Okta and Google Chrome Enterprise: Enhanced application protections with device assurance
As the digital landscape evolves, the need for robust security measures becomes increasingly critical. Organizations are constantly exploring innovative ways to ensure secure access to their systems and data. In this pursuit, Okta has taken a significant step forward by integrating its device assurance policies with Google's Device Trust Connector for managed Chrome browsers.
As most of the workforce uses Chrome to connect to the internet, administrators can use the power of Okta’s device assurance with Chrome browsers on ChromeOS, macOS, and Windows devices to secure applications. This huge adoption is an organic path for Okta to also leverage Chrome to collect new signals and empower administrators to make access decisions based on comprehensive device assurance policies.
Devices that use this integration must be enrolled in Chrome Browser Cloud Management or, in the case of Chromebooks, Chrome Device Management.
Device Trust connector is a Google Chrome service that provides a way to verify the security posture of a device via the Chrome browser before granting access to a protected application. Chrome browser collects a variety of device signals securely, including operating system, browser version, security patch levels, and disk encryption. Okta uses these signals per request to determine whether a device is compliant with a set of device assurance policies before making access decisions.
For example, an admin could create a device assurance policy in Okta that requires all users to use a managed Chrome browser with the latest security patches installed. If a user attempts to access a protected application with a non-compliant Chrome browser, they will be denied access.
How does it work?
The following flow describes how Okta collects device signals from Google Cloud and uses them during a device assurance evaluation.
A detailed diagram of actions taken by Okta and Google to secure the protected application.
The power of device assurance policies
Okta’s device assurance policies play a pivotal role in determining access privileges within an organization. These policies consider various factors such as device signals, compliance, and security posture to evaluate the trustworthiness of a device. By integrating with Google's Device Trust connector APIs, Okta can now gather essential device posture signals from the Chrome browser, ensuring a more comprehensive assessment of the device's security state.
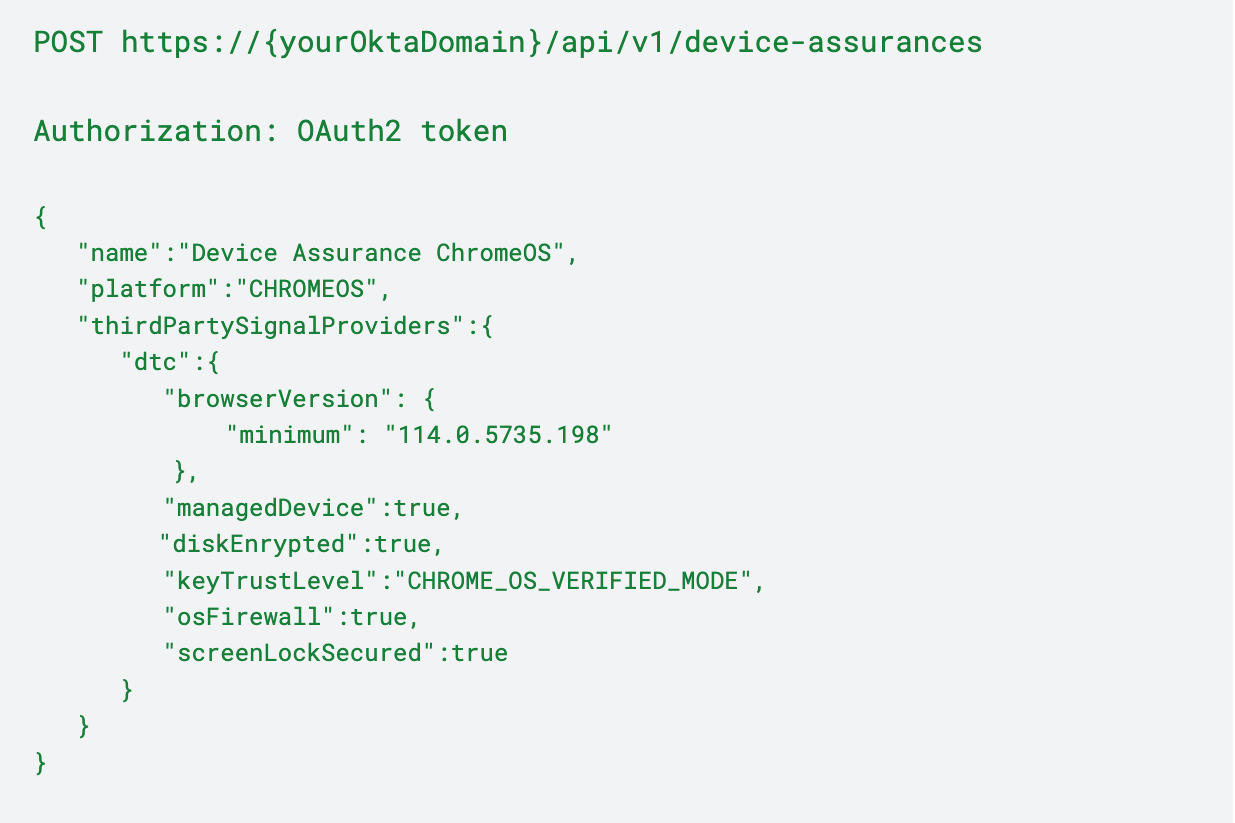
Device assurance for ChromeOS
Below is an API example of creating a device assurance policy for a ChromeOS device that must meet restrictions including device management, disk encryption, and firewall.
