Enhancing Identity Lifecycle Management in Just 15 Minutes
Transcript
Details
Rafael Kabesa: Thanks for that intro Alyssa. So please, don't leave after 15 minutes. In today's session, what I'm going to cover is how powerful the Okta platform is and how powerful it is in enabling you to manage identities in your life cycle in your organization. What I want you to take at the end of my presentation is that Okta is here to enable you to focus on what's important in your organization, to focus on innovation and moving your organization forward. I like to kick things off with a quote, "If everything seems under control, you're not moving fast enough." If you don't know who Mario Andretti is, he's one of only two drivers to win all four major race competitions: the NASCAR, the Formula One, the Indy Car and the World Sports Car Championship. And, speed was important for Mario, and I'm sure speed is important to you as well.
As an identity and access manager and professionals, you're expected to move fast and improve your user productivity. But on the flip side you're expected to do all that with less and less resources. And that creates some really challenging and complex problems. To start off, as all of you probably are familiar, is the explosion in user's and devices. If in the past you only had a single directory with just your employees in it, today you have contractors, you have partners, you have contingent workers, many external employees. So all these users also bring devices to the organization and in attempt to manage all that you have maybe multiple directories. All these users expect access, and they expect access immediately, and they don't care if it's a mobile app, if it's a cloud app, if it's an On-prem app.
And they also don't care what business process you have to follow. And to top all that, information security is coming at you and asking to report on usage, on access levels, on risks that's associated. And they also expect you to off board users immediately to plug any security holes but other stakeholders in your organization expect you to also renew access as they work and collaborate with people outside of the organization. As you can see IT is really struggling here and let's take a look at how that manifests itself in the organization. So we typically have multiple sources of truth. You might have your HR system, active directory; your ERP system, maybe, where you store your external users. And as users join, move, leave the organization, you probably have some communication with your HR stakeholder or some other stakeholders, emails, CSV spreadsheets.
Then you have to go put them maybe the right AD group and then create a corporate email or maybe assign a desk phone. Once you did that you have to go back, update HR, "Oh, this is they're corporate email, this is their corporate phone." You get tired of doing this again and again so you say, "Let's write a script; let's animate things." But the problem is the script breaks and then the person who wrote the script also leaves the organization, and you're in trouble. Next up, you have to provision create accounts, Office 365, ADP, Oprum cloud apps. More work for you. And then sometimes, depending on the role of the person, you'll have to go and have more set up communication between you and the BizApp owner. So something like Sales Force you might not have direct control of, and you'll have more spreadsheets, more emails going back and forth.
You did all that work, and the person on day one still doesn't have access to everything they need. So they file more IT tickets and more things that you have to do. And last, you have to report on access whether it's coming from information security or other stakeholders and you also need to suspend, revoke access based on the user type. So this is not just an IT headache, this also has security and productivity implications. At Okta, we have a lot of data about what we call business value and that's based on a forester model we developed. Depending on the scale of your organization, and I'm using 12,500 employees, which is about the average size of organizations here in the crowd, the cost of a security breach is estimated for about seven million dollars.
On top of that, you'll lose about 6,250 hours just on change requests, people moving within the company, changing roles, updating addresses, changing emails, et cetera. We also estimate about half a million dollars in cost and lost productivity for both IT and BizApp owner just for the task of provisioning and re-provisioning accounts in downstream applications. And not only that, every user in your organization is going to spend 300 minutes, every year, just waiting for access. So what can we do about all that? How about automating your onboarding and off boarding process? That's exactly what I'm going to demo.
What I have here is my Okta org, and my Okta org is connected to an HR system, to Work Day. So what I'm going to do is show you the entire life cycle, end to end. So I'm going to start off by hiring a new employee. I'm going to hire this new employee into my marketing org. Any Game of Thrones fans here? My new employee is none other than Emilia Clarke, yes, mother of all dragons and a London born resident. So Emilia joins and usually when a person joins he only has his private email and that's what they share before their first day. That's what I'm going to put here, some local .com and I'm going to designate that as a home email. And notice that detail because I'm going to show you how a corporate email process works.
So a few more steps in Work Day, going to hire Emilia for today. She's going to be a marketing manager. Regular employee. Going to be in field marketing, full time and, of course, she's going to be right here in the London office. So I hit submit, finish with the hiring process with Work Day and now before I go into my directory to look up Emilia, I want to show you one thing. One of the previous presentations, people talk about the automation and the capabilities we have around a [group rules 00:08:30] and that's exactly how we set them up. In Okta we have the capability to look at any attribute that comes off your source of truth, whether it's Work Day, My Case or Active Directory, if you'd like and then parse that attribute, use our expression language to parse that attribute and then assign people to specific groups based on that attribute.
