Oktane18 - Acxiom: Security and Remote Access with HR-as-a-master and MFA/VPN
Transcript
Details
Maggie Adams: Thanks again for joining us. Again, my name is Maggie Adams and I'm on the Business Development team at Okta where I help manage our security partnerships. That's many different partners, and actually, I'm here joined today by Pablo, Pablo Valarezo who is the IAM team lead at Acxiom, which is a marketing, data, and analytics company based out of Arkansas. I first met Pablo, actually, about six months ago. I reached out to Pablo about a case study that I wanted to do with one of my partners and an integration that we do together. That partner is F5 Networks. Reached out to Pablo. Pablo is a known Okta champion. As Acxiom is also a great Okta customer. Reached out about that and in working together on this case study, understood that there's a much larger story here with Acxiom, a really great story in their journey with modernization and identity together, and thought there's a lot more to tell here than just this case study.
Here we are six months later on the stage to really kind of dive into that story. Quick disclaimer, so I'm going to talk actually about a lot of messages that you may have heard today on the main stage, the Keynote today with Frederick Kerrest and others. To start here, there's a lot of security elements to the story today. Here at Okta, we view security driven by identity. Really, this is all ... I mean, it's however you want to call it. Identity driven security, zero trust, beyond corp. There's many different names, but these are the four pillars that we use to approach this. The first being, eliminate passwords with centralizing your identity. That's typically through Single Sign-on and Universal Directory, those products. Also, ensuring strong authentication everywhere, so adding that additional layer of security pervasive across your environment.
Third, reducing the attack surface area, so automated provisioning and de-provisioning of your users. Then finally, adding deep visibility and response across that entire environment. These are kind of the four ways that we at Okta ... We look at security and how identity fits into that together. At Acxiom, all of those are covered, but really the story today that we're going to focus on are under these two pillars. In centralizing their identity using single sign-on and universal directory, but really also our HR driven provisioning and using Workday specifically as a master. Pablo will speak into that. Then, in terms of security, replacing legacy, replacing legacy VPN, and MFA, and adding Okta's adaptive MFA across the board to hit strategic initiatives in that regard.
What that kind of looks like, so there's your organization. You might have on-prem active directory. You might be using universal directory maybe as well. All of that. There's different user directories and data storage that can sometimes be siloed, but really bringing that together with Okta. Also, that's seem through Workday. Workday is a master in the user provisioning that happens there. Bidirectional sinks, so when someone enters the organization, when they move laterally within the organization, when they leave the organization, to keep it all seamless throughout that process in that user journey. Workday is what we'll talk about here today, but we also work with other HR systems. Pablo will dive into that. Then, to really speak to access.
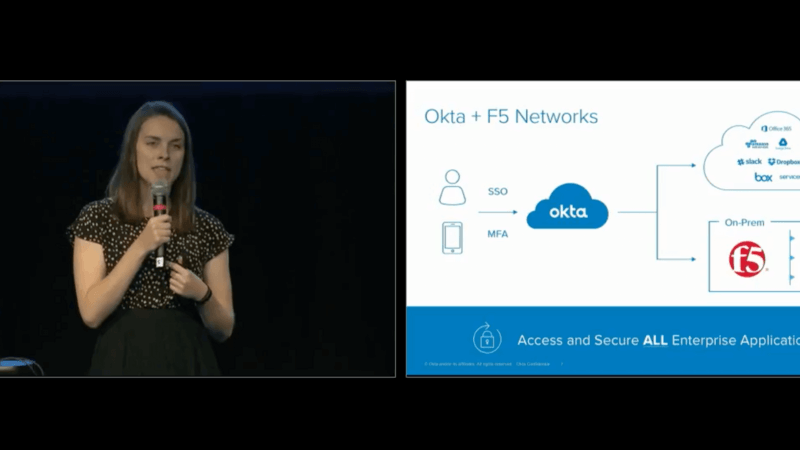
Our story with F5 is really a hybrid story. You have a hybrid environment, cloud architecture, many different applications that you're adopting, but you also have a legacy on-prem environment that you also need to provide that seamless and secure access to. At Acxiom, they had F5 ... They were using F5's VPNs to provide different VPN tunnels for internal resources for remote employees. Actually, it was ... Well, I don't want to steal your thunder, but it was actually at Oktane where they found out about this integration. This is actually the story that I first approached Pablo about. This is the seamless story and it's not just that access. It's not just providing the access to those applications, it's also securing them with MFA.
