Prevent Large-Scale Identity Attacks with Okta ThreatInsight
In today’s tech landscape, the importance of securing user logins has become a no-brainer. We’re constantly seeing reports of data breaches as a result of identity attacks, and we know those threat actors aren’t going anywhere. According to the 2018 Verizon Data Breach Investigation Report, stolen credentials are still the #1 culprit in confirmed breaches across all industries. And, 68% of breaches took months or longer to discover. This proves that we shouldn’t be taking a “roll the dice” approach to security. But, there’s good news!
To stay ahead of data breaches, organizations are continuing to adopt multi-factor authentication as an authorization requirement to all resources. This is excellent, and you should keep doing this! That said, we know that securing access to the cloud is a shared responsibility between Okta and all of you, and we want to make that responsibility as easy as possible for all of our customers.
To that end, we’re incredibly excited to announce the availability of Okta *ThreatInsight for all Okta customers! Let’s go through the specifics of what ThreatInsight is, and how you can use it to secure your organization.
What ThreatInsight means for your org
Okta believes it’s critical to secure access to your apps and infrastructure at all steps in the login process — at the router level, service layer, pre-auth, and post-auth.
Malicious IPs are blacklisted
At the router level, our amazing security team here at Okta does a great job of identifying malicious IP addresses causing identity attacks on multiple Okta orgs, or hundreds of users within one Okta org. These IPs are blacklisted, and on top of that, we have rate limits in place so as to not lock admins and users out of their org altogether in the case of a DDoS attempt.
Make informed IP blocking decisions
For every malicious login event captured by our service, we see many more suspicious events coming from IP addresses that we can’t confirm to be malicious with 100% certainty. There could be a legitimate use case for multiple failed logins depending on the scenario, such as when a hotel hosts a large conference.
In this scenario, it isn’t unreasonable to have dozens or even hundreds of login failures across multiple accounts in multiple Okta orgs, all of which appear to come from the same source (the hotel’s network). Blocking those IP addresses could actually block legitimate authentication attempts, which would ultimately be just as bad as falling victim to a DDoS attack.
With ThreatInsight, customers can take advantage of the global network intelligence captured by Okta’s network effect. When Okta sees large-scale identity attacks like DDoS, password spraying, high rate of login failure etc., those IPs are added to the ThreatInsight pool, and customers can choose to block access from those IP addresses. Essentially, Okta ThreatInsight allows you to secure your business before you’re the victim of an identity attack.
Audit suspicious IP addresses with Okta’s Syslog
We know that flat-out blocking IPs isn’t always realistic, so we’ve also given administrators the option to just audit suspicious IP addresses via Okta’s Syslog. And just like any other Okta event, ThreatInsight events can be pushed to any tool that can query the Syslog API.
Prevent account lockouts
Not only does Okta ThreatInsight help to protect against account takeover, but it also helps to prevent account lockout since it is evaluated pre-authentication. If we see the login request coming from a suspicious IP, we will immediately end the login process, thereby preventing an account lockout. We hear many customers ask us about best practices for preventing account lockout due to attacks on Office 365 legacy endpoints. While Okta ThreatInsight is not a silver bullet in stopping these attacks, ThreatInsight does also evaluate logins via Office 365 legacy endpoint (WS-Fed), and can help to prevent password spray attacks on this endpoint.
I’m sold, how do I enable Okta ThreatInsight for my org?
Okta ThreatInsight is available for all Okta customers. You’ll see the option to enable it on your org over the next couple of weeks. Follow these steps to setup ThreatInsight for your org:
