Executive Summary
Okta Threat Intelligence has uncovered a novel, sophisticated, and actively deployed Phishing-as-a-Service (PhaaS) platform targeting Microsoft 365 and Google Workspace accounts, which we are tracking as VoidProxy or O-TA-083.
Activity from the VoidProxy PhaaS has been observed since at least January 2025 and new domains and account takeover attempts are being observed daily. The platform is being used to target organizations in multiple industry sectors.
VoidProxy leverages Adversary-in-the-Middle (AitM) techniques to intercept authentication flows in real-time, to capture credentials and multi-factor authentication (MFA) codes, and to steal session cookies, thereby bypassing MFA protections.
This capability renders common MFA methods, such as SMS codes and one-time passwords (OTP) from authenticator apps ineffective. However, Okta offers a choice of authenticators for phishing resistance, including Okta FastPass, which prevented all account takeover attempts from VoidProxy in the attacks we have observed.
The primary objective of VoidProxy is the compromise of corporate accounts to facilitate subsequent malicious activities, such as Business Email Compromise (BEC), financial fraud, data exfiltration and lateral movement within victim networks.
Given its PhaaS model, VoidProxy lowers the technical barrier for a wide range of threat actors to execute AitM phishing attacks, significantly amplifying its potential impact. The platform represents a mature, scalable and evasive threat that challenges conventional email security and authentication controls.
The information in this advisory is provided to enable organizations to understand and mitigate the risks posed by this threat.
VoidProxy - Key Takeaways
Threat Analysis
Anatomy of an attack: The VoidProxy kill chain
The VoidProxy attack methodology follows a multi-stage kill chain designed to systematically bypass security controls and deceive end-users. Each stage is carefully orchestrated, leveraging a distributed infrastructure to achieve its objective of account takeover.
Stage 1: Delivery
The initial vector for a VoidProxy attack is a phishing email targeting users of major cloud services like Microsoft 365 and Google Workspace.
To bypass standard security controls, the operators use legitimate, high-reputation Email Service Providers (ESPs). We observed the use of Constant Contact, Active Campaign (Postmarkapp), NotifyVisitors and others to send their malicious lures. This is a deliberate choice, as emails originating from the trusted IP ranges of such services are less likely to be flagged as spam or malicious by email gateways.
Embedded within these emails is a link that often uses legitimate URL shortener services like TinyURL to conceal the real address of the phishing page. This serves to mask the true destination from both the user and automated scanners, increasing the likelihood that the user will click the link and reach the final destination.
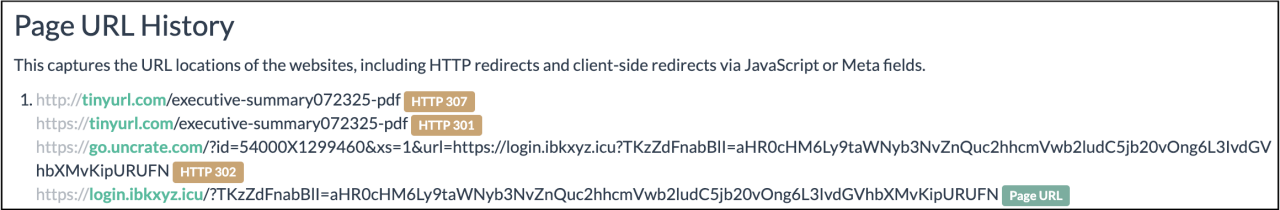 Redirects from TinyURL to phishing pages
Redirects from TinyURL to phishing pages
In one campaign, a threat actor impersonated Okta's HR function to lure the recipient into clicking a malicious link for a digital payslip.
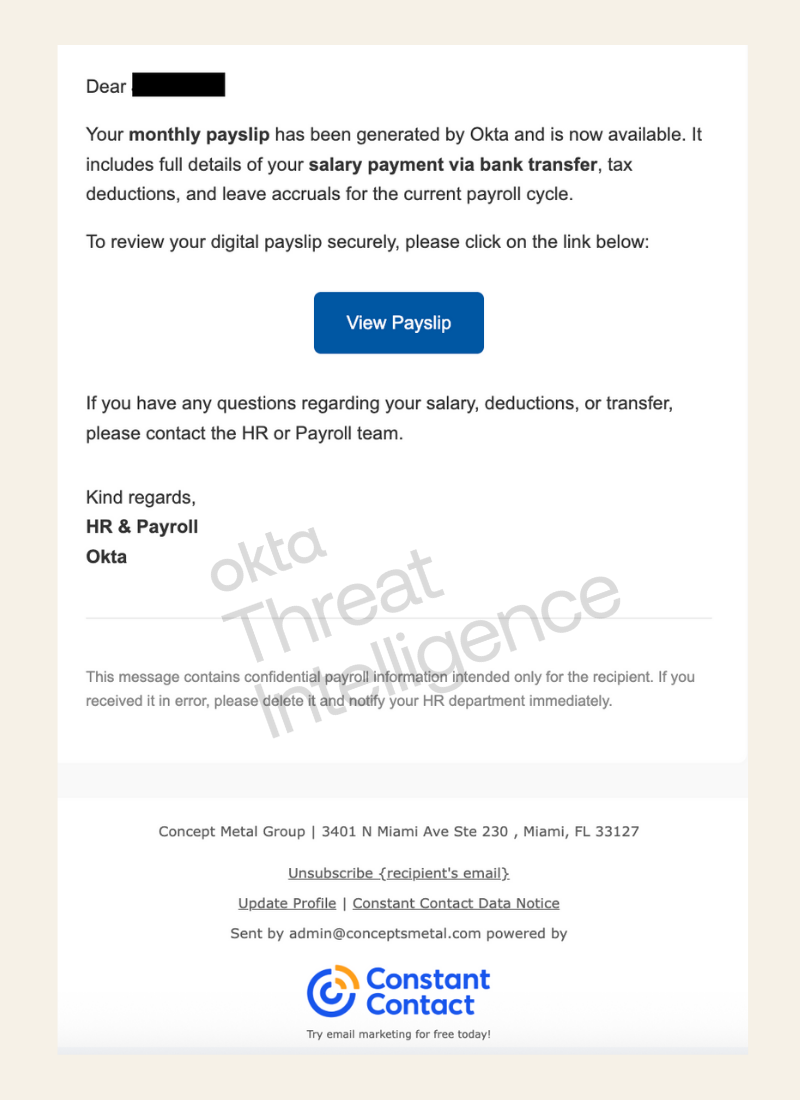 Figure 2: An intercepted phishing message abusing Constant Contact
Figure 2: An intercepted phishing message abusing Constant Contact
Upon furthers analysis of VoidProxy activity, we discovered a fraudulent DocuSign document, hosted on the Zoom Docs platform, which was also leveraged to mislead victims.