Stronger device assurance using Okta FastPass and Chrome signals on Windows and macOS devices
The Okta service can collect device signals from Chrome’s Device Trust connector, along with Okta FastPass using Okta Verify, on Windows and macOS. (Device Trust connector API for signal collection isn’t available for mobile devices, but stay tuned.) This provides administrators with additional security levers to configure phishing-resistant factors with FastPass and to check if the device is MDM managed.
Define the device assurance policy
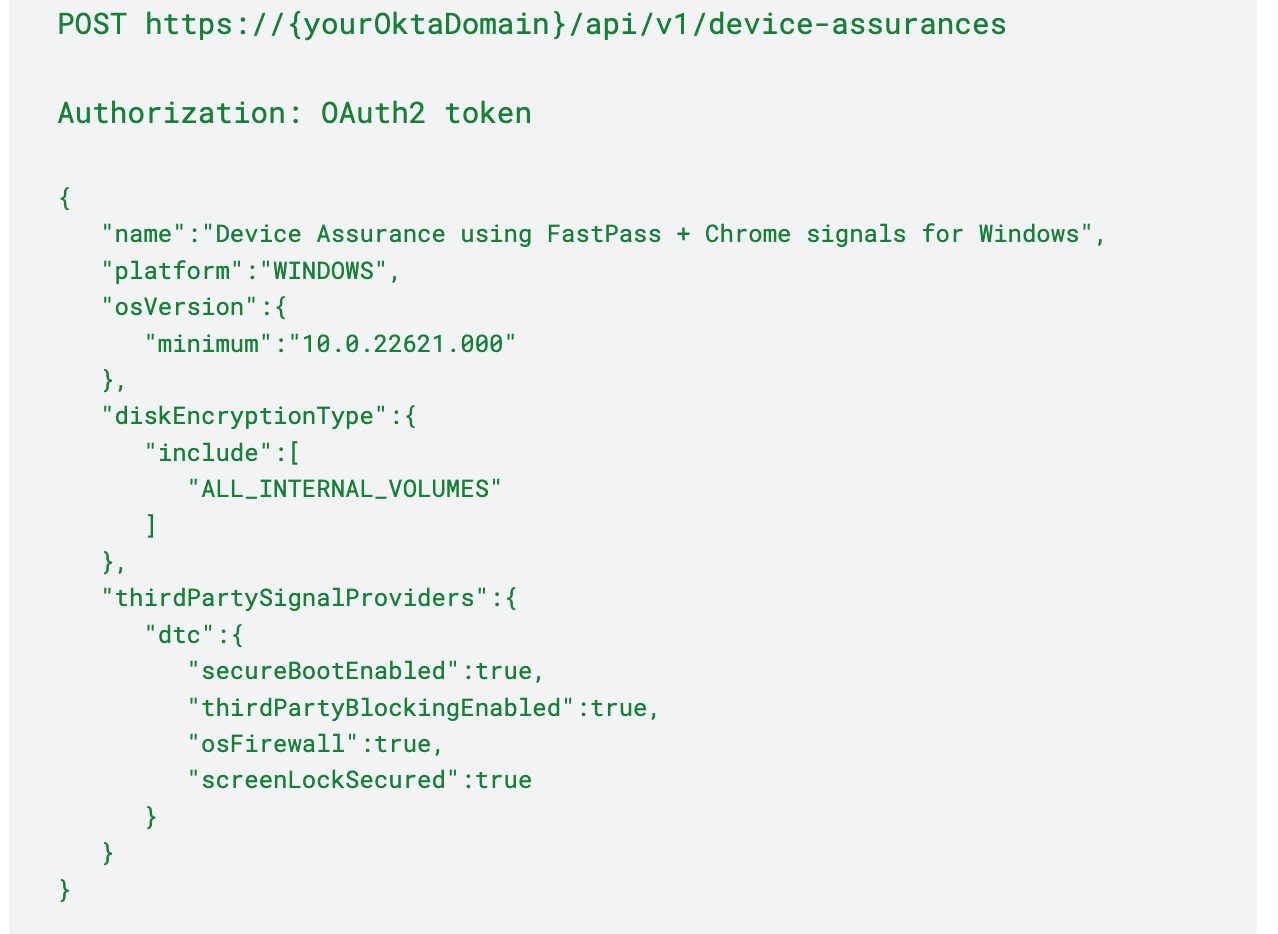
Windows
The following example shows a device assurance policy for Windows, wherein signals from Okta Verify and Chrome Device Trust connector are used to evaluate device context. The policy will evaluate the minimum OS version and