This was part of a strategic initiative for Pablo, from what I understand about MFA everywhere, MFA across the boards. Really making that available to you for the amount of security and usability that you want to offer. As that additional layer of security, it obviously needs to be secure, right? But it needs to be really easy to use. If you're going to put it everywhere, it needs to be simple for all of your users to adopt. Supporting many different factors, but one of the easiest to use is Okta Verify with Push, which Acxiom rolled out. Also, it needs to be extensible. It needs to not just cover those caught applications, but also putting MFA in front of your VPN, things like that for strong authentication everywhere. With that, I'll hand it over to the real expert, Pablo. Quick shot out, if you're interested in more, that original case study that we worked on together on F5, I have a couple copies so come find me afterwards and I'll pass them out. But with that, Pablo.
Pablo Valarezo: Thank you, Maggie. Thank you for the introduction and hello, everybody. Hope you're having a great conference, and really enjoying, and learning things, and taking stuff back to your day-to-day work, and finding a lot of value in every session, including this one. I'm going to talk about the journey that we've been in and looking at the agenda. I'll just do a quick overview, introduction to myself, who Acxiom is, and also look at kind of some of ... The problem we're trying to solve when I first looked at Okta. Then, walk through the journey and where we're going with this. Also, want to cover some of the different implementations with a little bit of detail. I'll try to share some tips that we found useful. Ultimately, we're trying to get to that identity centric security that you hear time and again.
A little bit about myself, I began my IT career when I joined the Air Force. It was '93, I think. There, I got introduced to Unix and networking databases, a little bit of everything. I didn't go very deep in that. Once I separated from the Air Force I joined Digital Equipment Corporation. Does anybody remember that company? Yeah, a great, great company to work for. In '98, Compaq computer equipment, they acquired Digital. At the time, it was the biggest merger in the computer industry. Then in 2002, HP acquire Compaq and I kind of moved along with those companies. But I did also take a year off. I convinced my wife to sell everything, and travel, and that was a great experience for us, a great way to ... I think a great way to start a marriage, and pre-kids, so we were able to talk.
Once I came back into the workforce, I joined Acxiom in IT and audit. When you're in audit and compliance, you look across all areas of security. What I noticed was that IAM really needed an infusion of energy, resources, and really attention. That's when I started kind of gravitating towards that area and now I lead the IAM team at Acxiom. Has anybody heard of IDPro? Any IDPro professionals? About a year ago, or maybe a year and a half ago, IDPro was founded and it has a ton of great resources if you're really interested. If you're in the profession, something to consider joining. There's the URL for that and a way to find me. I like to begin by explaining what Acxiom does and looking at the value proposition.
Customers who put the right data foundation in place for their omnichannel people-based marketing have great competitive advantage. If you don't know what that means, that's okay. We're going to cover through this and we're going to look at the similarities in the marketing ecosystem with the identity ecosystem. Basically, what this means is that data foundation allows you to unify all that information that you may have on a consumer and create a single view of that person so you can build great marketing campaigns. You can take that information and you can validate it, make sure that that person that you think you know is actually who that consumer is. Then you can enhance it with the digital data sources. Most importantly for marketing, you want to activate that across different touchpoints.
As you can see, this ecosystem kind of flows in the direction of bringing all that information together and then branching out in the form of campaigns. Last, you want to measure in real sales how that campaign is performing. What the data foundation looks like is identity. Acxiom has five decades of expertise in identity from the marketing standpoint. We have the data. We have a vast set of integrations with partners and other data sources. We have been building solutions for our clients. Half of the Fortune 100 companies are our clients. The most important part, for me, in what I help deliver is a stewardship. Acxiom has a great tradition of being secure and providing the privacy so we can protect our clients, their brand, and most importantly the consumers. Acxiom also is known for having the first chief privacy officer who helped us kind of bring in this entire privacy infrastructure that we have in place.