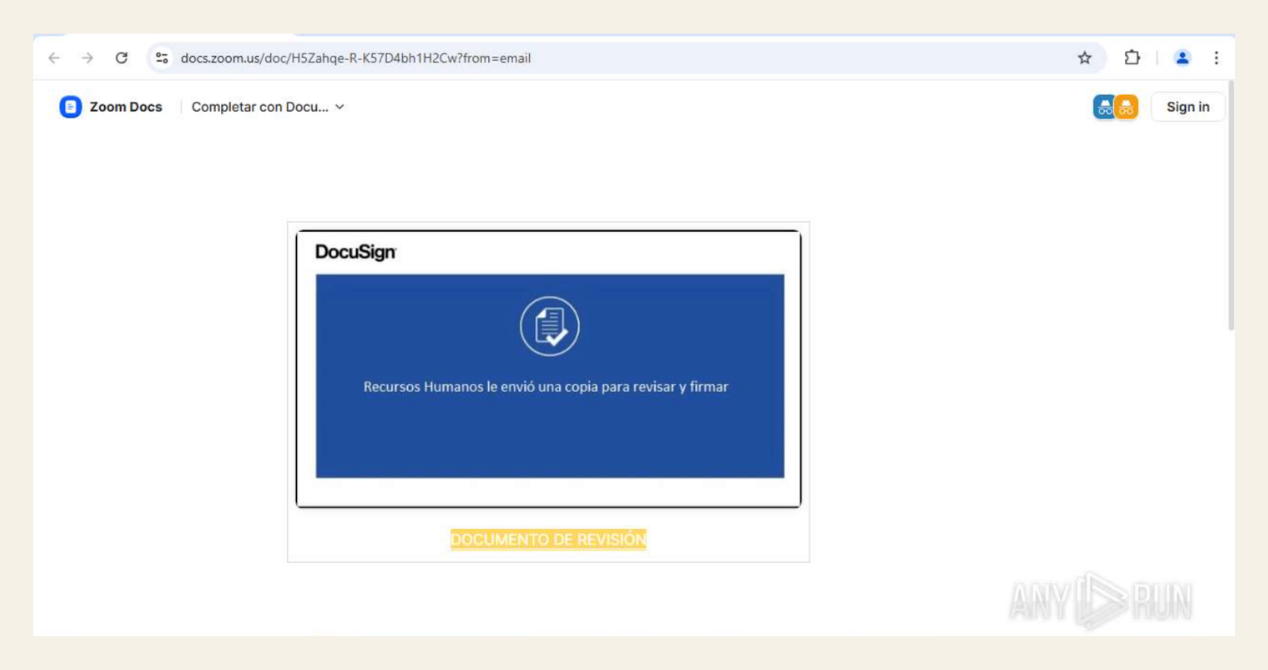 Figure 3: The DocuSign lure delivered via Zoom Docs, identified using AnyRun
Figure 3: The DocuSign lure delivered via Zoom Docs, identified using AnyRun
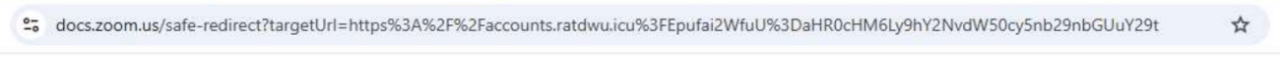 Figure 4: An AnyRun scan shows the redirect from a Zoom Doc link to the phishing domain
Figure 4: An AnyRun scan shows the redirect from a Zoom Doc link to the phishing domain
Step 2: Evasion and lure loading via Cloudflare Workers
Upon clicking the malicious link, a targeted user is not taken directly to a login form. Instead, the phishing site presents a Cloudflare CAPTCHA challenge. This is designed to filter out automated security scanners and bots, ensuring that only human users proceed.
