A Deep Dive Into Okta FastPass
This blog post is the second in a series focusing on credential phishing. Previously, in the blog The Need for Phishing-Resistant Multi-Factor Authentication, Mukul Hinge explained how threat actors are becoming more sophisticated, using various tools to overcome mitigations. Today’s post digs into the inner workings of Okta FastPass, explaining how it serves to provide strong phishing resistance and device assurance.
It’s been about eight months since we made Okta FastPass generally available (GA) to all Okta customers on Okta Identity Engine (OIE). Okta FastPass is deployed at scale, and organizations see over 4 million monthly passwordless authentications. Okta customers like Intercom, Rubrik, and NTT DATA have enabled this frictionless passwordless experience for their end users.
What is Okta FastPass?
FastPass is a cryptographic multi-factor authenticator that provides passwordless authentication to any SAML, OIDC, or WS-Fed apps in Okta. It is a device-bound authenticator, meaning it can only be used to authenticate applications on the same device. Okta FastPass provides strong security across multiple user devices, on any operating system platform, at a far lower cost than deploying roaming hardware authenticators. It is available on Windows, iOS, Android, and macOS platforms, ensuring that end users on any device can get seamless, phishing-resistant access to apps and resources.
But to see it in action, watch this short video and demo on the Okta FastPass page.
Why Okta FastPass?
Okta FastPass users love a phishing-resistant, passwordless, consistent experience across platforms. Okta FastPass only requires one enrollment per device, which can be driven through the first authentication, and integrates seamlessly with the biometric capabilities on the supported platforms (including FaceID, Windows Hello, and fingerprint sensors, to name a few). This provides additional security and reduces the dependency on out-of-band factors such as OTP and push notifications.
IT Admins can sleep well at night knowing that:
- When the use of passwords is reduced, so is the attack surface.
- Helpdesk costs drop as requests for password resets become a relic of the past. After rolling out FastPass internally, Okta’s own IT team saw a reduction in password resets by 98%!
- End users get a better experience and sign in to their apps more securely but quickly.
- After FastPass enrollment, admins can easily view the rich device context collected and managed throughout the device’s lifecycle.
- With strong cryptographic binding between the authenticator and user identity, high assurance proof of possession, and origin domain verification, Okta FastPass can provide strong phishing resistance in line with the NIST guidelines.
- FastPass leverages device context signals (some collected by Okta Verify itself and others through MDM and EDR integration partners such as CrowdStrike and Windows Security Center) to help admins make policy decisions based on the device posture. A key example? Admins can block all access to jailbroken/rooted devices—that’s real leverage!
How does Okta FastPass work?
Device enrollment
The Okta FastPass journey begins with an enrollment (or adding an account) process on the Okta Verify app of your device.
This process is easy and fast, yet multiple ways exist to complete the enrollment. One of the easiest ways to enroll is inline enrollment. Admins can deploy the app to the end-user devices, and users will be able to enroll as part of their normal authentication process!
In another method, If you are already authenticated on a desktop device, you can generate a QR code to scan from your mobile device, complete enrollment, and begin the FastPass journey.
But suppose you are on a desktop device or enrolling for the first time? In that case, you’ll need to authenticate using another method (for example, email magic link, SMS for true passwordless, or password—if your organization is still using them). Okta provides several ways to ensure that first-time user activation is secure for admins. For example, admins can pre-enroll users in SMS MFA prior to activation.
