The Secret Features of Okta Access Gateway: Part 5: Per-App Session Security
At Okta, we love to secure access to everything, from cloud apps, to consumer apps, to servers, and infrastructure—from a single platform. And that, of course, includes on-premises apps. In our new series The Secret Features of Okta Access Gateway, we’re going to explore some of the best secret features of Okta Access Gateway (OAG) to secure access to on-prem web apps, at scale.
OAG is a solution to secure access to on-prem web apps and the hybrid IT with Okta SSO and Adaptive MFA. If you want to learn the basics about OAG before diving in, click right here.
Each post in this 5-part series will be delivered by a specialist with strong experience using these secrets in the field. And to help you navigate through all the information, we’re framing the posts based on the following key areas:
In this post, we will explore OAG's Per-App Settings for individualized session management.
The Challenge: Setting granular security settings per application
Most organizations have multiple on-premises web applications with distinct security requirements. Critical software such as financial apps or apps subject to compliance, may have strict session timeout and logout policies, while other apps may have longer session times.
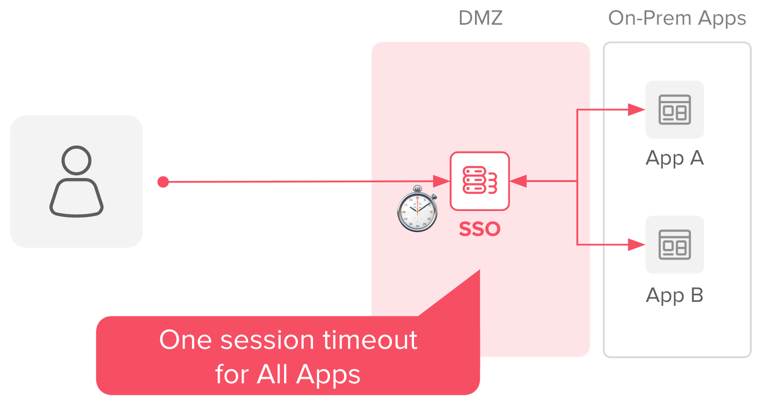
Providing individual session policies per app is a challenge for on-prem applications, mostly because traditional SSO solutions will apply a global cookie, and session, for all apps.
Most SSO on-prem solutions use a global session, and cookie, for all applications
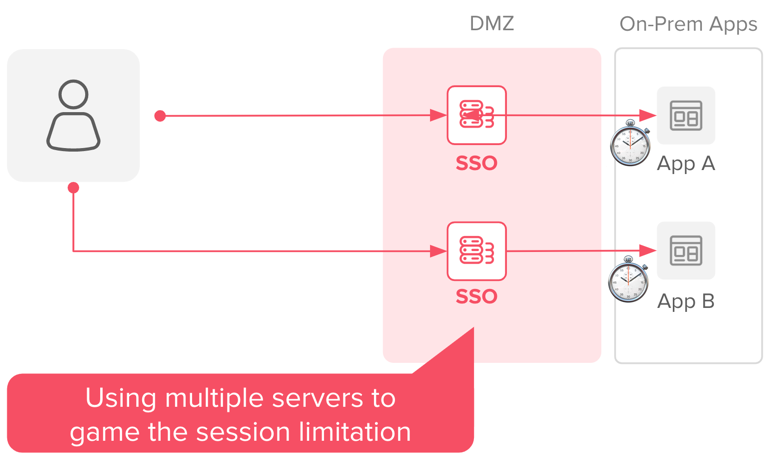
To overcome this challenge, many SSO solutions require either additional servers to establish sessions, or redundant policies to trick the cookie/session system. These approaches are expensive and complex.