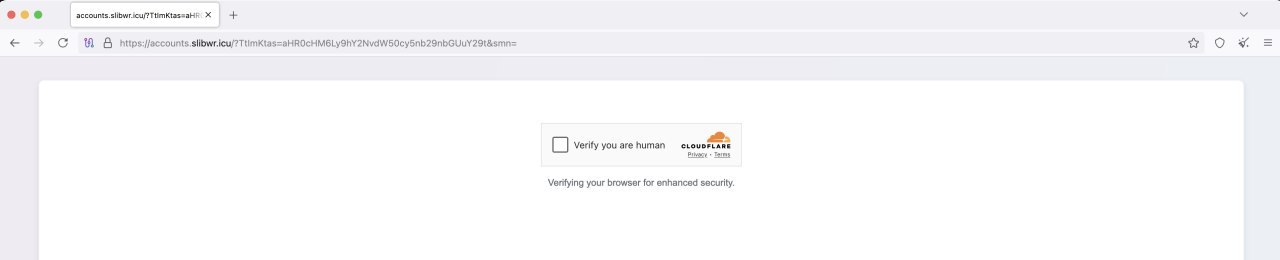 Figure 5. A Cloudflare CAPTCHA presented to a targeted user on the phishing domain
Figure 5. A Cloudflare CAPTCHA presented to a targeted user on the phishing domain
The user's browser then communicates with a Cloudflare Worker (*.workers.dev). We assess that this worker is likely to act as a gatekeeper and lure loader. Its primary functions are to filter incoming traffic and to load the appropriate phishing page for any given target. This architecture separates initial filtering from the core phishing operations of the campaign. Once a challenge is passed, the user is presented with the final phishing page, which is a perfect replica of a legitimate login portal.
The phishing domains use the following patterns:
- For Microsoft 365 targets: login. <phishing_domain>.<tld>
- For Google Workspace targets: accounts. <phishing_domain>.<tld>