Behind the scenes, and when available, Okta Verify generates public/private key pairs using the device’s Trusted Platform Module (TPM) and sends the public key along with some device context metadata to Okta servers. The private key remains securely stored in the device’s TPM. Here is a data flow diagram of FastPass enrollment:
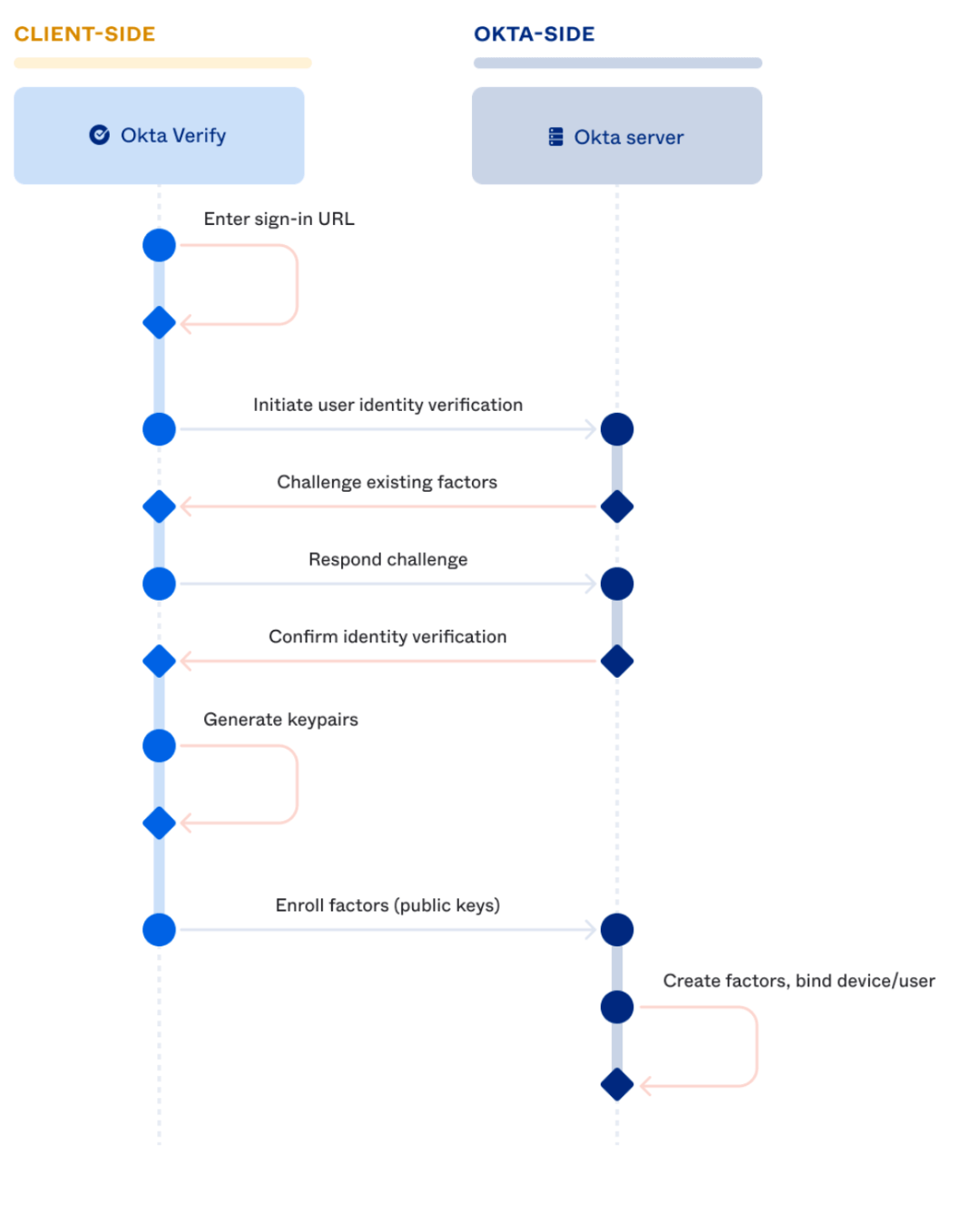
Successful completion of these steps means the user is enrolled into “Proof of possession” and optionally (if the user enabled biometric verification) “User verification” factors! Note that if the user enables biometric verification, an additional set of public/private keys are generated from the TPM, and the public key is sent to Okta’s servers.
