One of my favorite moments on the Okta Design team sparked when my manager and I sketched a version of the following graphic for the first time.
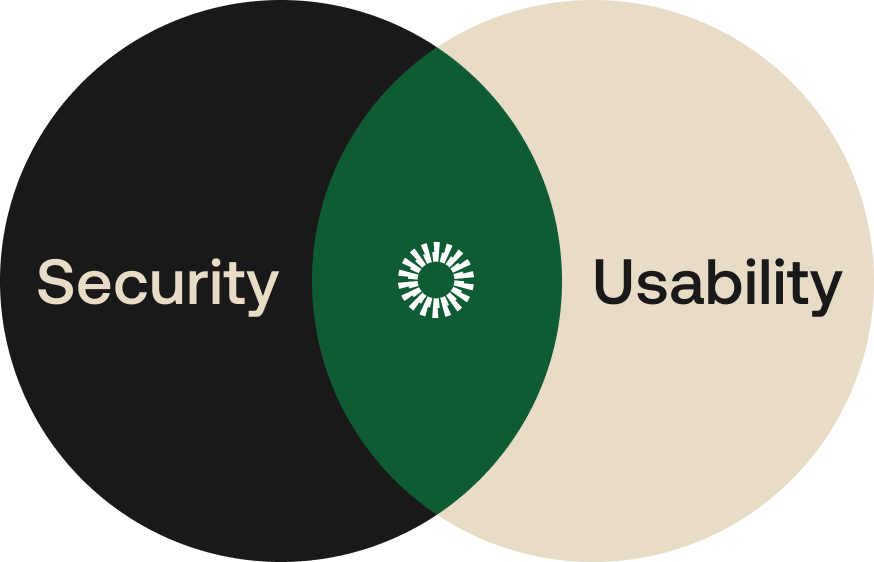
The most humbling moment came when one of our colleagues asked why we needed more than one circle. Why isn’t it all about security?
Security is more than a matter of on or off—otherwise companies like Okta wouldn’t exist. And the moment we introduce a person other than the designer to any interface, usability becomes a discussion of tradeoffs.
If neither security nor usability are binary, then why is their relationship often simplified to a linear spectrum?
A Venn diagram accommodates more realities faced by security admins and end users, as both personas shape policies and behavior.
But one of the most useful parts of any concept is finding who disagrees (and understanding why).
Driving in circles
We sketched the Venn diagram above to have more productive design critiques. The graphic became an opportunity to revisit broader assumptions with product and engineering.
So, why isn’t it all about security?
In my time designing three new products as part of Okta Device Access, I’ve often described security as a door. Okta’s extensive suite of products puts locked doors—and walls—around things our customers care about. We identify who should have keys and ensure doors open under the right conditions. Multi-Factor Authentication (MFA) is how many locks the door has. Single-Sign On (SSO) means opening one door automatically opens others.
Now, consider perfect security. It would be impenetrable. What would be more impenetrable than a door that never opens? Oops. If there was only a security circle, we wouldn’t have locked doors, we would only have walls.
Perfect usability would also be invisible. Instead of a locked door, we would only have an empty door frame.
So, let’s revisit that overlap.
Okta thrives in the overlap
After the downsides of perfect security and perfect usability, we arrive at how they intersect.
Identity becomes a useful lens here.
In the perfect usability example, there’s no room for identity since anyone can pass through. This moves us away from usability towards verifying identity, a traditional security concern.
How do we ask people to prove who they are? We could request something they know, like a password, something they have, like a phone with a special app, or something they are, like a fingerprint. Each of those are security characteristics but also come with usability implications. Memory is fallible. Devices malfunction and disappear. Fingers have accidents and legal constraints about who can ask for and store biometrics.
What began as a basic concept—open this door for the right person under the right conditions—becomes a nuanced discussion. What conditions? What constitutes “right person?” With software automation and artificially intelligent agents, should we restrict ourselves to people? And is this the right door to contain all these questions? When was the last time this (non-)person opened the door? How many doors have been opened? Under what conditions? Can we afford to ask any one person all these questions for the sake of better security?
“How do we make the most secure thing the easiest thing?”
— Okta’s SVP of Design and Research
Answering these questions makes Okta and our customers thrive. It's worth labeling the overlap in the security and usability Venn diagram. “Usable security” combines usability that keeps end users productive with security that lets administrators worry less.
If you enjoy questions like these or revel in the curiosity brought forth by a good diagram, consider joining us at Okta Design. We’re hiring.