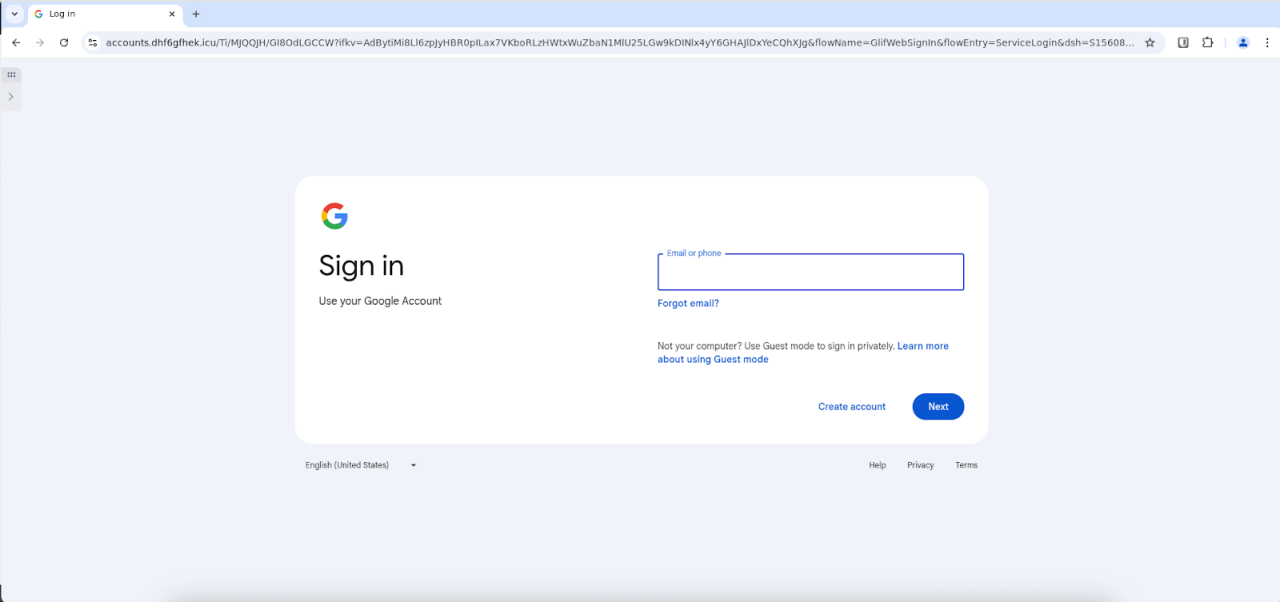 Figure 6: A VoidProxy phishing page targeting Google accounts
Figure 6: A VoidProxy phishing page targeting Google accounts
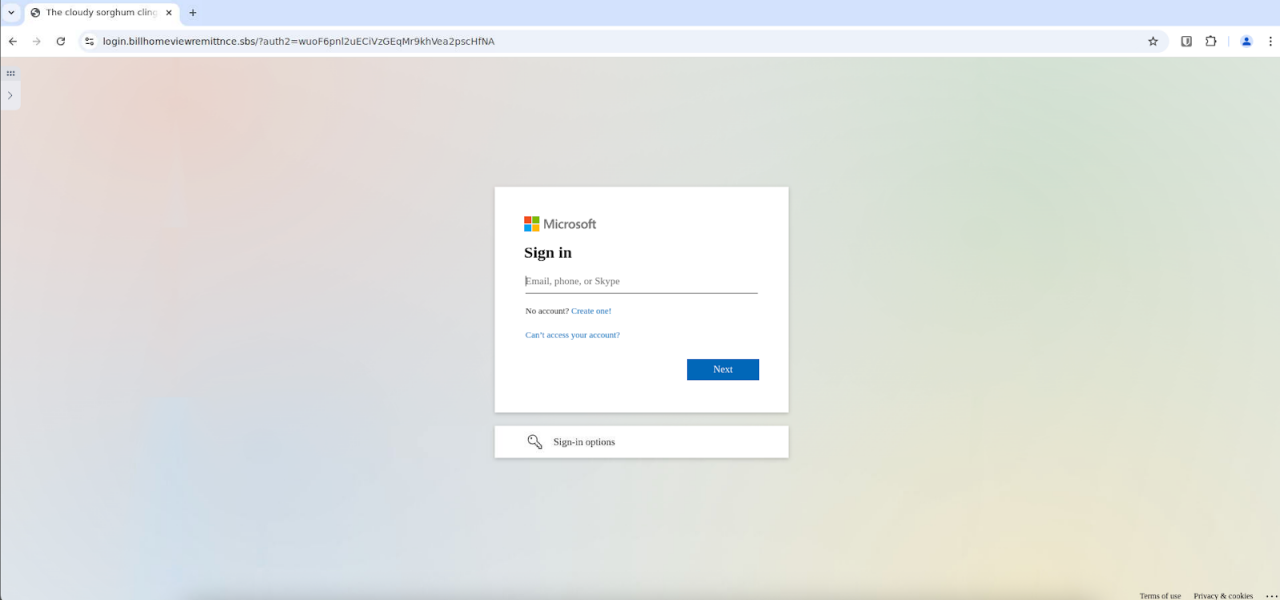 Figure 7: A VoidProxy phishing page targeting Microsoft accounts
Figure 7: A VoidProxy phishing page targeting Microsoft accounts
If the phishing page detects the visitor is a scanner or security tool rather than an intended target, it returns a blank page that displays the text "Welcome!".
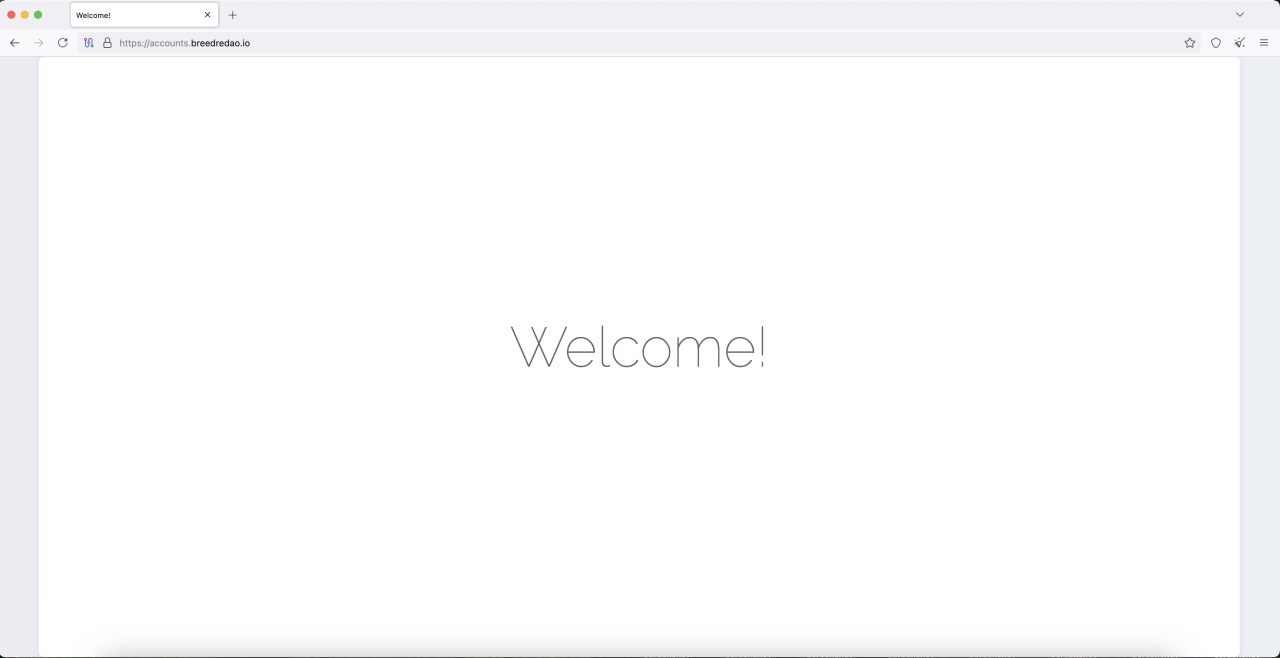 Figure 8. A phishing pages displays a “Welcome!” page for unwelcome visitors
Figure 8. A phishing pages displays a “Welcome!” page for unwelcome visitors
Stage 3: Credential interception for SSO-protected accounts
This stage reveals the sophisticated, multi-layered nature of VoidProxy, particularly its ability to compromise high-value targets that use identity providers like Okta.