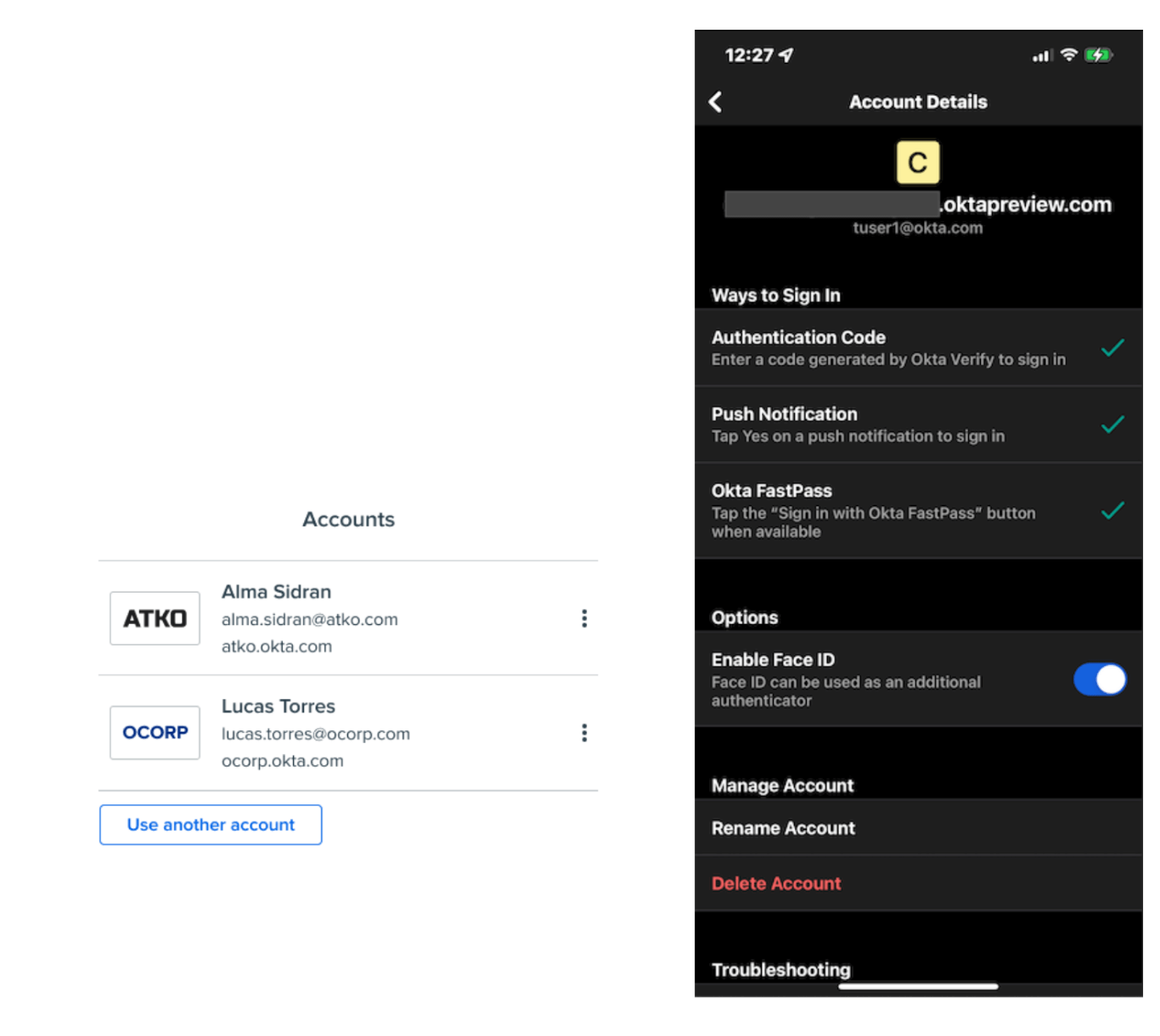
Below are screenshots of FastPass enrollments in the Okta Verify app on macOS and iOS devices.
