Navigating credential and fraud risks: The phishing resistance authenticator effect
Image generated using DALL·E 2
This blog explores the robust security benefits of phishing-resistant authenticators, which can significantly bolster an organization’s cybersecurity measures beyond the scope of phishing attacks. The percentage of phishing-resistant authentications serves as a tangible indicator of an organization’s proactive use of these authenticators. We firmly believe that this data-driven analysis, drawing from cyberattack events across numerous organizations, can compellingly advocate for organizations to redouble their efforts in adopting phishing-resistant authenticators.
Phishing-resistant authenticators are designed to prevent real-time phishing attacks by not revealing sensitive authentication data to fake applications or websites. This is achieved by cryptographically binding the channel being authenticated to the output of the authenticator. For instance, in an Adversary in the Middle (AitM) attack, if a phishing attempt leads the user to a fake login page, the attacker cannot replicate the response's cryptographic binding, making the authenticator resistant to phishing attacks.
Okta supports several phishing-resistant authenticators, including:
- Okta FastPass, a device-bound passwordless authenticator
- FIDO2 WebAuthn authenticators (security keys)
- Device-bound FIDO2 WebAuthn authenticators (e.g. FaceID, TouchID, Windows Hello)
- PIV smart cards
- Hardware-based security keys (e.g., YubiKey)
It’s clear that the phishing-resistant factor is the gold standard for preventing phishing attacks, as documented in CISA’s phishing-resistant multi-factor authentication (MFA) factsheet. However, there are more reasons to be phishing-resistant, albeit not particularly related to phishing attacks.
Credential and fraud risks
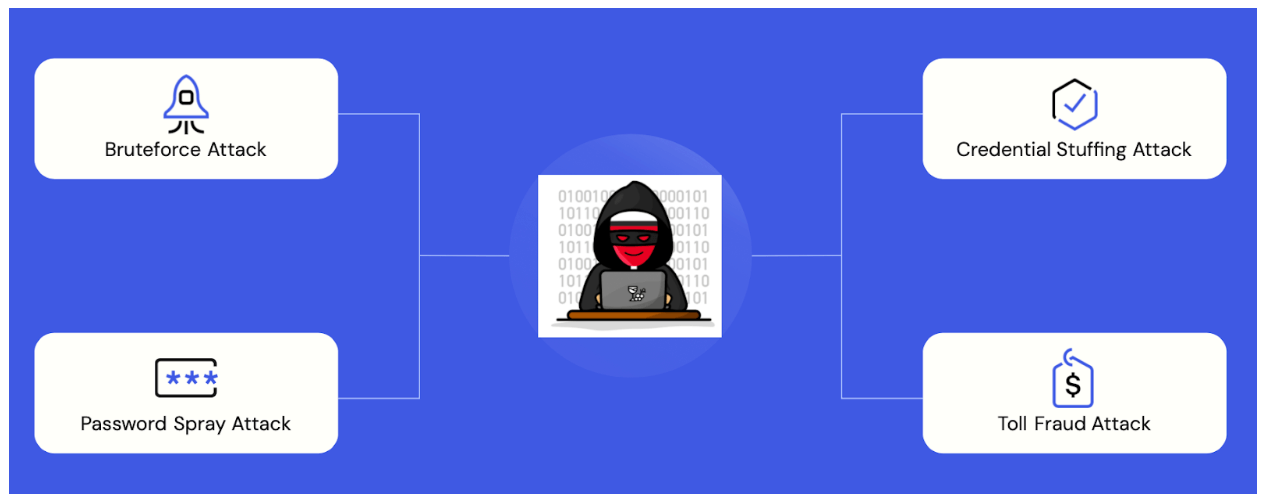
Here, we consider four common credential and fraud risks in Identity and Access Management (IAM) as we detect and prevent them at Okta:
Brute-force attack: In a brute-force attack, threat actors use trial and error to take over accounts. These attacks are typically slow and aim to take over a large number of accounts.
Credential stuffing attack: In a credential stuffing attack, threat actors acquire credentials from a breach/password dump site or darknet. The threat actor then uses automated tools to take over accounts with those credentials.
Password spray attack: In a password spray attack, threat actors identify valid usernames and then attempt common passwords against the usernames, hoping for a successful account takeover.
Toll fraud attack: In a toll fraud attack, fraudsters artificially generate a high volume of international calls/SMS on expensive routes to make money.
