How to Unlock Security Orchestration through Identity
Corporate data is a popular target for hackers, with over 9,600 breaches recorded between 2008-2019 in the U.S. alone. Not only are attacks growing in volume, but also in sophistication: A study by the Identity Theft Resource Center (ITRC) indicates that account takeovers increased by 79% between 2017 and 2018.
Devastating attacks like these can happen in the blink of an eye: It takes less than four minutes, on average, for an employee to click on the malicious attachment in a phishing email. So if your security team isn’t getting real-time contextual alerts–or if they’re overwhelmed by too many alerts to prioritize them–the risk of breach could be high.
It’s becoming harder and harder for security teams, who are often understaffed and trying to manage disparate tools across a complex infrastructure, to safeguard the enterprise against a high volume of increasingly sophisticated attacks.
In this post, we’ll break down how these breaches are occurring, why the risk is growing, and how to address these challenges through identity-driven orchestration between Okta and Demisto, a Palo Alto Networks Company.
The Threat Landscape Has Changed… And So Has Your Organization
Attackers are shifting away from attacking enterprise infrastructure directly, and instead are targeting users and their credentials to take over user accounts. Through credential-based attacks like phishing and formjacking, bad actors work to convince (or trick) users to hand over their usernames and passwords, and if successful, inadvertently grant them access to enterprise assets. Attackers are smart—why hack in when you can just log in?
From an organizational perspective, the rise of cloud and mobile technologies has caused enterprise users and data to reside outside of the traditional security perimeter. Identity is the new perimeter and organizations need to adjust their security strategies appropriately. Security teams that hope to combat the deluge of increasingly sophisticated credential-based attacks need to establish identity as a key security control point, and provide policy-driven access control that protects all users and every login attempt.
Only with identity at the center of its security strategy can an organization develop a strong, integrated threat response program that can help mitigate the high number of increasingly sophisticated attacks. Okta has partnered with Demisto, a Palo Networks company, to deliver strong, integrated threat response.
How Identity Powers Security Orchestration and Response
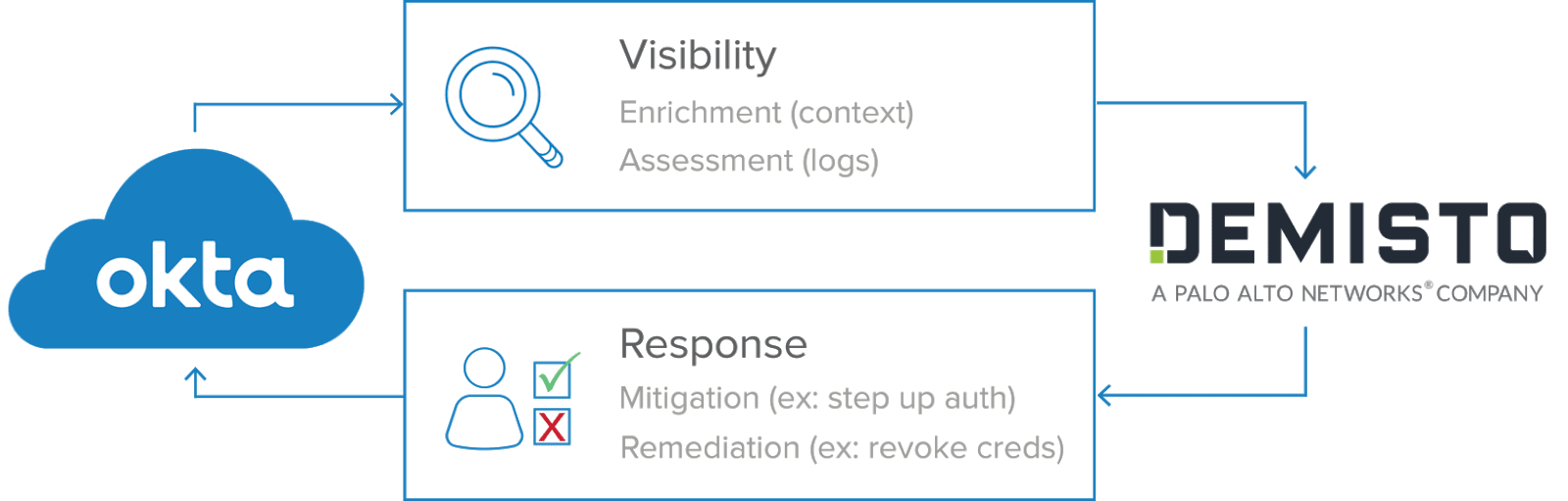
Okta integrates directly with Security Orchestration And Response (SOAR) solutions like Demisto to enable identity-based, automated response actions to help combat credential-based attacks. As each alert is generated, Demisto can automatically query Okta for relevant user activity as well as critical contextual information to help security teams identify suspicious activity. If the investigation suggests a user account has been compromised, RESTful API connections enable Okta to take automatic remediation actions to protect the user account directly from the Demisto console.
Automating this first line of defense across identity and incident response, rather than relying on manual human intervention, provides orchestrated security against threat actors and frees up security teams to tackle more complex tasks. Okta integrates directly with the tools security teams are already using to enable identity-centric actions within familiar dashboards, like Demisto’s War Room, rather than shuffle back and forth among multiple tools. Integrations like this make your security team more efficient and effective against more sophisticated attacks.
The Okta + Demisto Integration In Action
Here’s how Okta and Demisto work together to automate security response with identity as the security control point. RESTful API connections let Okta seamlessly provide Demisto with additional visibility into user activity, like failed login attempts, as well as identity context, like the groups a user belongs to and the applications they’re allowed to access.
