Assessing Where Your Organization Lies on the Zero Trust Maturity Curve
Most of us are now familiar with the term “Zero Trust”, seeing it emblazoned on many a booth and bus at security conferences throughout the year. The term has certainly reached buzzword status, and with good reason: today, security leaders recognize more than ever the need to move away from a perimeter-oriented approach to security.
But putting a modern, Zero Trust security model into practice is easier said than done. Where do I begin? What if I don’t have the resources to completely rethink my strategy? How do I go from zero, to Zero Trust?
Step 1: Stop hackers from logging in
Cloud and mobile have served as the catalyst for the meteoric rise of Zero Trust over the past few years. With more people, accessing more resources, from more devices and locations than ever before, the only commonality today is that someone needs to access something – and our protections need to mirror these new controls. That’s why many organizations, such as AECOM, 21st Century Fox, and USA Today, are leveraging identity as the foundation for their Zero Trust strategy. (And while the foundation, we’d also note that identity not a silver bullet for a holistic Zero Trust strategy. More on that later.)
If that wasn’t reason enough, Verizon’s 2019 Data Breach Investigations Report found that more than 70% of hacking-related breaches were caused by stolen credentials. Today, threat actors don’t have to hack in – they can just log in. Why not spend time and resources on closing this major – and more easily solvable – gap first?
Step 2: A test you’ll want to take
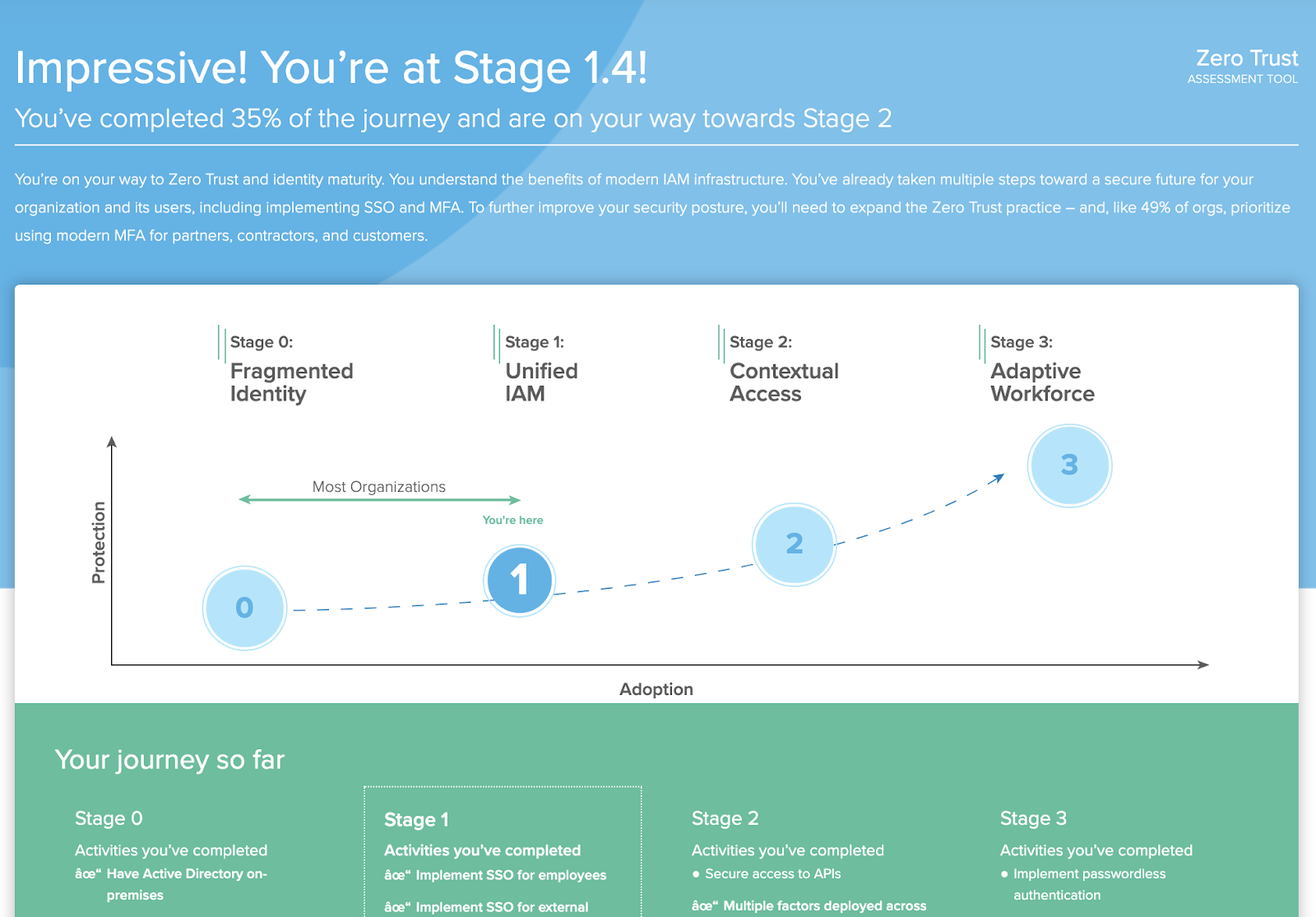
Ok, so you’re all-in on Zero Trust, and you’re ready to say yes to identity and access management as your foundation. What’s next?

