How to Centralize Identity for a Rapidly Changing, Distributed Workforce
In the past, centralizing identities has been associated with mergers and acquisitions (M&A) or domain consolidation efforts. More recently, organizations are being pushed to provide workplace resources to a remote workforce. And, as companies realize the benefit in productivity and cost savings, what began as a safety and health measure will morph into a normal operating pattern—on a global scale.
The Remote workforce
Recent surveys forecast that approximately 25-30% of the global workforce will be working from home multiple days a week by the end of 2021. Meanwhile, modern organizations are aiming for peak operational efficiency by sharing resources through B2B (business-to-business) partnerships. But how do security teams ensure their employees are adequately protected, and that partner users are properly authorized for access? And with employees and partners scattered throughout the globe, on disparate networks, how do IT teams give this workforce the same level of access they’ve come to expect?
As most companies have not designed their VPN infrastructure to accommodate their entire workforce, much less their business partners, traditional VPN solutions are falling short. Nightmare stories about latency in user experience, lack of multifactor authentication (MFA) and users bypassing VPN controls outright, are plaguing IT departments and rendering B2B use cases unactionable.
Enabling a distributed workforce
The route to enabling resources for a distributed workforce can vary. Resources may reside in a corporate data center or cloud-hosted, but the one constant in this equation is identity—the user who is requesting access. Identity has become the modern perimeter, where access and authorization are dictated by an individual user and their location. By extension, it accelerates enablement by also tying resources with users. Regardless of location or network, centralizing identity can provide secure access to appropriate services and their users.
The Okta Identity and access management framework
Okta, born in the cloud over a decade ago, continues to differentiate itself in the Identity space and be recognized as the standard for Identity and Access Management (IAM). An incredibly rich and sophisticated offering in the Okta catalog is Universal Directory (UD), a centralized metadirectory capable of consolidating identities from different networks and different user stores—all under one umbrella, as shown below. By having access to the entire identity set, IT and Security admins can configure access and authentication policies against those identities from a centralized platform, regardless of where they originated. Access control policies leveraging behavioral analysis accompanied by Okta Adaptive Multi-factor Authentication are just the tip of what is possible when admins have the definitive source anchor of a user’s identity.
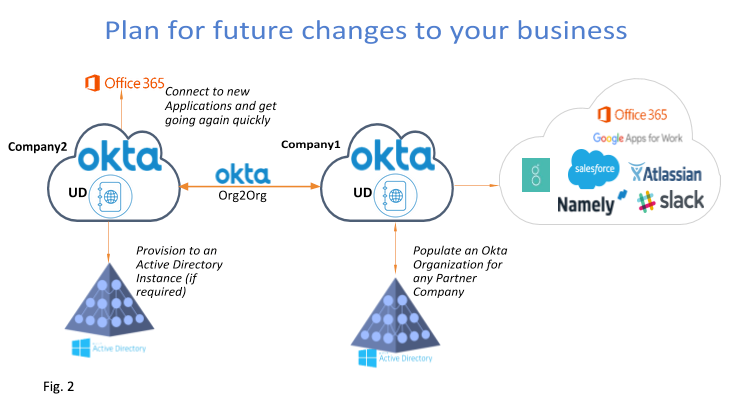
Okta’s Org2Org federation scheme can facilitate shared access to resources hosted in partner organizations. By establishing a trust between two parties, a direct federation is deployed to allow users from one organization to access resources protected and federated with the Identity Provider of the other (B2B). Once again, the core enabler in this scenario is Okta’s Universal Directory, which allows one organization to house the identities of users who attempt to access shared resources from another org, as shown below.
Any organization can seize the remote work opportunity
When a user attempts to access a resource, Identity is the one constant in a chain of attributes and metadata. The location, IP address, browser, device – even the end service – are all subject to change, and may not reflect real-time, downstream user action. So, as the linchpin of access and enablement, identity should always be the core tenant through which solutions are built. Centralization speeds up consolidation of disparate domains and scattered user stores, while facilitating the sharing of resources across an organization. Lastly, the modern ability to centrally store users (with granular security and access control policies) gives enterprise and mid-sized organizations the tools to withstand and build on an ever-changing technology landscape.
Whether you’re focused on delivering on IT initiatives or pushing forward with zero trust, identity should be the centerpiece of your enterprise’s access, enablement, and security. Centralizing identity is a straightforward path toward immediate value and business productivity.
Need to know more? Check out our page on The Importance of Centralized Identity Management. Interested in how to make your remote work infrastructure scale and grow overtime? Check out The Ultimate Guide to Dynamic Work whitepaper.