Beyond Your Borders: How to Securely Work with Your Partners and Contractors
Not too long ago, most—if not all—business operations were conducted on premises, behind the safety of a firewall, and on devices managed by the company. Though it may not have seemed like it back then, those were simpler times.
Today, it’s common for modern enterprises to work with a variety of users from outside the network. These users are known broadly as the extended enterprise.
Although a robust extended enterprise can be critical in empowering organizations to scale their operations, it also poses myriad risks and challenges.
The extended enterprise and its challenges
Members of the extended enterprise might include users such as distributors, resellers, contractors, temp workers, and partners. As such, they either operate outside your network—coming in from unknown devices and locations—or they operate inside your network temporarily.
To do their jobs effectively, these users require selective and sometimes time-limited access to some of your sensitive information. However, this brings up many challenges for IT:
- Integration complexity. Connecting third-parties to your internal resources can be technically challenging—in particular, if you’re trying to connect old tech to new.
- Increased IT support. Providing personalized access—not to mention ongoing support—to these partners and contractors can place a huge strain on your IT team.
- New security risks. New users with new use cases from new devices and locations inevitably bring new security risks.
5 customer questions IT must solve for
These three challenges help frame the problem at a broad level, but our customers are more concerned about getting answers to the following questions.
1. How do I connect to partner identity sources?
Working with partner identities can be tricky business—you neither want to add them to your Active Directory (AD) and manage their profiles and lifecycles, nor do you want to pass a CSV file back and forth. Instead, Okta recommends connecting to a partner’s Identity Provider (IdP) via Federation. If a partner doesn’t have an IdP, they can rely on Okta to be one.
2. How do I provide secure and selective access?
Providing your extended enterprise with access is key, but it needs to be both easy and secure. Okta Single Sign-On (SSO) combined with Multi-Factor Authentication (MFA) is a simple and highly secure mechanism for granting employees as well as contractors, partners, and temp workers access to the tools they need. They can access SSO through any internet connected device, anywhere in the world.
Okta looks beyond just usernames and passwords to also consider user behaviour, where they are, what app they’re trying to access, and what network and device type they’re using to make a contextual decision on whether to grant or deny access, or whether to prompt an authentication factor.
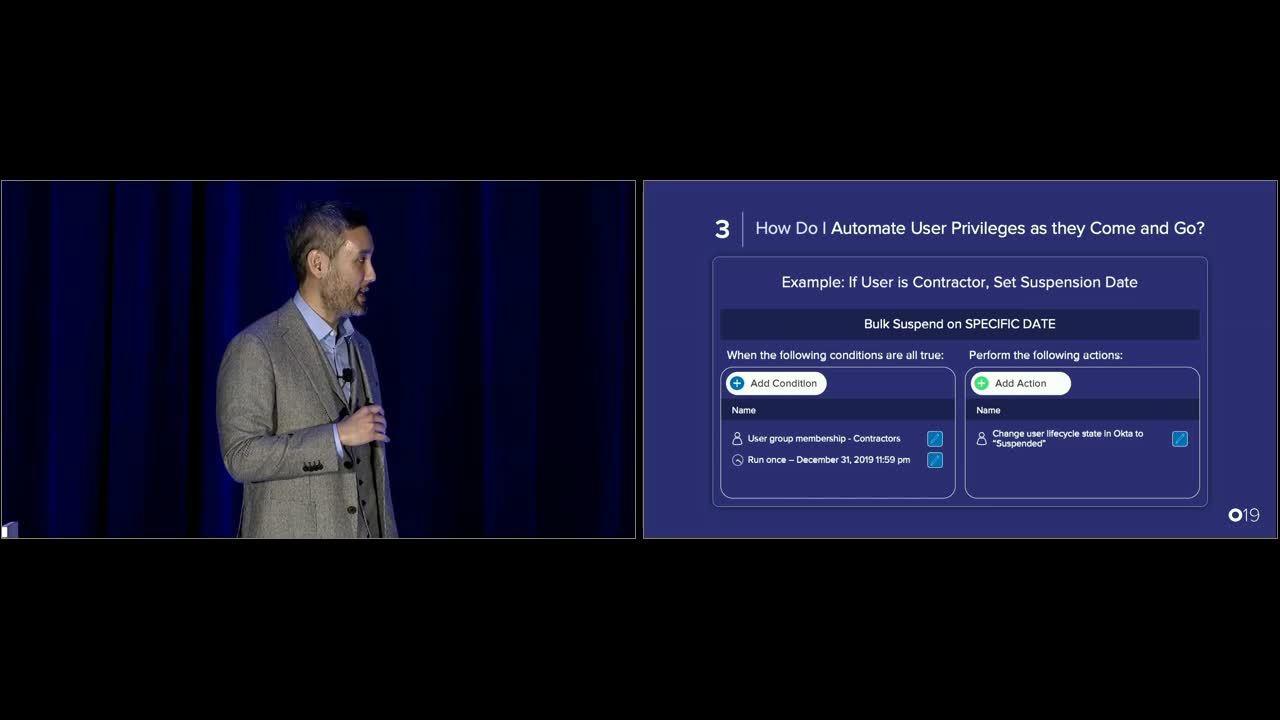
3. How do I automate user privileges as they come and go?
Because temp workers and contractors are short-term employees by definition, organizations need to ensure they get access to the resources they need from day one.
Doing this manually is a time-consuming and error-prone approach for IT—Okta Lifecycle Management offers a streamlined solution. Through a centralized policy, Okta automatically ingests user information from the source and then pushes it to ensure the user is properly assigned to the right resources every time.
4. How do I validate proper compliance?
In today’s regulatory environment, you may be required to prove compliance to an auditor at a moment’s notice. But a wide extended enterprise means the people who have access to your systems is constantly in flux, which can result in stale accounts. Okta offers several reports to provide real-time visibility into your IT environment so you know who is accessing what and whether they should be doing so.
5. How do I offload management of partner users?
Enterprises don’t want to clog up their IT help desk managing partner users. IT want self-service tools that will allow users to manage simple account related issues themselves. Okta offers several including password resets, account lockouts, and MFA enrollment.
Beyond that, IT want to empower other admins to do basic admin tasks. Okta has several tools to help, including predefined admin roles that easily delegate admin tasks to others, including partners, without giving full admin rights.
A customer in Christmas crisis
Dick’s Sporting Goods—the largest omni-channel sporting goods retailer in the US—has a seasonal workforce that relies on outside contractors.
During the winter holiday months, the organization grows from four customer call centers to nine. As a result, it’s IT team needs to onboard all new agents in less than a month, and deprovision them in half that time after the holidays.
This manual onboarding required an additional 1.5 full-time employees, prompting the organization to look for a more efficient and affordable way to grant new teammates the tools they needed to succeed. Okta’s hub and spoke approach provided the solution they were looking for.
Since implementing Okta, the company has significantly reduced its licensing costs and sped up their holiday ramp-up time.
Learn more
To learn more about how Okta can help enable and protect access for your partner and contractor users, check out our webinar, Secure, Simplified Access for your Extended Enterprise, view the Oktane19 video session below, or contact us directly.