How to Boost User Retention with Risk-Based Authentication
Today consumer-facing service providers have a stark choice—to offer robust security or an easy user experience. But for many organizations, missing the mark on either of these elements can seriously damage their user engagement and retention rates—and by extension, their bottom line.
To address this, we have now made Risk-Based Authentication generally available with the intent of eliminating the need to make the tradeoff between security or usability.
Now that Risk-Based Authentication is GA, I’d like to elaborate upon the security vs usability challenges that our customers face, break down how this feature can help, and how to get started with Risk-Based Authentication.
Let’s dive in.
The challenge: Balancing user experience with security
For consumer-facing service providers, user retention is a top priority. Losing users is like losing dollars, and the experience your users face plays a major role in what that retention rate looks like.
For many organizations, a major bottleneck that causes user drop-off is the user’s login experience. Auth friction is real, and poorly designed authentication leads to high drop-off rates for your users. Nobody likes to repeatedly log into applications, enter a complex password, and confirm their identity via MFA for routine actions—especially on mobile devices.
But this doesn’t mean you can afford to sacrifice security for a better user experience, lest your users fall prey to Account Takeovers, which can each cost your users as much as $290 and 16 hours to resolve, according to a study from Javelin Study & Research.
Your customers need to be able to log into your app with as little friction as possible, regardless of where, when, or on what device they are accessing from—all without compromising on security.
The Solution: Risk-Based Authentication
Okta's Risk-Based Authentication is a machine learning-driven smart access engine that improves security and authentication experience. Risk-Based Authentication analyzes the probability of an account compromise in each authentication request, and responds with the appropriate next steps—either a seamless login or a step-up authentication request.
How it works
For each login attempt, the system observes a series of individualized contextual variables including the device, location, IP address, typing biometrics, and more. Based on this information, Okta builds profiles for each user. Think of this as the "Digital DNA” of a user's normal login pattern.
Based on this context from previous logins, the system will classify login attempts as…
Low Risk
Example: Your long-time customer, Jane, attempts to log into your app using her usual device and IP address from her home city of Chicago at 10 AM—the same time and place she usually authenticates from.
System response: Jane may proceed into the application without further authentication required.
Medium Risk
Example: Jane attempts to log into your app from Chicago, as usual. But this time it's via a different device, and at 7 PM instead of 10 AM—not too out of the ordinary, but better safe than sorry.
System response: Jane may be prompted with an additional authentication factor before access is granted. Just to be safe.
High Risk
Example: Jane attempts to log into your app from an unrecognized device in Moscow at 2 AM local time. Hmmm… Pretty suspicious.
System response: Jane’s account is locked out completely, and your administrator is alerted to this suspicious activity.
The beauty of Risk-Based authentication is that these responses are customizable. Administrators can pair risk levels with the response they feel is appropriate to automate a dynamic approach to authentication security.
For a high-risk login event, administrators can require passwordless authentication and authorization via only strong authenticators, such as a FIDO2.0 compatible factor and Okta Verify Push. And, for low-risk logins, administrators can provide a passwordless experience with any factor best suited for the organization, such as only SMS, Okta Verify, FIDO2.0 token, etc.
Combine Risk-Based Authentication with Factor Sequencing for even better customizability.
The impact: Your users remain your users
Risk-Based Authentication means lockouts for malicious actors and reduced friction for your legitimate users.
Reduced auth friction means improved user experiences and increased product engagement, which means improved user retention, which ultimately means increased revenue.
And who doesn’t want that?