disk encryption signals collected from FastPass and secure boot, 3rd-party blocking, firewall, and screen-lock signals from the Chrome Device Trust connector. As a next step, you would then associate this device assurance policy with the app sign-on policy.
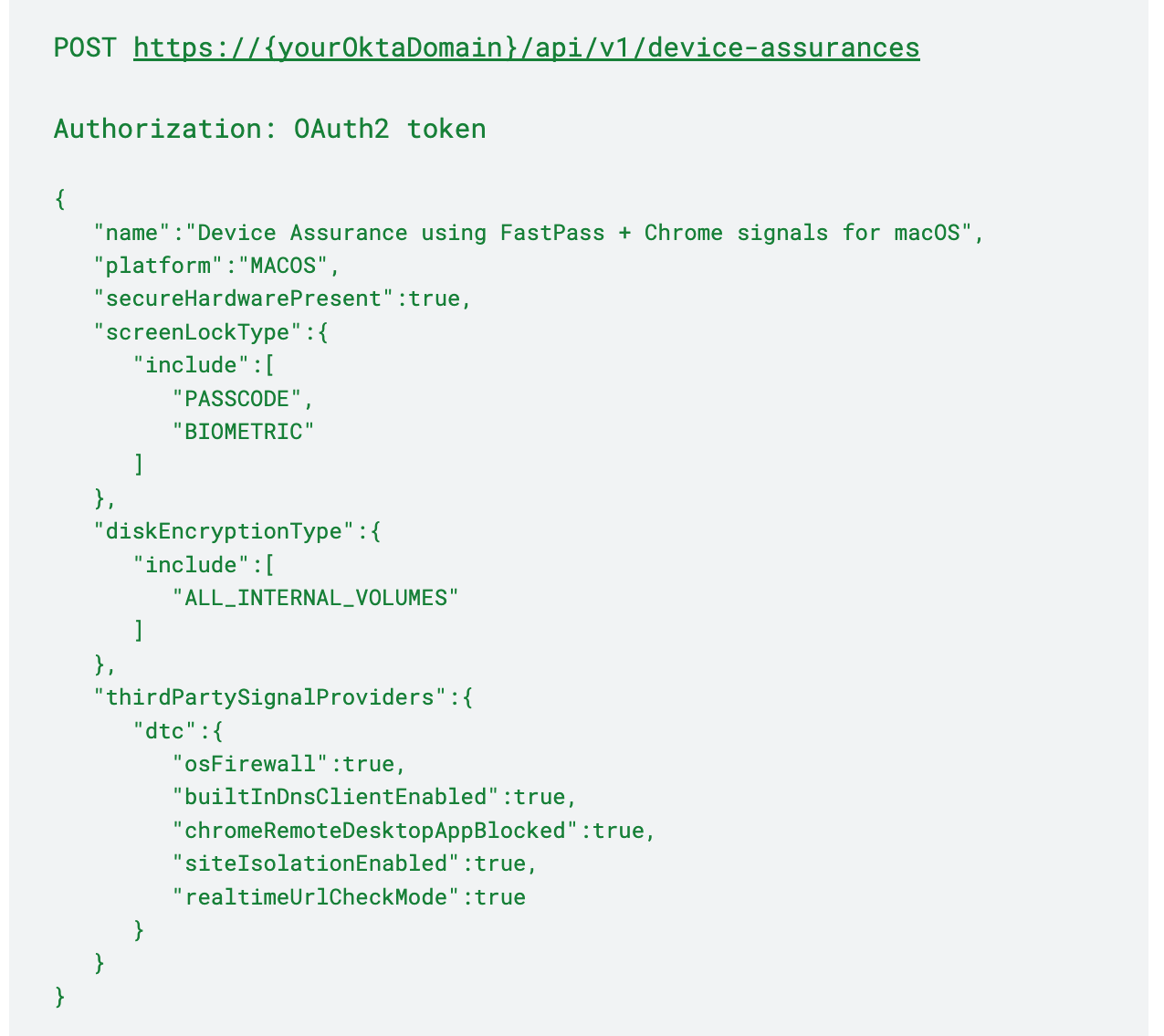
macOS
The following example shows a device assurance policy for macOS, where signals from Okta Verify and Chrome Device Trust connector are used to evaluate the device context. The policy will evaluate secured hardware checks, screen-lock types, and disk encryption signals collected from FastPass, as well as firewall, DNS settings, site isolation, and URL check signals collected from Chrome Device Trust Connector. As a next step, you would associate this device assurance policy with the app sign-on policy.