To look at an example of what this complex ecosystem looks like, identity resolution is a term that I've seen both in the identity ... From the identity standpoint and from the marketing standpoint. What it means is that the same person may look different, depending on what touchpoint you're looking at. Rebecca, for example here, may appear as one person if you look at one interaction that she had with one company, or perhaps interactions with devices. All of this is information that marketing is trying to understand and compile. As Rebecca has gone through different life stage changes and as she interacts with different devices. Again, she may look like different people. The end goal is a single view of Rebecca. Whether she is at work, whether she's out shopping, or behind the computer maybe doing some online shopping, you want to have that single view from the marketing standpoint.
But I would argue that from the identity standpoint, I mean, all of this is similar. Whether it's a user in your company, a partner, contractor, a client, you want to have a single identity view. That is how I try to think about identity and how it crosses from marketing to IAM. Let's go back to the journey and talk a little bit about Acxiom and LiveRamp. In the summer of 2014 Acxiom acquired LiveRamp. As you can see from this, Acxiom was the almost 50 year old company that wasn't ... Was more mature, distinguished, maybe had a little gray hair, a receding hair line, and didn't move as fast, and wasn't as lean as he once ... It once used to be. LiveRamp was pretty young, a tween, and a rebellious tween. All right. Very proud of being a rebellious tween. Acxiom had the global presence. We had already been around the world and spoke a couple languages, there's three or four, and had offices around the world. LiveRamp not so much, it was a start-up. And because it was a start-up, it was able to inboard things in the cloud a lot quicker than Acxiom, which had its ITO own premise.
Culture wise you could imagine 50 years of being in business doesn't allow you to continue to sustain that start-up culture. So, LiveRamp use Mac's and G Suite, Acxiom used PC's and Office 365, so there's a lot of differences there, but Acxiom had that mature security in compliance and privacy programs that LiveRamp needed to sell to the same customers. We'll talk a little bit about that. How Acxiom was able to influence that.
To look at the experience of LiveRamp associate, by having this connected systems, because they didn't do a lot of identity and access it was kind of the same scenario. Rebecca or Becky or Becca, she looked different even though she was a LiveRamp associate depending on which system she was going to. And when she left the company, we had a security challenge of disabling access across all the applications.
On the Acxiom side, we started about four years ago, I think we were pretty early on in Okta and so we were already integrating systems. We were doing Office 365 sales floors, one of my favorite ones, Lucidchart because it was the first skin based provisioning that we did. So, for diagramming and some of the diagrams in here are using Lucidchart and the integrations continued kept coming to us. Everybody wanted their application to show up in the portal, so it was a great place to be. The Acxiom experience for the associate was a single sign-on, right? So, you've heard the story many different sessions, a lot of success, people got high-fives and people open tickets to the help desk just to say thank you which to me that's unheard of. But that's how impactful it was.
So, what happens when you have these two cultures, these two businesses? Well, the organization that I'm part of which is the Acxiom workplace experience very proud to be, was born about two and half years ago with intent of given every associate the best work life experience it can be. So, you wanted a new headset, you can get that by opening a ticket or now you can go to a vending machine and you can get peripherals for your laptop or different things. We did lotteries, from the technical standpoint, we did a lot of that stuff. But it was also amenities, better travel tools and we looked across all the different applications that we use for collaboration. We tried to integrate or standardize on Office 365 or G Suite, but ... What is it? Love, hate relationship a little bit. So we didn't make a lot of progress there except for sharing calendars and things like that and building a lot of collaboration.
AWEL does free food and anything that touches the Acxiom workplace and associate is something that it was doing. And part of that was project unify where we try to bring synergies and try to deliver the better experience with better technology. So, we looked at telephony, we looked at collaboration, we looked at video conferencing and one by one we started rolling out all this, again, that made people more productive and enjoy their workplace experience better.
From Project UNIFY, one of the biggest challenges that we had was rolling out security. We wanted to make LiveRamp while continuing this roadmap that we set Acxiom on. So, one of the first things that we did was roll out MFA like Maggie mentioned to everywhere. And, at the time we were using the physical tokens that come very hard to manage. I remember seeing boxes and boxes and boxes of tokens that people lose and so we had to have a big bag. Nobody knew ... It was just a nightmare. Nobody misses that type of setup. So, we waited until Okta verified with PUSH was general access and we decided to roll it out. Simple and intuitive.