How to get started
Risk-based Authentication is included in Okta’s Adaptive SSO and Adaptive MFA products. Here’s how you can get started with Risk-based Authentication in Okta:
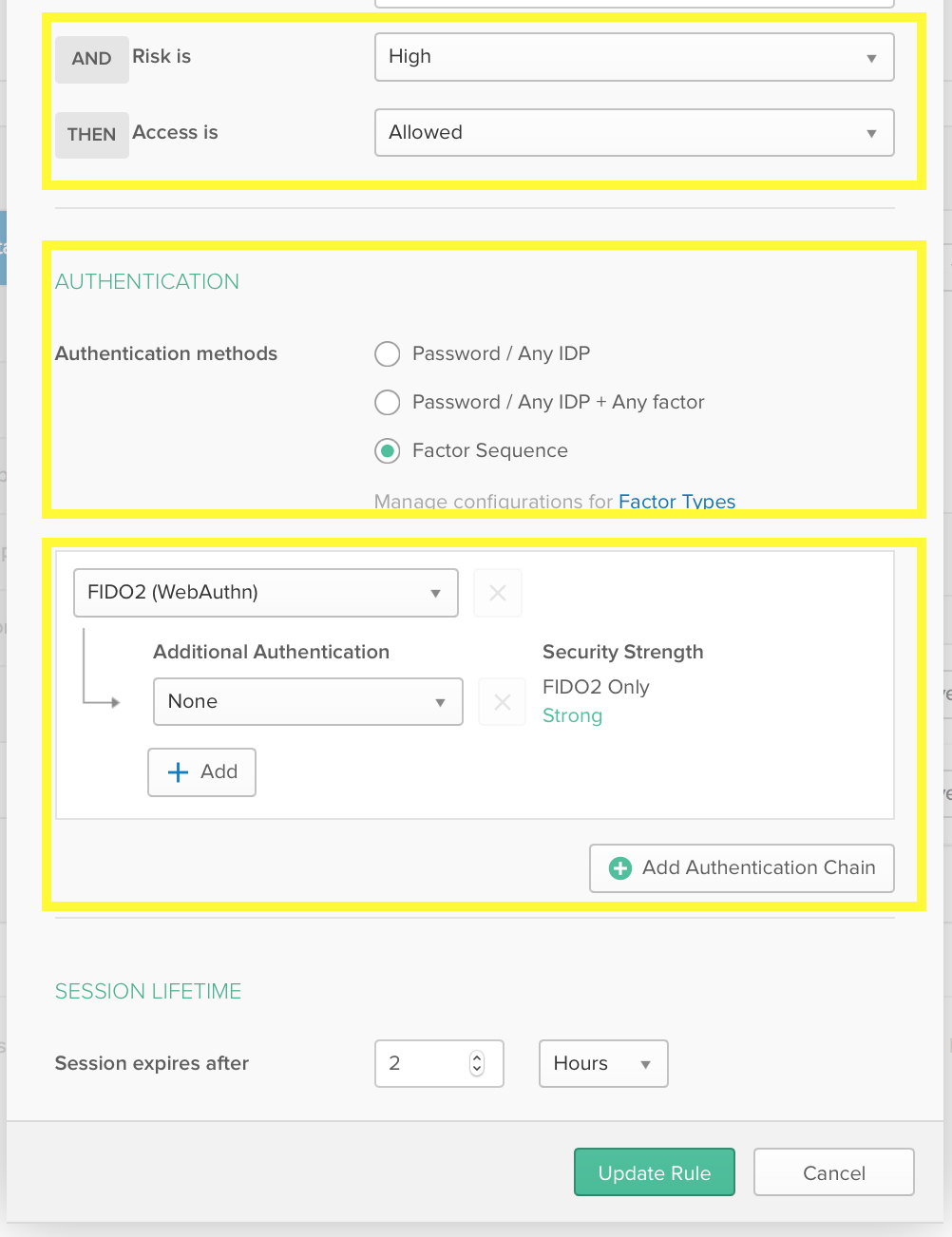
1. Head over to your org’s access policies and create a new sign-on rule.
2. You’ll notice updates to the UI that include defining a risk level, as well as customization on how to respond based on risk.
You’re all set! From here, you can start testing out the feature based on the risk levels defined in the UI.
Learn more
Risk-based Authentication is in its early stages today, and you can expect to see us expand the capabilities of this feature over the next few months and beyond.
Check out the resources below for more information:
- Documentation > Risk Scoring
- Data Sheet > Okta AMFA: Protect Against Account Takeover and Fraud
- MFA Deployment Guide