In my case, what I did is I looked at the user title coming in and if that contains the word "marketing" I put them in the marketing group, if that contains sales, I put them in the sales group. Something very simple but it can involve something a lot more complex than that. So, remember that and now let's go to my directory and look up Emilia. Emilia already created here in my directory. And note what apps Emilia got assigned. So Work Day, Ring Central, maybe birthright apps, everybody gets those. But Marketo is a very specific marketing app, right? I assign Marketo because of that group rule that put Emilia in the marketing group and in turn the marketing group is associated with Marketo. Not only that, I also assigned Emilia to the marketing OU in active directory, again as a result of being associated with the marketing group she'll get automatically assigned into the marketing OU.
So, here we go. Here's Emilia. What's the next step? I want to assign Emilia a corporate email, right? Remember you only had her private email. I don't have an exchange server set up here but just to illustrate I'll show you how I change that in AD. So I'm going to change it to my company name .com, hit apply, okay. And now what I'm going to do is sync through my directory integration with Active Directory, all the changes. What I'm doing here is importing the changes manually, but you can schedule that. It's not something you need to do every time. You can schedule it happen as often as you like. So, I sync that, going back to Emilia. Going back to her profile, notices how her primary email got updated based on the change that happened in Active Directory. That's great, right?
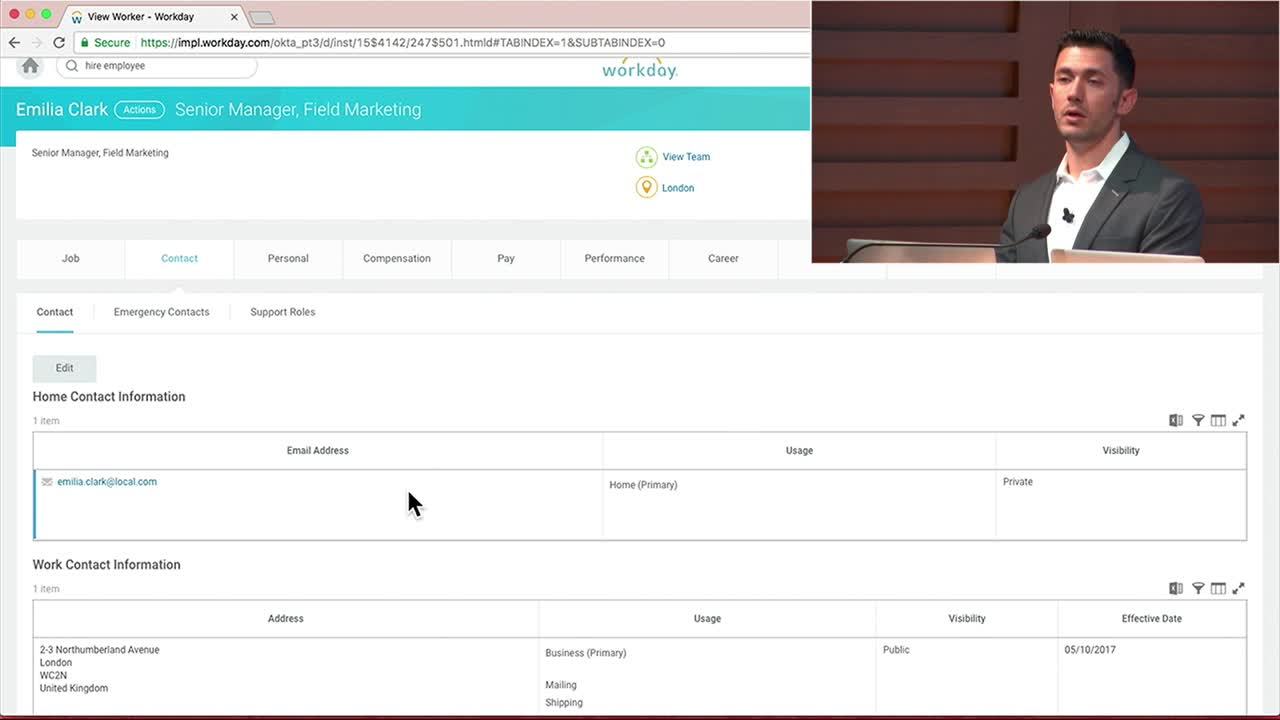
But not only that, I have also a bi-direction sync with Work Day. So if I'm going to look up Emilia in Work Day and look at her contact info, you notice this was her home address, her private address? I scroll down, I have here her new corporate address. Again, I didn't need to email, there was no spreadsheets, there was no IT ticket generated in this entire process, end to end sync. Another cool feature you can take advantage of is doing the same thing for a phone number. I also set up Ring Central as profile master for my phone numbers. I have provisioning set up with Ring Central, so as soon as I hired Emilia into my corporation, got provision into Okta, Okta automatically created an account downstream in Ring Central, Ring Central assigns a phone number. And now what I do is similar to AD, I'm syncing back all the changes from Ring Central.