Authentication flows
To support multiple platforms and provide a consistent user experience, Okta FastPass uses numerous ways to perform authentication, known as probing schemes on various platforms. There are two broad categories of probing schemes. “Silent probing,” where the Okta Sign-In Widget automatically checks if FastPass is configured on the device, can be used to authenticate the user. “Interactive probing” occurs when the user clicks the Sign in with Okta Verify button. FastPass always tries silent probing before falling back to interactive probing.
Below are the various probing schemes FastPass uses:
|
Method Name |
Method Type |
Supported Platforms |
|
Loopback |
Silent |
macOS, Windows, Android |
|
Credential SSO Extension |
Silent |
iOS, Safari browser on macOS (managed devices only) |
|
AppLink |
Interactive |
Android |
|
Custom URI |
Interactive |
Windows, macOS |
|
Universal Link |
Interactive |
iOS |
Loopback server
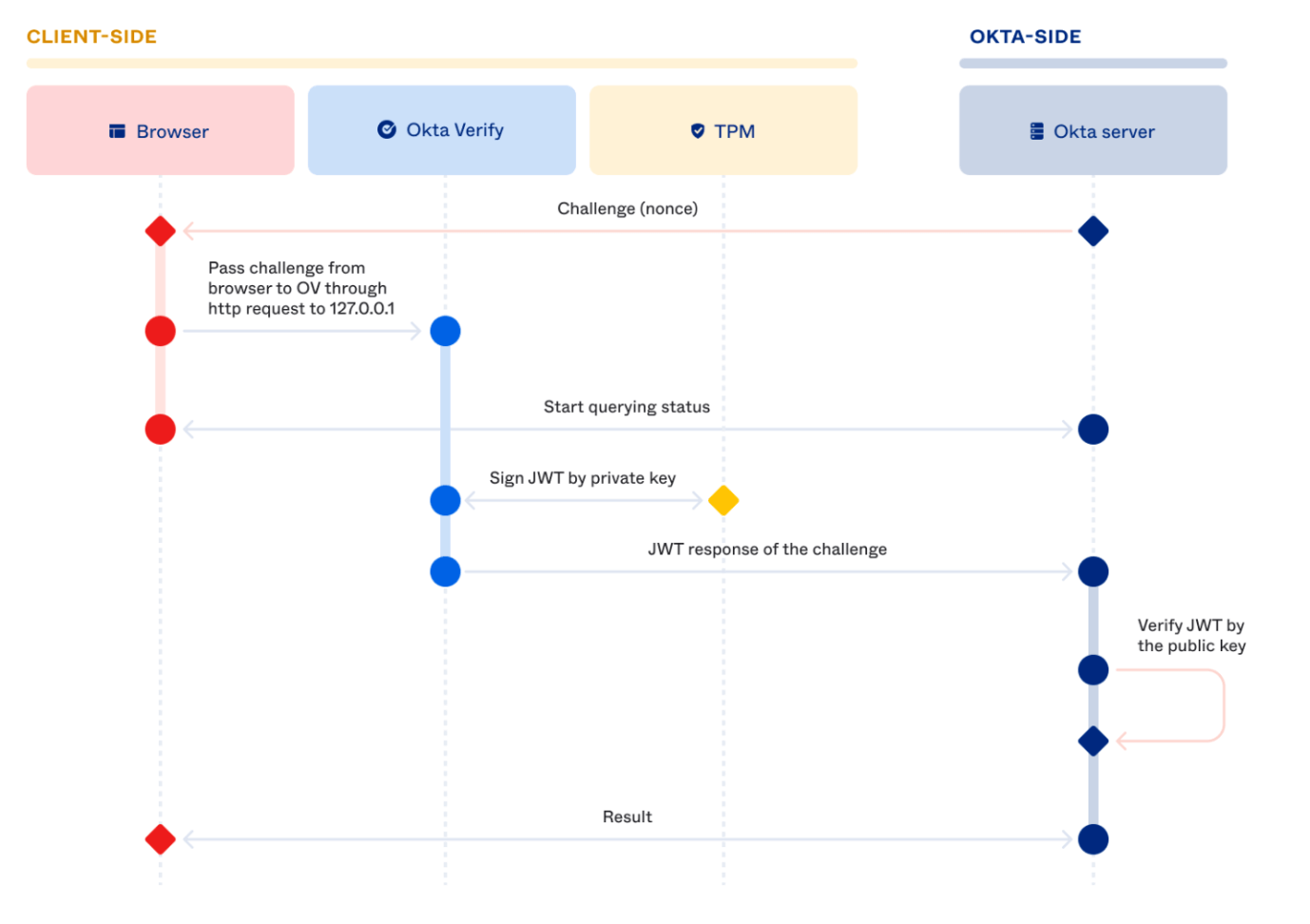
Okta Verify runs an HTTP server on the device on a local host port that listens and responds to probing requests from the Okta Sign-In Widget.