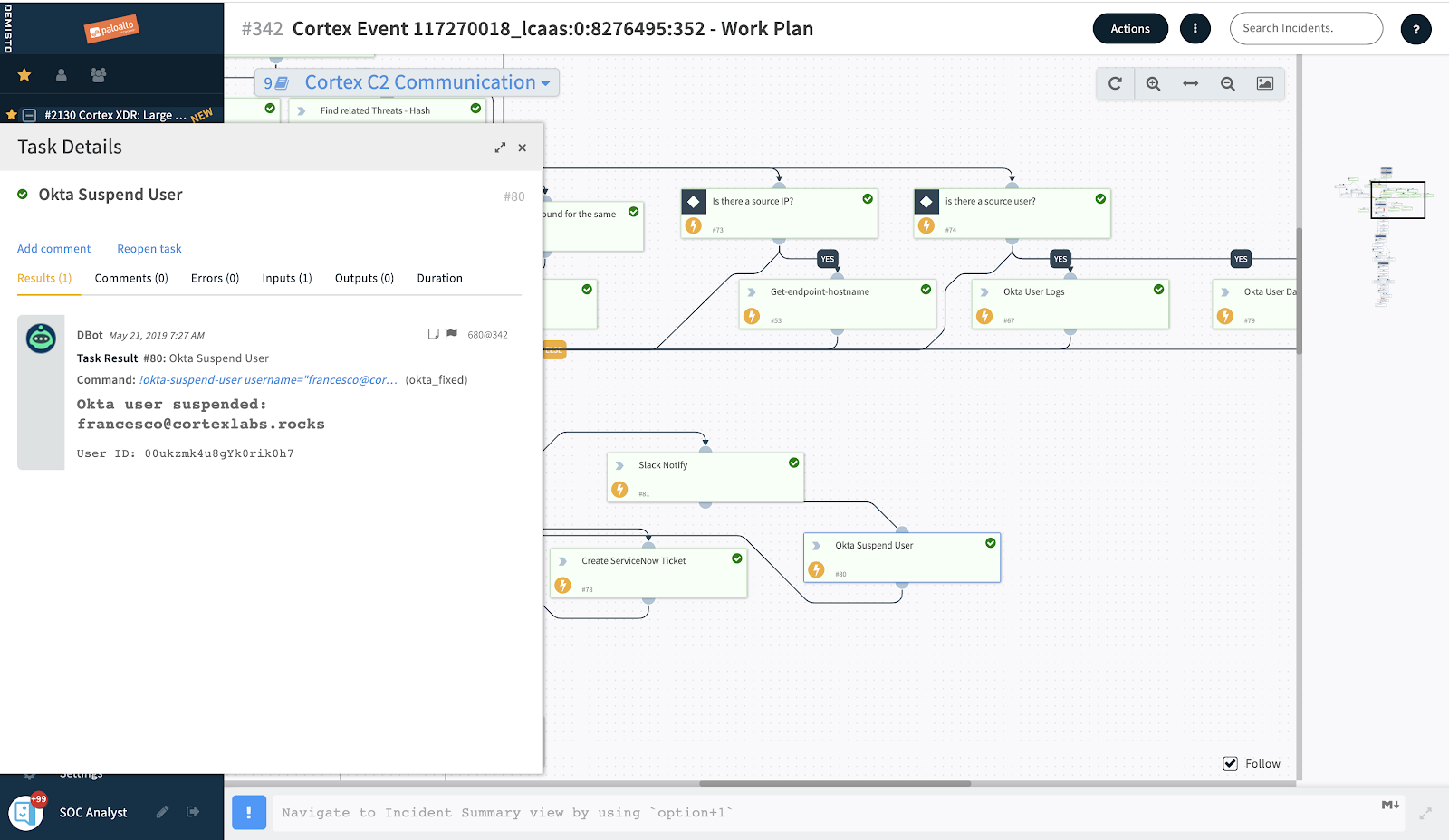
With this additional context from Okta, Demisto can orchestrate an informed identity-driven response to mitigate the threat, including prompting for step-up authentication, or even remediate the compromise, like forcing a password reset.
For instance, if a security team is alerted after multiple failed login attempts by one user, they can quickly and easily find out what groups this user belongs to and what sensitive applications and data they have access to — all in order to better understand the risk of the situation. If after further investigation the security team identifies more suspicious activity, they can enforce remediation actions, like prompting for Okta MFA to make sure the users are who they say they are, or even force a password reset when the user account is clearly compromised.
Okta’s rich identity data and strong user controls and Demisto’s powerful workflow engine work together to let enterprises confidently handle today’s high volume of sophisticated attacks, with automated, policy-driven response actions that enable identity as a key security control point.
Safeguard Against Credential-Based Threats: Deploy Identity-Driven, Automated Response
With threat actors increasingly targeting employees’ credentials and users and with data continuing to reside outside the physical boundaries of organizations with increased frequency, it’s time for security teams to shift their approach.
Use strong identity tools such as Okta to centralize access control across the enterprise, and protect sensitive data from attacks in real-time with automated response and remediation tools that counteract a wide variety of complex threats, while minimizing the strain on your security team.
Okta and Demisto help your enterprise stop hackers in their tracks with contextually informed, automated security response, empowering your teams to protect against the growing volume and increasing sophistication of today’s threat landscape.
Learn more
Get more information on how to secure your organization’s sprawling infrastructure from our whitepaper: Getting Started with Zero Trust: Never trust, always verify.