Working around the session limitations with more SSO Servers
The Solution: Individualized cookies and native session management per app
To support individualized session timeouts per application without requiring additional servers or jerry rigs, Okta Access Gateway natively implements
- Individual cookies per application
- Per-app session management options
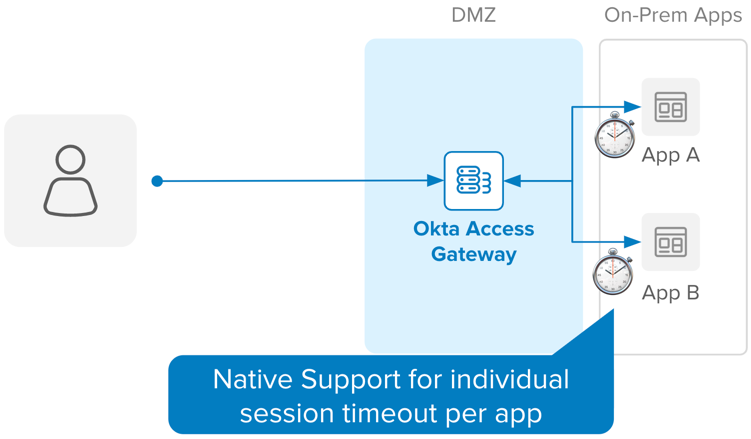
By combining these features, OAG provides true session management, per app. This means that, by the time the sessions are established, App A and App B are independent of each other. This allows you to configure idle and total/maximum session duration, within each application, defined within the OAG instance.
OAG uses individualized session settings, and cookies, per app
The session settings are defined in the Application page, under the Advanced section:
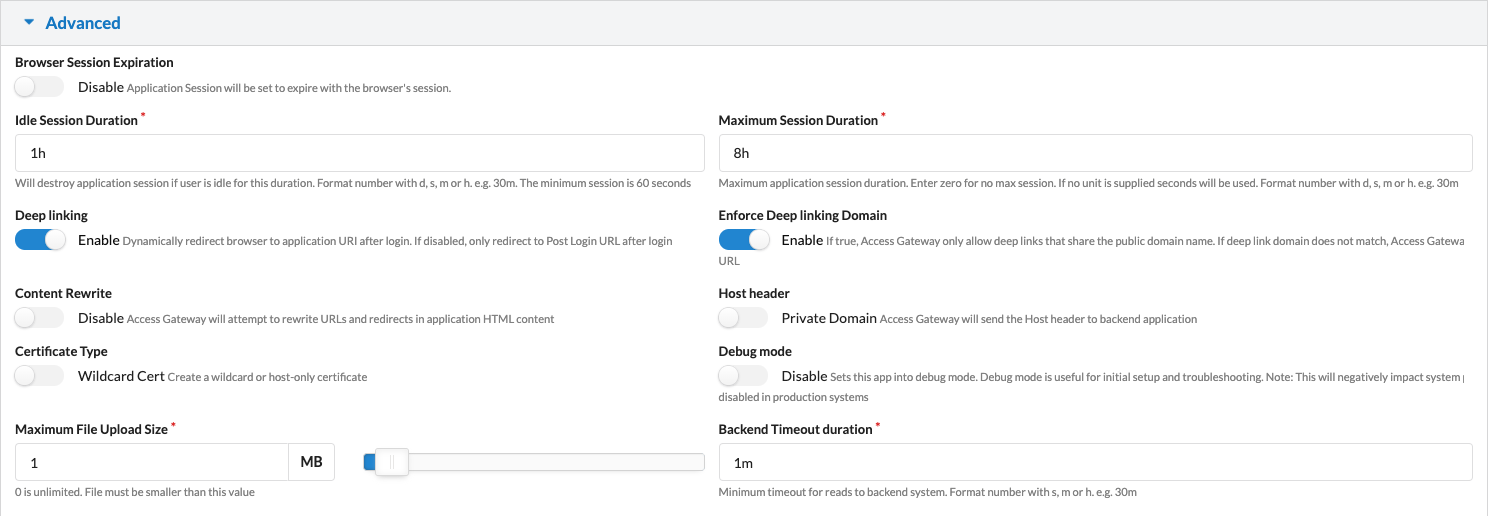
The Advanced tab allows you to tweak settings available only due to the individualized cookie/session per app. Options range from custom timeouts for session inactivity and duration, to debugging per session, to the use of custom paths for logout and global versus app-only logout.
OAG provides individual cookies and session management per application, making it possible to customize session timeouts per on-prem application—without requiring expensive or complex solutions such as using multiple servers or tricking the SSO system.
So, if you want to really dig deep into how Access Gateway works, check out this on-demand webinar—there's a cool demo in it. ;-) And if you liked this one, be sure to circle back and read the other 4 secret features of Okta Access Gateway!