For example, when you log in to an app protected by Okta, you will be redirected to the Okta Sign-in Widget for authentication. The Okta Sign-In Widget silently interacts with the Loopback server.
The Loopback server sends a challenge signed with the private key along with the origin domain and device context signals, which the server can verify. If the policy conditions are met, the Okta backend will generate a SAML assertion (or OIDC access token) and redirect the browser to the service provider.
Credential SSO extension
This probing scheme is available only on Apple devices managed by an MDM provider on the Safari browser. It leverages Apple’s Extensible Single Sign-on framework. It involves configuring the SSO Extension setting on the MDM provider console to push an MDM profile to the end-user devices. Apple’s SSO framework then invokes the FastPass SSO extension for the HTTPS requests going to the configured domain, for which the FastPass can dynamically generate headers and sign. Check out the documentation for configuring the SSO FastPass experience on iOS and macOS.
AppLink, Universal Link, and Custom URI
App Link, Universal Link, and Custom URI are platform-provided app launching mechanisms with deep linking capabilities in Android, iOS, and macOS, respectively. During the authentication flow, the Sign in with Okta FastPass button on the Okta Sign-In Widget leverages these platform-provided features to launch the Okta Verify app along with the challenge request for FastPass to process and authenticate.
Device assurance
In addition to providing strong passwordless cryptographic authentication, Okta FastPass allows admins to configure policies based on the device context. Okta FastPass uses the device posture signals gathered by the Okta Verify app and/or third-party integrations (Tanium, CrowdStrike, Windows Security Center, etc.) to help enforce policy conditions.