Again, you can schedule these. There's no need to do these things manually like I do here, it's just to speed things up. Once I scheduled sync with Ring Central, I can go again to Emilia's profile and you can see her phone number got imported from Ring Central. Not only her phone number, but also her extension. How I did that, I did that using what we call attribute transformation. So I can take whatever attributes coming from one sort, use the Okta expression language, manipulate it and put it in whatever format I want in a different source. So not only I put it in Okta and synced it into Okta again, I can write back to Work Day and do the same thing. So if I go here and refresh the contact details for Emilia you can see her phone number and her extension got updated, again, I didn't need to do really anything.
Alright, so, this is great, but another thing that happened here is that Emilia got bored with her marketing job and she says, "Well, you know what, I want to move into sales." Can't really say no to Mother of Dragons, so lets do that. What I'm going to do here is change her job, change her business title. Remember she was in marketing so I'm going to assign her as a senior sales manager here in Work Day. Click done, here, our title's changed. Again, just to remind you, right, we had two rules set up. One was for marketing one was for sales and now what should happen is that she's going to move between groups, right? So, Emilia... let's look at her profile. See her title changed immediately, right? I didn't need, again, to do anything. Everything got synced automatically. But not only the attributes got update, also, the app assignments got update, right?
So Emilia is no longer in marketing. She no longer needs access to Marketo, so I automatically revoked that access based on that group association. Now Emilia is part of the sales group and she got revoked Marketo but also got assigned Sales Force. Now she needs to work with Sales Force as a sells person. So again, this is something that is very important in terms of controlling who has access to what. That was fine, but what happens when Dave from information security comes and says, "Rafael, I need a report on all the access that Emilia has."? No problem, I'll go to my reports section. We have here our new app access audits report. So I have two types of reports, let's start with the first one. Let's see all the applications assigned to Emilia. I can run a report here on Emilia. And you can see, not only I can see all the apps that Emilia got assigned to and what she has access to, but I also can see how she got assigned.
Note how the assignment type associated here is grouped. So all the apps that have a group means she got assigned through a group rule. Let's look at a more broader perspective. Let's say you want to audit who has access to Sales Force. I can run this report on Sales Force and see all the users who have Sales Force. So I can see a lot of the users basically adhere with my policy, right? My policy says, if you have sales in your title you get Sales Force, so all these users should be okay. But, there's going to be exceptions here and maybe Grace here that got assigned through an individual assignment through an Okta admin might be something I want to audit because it didn't happen automatically through the group rule. That's great, but, you know, your auditor insists on having extra data to kind of cross reference things.
So we added this advanced report capability based on what our customers asked for. I can add any attribute from the app profile to my report. So in this case I want to add what is the Sales Force profile in the down stream app and also, let's say the auditor asked me for the department. Maybe he wants to cross reference that. I run the report, and again I get a very detailed list of all the people who has access to Sales Force, how they got assigned, but also their license type. Obviously, I have just a demo Sales Force tenant so everybody here is a Chatter Free User, but in you case you will see all the entitlements, all the different roles that they have in the organization. And again, the department here is clearly marked. So maybe for audit purposes you want to why Duke from Human Resources have access to Sales Force.
Right, well, we finished reporting. So what happens next is that my CEO comes to me and he says, "You know what, Emilia, not meeting her her quota. We need to let her go." Unfortunately, Emilia, not performing well and what we're going to do is terminate her in Work Day. The primary reason, I want you to notice that primary reason is involuntary. So, involuntary. Poor job performance. We'll set it up for today. Click submit. And the reason I'm highlighting the fact that it's involuntary is that our customers came to us and said, "When somebody get terminated involuntary, I want their access cut off immediately." I don't want to wait because maybe it's a mutual process where somebody just moved so there's no bad intentions involved. But in the case of involuntary termination you don't want to open that window for any ill intent.
So one thing I wanted to show you is how we set it up in Okta. If I got to my Work Day set up and look at the provisioning setting I did here. Notice how immediate termination reason is marked as "Terminate employee involuntary star". So that means any reason. When I'm getting termination reason from Work Day when somebody gets terminated, if it comes back with that flag of involuntary, no matter what it is, I'm going to deactivate that user immediately. So go back, look for Emilia. And you can see her status is deactivated. And if I click on her profile, she got unassigned from all the apps. Right? Now security gap. But not only that, if I go down to AD and refresh the disabled user list you can find Emilia here, too. Not only I revoked access from us, but also disabled her as an active directory user so any entitlements as association with a certain group, a certain ADU, also got disabled.
