How to Enforce Least Privilege Access on Linux Servers Using Sudo
Security is and should be outcome-oriented. In that spirit, access management can be boiled down to a single phrase—ensuring that only the right people have the right levels of access to the right resources under the right conditions at the right time.
In a true Zero Trust world, granting access through the front door isn’t enough, you also need to be able to control and enforce what can be done once inside. This is where the principle of least privilege applies, only granting the minimum rights to perform specific functions. Unlike Chotchkie's from the movie Office Space, the bare minimum is actually encouraged here.
A common challenge with putting the principle of least privilege into practice lies in the enforcement—how can you ensure that what is written in policy is effectively adhered to in practice? I’ve often referred to this as the Adherence Gap. Thankfully for Linux systems, there is a native OS construct called sudo which makes this possible by controlling the allowed tasks local users can perform.
Managing sudo permissions is challenging, though, as it’s handled as a local file on each server. How can you ensure consistency across all of your servers? What happens if you need to make a change? These have never been easy questions to answer, and they only get harder at scale, leaving Sys Admins to write a lot of custom bash scripts just to try to stitch things together.
With Okta Advanced Server Access, IT and Security admins can now centrally manage sudo privileges across server fleets at any scale, automating the lifecycle of policy from end-to-end, tied to your Identity system of record.
Starting with role-based access controls
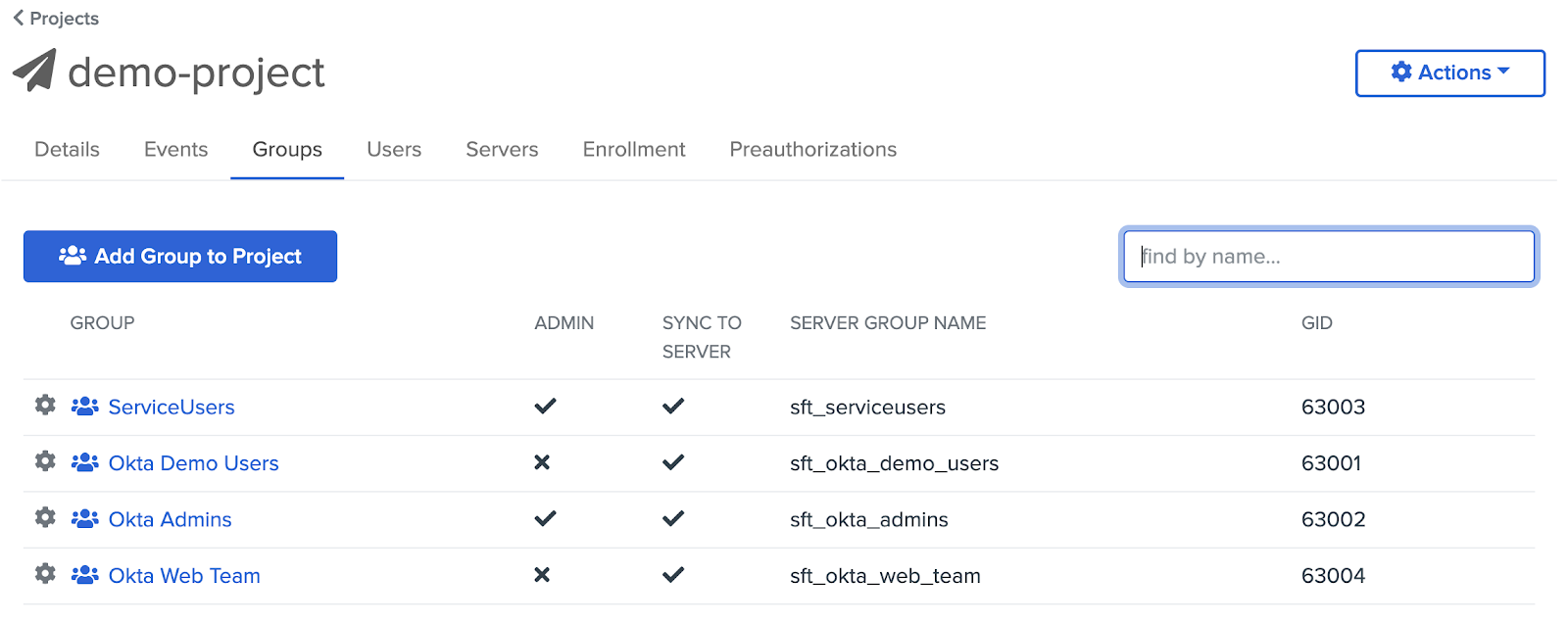
In Okta Advanced Server Access, role-based access controls are a function of the project structure—a project is the authorization scope that covers who can access which servers. The baseline mechanism for enabling sudo privileges is a function of the group assignment—i.e. members of the “admin” group are granted sudo privileges, while members of the “web” group are not. Group assignments are managed via the Advanced Server Access dashboard, and are reflected on the respective servers downstream as local accounts.