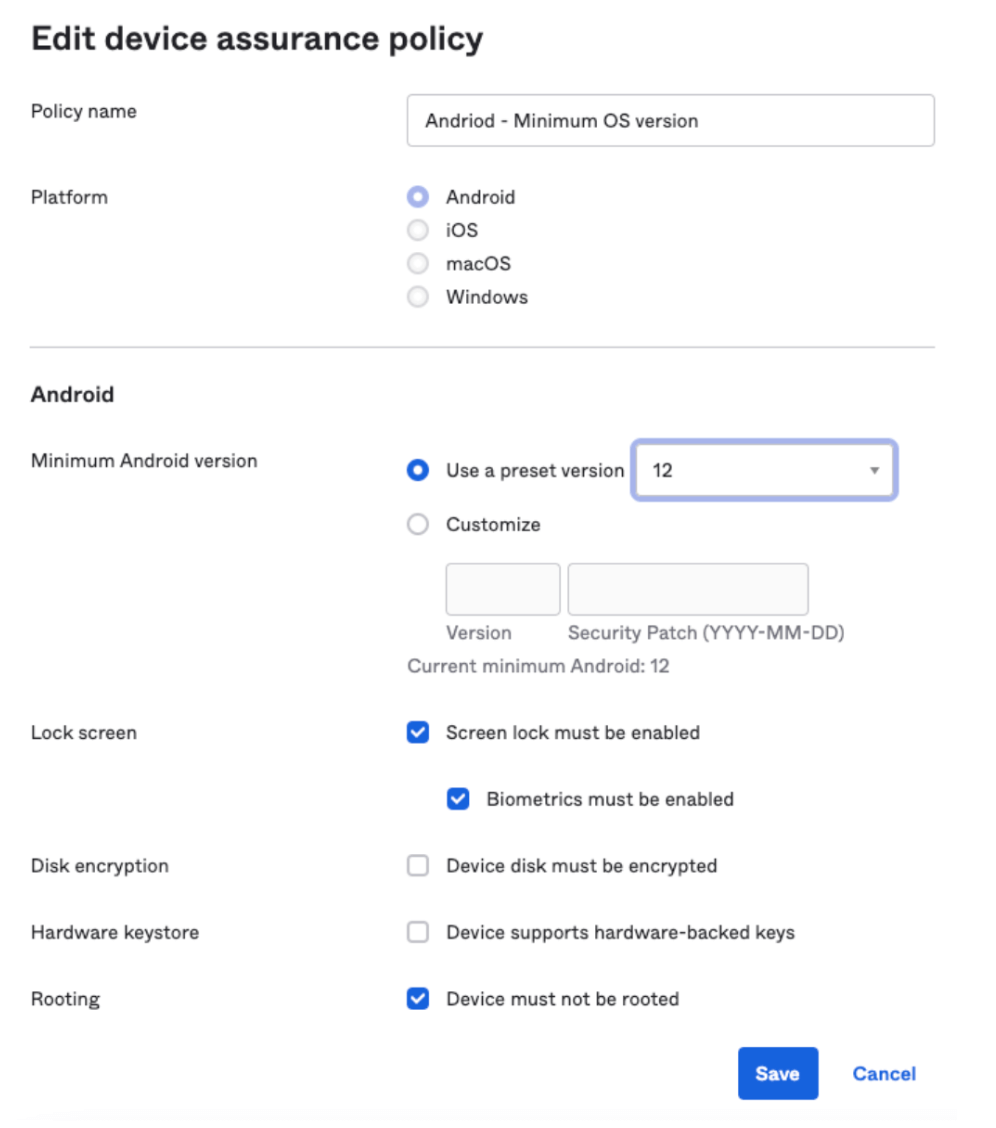
Device assurance policies allow administrators to control access to company resources. They can be created once and reused in multiple authentication policy rules. Here is a screenshot of a device assurance policy that ensures the Android OS version is 12 or higher, the user has setup password and biometric, and the device is not rooted.
Additionally, we have added a health check screen to Okta Verify, which alerts users about their device posture and recommends corrective actions.

Phishing resistance
Okta FastPass provides strong resistance to credential phishing attacks. The Loopback server and the SSO extension methods described above have strong phishing resistance capabilities. The fallback methods, such as Universal Links (iOS), Custom URI (macOS), and App Links (Android), do not provide the same level of phishing protection. However, we can use some of these methods to launch Okta Verify and enable users to authenticate using the phishing resistance bindings such as the Loopback server. Okta’s policy configuration page guides the admin to configure the app sign-on policies with phishing resistance correctly.