Okta has multiple detection and prevention mechanisms to counter the above tactics, techniques, and procedures (TTP). For instance, Okta ThreatInsight aggregates data about sign-in activity across the Okta customer base to analyze and detect potentially malicious IP addresses. Admins can configure account lockout functionality to lock out users after several unsuccessful attempts that can be configurable. We have an anti-toll fraud system to protect our systems from toll fraud while providing reliable telephony service to our customers using a heuristic engine, machine learning, and rate limit framework.
To understand the phishing resistance authenticator effect on the credential and fraud risks mentioned above, we compile the detections triggered by Okta’s detection systems. This is formally defined as:
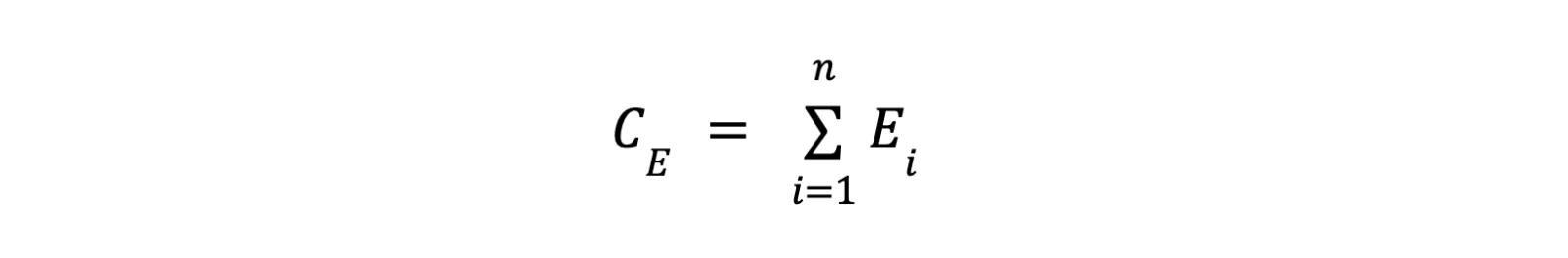
where
- CE represents the total credential and fraud events count for an organization for a given time window as detected by Okta. The time window for aggregation can be a day, a week, or a month. We have chosen a month as the time frame for deriving a sample for an organization.
- Ei represents security events for each detection for a given time window, where i ranges from 1 to n, indicating the sum of all cyberattack events from 1 to n.
The credential and fraud risks term is then computed and normalized as the ratio of the CE to the maximum possible event count:
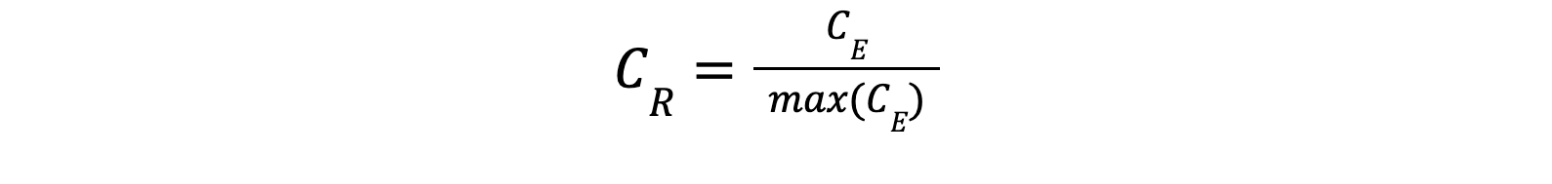
Phishing resistance measure
An excellent way to evaluate the use of phishing resistance authenticators in an organization is the ratio of the number of phishing resistance transactions to the total transactions:
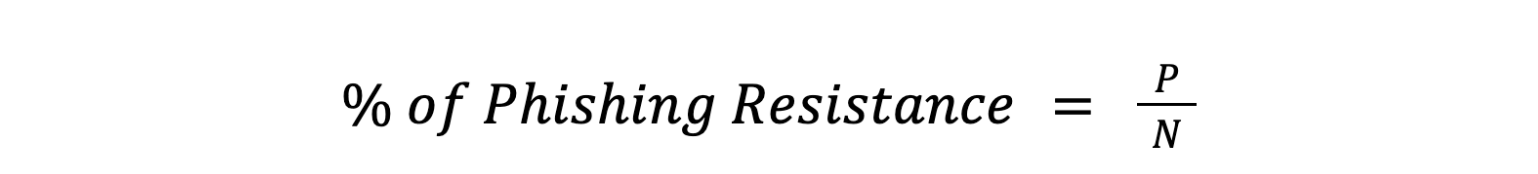
where
- P represents the number of phishing resistance transactions (enrollments, logins, recoveries).