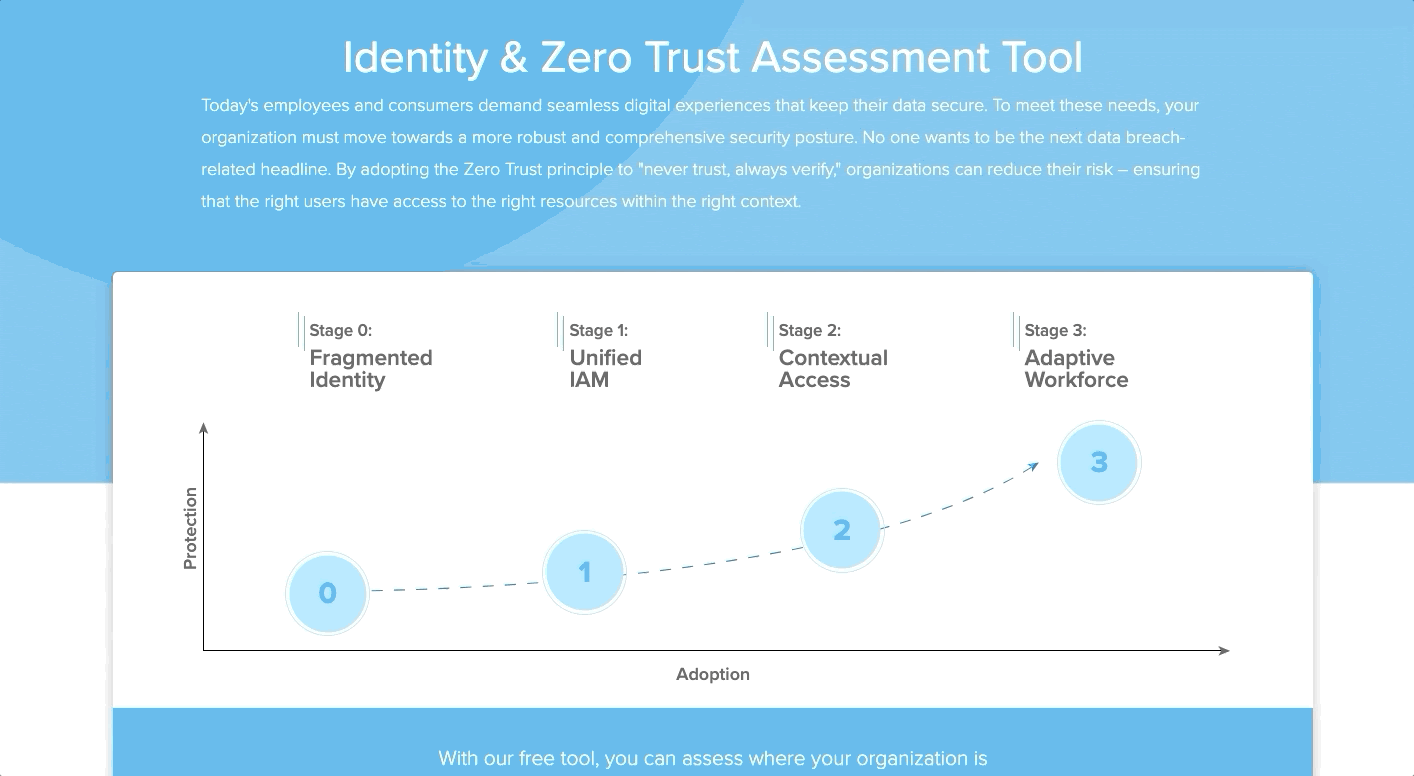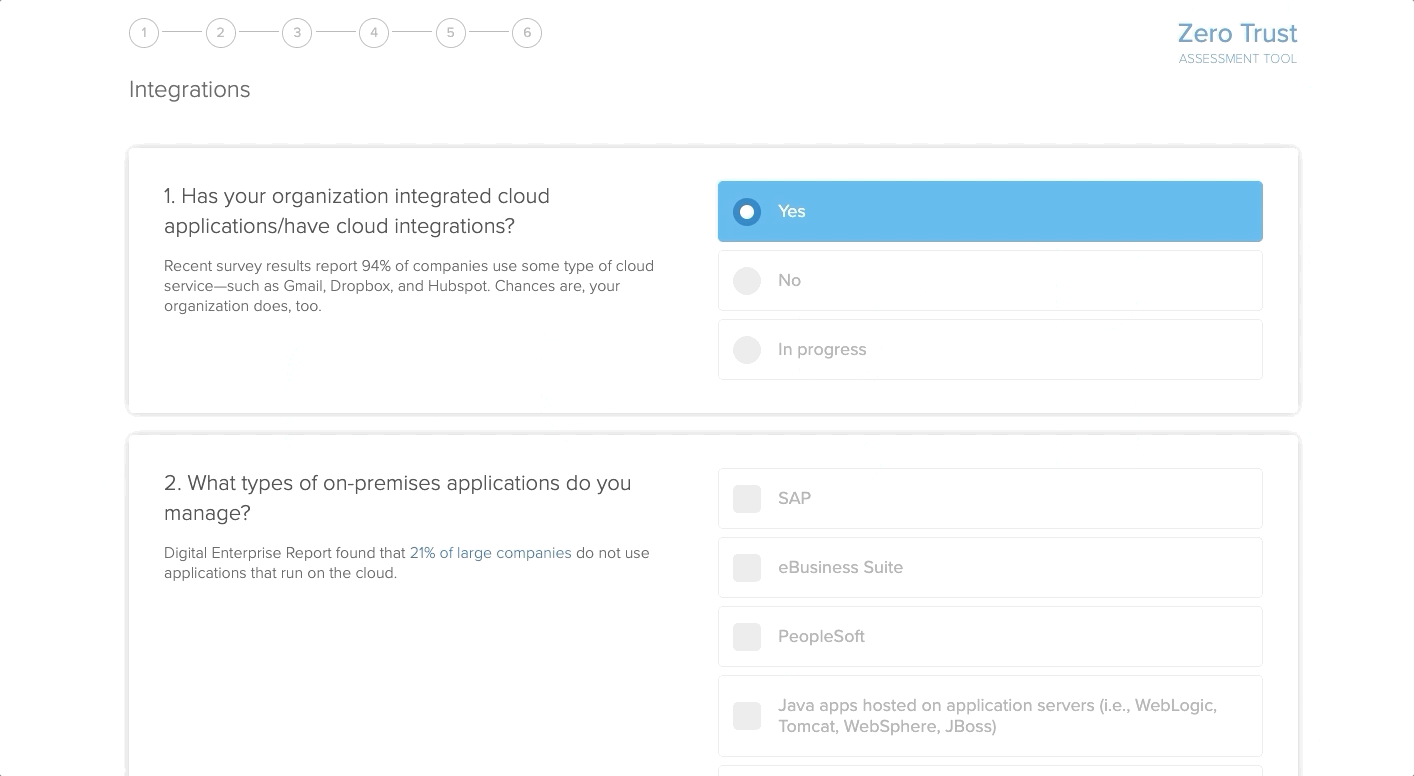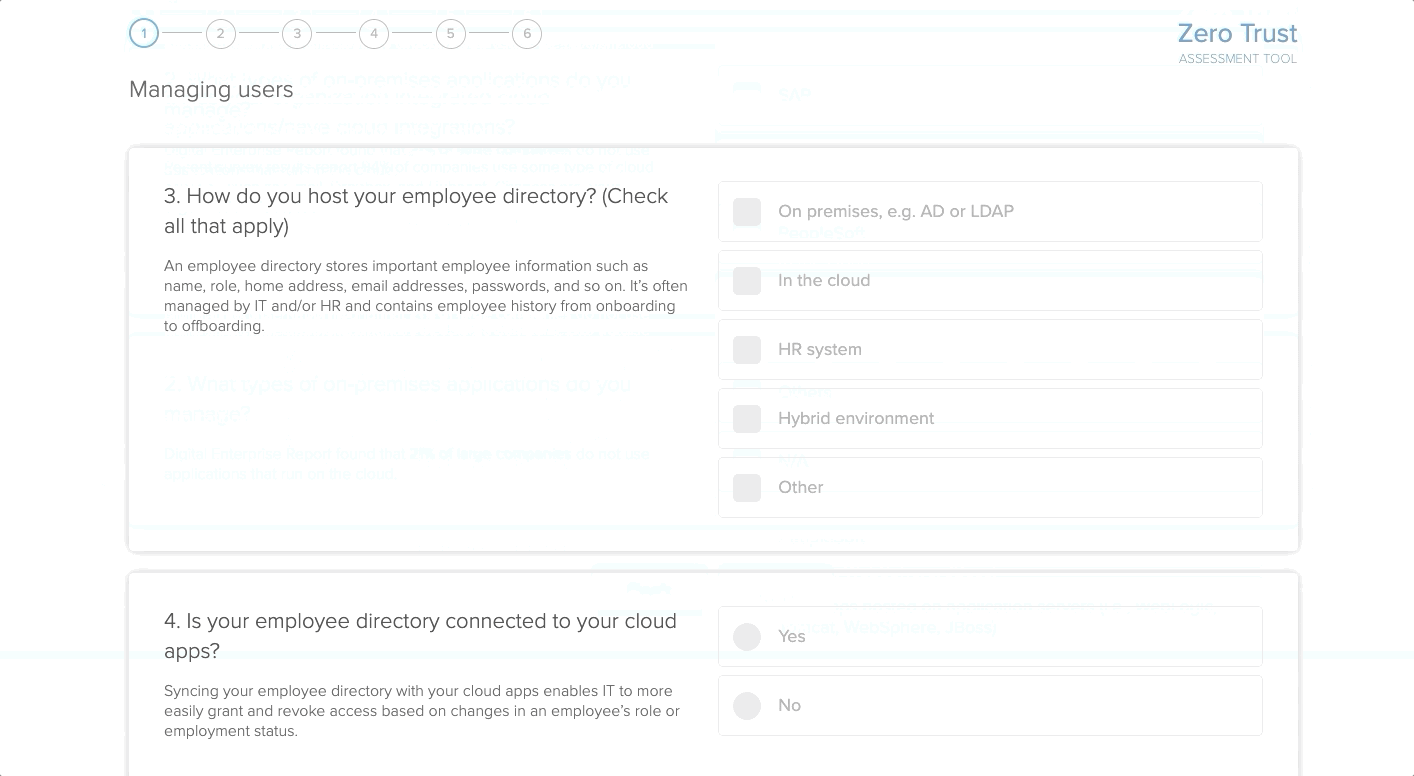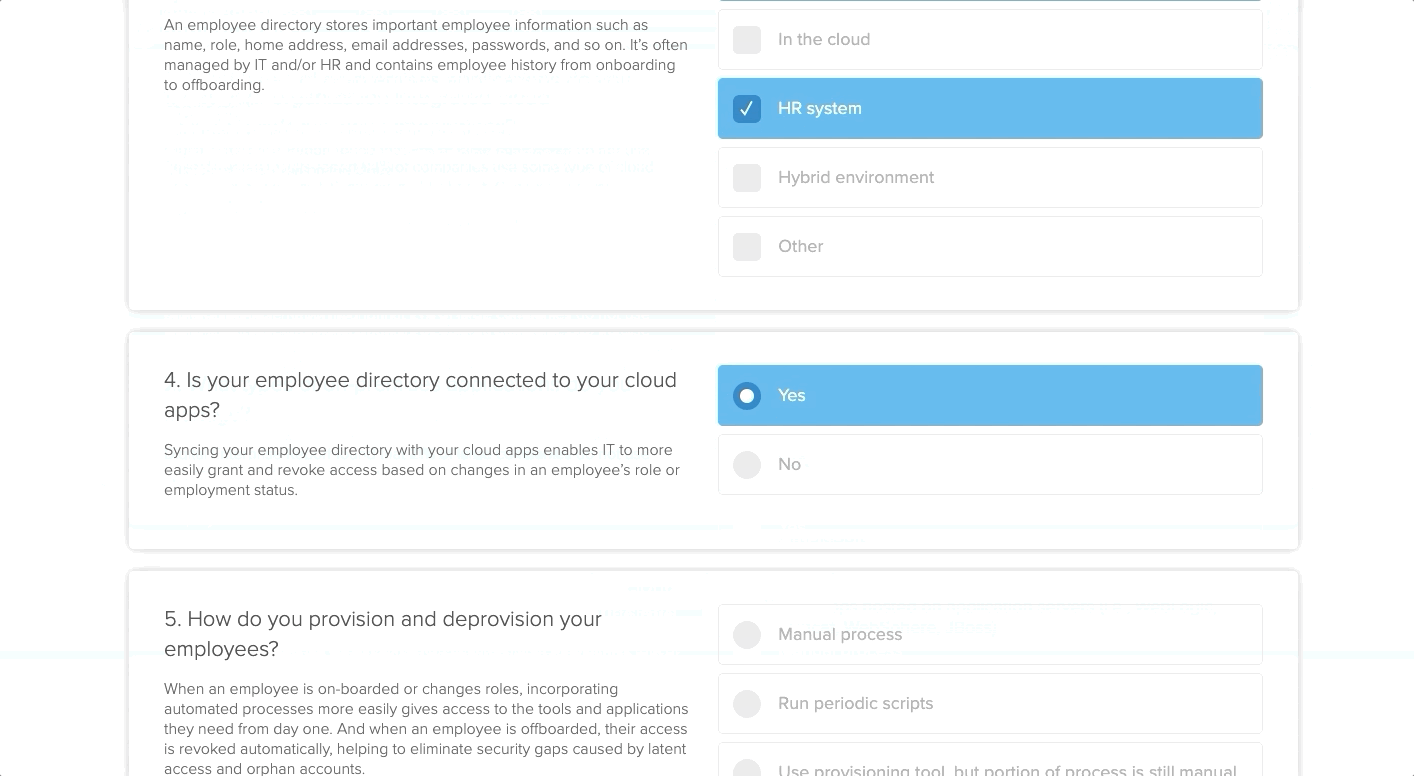
We’re now launching an Identity Zero Trust Assessment Tool to help organizations with the identity part of their Zero Trust strategy – giving them a prescriptive roadmap for putting Zero Trust identity and access controls in place. Based on Okta’s identity access and management (IAM) maturity curve, the assessment reviews organizations’ identity-driven security practices on everything from the type of resources they manage to how they provision and deprovision users. It