Okta Access Gateway + ThreatInsights = Protecting On-Prem Apps
At Okta, we love to secure access to everything from a single platform. This, of course, includes on-premises apps.
As spoiled here, our specialists wanted to weigh in on how OAG is at its best when paired with the features that make up the Okta platform. In other words, we’re giving you the Secret Sauce! This month, Senior Solutions Engineer, Bob Burgess, takes on the recipe for securing access to on-premises web apps.
In this post, I’ll show you how to combine OAG and Okta ThreatInsights to automatically mitigate identity attacks and account lockouts to on-prem web apps, at scale.
PS: For context, Okta Access Gateway (OAG) is a solution to secure access to on-premises web apps in a hybrid IT environment using Okta SSO and Adaptive MFA. If you want to learn the basics about OAG before diving in, click here.
The Challenge: The need to automatically mitigate coordinated identity attacks at scale
Organizations enabling remote access to on-prem web apps are subject to login attempts from anywhere. This includes legitimate users as well as bad actors, which will try to exploit your systems through identity attacks, which range from credential stuffing and password spraying to denial of service attacks via account lockouts.
Preventing these threats with legacy security is impossible since attackers, using coordinated attack techniques through distributed agents and Tor exit nodes, can easily work around traditional security controls (e.g., IP addresses, network blacklists, and firewall rules).
To mitigate these threats, organizations need a smart security control, capable of automatically detecting identity threats across IPs and regions. It must also scale to mitigate distributed attacks, and prevent denial of service attacks due to account lockouts.
The Solution: Combine Access Gateway and Okta ThreatInsights
Happily, Okta has a solution for this: Okta ThreatInsights.
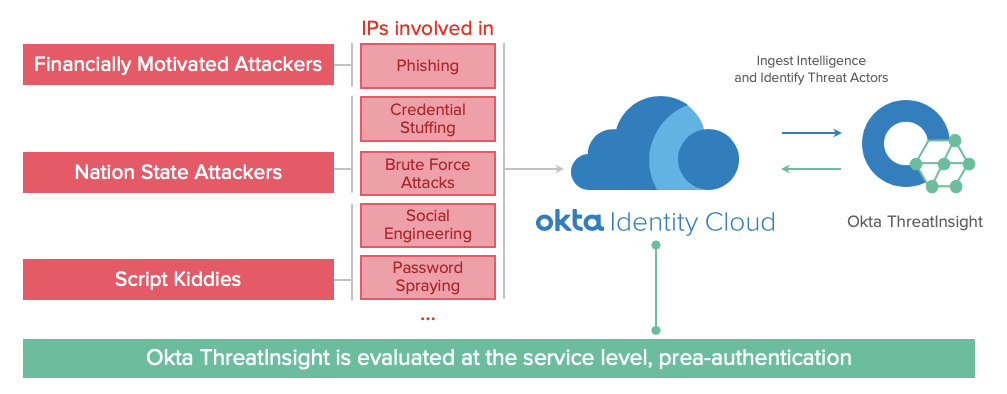
Okta ThreatInsights is an intelligent security control, available to all Okta customers, that evaluates billions of login attempts across all Okta orgs to detect and mitigate suspicious, anomalous, and risky behavior based on the various IP addresses that access the Okta service:
Proactively secure users with Okta ThreatInsight
When you turn Okta ThreatInsights on, it works for all applications secured by Okta. And of course, this includes the on-premises web applications secured via Okta Access Gateway. (A mind blowing moment for sure...).
What does it look like?
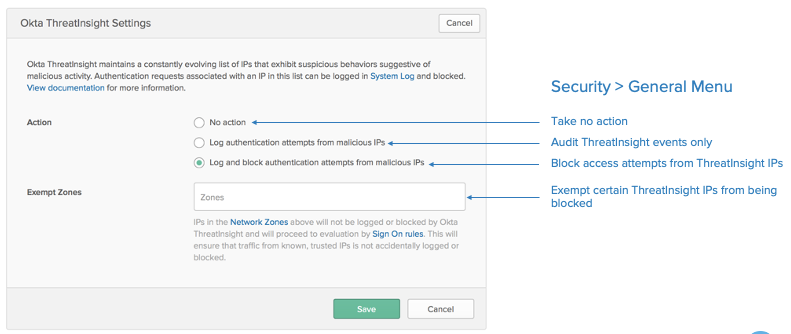
To enable Okta ThreatInsights, access Okta as an Administrator, and update the ThreatInsights under Security > General. ThreatInsights offers the option to just monitor/log events, to test the system efficacy, or to block suspicious events directly.
ThreatInsight Administration panel. For details, check our documentation.
With ThreatInsighs enabled, the login to all apps – including on-prem apps secured with OAG – will have the following steps:
-
User/malicious actor tries to access the app
-
User/malicious actor is redirected to Okta for login
-
User/malicious actor submits credentials
-
ThreatInsights checks the authentication access and the security thresholds before validating the credentials: If a malicious attempt is detected:
-
The malicious attempt is audited in your syslogs with details including the agent, geo location, and IP address.
-
The malicious attempt is blocked before the credential is validated.
-
-
Legitimate login requests are authenticated, authorized, audited, and then retrieved to Okta Access Gateway to complete access to the on-prem app.
By combining Okta Access Gateway with Okta ThreatInsight, you can proactively prevent bad actors from logging into on-prem apps or locking out accounts—all with just one setting in the admin console. With this setting enabled, Okta will identify threats in the ThreatInsight pool and block access from malicious actors at a pre-authentication level, allowing you to confidently enable your remote workforce to access on-prem web apps.
Interested in learning more about the secret features of Okta Access Gateway? Check out our previous series, The Secret Features of Okta Access Gateway.