
- Home
- Shape Security
Integration detail
Shape Security
Overview
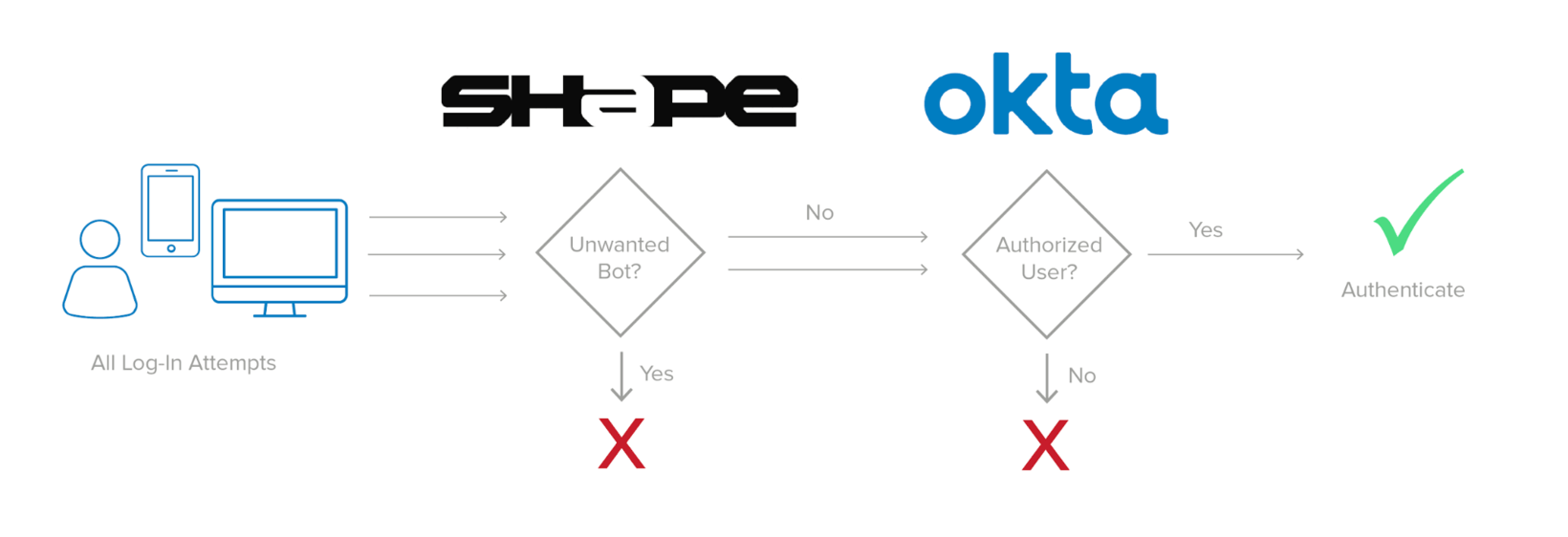
Okta works with Shape Security’s Enterprise Defense to detect and deflect automated attacks before they reach your websites, mobile applications, and APIs. The combination proactively mitigates the risk of credential stuffing and automated fake account creation. The Shape solution collects incoming login traffic–before log-in–and makes real-time, analytics-driven decisions on whether the login attempt is fraudulent, bot-based traffic that should be automatically blocked, or legitimate traffic that’s worth evaluating. This filtered traffic is passed on to Okta, which evaluates the login attempts and grants individuals access based on contextual policies.
The Challenge
- Bot-driven imitation attacks like credential-stuffing—where cyberthieves test millions of stolen passwords against your system—can account for a significant portion of login traffic
- This unwanted activity presents a constant threat to security, requires teams to spend valuable time fending off attacks, and impacts the bottom line via increased fraud
- All this fake traffic, and the measures security teams take to counteract it, can mean extra hurdles for legitimate end users and developers trying to access their applications
The Solution
Okta’s best-of-breed identity solution works with Shape Security’s Enterprise Defense to detect and deflect automated attacks before they reach your websites, mobile applications, and APIs
The combination proactively mitigates the risk of credential stuffing and automated fake account creation, keeping enterprise assets safe and reducing hours of remediation time and customer support
Adaptive software informed by deep learning assesses login traffic before login begins, keeping the process seamless and invisible to authorized users—no new security hurdles
Safeguard your customers from unauthorized logins
Okta’s authentication solutions, including Contextual Access Management and Multi-Factor Authentication (MFA), work together with Shape’s Enterprise Defense solution to protect your websites, mobile apps, and APIs automatically and simultaneously. In addition, the best-of-breed security technologies are easy for security teams to deploy and for authorized end users to navigate.
Deflect hostile traffic with a double layer of defense
The Shape solution collects incoming login traffic —before log-in—and makes real-time, analytics-driven decisions on whether the login attempt is fraudulent, bot-based traffic that should be automatically blocked, or legitimate traffic that’s worth evaluating. This filtered traffic is passed on to Okta, which evaluates the login attempts and grants individuals access based on contextual policies.
Upgrade your security posture to one that adapts as attacks evolve
Shape’s solution uses supervised and unsupervised deep learning methods to detect attackers’ techniques as they evolve and then autonomously deploy appropriate countermeasures. In addition, as soon as a new attack technique is observed on one Shape customer, all other Shape customers are immediately protected from it. And Okta’s Adaptive MFA allows for dynamic policy changes and step-up authentication in response to changes in user and device behavior, location, or other contexts, helping you stay secure as risk levels change.
Thwart credential-stuffing and other imitation attacks at the door, before they endanger enterprise assets
- Deny automated credential-based attacks across your entire ecosystem (websites, mobile applications, and APIs)
- Block cyber criminals from taking over legitimate accounts or establishing fake ones
- Deter future attacks with an evolving, machine-learning-based, cloud-first holistic security solution
- Provide easy access that safely lets in authorized users, while protecting apps and assets across the enterprise
Documentation
Here is a section all about documentation, integration, and implementation.
-
Datasheet:
Okta + Shape: Protect Against Automated Login Attacks and Fraudulent Account Takeover
Read it

