4 Ways to Elevate Your Identity Game with Lifecycle Management
All types of companies struggle to keep up with the increasing pace of change in today’s business environment, especially as dynamic workforces become more prevalent. At the same time, employee, partner, and customer expectations for frictionless (but still secure) experiences are soaring. In this 5-part blog series, we’ll review the pivotal role that identity and access management plays in helping you address these demands—especially when it comes to getting your user lifecycle under control.
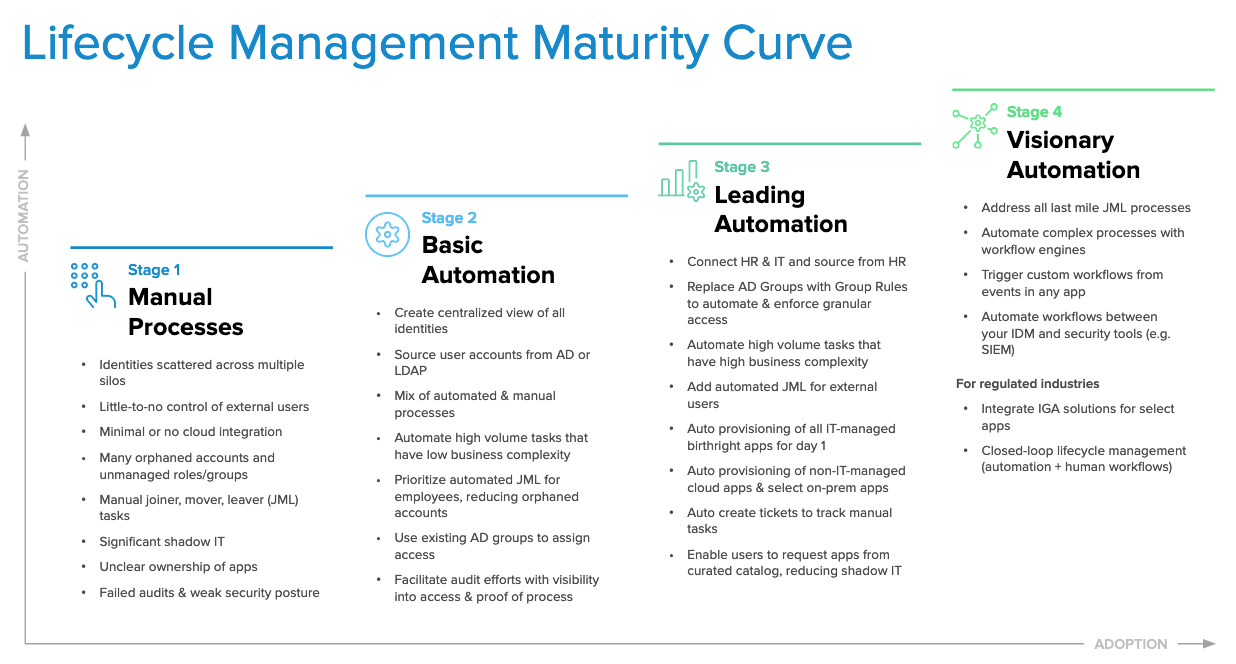
In particular, many of our customers embrace lifecycle management automation to streamline tedious provisioning, entitlement configuration, and deprovisioning processes as part of employee or contractor onboarding and offboarding. Over time, this LCM adoption matures with visionary LCM workflows that not only decrease costs but increase productivity and improve your security posture as well. Based on insights from working with the thousands of organizations who rely on Okta as their foundation for modern IAM, we developed our LCM maturity curve:
As you can see, each stage touches on four primary challenges that span the employee lifecycle from hire-to-retire (or any other user journey, for that matter):
- Managing identity data
- Managing identity lifecycle processes
- Managing access grants
- Managing audits and compliance
By incrementally modernizing these key elements of IAM in a staged manner over time, you can quickly realize initial time savings and achieve fast ROI, rather than trying to configure every possible feature of Okta Lifecycle Management all at once. And no matter how mature your identity strategy is, there are always ways to further advance automation in ways that help your IT and security teams save even more time and money.
Managing Identity Data
Of course, everything starts with your data. Properly managing identity data is all about creating a reliable system of record. It should span all of your users—primarily employees, but also contractors, partners, and customers. Any identity-related initiative, such as single sign-on (SSO), provisioning, or multi-factor authentication (MFA), requires a single view of everyone who needs access to your IT ecosystem. Creating this centralized view is never easy because it’s fraught with questions like:
- What is my authoritative source of user information?
- If I have multiple sources, how do I synchronize data between them?
- How should I create unique usernames and email addresses?
Managing Identity Lifecycle Processes
More and more, we’re noticing that identity lifecycle decision-making is no longer contained solely within IT. Increasingly, app owners and business unit managers also play a key role in determining who gets access to what. And today, many organizations’ provisioning and deprovisioning processes are driven by highly-customized business logic and policies that most solutions can’t handle out-of-the-box. This leaves your IT team with responsibility for at least some manual identity tasks that take them away from more value-added work.
Managing Access Grants
Another opportunity for offloading tedious work is by automating access decisions and enabling self-service for end users. This further reduces dependence on IT, and sets you up to securely and consistently grant access to new employees, contractors, partners, or other user types as your organization grows. However, with remote work environments driving up demand for things like new digital collaboration resources and temporary grants for elevated access, managing access grants is a lot more complicated than just turning on or off a light switch.
Most likely, you have to accommodate the following business requirements:
- Give people a variety of resources (applications, entitlements, roles, groups)
- Involve several stakeholders in access decisions (IT, business app owners, people managers)
- Meet individual needs through frequent exceptions (VIP accounts, parental leaves, alumni rehires)
- Take many confusing frameworks and models into account (attribute-based or role-based access controls, hierarchies, delegation)
Managing Audits & Compliance
Not to be overlooked, the last major hurdle to effective identity management is managing audits and compliance. While your security team is in charge of helping auditors understand who has access to what, IT is often asked to provide that data for them. Some organizations at the early stages of LCM maturity manage this in long spreadsheets of account info—a time-consuming process. Others implement sophisticated identity governance and administration tools to automate access reviews, adding yet another potential data silo. Regardless, automated access reporting and other advanced LCM strategies can ease your compliance burden.
To help organizations overcome each of these barriers at their own pace, our next four posts in this series will provide gradual steps to consider as you advance your adoption of Okta LCM. In part 2 of our series, Blaze Trails through Identity Data, we’ll provide a step-by-step guide to up-leveling your identity strategy. Along with a practical framework of best practices, it includes recommendations and goals for four common stages of lifecycle management maturity. Look out for it after August 28th!
Looking for more LCM knowledge right now? Learn more on our Lifecycle Management page.