SMS at the time was already something the NIST had deprecated. So, we were able to roll that out, a few people complained, but overall it was a huge success. And one of the things we did was empower the help desk. And this is a tip, if you have already done this, great, if you haven't, you haven't rolled that in the face. Something to do, as part of your rollout, we just gave the help desk a Chiclet, an application that they're owners of. And all that Chiclet does is mandate MFA every single time so the help desk agent that's working with somebody who's having trouble can say, "Okay, I'm going to give you a Chiclet, click on it, that way you have to do MFA." And that way the person can make sure that it works while in the office where we don't require it before they go home and then they try it a night and of course once they're done, the help desk can take it away. That worked beautifully for us. And, of course, we've adopted the admin console MFA, which is an early access feature. Really happy to see Okta continue to make the experience by making the automatic PUSH checkbox available.
So, moving onto the VPN experience. The MFA solution that we had was funky, janky, I had to look up the definition of janky because my VP uses that word a lot, I don't know, but we wanted to modernize it, right? And, those tokens were mostly used for VPN, we had some applications that were not covered so, like Maggie said here at Oktane, we learned about this integration with F5, so we can do SAML directly to F5 and then with the admin access application admin, we can deliver that experience of the team that supports VPN, they can now instantiate new integrations with their VPN's and they can move very forward and they can provision it and de-provision it, change the configuration. So, overall it was a great experience and, as you can see, the work as a Master was not rolled at the time, but it was already on the roadmap.
So, what we wanted to see was, can we make a dynamic in scale. At Acxiom, again privacy is paramount and we build these secure environments for our clients. Some of them are very large, some of the not so much but they're all protected with VPN tunnels and what we're able to do by having Workday as a Master now is making more dynamics, so we can scale very quickly and ask people are onboarded to a team, to a different client and they support that client, they can get that access. We're still in the early stages of making that fully dynamic but it's work in progress and integration that we have with F5 is allowing us to do that.
So, Workday as a Master, Patrick back there, who is the man, who helped us roll it out from professional services. We engage with Okta PS and went many different iterations of testing and working with a Workday sandbox in Okta preview and we wanted to push identities directly to AD and wanted to push groups, I mean we wanted, I wanted it all. So, what we rolled out was that integration where we made Workday the Master for about 95% of our accounts. And, again, working with PS, to me it was such a success because we touched 95% on a Saturday night. And Monday morning, or actually Sunday night which is the Monday morning for China, everybody came in and they can log in and nobody knew that we had done this. But, we had touched all these attributes across Okta, across AD, across many of the systems like Lucidchart where it was already skim integrated and people all of a sudden were like, "Wow, I see all this stuff what my name was three years ago and all of a sudden my name is up-to-date. This is great." So, a huge success.
So, as you can see the F5 integration for the security is based not directly on Okta as we use an AD for permissions, but again, AD is just getting fed this information which come from Okta, which come from Workday. Scott Howe, he's our CEO and President, he kicked off our sales summit a couple weeks ago. And in his keynote, he answered a question that I've been wanting to ask him myself. Apparently a lot of people have been thinking about this and the question is, "Can we just slow down?" We are doing so much and we don't want to stop, but we want to slow down. And his answer was, "No, absolutely not." The company's that get complacent die a slow death, to paraphrase his answer.
So, we've been doing a lot. Business challenges continue to come to me to do M&A type activities so, one of the things that we wanted to do for LiveRamp was give them their own identity, right? In the form of a Okta portal that was branded to LiveRamp and again, our company continues to go through a lot of transformation. So, we wanted to have that flexibility but also the standardization and I proposed in four different slides, this is how we roll this out. Got immediate approval, went to work and in a matter of weeks, we have deployed or LiveRamp that Oktava comp. Every bit of LiveRamp is always happy, the tween doesn't want to be necessarily be associated with a 50-year-old, so they have their own brand and most of it was enabled by this Org2Org integration.