1. Contact Okta’s support team to have the feature enabled on your org.
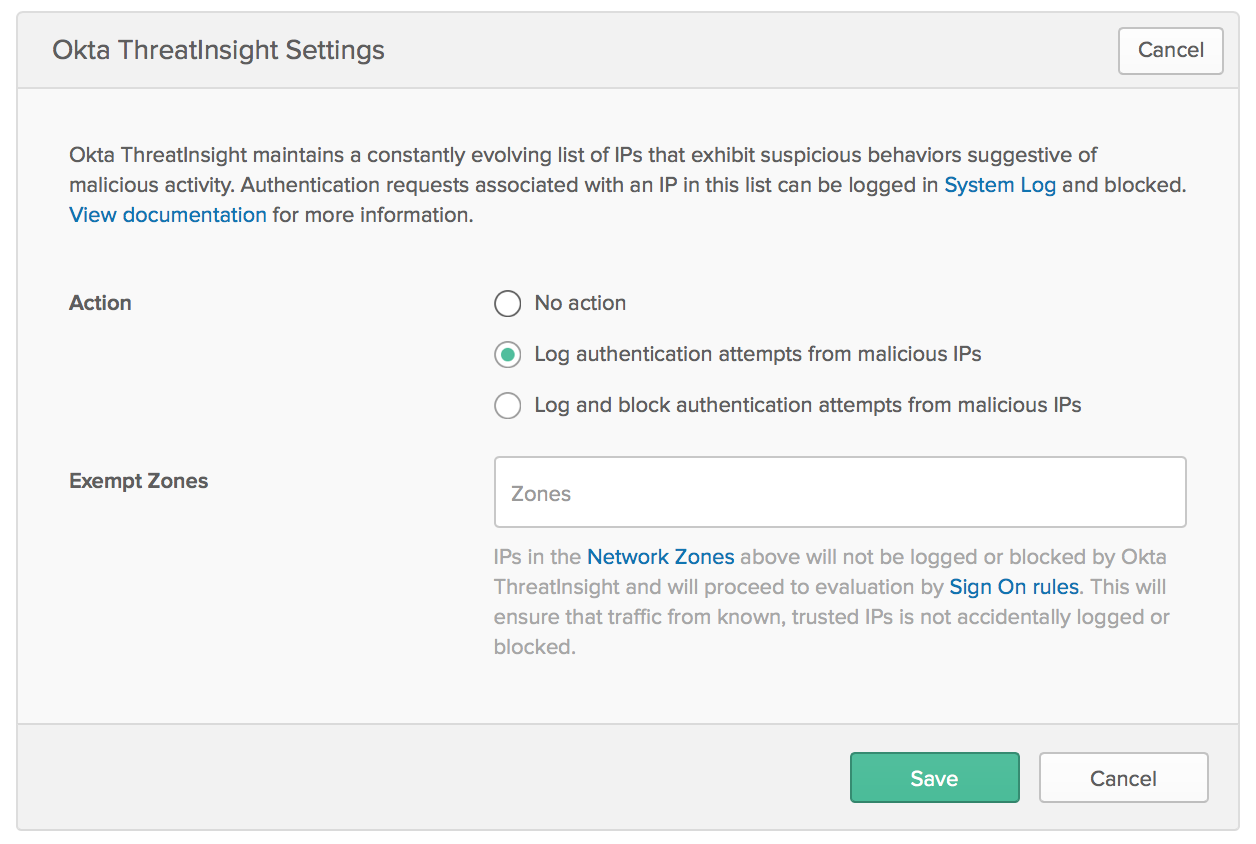
2. Once the feature has been enabled on your org, you can choose the mode in which you want Okta ThreatInsight to operate. Under Security - General, you will see a new section for Okta ThreatInsight Settings with the following choices:
- No action - Okta ThreatInsight will not check for any suspicious IPs.
- Log authentication attempts from malicious IPs - only audit suspicious IPs in Syslog, but do not block access from these IPs
- Log and block authentication attempts from malicious IPs - audit and block access from suspicious IPs
You’ll also see an option to exempt certain IP addresses from ThreatInsight. Using the
Syslog entry for ThreatInsight, you can identity IPs that are being logged, and add those to the exempt zone if needed.
And that’s it! You’re all set with Okta ThreatInsight.
We’d love to hear your feedback on Okta ThreatInsight as we start rolling it out to customers. And, if you want to learn more about all the controls Okta has in place to secure your logins, check out the blog here.
*Okta ThreatInsight is just one tool in the security toolbox. It cannot guarantee 100% malicious IP address detection or 100% threat detection. Okta ThreatInsight covers and blocks certain malicious traffic to the following endpoints – api/v1/authn, app/office365/{key}/sso/wsfed/active, and wsfed/passive. Please note, per our Master Subscription Agreement, endpoints are considered Free Trial Services.

