid cloud or hybrid IT strategy, get compliant with PCI-DSS and other regulations, and successfully implement a zero trust strategy.