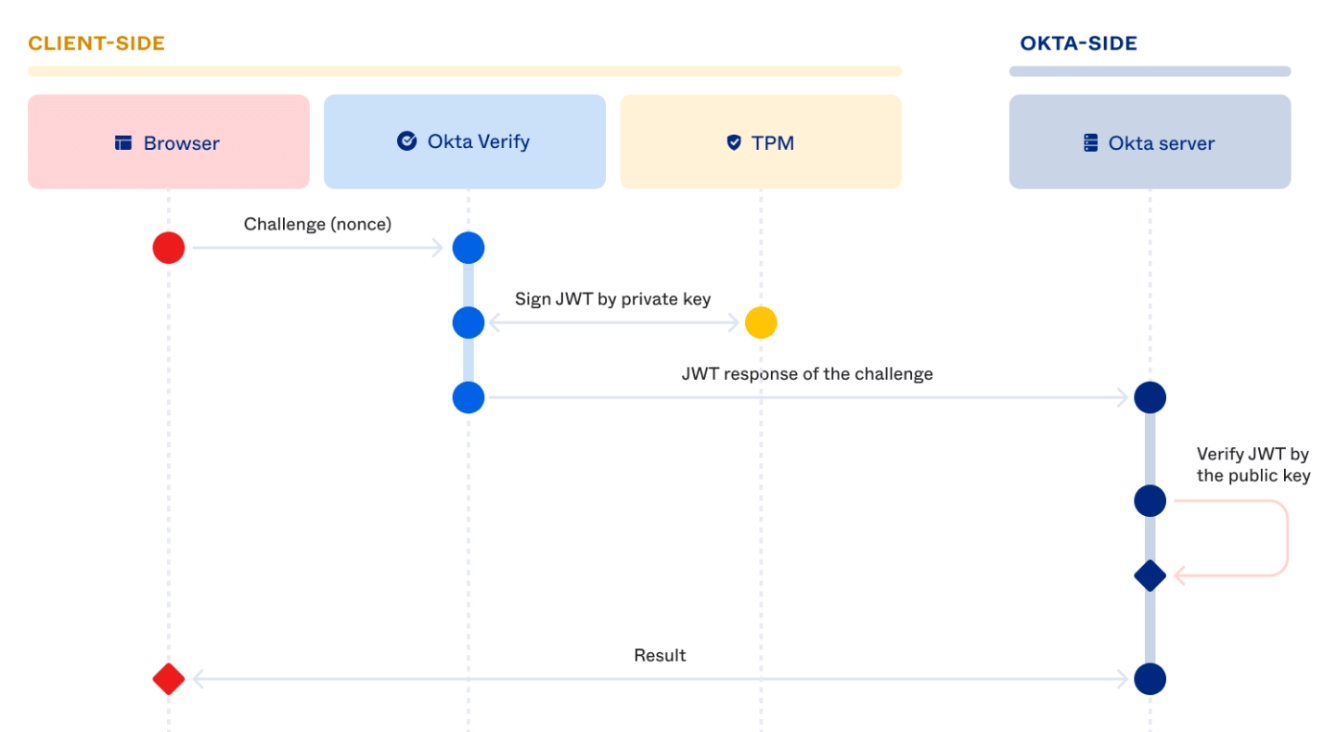
The below diagram shows how Okta’s Loopback server binding helps in preventing phishing attacks involving an adversary in the middle attack using a proxy server such as evilginx.