So, who here has done Org2Org? Okay, that is ... You don't count. If you haven't done this, I'd say one of the greatest tools you can put in your toolbox is that type of Org2Org integration. So, what we're doing here, Workday continues to be our source of truth for HR. Once somebody's provisioned to Acxiom based on dynamic attributes they get put into groups, which then get pushed to LiveRamp. And those permissions get pushed to LiveRamp and applications get pushed to LiveRamp and application access gets pushed to LiveRamp. So, now because we do onboarding off associates, there's no more work for us to do, most of this it just happens. And, if you have an Okta Org, chances are you have an Okta Preview Org, you can do it between the two. So, that's my suggestion to you. Go back and do that integration and test it out because at some point, you may do a merger or an acquisition, and this solution is my favorite tool nowadays.
One thing that we stumbled upon, which was great, and another tip for you if you have Slack, which has been great since ... part of the Unify project that we did was adopting Slack. And so we're designing these groups because people move. I move, and when I move ... I moved over the years so much that I knew that in the process of moving you look for somebody in your new environment where you can find affinity, you know? I used to have a Jeep. I used to go four-wheeling. I look for somebody with a Jeep. "Hey! Let's go do this."
Similarly, in the onboarding experience you want to give that to your new hires. Is that a developer? Put him into Code Ninjas, Slack Channel immediately. Don't leave them out there looking through channels trying to figure out what they want. Offer them at least some of those things.
That's one of the things that we're doing. We push this very rich user profile, including a URL to Workday to the profile. So the most common thing that I end up doing when I'm talking to somebody is I look them up in Slack. I may be chatting with them with one link that was pushed from Workday to Okta to Slack. I can look at their profile.
So there's a much better integration. And again, most of this is dynamic. We're using dynamic groups extensively because we're pushing that rich profile with 60 different attributes. I think that was a record. Was it a record, Patrick?
Patrick: Yeah.
Pablo Valarezo: At the time. 60 different attributes for one person. I mean, that's a lot of information. You can do a lot with it. So, dynamic groups, I know they're a huge tool and something that I highly encourage you to look into if you're not already.
So Forrester came up with an ROI calculator for IDaas, and when we first rolled out Okta, marketing approached me and said, "Can we do this calculation with you? We have an Okta version of the calculator." And so we saw the great ROI, but again to me, that ticket that somebody will open just to say, "Thank you," that is success. I mean, that is great feeling.
Somebody sat next to me in a conference room one time. We didn't talk, we didn't know each other. I still don't know who that person was. But I remember so clearly she opened her laptop and she was like, "Wow! This Okta thing. This is like the best thing that Acxiom has done in 30 years." And I just smiled. I didn't say anything. And she left, I left, but that moment really stuck with me.
Fifty years of course we have had our PCI compliance. We have FISMA compliance. We just earned a high trust. And not that Okta is the only thing that auditors look at for this, not the only thing you have to be compliant, but is a whole lot easier and it takes time away ... it gave us time back to not have to go through these rounds and rounds of evidence gathering. That was on my team, and we no longer have to do that so much. And of course, GDPR. Are you GDPR ready? Who's 100% GDPR ready? Right there.
I got some ... I'm prepared. I don't have any new socks but I have those so I think I'm okay in Great Britain. So some of the things are not in here. We were named Partner of the Year by Citi and by Walmart; it's one of our biggest customers. A lesser success ... and again, one of the tips for you is to have plenty of time to be compliant with GDPR. I think it's May 25th or something, so you got plenty of time.
Dynamic groups ... so here's a situation that ... where I found a lot of value in some of the early access features. Okta allows you to see the assigned users ... current assignments, right, for an application. You can see who's signed on, when they signed on, and who's signed the app. But it doesn't give you the context of who is a European Union citizen ... a data subject in GDPR terms within the same report.
So what you can do is go to the profile editor, right? If you are importing that data and you know the country for a person, go to profile editor, find a profile for that application, and you can add it, add the country, to the profile for the app, and then you go to current assignments and you export it, and you can add the country to it, throw it into a Pivot table, and there's a list of people that need to get their access cut off because they're not ... because they're in France or Germany.
