
- Home
- Centralized Logging
- Splunk Add-on for Okta
Integration detail
Splunk Add-on for Okta
Overview
The Splunk Add-on for Okta allows a Splunk software administrator to collect data from Okta. The add-on collects event information, user information, group information, and application information using Okta Identity Management REST APIs. This add-on also supports remediation commands that allow you to add a user to an Okta group, remove a user from an Okta group, deactivate an Okta user account from the Splunk platform and create custom alert. After the Splunk platform indexes the events, you can consume the data using the prebuilt panels included with the add-on. This add-on provides the inputs and CIM-compatible knowledge to use with other Splunk apps, such as Splunk Enterprise Security and the Splunk App for PCI Compliance.
The Challenge
- Stolen credentials are behind most data breaches,* and malevolent actors can move quickly once they’ve logged in
- Security analysts need visibility into the right data at the right time to be able to quickly identify and triage credential-based attacks
- They also need to be able to interpret and respond to anomalous behavior in real-time, without added steps or complexity
The Solution
The Okta + Splunk integration arms security teams with enriched identity data and powerful visualization and analysis tools to understand user behavior thoroughly and act quickly
Okta sends rich identity event data to Splunk, which can be aggregated and correlated with information from other sources for a comprehensive view of user behavior
Security workflows to resolve incidents involving identity are streamlined because security actions in Okta can be triggered directly from Splunk
Gain powerful insight into user behavior
Okta + Splunk work together to aggregate and correlate identity data from Okta alongside other logs from across the IT environment. Security teams can use Splunk’s visualization and analysis tools to interpret this enriched data and instantly spot anomalous and potentially dangerous user behavior.
Take quick, decisive action against threats as they arise
Okta’s rich identity context enhances Splunk’s toolset, giving security analysts a fast track to threat remediation at the user level. Suspicious behavior can trigger a security action through Okta, for example automatically moving a suspect user to a higher security group and restricting access or requiring multi-factor authentication, containing the threat before it spreads.
Add business value with deep understanding of user behavior
Beyond security, Splunk’s tools plus Okta’s enriched identity data can help enterprises analyze trends in business app usage and adoption at a deep level, enabling teams to more efficiently make enterprise provisioning decisions and assign and retire licenses.
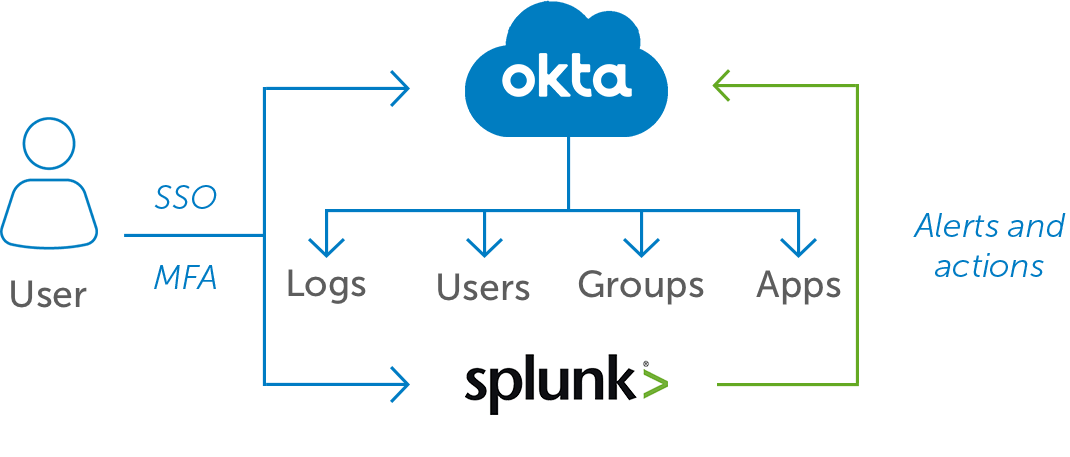
Use enriched identity data to dramatically enhance your security team’s visibility and response
- Aggregate rich identity data from Okta and correlate it with information from Splunk for advanced parsing and data modeling of user behavior
- Use these deeply informed, consolidated visualizations to shorten the time to detect inappropriate activity and remediation
- Enable decisive containment actions, including limiting user access, prompting for multi-factor authentication, and other remedies
- Monitor enterprise trends in app usage and adoption to enable more efficient and effective licensing and provisioning
- Protect Splunk’s rich data stores from malevolent actors with Okta’s MFA, while keeping log-in simple with Okta’s SSO