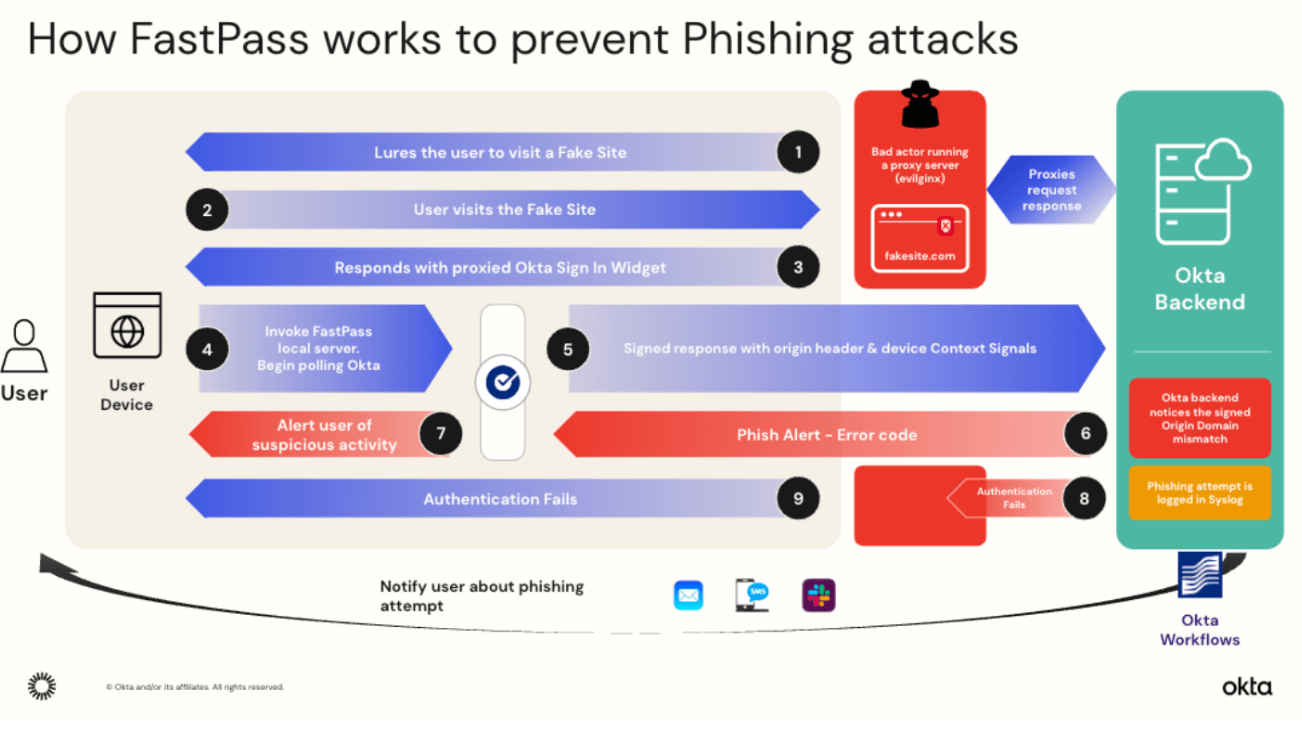
Since Okta FastPass includes the origin header in the signed response payload, Okta can easily detect the domain mismatch throw and alert administrators and end-users, in addition to rejecting the authentication request.
Admins can use Okta Workflows to alert the end-user through a back channel such as Slack or email or to take other actions such as blocking traffic to and from the phishing site.
Combining this with device assurance policies, Okta can provide strong protection from other forms of endpoint attacks, such as malware or ransomware. Okta’s partners, such as Crowdstrike and Windows Security Center, can provide valuable signals on the presence of malware on the device, which Okta leverages to enforce strong authentication policies.
What’s Next?
For the last eight months, we have been working closely with our customers (both internal and external), listening to their feedback and suggestions for improvement. We have fixed several UX issues and incorporated suggestions to make FastPass even better for our customers. We have hardened our mobile apps (using obfuscation and tamper detection, for example), collected additional device context such as jailbroken or rooted devices, and queried devices for having a passcode, to name a few. This empowers admins to make policy decisions based on device assurance levels. This is especially important for BYOD scenarios.
In the coming months, we’ll be working on improving the user experience, providing more information to let users unblock themselves in error situations—without compromising security. By partnering with other security vendors, we’ll gather more device posture signals () to empower admins to block potentially compromised devices. We’ll also add functionality to provide more visibility to the administrators and phishing attempts.
To sum it up, FastPass provides robust, seamless, frictionless, and phishing-resistant authentication to the end-users while delivering peace of mind and cost savings for companies.
Take the next step:
- Read the Okta FastPass Documentation for more details and how to configure FastPass in your organization
- What to start the passwordless journey in your company? Contact Okta Sales