We have a road map. Some of the things we're trying to do. The help desk. We've partnered with the help desk so much. One of the things that we want to do is give them the verification capabilities with a push, right? When somebody's talking to the user that calls in and is screaming, "Give me my new password" or "Reset my NSA," whatever it is, we want to be able to push. Just give the agent the ability to say, "Hey, I want to push in, and if you are who you say you are, you should have your phone and you can verify."
That's one of the things we're looking at, how do we integrate API to do that. We'd also like to see proximity authentication. I'm glad to see some of the stuff that was announced yesterday in regards to no password. I envision it where you can your cell phone on you, you walk up to your computer and it unlocks. That would be nice. Or maybe a single tap. But most importantly when you walk away, the computer locks, right?
Group lifecycle is something I got to ask yesterday in one of the road map sessions. To me, Okta's still pretty new even though we've been there for four years. We build a strategy around dynamic groups but don't want it to get cluttered the way AD is. We don't want these groups that were created once for an organization's get-together or something. I came across one of those that happened about two decades ago. And the group is still there, and it's been empty for a long time. So, there's a lot of clutter, there's a lot of stuff that I would like to see Okta invest in this lifecycle where you can say, "I'm going to build a group. It's for this project. This project's six months, and that's the expiration date for this group." And after six months, it sends a notification and then it gets removed.
So some of these ideas are of course in the community. If you're not using a community, definitely go out there, look at the ideas and up vote them and down vote them if you don't think they're valuable.
To bring you back around to this ecosystem concept, with IAM I believe you can deliver a lot of business value because ultimately what you're trying to do is to unify this ... everything you know about an employee, about a client, about any user into one identity, which you can verify, you can validate and you can enhance with digital attributes. And then you want to give them the right access for the right amount of time in the right experience.
To us, that user experience is something that I believe we've adopted since we got Okta. IT used to throw out a lot of projects out there, and with Project Unify and some of the things we've done, I mean, the end user experience really needs to be great or we don't do it.
Last, we want to audit the access. We want to audit licenses. We want to audit who has an account. We want to do all these things so they're part of the IAM ecosystem. So we've built this foundation with that identity in mind, with the attributes, with everything integrated, everything that we have so far integrated, and most importantly with our security.
With that, I think we'll open up to questions if anybody has one.
Thank you. Thank you very much.
I was asked to make this request for the survey card, so I don't know if the survey cards around but make sure to fill out.
Speaker 1: There are survey cards located at the two tables at the back of the room so if you could please fill some out before you leave that would be great.
Pablo Valarezo: You have a question?
Speaker 2: Yeah. Do you guys use working directory groups as part of your Workday, Okta advanced mastery?
Pablo Valarezo: Absolutely.
Speaker 2: How do you incorporate those into your solution?
Pablo Valarezo: So, we ... I took a very hard look at the AD groups that we were using, and my team used to do different clones. We would have templates and they would clone, disable the accounts into new accounts. AD used to be the master of course. And we have built out these clones for every office that Acxiom ever opened ... LiveRamp ever opened. So there was all these clones out there that ... again, they were just cluttering AD.
So we decided on a strategy of a single OU per country, and that matches up to workday provisioning groups, so we could have done it in Okta with dynamic groups, but we decided to offload that work to Workday, and so we have one ... wherever Acxiom does business, wherever have offices, we have one provisioning group that ties into Okta and then pushes two different ADs. Asia-Pacific is its own thing. And that has kept it really clean. We're ...
At some point we may go to AD and centralize that around the country, but still in the U.S. we have many different OUs. They're not being used any ... No new accounts are getting created into different OUs. We have one for the U.S. where we have the most offices. And that's worked out very well.
Other questions? Thank you very much. Good luck to you. Have a great day.
Acxiom serves as the data foundation for the world’s best marketers. Next year, the company turns 50 years old, meaning it has evolved throughout several waves of technology. Okta has enabled its most recent transformation beginning with the Okta Identity Cloud and extending this through integrations with Workday, F5 Networks, among others. Learn more on how Acxiom leverages Workday-as-a-Master for provisioning and de-provisioining, and Okta’s Adaptive MFA for enhanced security everywhere.