System-wide sudo management is a strong security feature in itself, but to truly adhere to the principle of least privilege, command-level sudo management is needed. This is where Okta Advanced Server Access takes it to the next level.
Introducing Sudo Entitlements Management for Linux
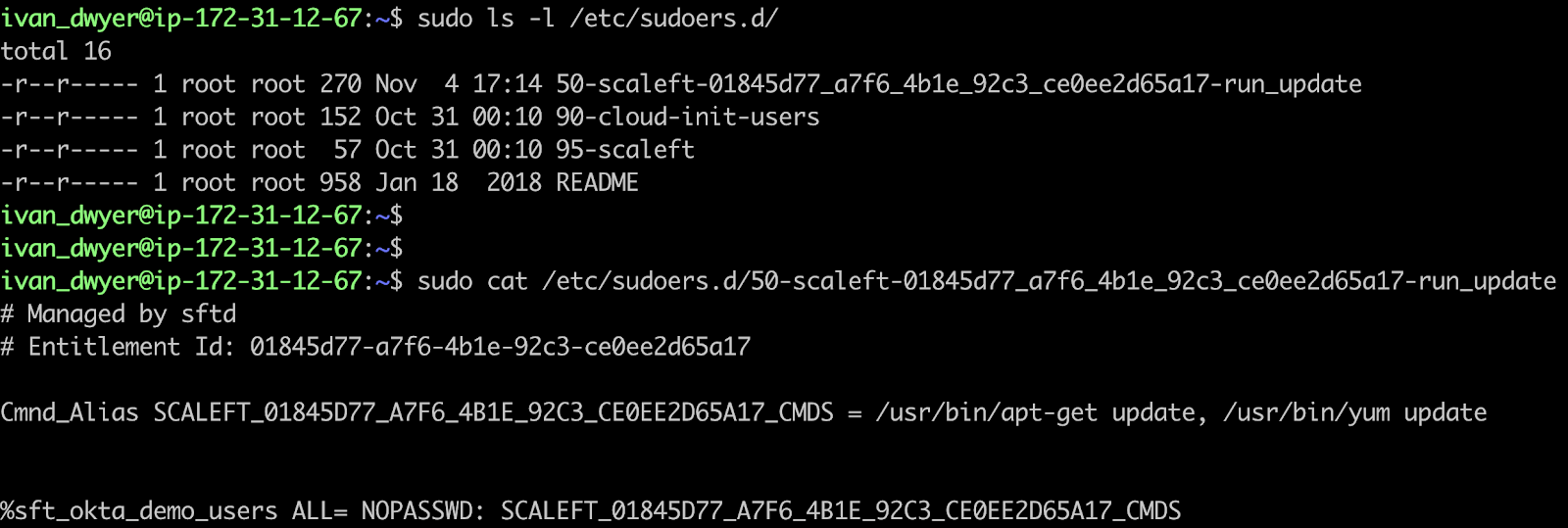
Each server that is enrolled with Okta runs a lightweight agent to manage the lifecycle of local user and group accounts. Expanding on this functionality, the server agent now manages command-level sudo permissions as individual drop-in files included in the primary /etc/sudoers file.
a
As it does with user and group accounts, the server agent periodically calls back to the Advanced Server Access API for any updates, and reflects the change locally, emitting an audit event for posterity. The power of this lifecycle management only compounds with scale—imagine being able to automatically provision consistent policy across hundreds, thousands, or tens of thousands of servers near instantly!
Administrators manage these policies within the Advanced Server Access dashboard, and when bound to a specific project group, get provisioned to every downstream server within a project.