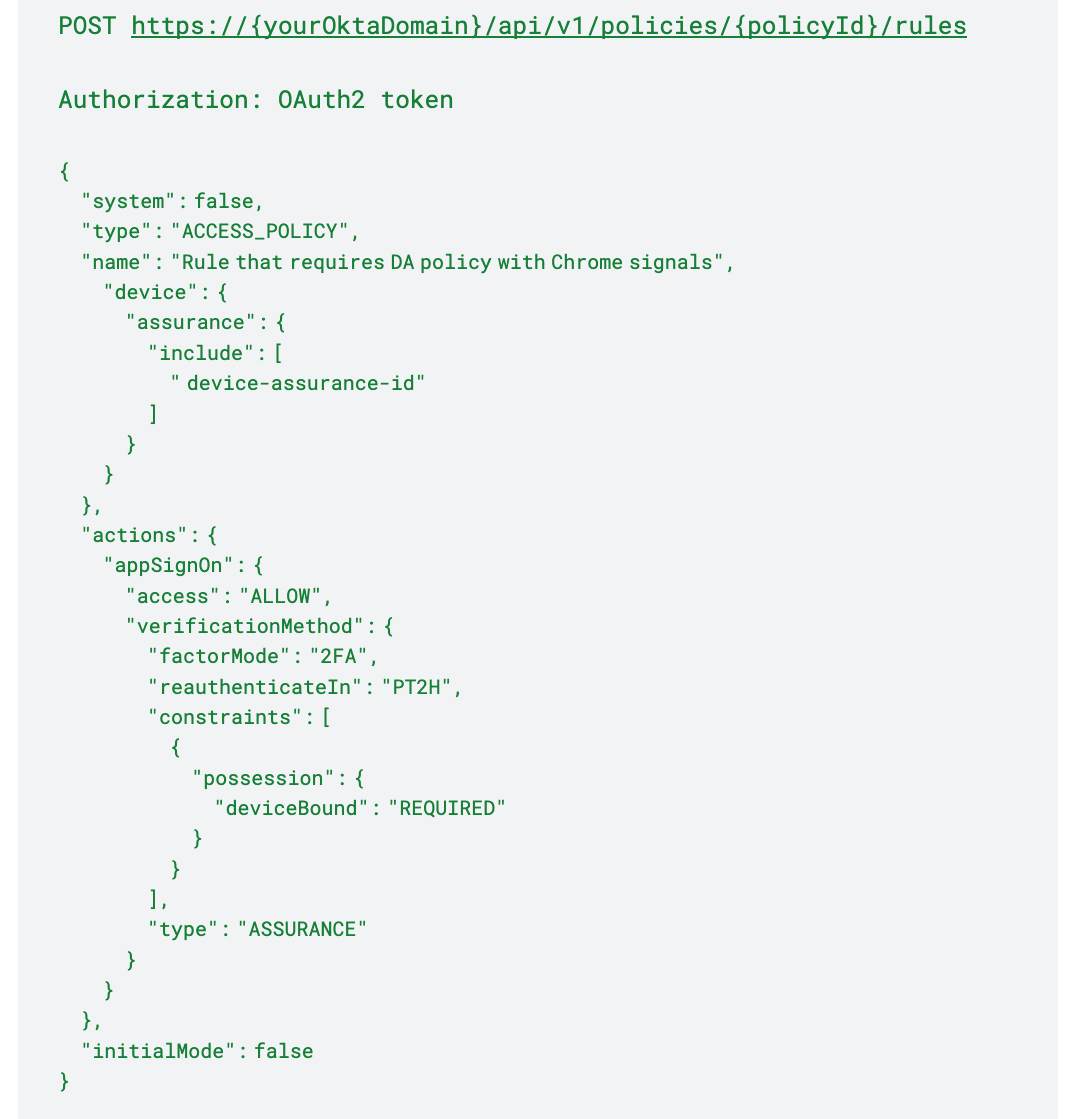
Configure the above device assurance policy with an app sign-on policy rule
After creating a device assurance policy, you will need to associate it with an app sign-on policy rule. Please note that multiple device assurance policies can be used in a single app sign-on policy rule, and only the device assurance policy with the matching platform will be executed.