After the victim enters their primary Microsoft or Google credentials on the phishing page, the data is redirected to the core AiTM proxy server (hosted on sslip.io/nip.io infrastructure).
If the proxy detects that the account is federated through Okta, the user is seamlessly redirected to a second phishing page, which mimics the organization's specific Okta sign-in page.
This second-stage phishing page uses a different set of subdomain patterns:
- Okta (via a Microsoft lure): newnewdom<random>.<phishing_domain>. <tld>
- Okta (via a Google lure): securedauthxx<random>.<phishing_domain>. <tld>
securedauthxxccbgchgfj.xhfwez[.]icu
securedauthxxdcigbjdddj.losozr[.]icu
securedauthxxeafihgjdhb.dcohcv[.]icu
newnewdomnewcgbdhghjhi.prophfrot[.]top
newnewdomnewebjjfjegfd.eeocl[.]com
newnewdomnewdihbddahf.access-point[.]icu
Figure 9. Example subdomain patterns generated for SSO-protected users
Stage 4: AitM relay and session hijacking
In the final stage of the phishing attack, a core proxy server hosted on sslip.io or nip.io infrastructure executes an Adversary-in-the-Middle (AitM) attack.
The server acts as a reverse proxy to capture and relay information including usernames, passwords, and MFA responses - to legitimate services like Microsoft, Google, and Okta. This process results in the threat actor taking over the account.
VoidProxy Infrastructure
VoidProxy employs a multilayered approach composed of distinct stages, each with its own specific characteristics.
The operational infrastructure of VoidProxy is a combination of disposable, high-turnover frontends and a more persistent, resilient backend hosted on serverless architecture.
Domain and subdomain patterns
VoidProxy's operators adhere to a consistent set of patterns for infrastructure deployment:
- Phishing domains: The primary landing pages are hosted on domains registered with a variety of low-cost, low-reputation TLDs, such as .icu, .sbs, .cfd, .xyz, top, and .home. This strategy minimizes operational costs and allows the attackers to treat the domains as disposable assets, quickly abandoning them once they are identified and blocklisted. The phishing sites are placed behind Cloudflare, effectively hiding the real IP address of the phishing site's server and making it harder for security teams to trace and take down the malicious host.
- Subdomain prefixes: Analysis of multiple VoidProxy URLs reveals the recurring use of specific subdomain prefixes, notably: accounts, login, portal, securedauthxx and newnewdom. We assess that it is likely these prefixes are generated automatically by the kit's deployment script in order to target patterns used by specific identity providers.
Security filtering using Cloudflare Workers
As described above, the PhaaS platform uses a distributed architecture. Cloudflare Workers (*.workers.dev) acts as an initial gatekeeper, serving the phishing content and performing preliminary checks, such as presenting a Cloudflare CAPTCHA challenge.
An interesting insight into the operational model of the VoidProxy PhaaS comes from the naming convention of its Cloudflare Worker endpoints. After analyzing multiple cases, a consistent pattern emerged: all the Cloudflare Worker endpoints were crafted using the same naming construct. The threat actor has been using plausible-sounding English names like aidenveliz, kelvingomez, and sammybruce in the subdomain:
<alphanumeric>.<firstnamelastname>.workers.dev.
This pattern strongly suggests an automated or semi-automated provisioning system for the PhaaS customers (threat actors who rent the kit). Manually creating and managing unique Cloudflare accounts for each threat actor who bought the kit would be inefficient and difficult to scale. Instead, it is likely that the VoidProxy operators use a master account or API key to programmatically generate this infrastructure. The randomly-generated <firstnamelastname> component likely serves as a unique namespace for a specific customer or a large-scale campaign. The <alphanumeric> prefix then acts as a unique identifier for a specific phishing page instance deployed by that threat actor. This architecture provides a layer of isolation between buyers of the kit and makes it more challenging for researchers to link all VoidProxy activity to a single controlling entity.
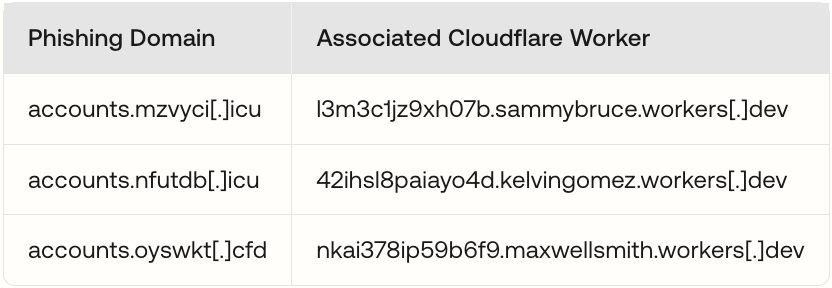 Figure 10: Examples of abuse of Cloudflare Workers
Figure 10: Examples of abuse of Cloudflare Workers
Core proxy and C2 infrastructure
The core of VoidProxy's operation - both the AiTM reverse proxy and the attacker's administrative panel - are hosted on servers accessed via dynamic DNS wildcard services sslip.io and nip.io. These services are designed to resolve hostnames with embedded IP addresses directly to those IPs, a feature intended for development that has now been weaponized for malicious purposes.
This infrastructure serves as:
- AitM proxy engine: This is the server that performs the actual adversary-in-the-middle attack, relaying traffic between the victim and the legitimate service to steal session cookies.
