A Path to Achieving Network Security ZEN
As new philosophies around network security arise alongside ongoing technological advances, forward-thinking companies are changing the way users interact with—and feel about—network security as part of their work day.
People are the new perimeter
Up until recently, network security relied upon a network perimeter—anything inside the perimeter was considered trusted and anything beyond it was considered untrusted. This approach has become increasingly problematic. With the influx of mobile and cloud applications changing the way we work and access data, the traditional perimeter has been dissolved—it’s no longer safe for enterprises to assume trust.
What followed was an approach that no longer assumed security, making people the new perimeter and establishing identity as the lynchpin of a secure strategy. One framework for this mentality is Zero Trust, which assumes that we can no longer have a network perimeter-centric view of security. However, when put into practice, users often resorted to weak password practices, leaving their organizations vulnerable to phishing attacks and data breaches. In this new world, hackers don’t break in. They log in.
There has to be a better way.
Adobe paves the way with ZEN
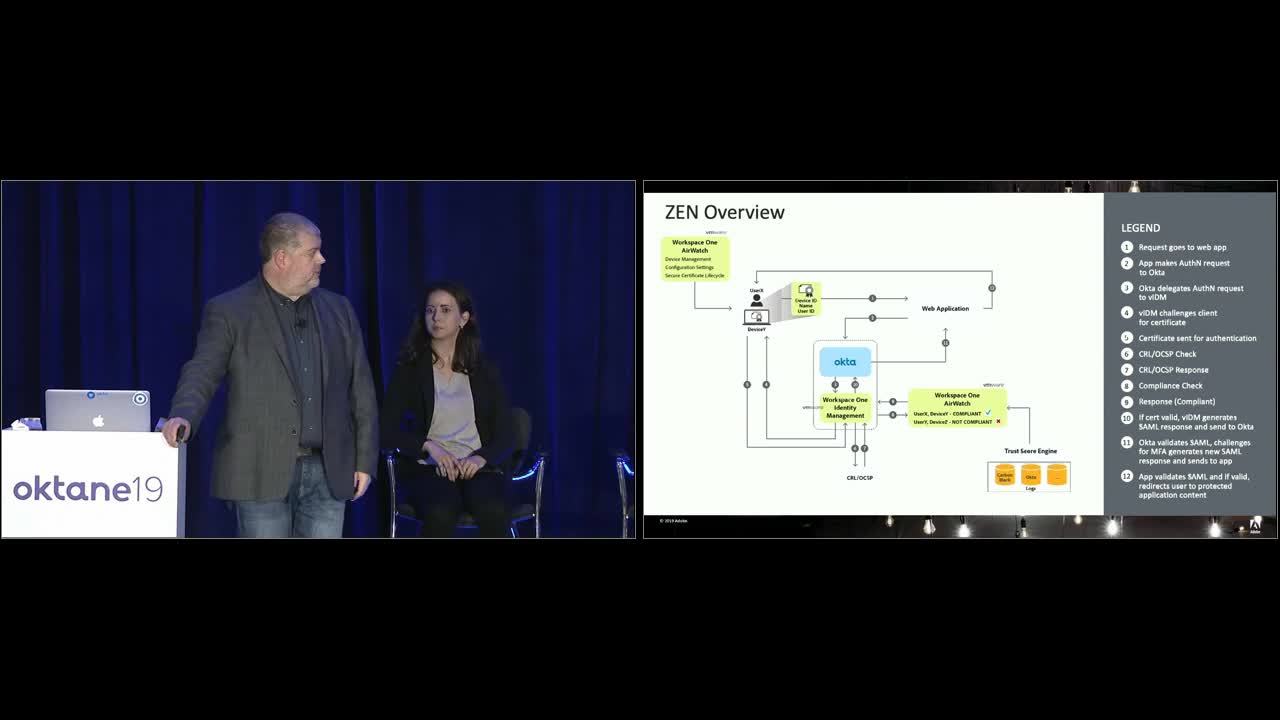
Adobe leaders recognize that Zero Trust is the way of the future, and enlisted Okta and VMware to help them move away from VPN-dependant operations and toward cloud solutions. They called this project ZEN (Zero-Trust Enterprise Network) and it has become an example of best-in-class security combined with best-in-class user experience.
ZEN leverages contextual access management to verify user identity—whether it’s on prem or via regular application authentication. This new approach meant 16,000 people no longer had to update their passwords every 90 days, and 46,000 hours of employee frustration were recovered.
Along with contextual access management, Adobe developed a trust score engine to analyze behavior across different types of apps and feed information back to VMware to help define and set compliance flags. Each user is also given a trust score, which can increase or decrease over time. When users opt out of security measures, for instance—which they’re empowered to do so via a device management portal—their trust scores are affected.
In this framework, peers can see each others’ trust scores, and management can access aggregated scores, allowing them to compare scores between teams. This approach encourages accountability, and puts security back in the hands of individual users.
A worthy investment
By reducing friction for their users while simultaneously bolstering security, Adobe has achieved something many companies only dream of. Their novel approach to network security means they have employees proactively reaching out to IT to become ZEN-enabled.
To learn more about Zero Trust environments and how identity sits at their core, read Okta’s whitepaper on the subject: Getting Started with Zero Trust: Never trust, always verify.