- N represents the total number of transactions.
Phishing resistance and risks: The relationship
We have compiled all the security events as detected by Okta over eight months between January 1, 2023, and August 30, 2023, for the aforementioned attack vectors. We have also computed the corresponding phishing resistance score for each sample record for our analysis.
We want to understand the relationship between the credential and fraud risks (CR) and phishing-resistant transactions while addressing inherent data noise. We followed a systematic methodology of binning and aggregation. We first discretized values into defined logarithmic bins and then computed mean credential and fraud risk values within each bin for structured analysis. This approach attenuated noise-related fluctuations and provided a more cohesive representation of the relationship between the credential and fraud risks and the use of phishing-resistant authenticators.
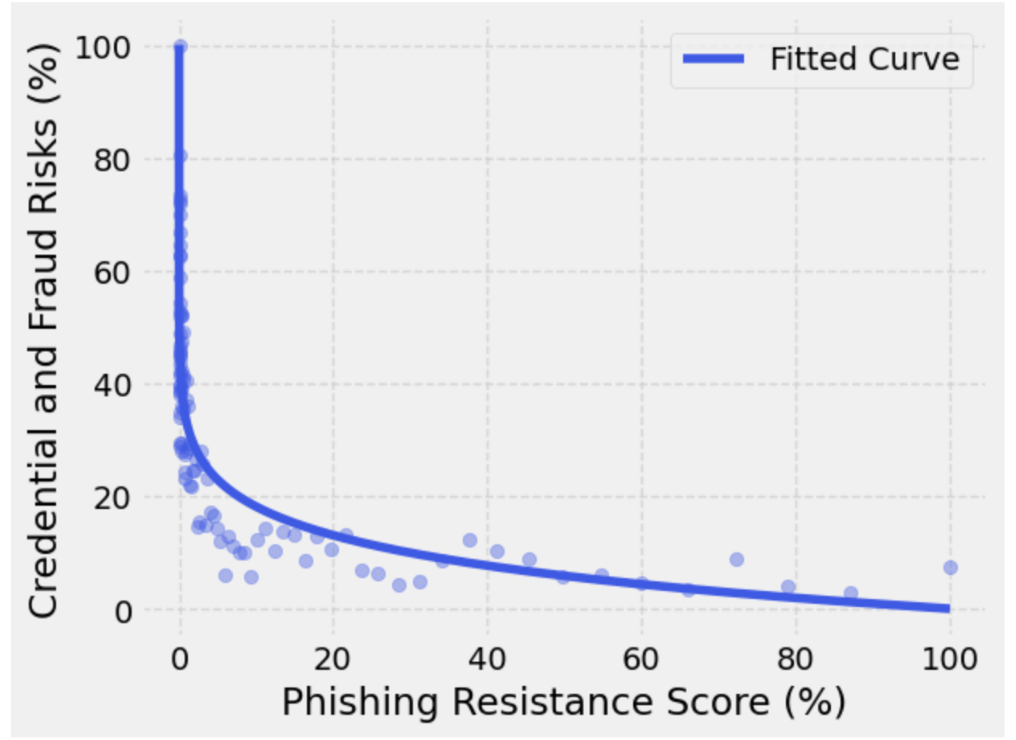
Figure 1
Figure 1 illustrates the relationship between the credentials and fraud risks and the use of phishing resistance. The credential and fraud risks decrease as phishing-resistant usage increases. In particular, credential and fraud risks diminish as phishing-resistant usage approaches 100. This is expected; however, what’s interesting is that there is an exponential decreasing trend in the figure. As phishing-resistant usage increases, there’s a notable exponential reduction in credential and fraud risks. When an organization hits 100% phishing resistance for all its use, the risk is significantly reduced, which is the desired state for an organization.