- Attacker admin panel: These URLs also host the web panel that PhaaS customers use to configure campaigns, monitor victims in real-time and access stolen data.
The use of the "voidproxy" prefix is a self-identifying marker for this C2 infrastructure. This architecture, which separates the initial lure loading on the phishing URL domains from the core logic (*.sslip.io), demonstrates a sophisticated, multi-layered approach designed for operational efficiency and resilience.
Infrastructure used in account takeover activity
Okta Threat Intelligence observed several account takeover attempts following successful VoidProxy phishing campaigns.
Account takeover attempts were successful against users relying on non-phishing-resistant MFA methods (such as OTPs and push requests). The AitM capabilities of VoidProxy allow the attackers to intercept and relay these one-time codes and push notifications in real-time, effectively bypassing the MFA challenge.
By contrast, Okta FastPass successfully prevented all account takeover attempts. FastPass binds the authentication to the legitimate domain and device, making it impossible for AitM proxies to intercept and replay valid session information.
This demonstrates the critical importance of deploying phishing-resistant MFA to effectively mitigate threats from sophisticated PhaaS platforms like VoidProxy.
Following a successful compromise of user credentials, the threat actor(s) were observed attempting to authenticate from IPs that were predominantly hosted on the following ASNs:
- AS36352 - HostPapa
- AS149440 - Evoxt Enterprise
- AS210558 - 1337 Services GmbH
- AS401120 - cheapy.host LLC
- AS23470 - ReliableSite.Net LLC
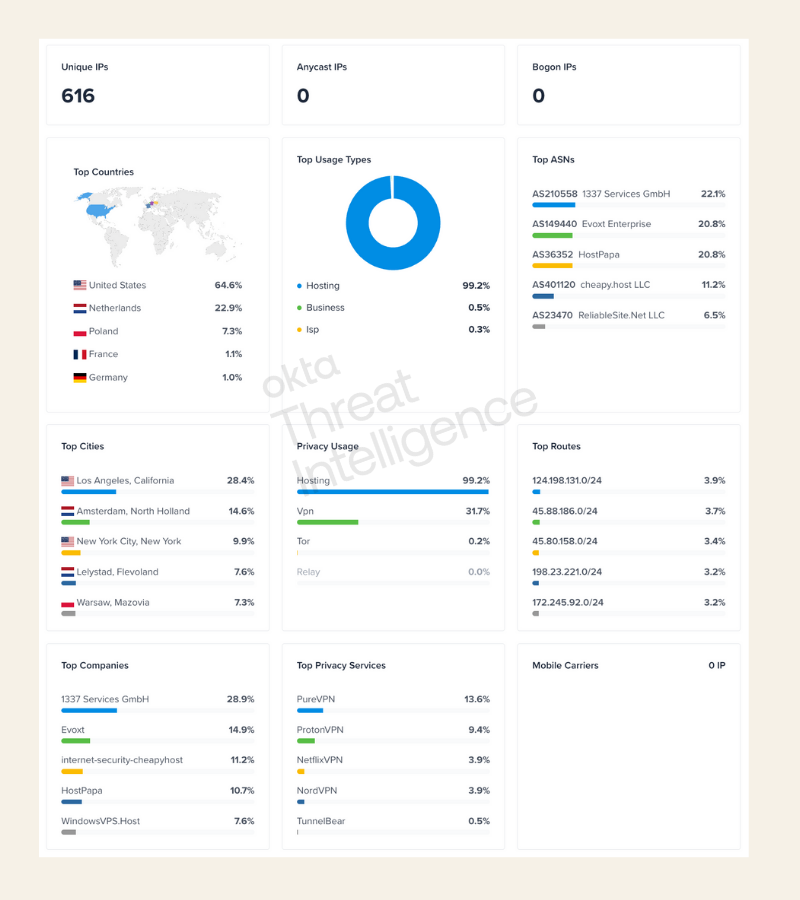 Figure 11: Dashboard of hosting providers behind VoidProxy infrastructure
Figure 11: Dashboard of hosting providers behind VoidProxy infrastructure
The VoidProxy admin panel
Analysis of the phishing kit reveals a full-featured administrative panel that allows PhaaS customers to manage and monitor their campaigns. This panel provides a comprehensive interface for orchestrating attacks and collecting stolen data.
 Figure 12: VoidProxy admin login page
Figure 12: VoidProxy admin login page
Conducting further analysis on the admin panel webpage, we observed the
different capabilities and services the PhaaS offers.