also explores which authentication methods they deploy, the policies they have in place, and their future business priorities.
The results show respondents what projects they’ve completed, where there are opportunities to take action, and places them in the stage with the first project they’ve missed — all to ensure a thorough implementation (though we’ll still highlight projects you’ve completed further along the curve for reference!) For added context, the assessment also shares insights from other organizations going through their own implementation processes.
Step 3: Chart a course for Zero Trust
By using the Identity Zero Trust Assessment tool, our aim is to help organizations understand where they stand, where they need to get to, and offer recommendations on how to do so in a way that meets your organization’s requirements.
It also will surface recommendations for how identity and access management fits into the broader Zero Trust ecosystem – because there is no single solution that solves for all aspects of the Zero Trust framework (and if you’re looking for more insights, check out the latest full The Forrester Wave™: Zero Trust eXtended Ecosystem Platform Providers, Q4 2019).
Get started with the Identity & Zero Trust Assessment Tool and let us know what you think: we’re happy to review your results with you, share best practices, and help see how you can further strengthen your identity-driven security foundation if you have questions or would like more insight.
For more resources on how to get started or continue along your Zero Trust implementation, check out:
- Zero Trust in Practice (Webinar)
- Navigating your Identity and Access Management Journey - Blog
- The Maturity of Zero Trust Across Organizations - Data Infographic
- Getting Started with Zero Trust: Never trust, always verify - Whitepaper
- Okta Helps USA TODAY Network Maintain Security and Trust - Customer journey