For the sake of completeness, we fit a modified bounded exponential decay function for credential and fraud risks as a function of phishing-resistance % (PR), which is formally defined using the following equation:
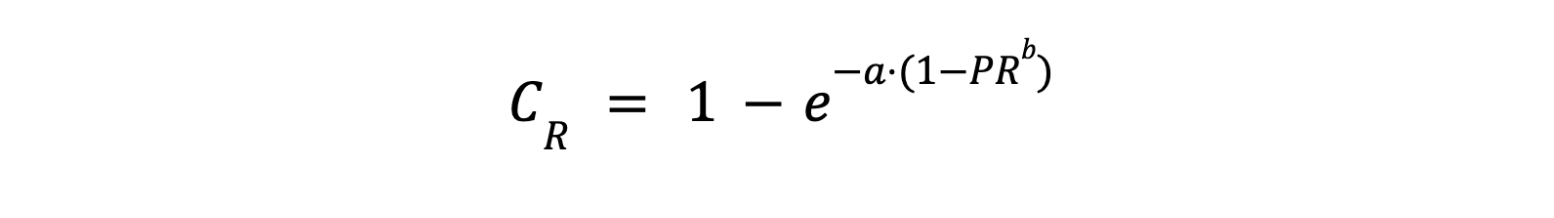
After applying the Levenberg-Marquardt algorithm for nonlinear least-squares curve fitting, the above equation can be written as:
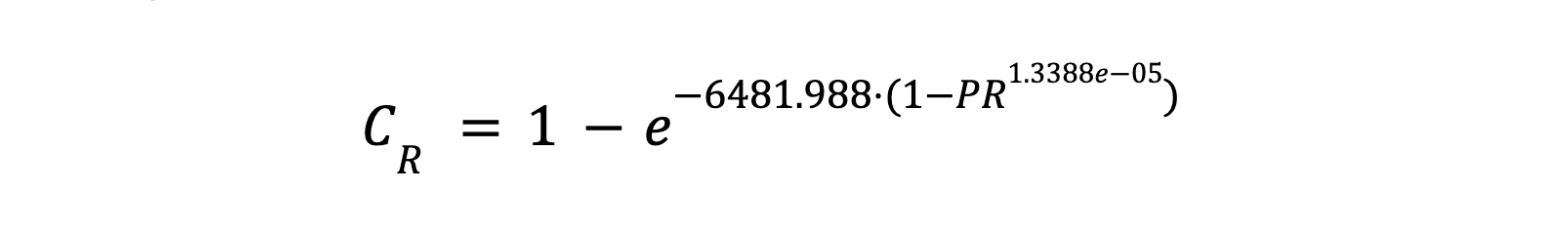
The fitted curve is also illustrated in Figure 1. An organization's lack of phishing-resistant authentication (% of phishing resistance = 0%) puts it at greater risk of credential access and fraud attacks. In this scenario, the credential and fraud risks metric is 100%. However, it’s worth highlighting that with the adoption of 20% phishing-resistant authentications, as determined by the % of phishing resistance metric, organizations can reduce the credential and fraud risks to ~15%, an improvement from 100%.
|
Organizations can significantly reduce their credential and fraud risks by adopting phishing-resistant authentications. |
Statistical hypothesis testing
We would like to validate the hypothesis that organizations with low phishing-resistant use have significantly higher credential and fraud risks than organizations with relatively higher phishing-resistant use. We created two groups based on phishing resistance usage to facilitate this statistical hypothesis testing. The samples with phishing-resistant usage <20% are assigned to Group A, while those with phishing-resistant usage >=20% are assigned to Group B.
We perform the t-test to determine the means of two independent sample scores. The independent samples t-test, also known as the two-sample t-test, is a statistical test used to compare the means of two independent groups to determine if there’s a statistically significant difference between them.
In our statistical hypothesis test
- The null hypothesis (H0) is that there is no significant evidence that Group A's credential and fraud risk values are higher than Group B's.
- The alternate hypothesis (Ha) is that Group A's credential and fraud risk values are significantly higher than Group B's.
- The significance level (alpha value) is set to 0.05.
To perform the t-test, we first need to evaluate what variants of the t-test should be used. Although t-tests are relatively robust to deviations from assumptions, it’s always a good practice that the common assumptions made in t-tests are valid. These assumptions include:
- Continuous data
- Normality or large sample size
- Independence and random sampling
- Homogeneity of variance (Homoscedasticity) for Student’s t-test and unequal variance for Welch's t-test
Our data meets the first three assumptions. However, we need to check for homogeneity of variance to confirm if we need to conduct Student’s t-test or Welch’s t-test. We can verify this via Levene's test.