Dashboard page (/dashboard)
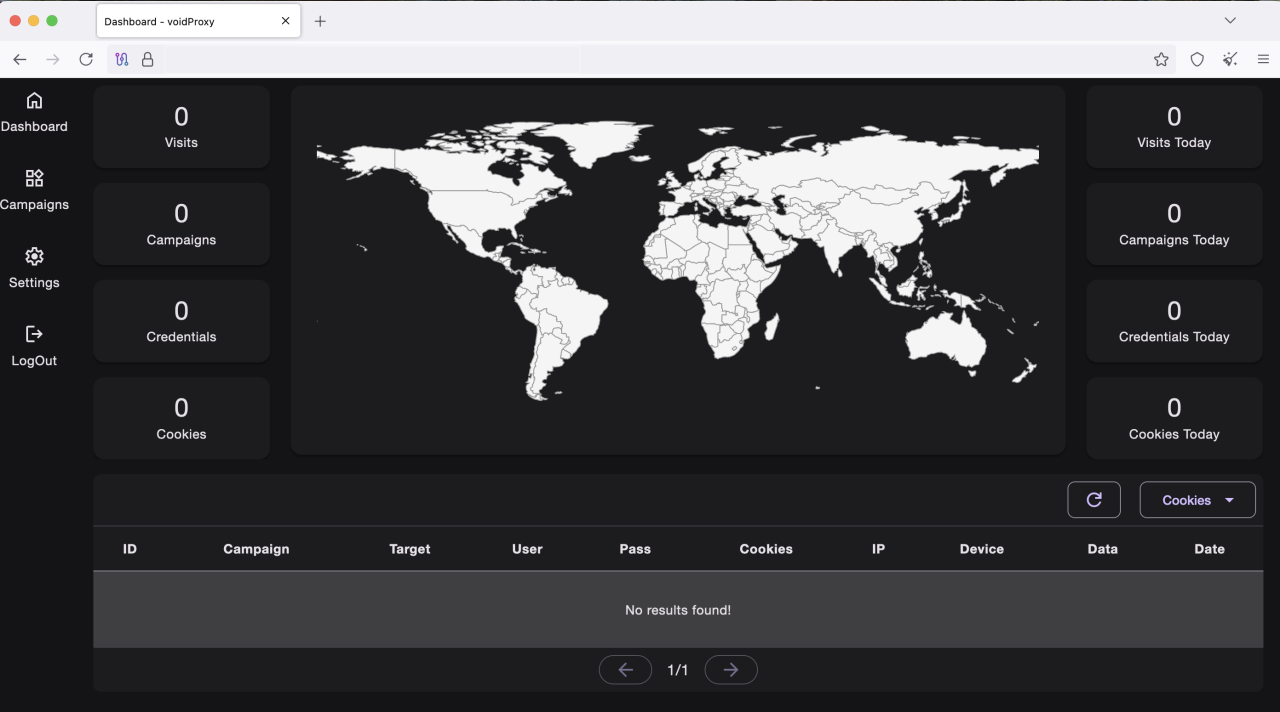 Figure 13: VoidProxy admin panel dashboard
Figure 13: VoidProxy admin panel dashboard
This page serves as the central hub for the operator, providing a high-level overview of campaign performance and recent activity. Key metrics displayed include:
- Campaign overview
- Total clicks and total submissions
- Stolen credentials
- Recent activity and live feed
- Victim locations
Campaigns page (/dashboard/campaigns)
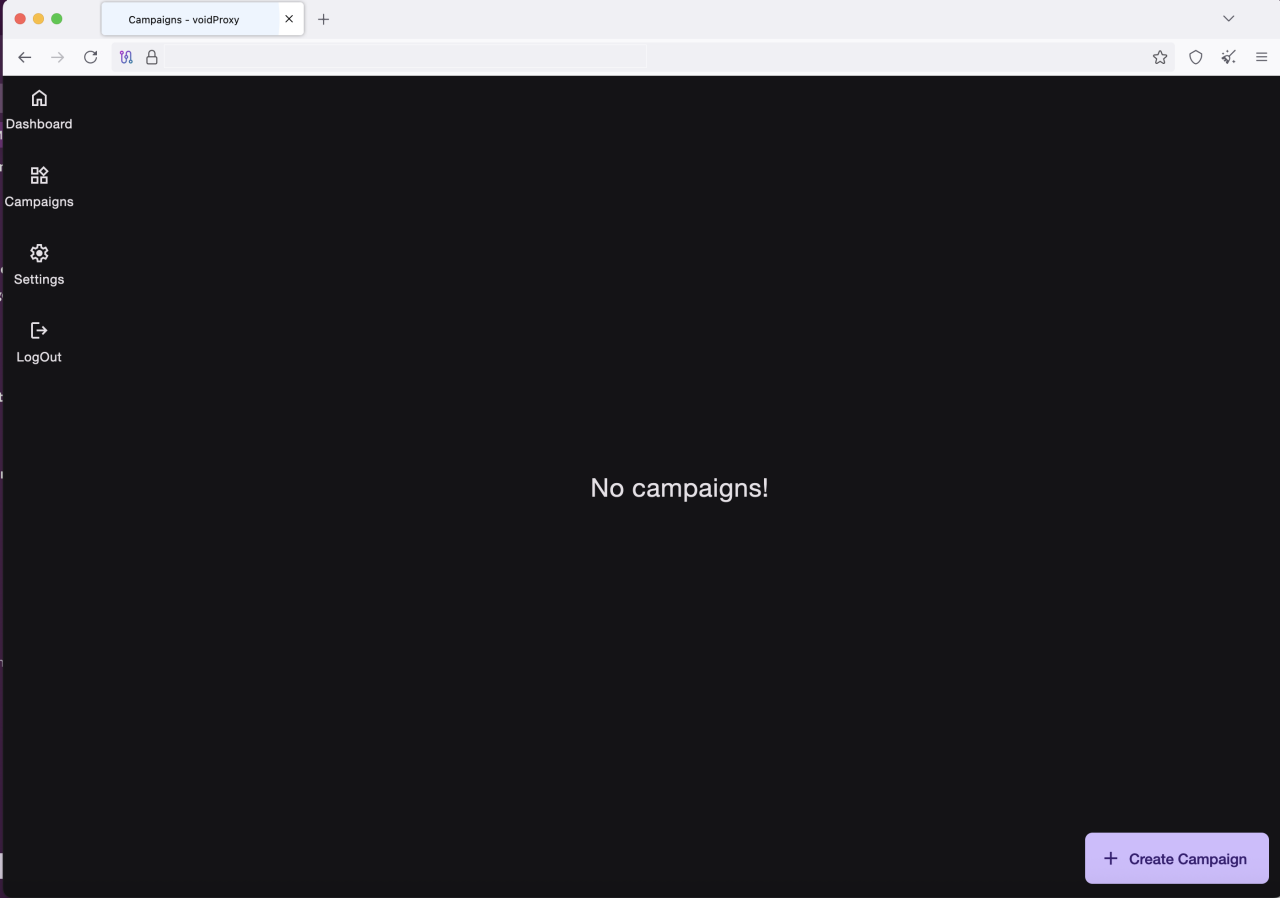 Figure 14: VoidProxy admin panel campaigns page
Figure 14: VoidProxy admin panel campaigns page
This section of the admin panel is dedicated to creating and managing phishing campaigns. It features a data table with functionality to control each campaign.