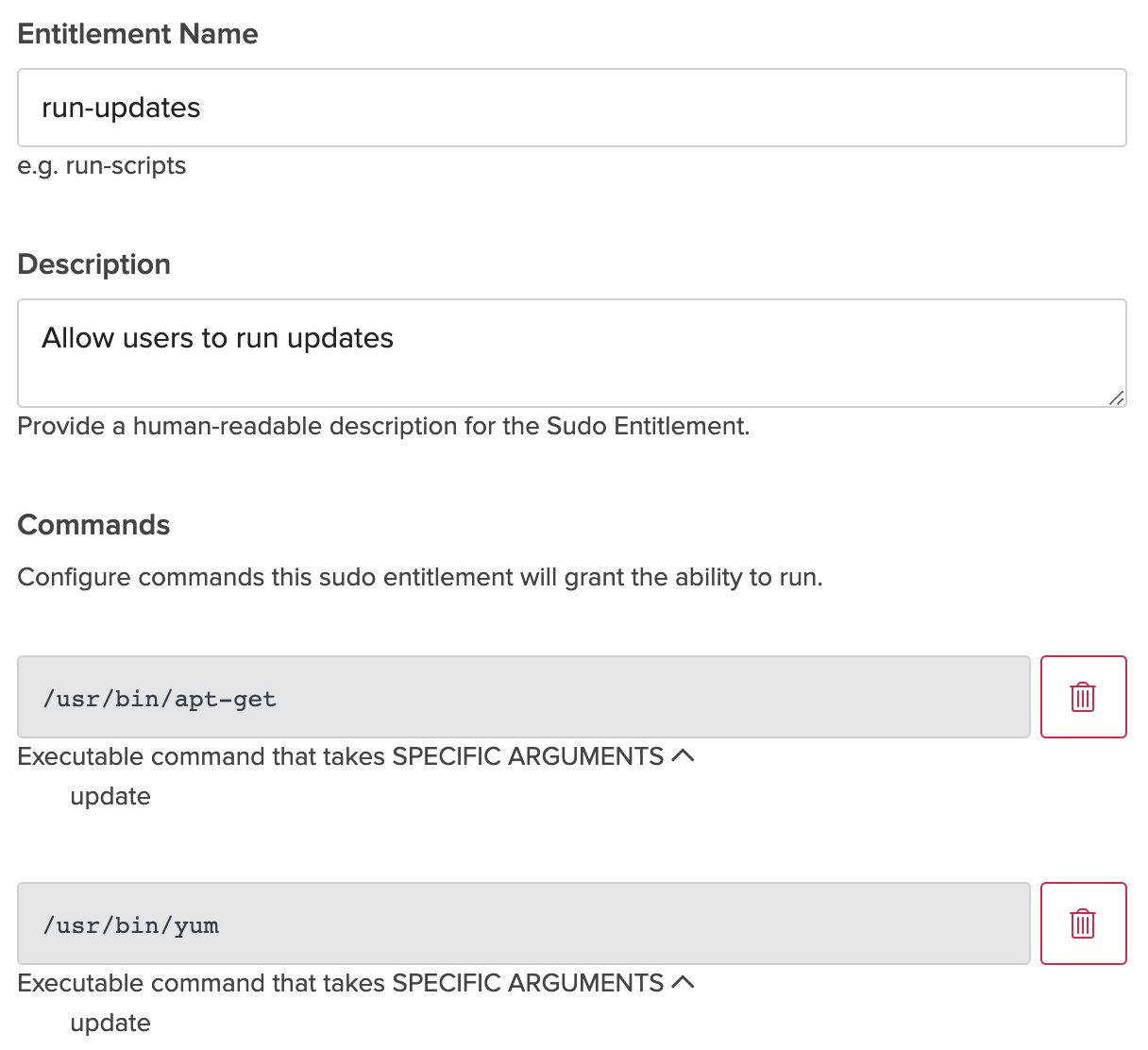
The following types of sudo entitlement commands are supported:
- Executable: The ability to run a service with optional parameters. Ex: sudo /usr/bin/apt-get update
- Directory: The ability to execute files in a protected directory. Ex: /usr/local/customscripts/*
- Raw: The ability to run a custom script or series of piped commands. Ex: echo ‘I Am Root’ | sudo tee > /usr/local/protectedfile
Example Entitlement view in the Advanced Server Access Dashboard
Example Entitlement as written on a server
The impact: Elegant enforcement of least privilege access
Sudo Entitlements Management for Linux gives IT and Security managers the flexibility to clearly specify who can perform what actions across which servers. Through a central management plane with end-to-end lifecycle management, you can ensure that least privilege access is effectively enforced across your most critical infrastructure resources.
As with every feature of Advanced Server Access, this was designed to work with native Linux constructs, meant for automation at scale. Managing policy is hard—Okta abstracts that complexity for sudo in a truly elegant manner, providing greater security assurances and productivity outcomes.
Get started with Sudo Entitlements Management for Linux
Sudo Entitlements Management for Linux is now generally available for all customers of Advanced Server Access. Click here to learn more about Advanced Server Access, or sign up for a free 30-day trial of ASA here.