You could add additional controls within the sign-on policy such as a requirement for a device-bound authenticator and multiple factors to provide more security.
The following example creates an app sign-on policy rule that has an Allow action with 2FA and a device assurance whose id is device-assurance-id. You can get the device-assurance-id from the response of the POST /api/v1/device-assurances.
You can read more about configuring app sign-on policy rules with device assurance.
Seamless integration for enhanced access control
The integration of our device assurance policies with Chrome Device Trust connector APIs brings several benefits to organizations seeking robust access control solutions. Let's explore some of the key advantages.
Comprehensive device posture signals
Okta can now tap into a wide range of device posture signals collected by the Chrome browser. This includes information on device integrity, security patches, encryption status, and more. By leveraging these signals, Okta gains a deeper understanding of the device's security status, allowing administrators to make more informed access decisions.
Real-time assessment
Okta can now monitor and evaluate the latest device posture signals by collecting the latest signals from the Chrome browser at every access to secured resources protected byChrome-based device assurance policies. This ensures access decisions are based on the most up-to-date information, reducing the risk of unauthorized access by potentially compromised devices.
Adaptive access control
With device assurance and Device Trust connector, administrators can enforce access policies based on the specific device posture signals collected. For example, if a device lacks critical security patches or exhibits suspicious behavior, access can be automatically restricted or additional authentication factors can be enforced.
This adaptive approach to access control helps organizations maintain a robust security posture. Okta will also provide end-user-specific messages to self-remediate issues the end user can control, such as browser version updates and enabling screen locks. This decreases the amount of time spent assisting end users, freeing up administrator/support time.
Simplified administration
Integrating Okta and Device Trust connector APIs streamlines the administration process. Device assurance policies can now be set within Okta's centralized management console, with devices and users managed in Chrome Browser Cloud Management.
Strengthened security ecosystem
By leveraging Google's Device Trust connector APIs, Okta has further fortified its security ecosystem. This integration complements Okta's existing capabilities, such as FastPass and CrowdStrike integration, providing organizations with a comprehensive solution for managing Identity and access across diverse devices and platforms.
How to get started
To start the integration, you will need to:
- Make sure your Chrome browser/ChromeOS device is Chrome Browser Cloud Management managed or MDM managed.
- Enable the Device Trust connector APIs for the managed Chrome browser in your Google Cloud project.
- Enable Device Trust Connector by adding a Chrome Device Trust integration under Security > Device Integrations > Endpoint security, in Okta’s Admin Console.
- Create a device assurance policy that uses the Device Trust Connector signals for the supported platforms under Security > Device Assurance Policies, and link it to an app sign-on rule.
Once you have completed these steps, users who attempt to access protected resources from a managed Chrome browser will be checked against the device assurance policy. Access decisions will be evaluated against the latest signals collected during the authentication flow.
This integration marks a significant milestone in enhanced security and access control. Okta can now leverage Chrome browser's device posture signals to make informed access decisions based on comprehensive device assurance policies.
And organizations can now embrace a more adaptive and robust approach to access control, ensuring that only trusted devices gain access to critical systems and sensitive data. Okta continues to be at the forefront of innovation, empowering organizations to build a secure digital future.
Review Okta’s Chrome Device Trust documentation for additional information. To learn more about Okta device assurance, read our feature announcement blog.