Levene's test
Levene's statistical test checks whether the variances of two groups are equal. The null hypothesis is that the population variances of the two groups are equal. If the null hypothesis of equal variances is rejected, then there is a difference between the variances in the two groups.
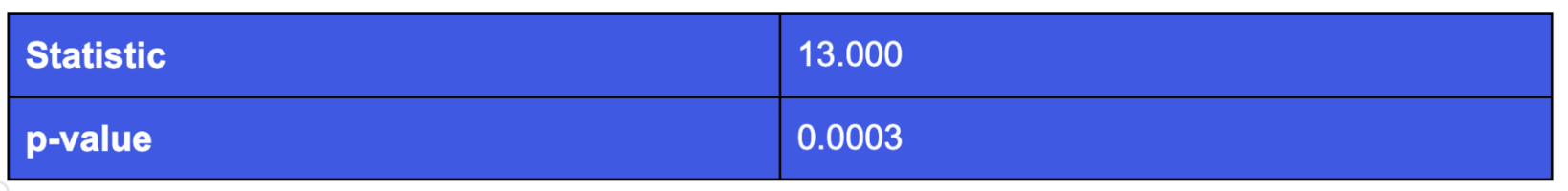
The test statistic for Levene's test is tabulated above for our two groups. Based on Levene's test statistic, we can reject the null hypothesis and confirm that the variances of the two groups are not equal. This implies we would have to perform Welch’s t-test rather than the standard Student’s t-test.
Welch's t-test
Welch's t-test, or unequal variances t-test, is robust to violations of homoscedasticity. The null hypothesis in this test is that two populations have equal means. It is also known as a modification of the independent samples t-test that does not assume equal variances.
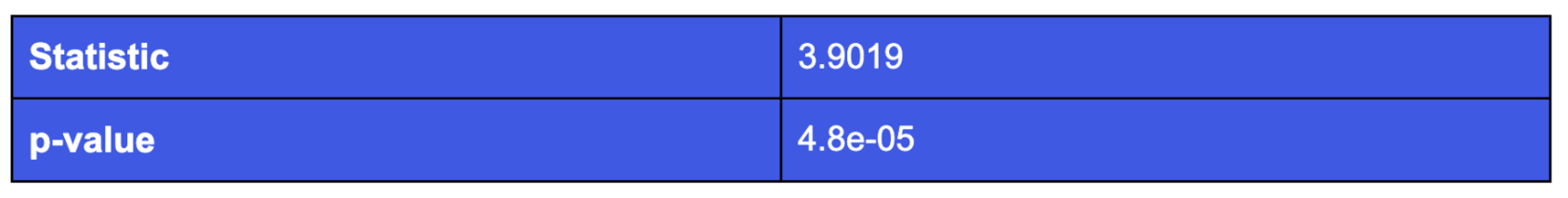
Now, we report the test statistic for the Welch's t-test for our two groups in the above table. Based on Welch's t-test statistic, we can reject the null hypothesis. This implies that Group A's credential and fraud risk values are significantly higher than Group B's credential and fraud risk values. In other words, we’ve validated our hypothesis that organizations with low phishing-resistant usage have significantly higher credential and fraud risks than organizations with relatively higher phishing-resistant usage.
Key takeaways
- The percentage of phishing resistance (PR) is the metric we’re introducing to evaluate the use of phishing resistance authenticators in an organization. Organizations should monitor and improve this metric to improve their security posture.
- Credential and fraud risks drop sharply when you use phishing-resistant authenticators. Start your phishing-resistance journey today to precipitously reduce the risk. Okta recommends using phishing-resistant factors such as FastPass, WebAuthn, and Smart Cards (federal) for all flows.
- Statistically, organizations with low phishing resistance face significant credential and fraud risks compared to those with higher phishing resistance.
- Achieving 100% phishing resistance is necessary to mitigate credential and fraud risks for the attack vectors discussed, indicating 100% utilization of phishing-resistant authentications.
- Protection measures against phishing attacks can effectively eliminate attack vectors associated with credential access and toll fraud, even though these are seemingly unrelated. Phishing-resistant authenticators are emerging as a potent deterrent against non-phishing attacks.
Have questions about this blog post? Reach out to us at [email protected].
Explore more insightful Engineering Blogs from Okta to expand your knowledge.
Ready to join our passionate team of exceptional engineers? Visit our career page.
Unlock the potential of modern and sophisticated identity management for your organization. Contact Sales for more information.