That's the end of the demo. Just to recap we saw the entire user life cycle, right? From the point of hire, how we assign apps based on group rules. How when people move we can change their app assignment. We showed how we can report on access and then also showed how we cut off access upon termination. One thing I didn't get a chance to show you, but pay attention in the next session for Mike's presentation on how we can enable an access request work flow. So that was already mentioned in the GDPR session, how we can enable somebody to access request for specific apps and that gets routed to a person maybe outside IT and Mikes' going to show that. So pay attention to that.
So that's all we can do today for you and that also has implication, again, we measure through our business value practice on how this increases productivity and security. We estimate a 75% decrease in chance of breach, so if you just consider that scenario of involuntary termination and how we cut off access, how we disabled access to an app that no longer needed for your new role, that's a major security gap that we can plug. On top of that, all the change request, I didn't need to do anything. Everything was completely automated from change of role to assigning of an email to assigning of a phone. Everything got automated. Also remember that half a million dollar number on provisioning and de-provisioning request. We estimate that we can cut that by half. We have over 80 provisioning connectors to all the top applications in our Okta application network and we can automate the entire process of creating, updating and removing accounts.
And then, if you have multiple active directories and you need to manage multiple domains using our AD agent it's really easy to consolidate all of them into Okta and reduce all the maintenance around that completely. That's of course everything we can do for you already today, but what's next? What are we thinking about in terms of the next lifecycle frontier? One thing that is certain is that today's landscape is very different than the future one. And to give a better sense for what I mean, consider this stat from Innosight, "75% of S&P 500 companies will be replaced by 2027." If you find that figure hard to believe, just look at a report that JP Morgan released looking back at the S&P 500 since 1980 and seeing that about 64% of the S&P 500 index companies got replaced, or about 320 companies.
JP Morgan called that creative destruction. And how does creative destruction look like in our context? It looks like very company is developing application or what the the industry called digital transformation. So every company is now required to create digital experiences to interact with their customers, with their partners, or even with their own employees. But with those new experiences and new interactions, there's new types of lifecycle's, and with new types of lifecycle's there's new types of requirements. So consider those profiles, the contingent worker, a partner or contractor, and how onboarding and off boarding looks very different in their case. So some of the things we're going to do to help you with managing those lifecycle is building a self-service portal where they can register themselves.
So you don't have to go and input all that information yourself, they can go in, fill in all the attributes you require and then the request comes to you and you can approve access. But if you really want to scale that, you want to delegate that access decision outside of IT, right? You can't be the bottleneck of all those access decisions for external users. So what we'll do is enable you to designate a sponsor for specific groups of users, like your external users, to get re-routed through their sponsors. So consider somebody in your marketing org knowing and collaborating with a contractor and the request will come to them in their Okta portal and they can approve that access knowing who the person is.
Looking at off boarding, again, different lifecycle, right? The lifecycle of external user is not governed by an HR system. So we're building what we call a user lifecycle policy. You can assign that policy to specific groups like the people here, a contractor group or a contingent worker group, and then have a date based automatic suspension. But in order to enhance security even further, the amount of external users can be very large, you want to also have controls on that in terms of activity. If you have, for whatever reason, some sleeper accounts there that weren't in active for the last 30, 60 days, or whatever policy you want to implement, we can automatically suspend those, as well.
But consider that scenario, right? Let's say I'm a partner and I work with your organization and I got suspended after 30 days but now I need to work with you again, but I don't have access. So what do I do? Do I call you? Do I send an email to my sponsor and then my sponsor needs to contact IT so you can reactivate me? Not ideal, right? So what we're doing is enabling self-service reactivation. What you can do is put a trusted email domain, like your partner email domain, in the Okta system and then because that's a trusted email domain, as a partner, I can go an ask for a reactivation link that's going to send to my active partner email. And I can click a link, get un-suspended, get reactivated and collaborate with you again without needing to bother IT or anyone else.
And how are we going to enable you to use all that? There's two options. We're going to give you widgets out of the box that you can connect to whatever processes you have in our systems, you have in your backend. Or another option is to leverage our API's. So, if maybe in the partner or contractor case, you need something very basic, just get up and running. For your customers you might want something a lot more customized with better design, better UI, so we're having an API first approach where we're exposing all that so you can build beautiful UI's on top of that authorization layer. With that I'd like to thank you. Hope you enjoy the rest of the afternoon and the sessions. Have a great rest of your day.
In today’s increasingly dynamic IT environment, IT professionals spend many hours managing multiple identity lifecycles. This includes securing multiple identity sources, ensuring appropriate access is granted or adjusted in a timely but secure manner when new employees join the organization or change roles,, and also suspending and removing access quickly when necessary. Okta continues to innovate in identity lifecycle management, allowing customers to create a single source of truth, delegate access decisions, and easily generate access reports. Learn how to save time and money by automating the lifecycles across any business process for all your users.