- Management: operators can create a "New Campaign" or manage existing ones.
- Details: columns display "Campaign Name," "Target Service" (e.g., Microsoft 365, Google), "Status" (Active, Paused), and "Creation Date."
- Metrics: key statistics like "Total Clicks" and "Total Submissions" are shown for each campaign.
- Actions: operators can "Start," "Stop," "Pause," or "Delete" campaigns.
Individual campaign page (/dashboard/campaigns/[campaign_id])
This page offers a detailed, granular view of a single campaign, allowing the operator to inspect captured data and logs.
- Victim log: provides detailed logs of victim interactions.
- Captured data: displays all stolen data, including "Stolen Credentials," "Session Cookies," "IP Addresses," and "User Agents."
- Actions: includes an option to "Download Log" for offline analysis.
Settings page (/dashboard/settings)
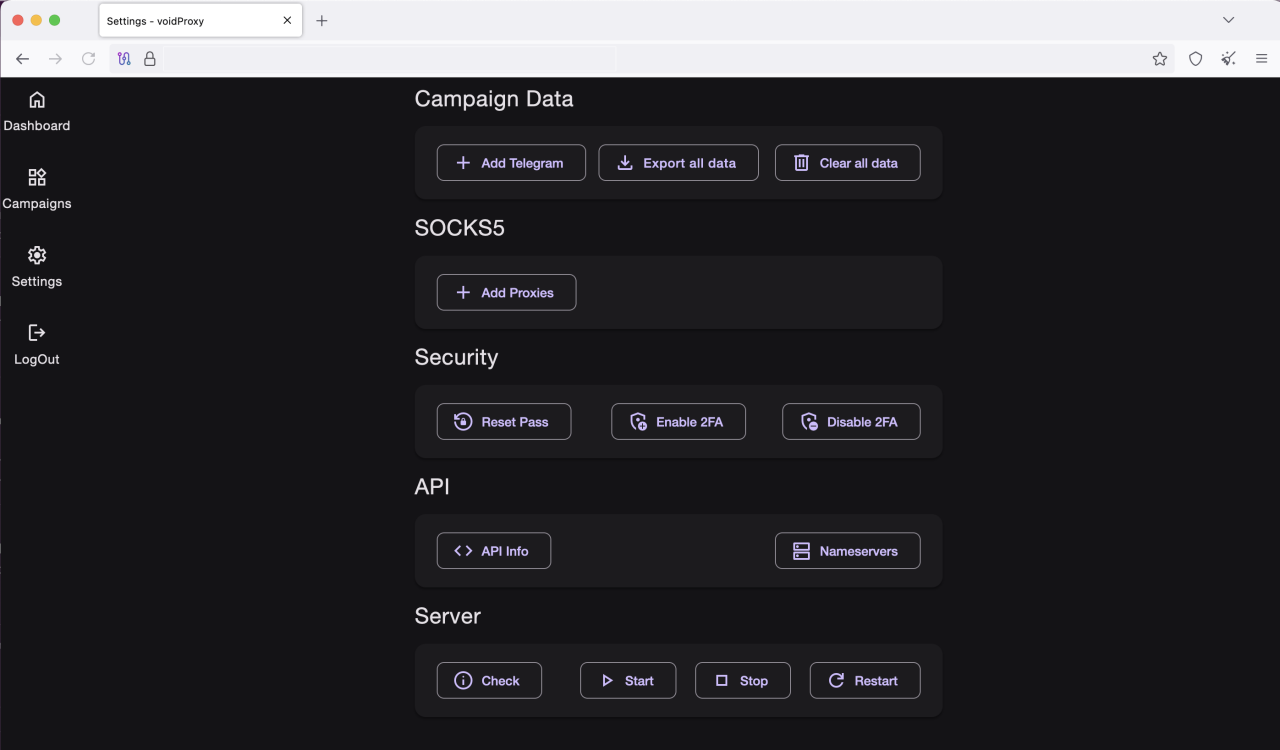 Figure 15: VoidProxy admin panel campaigns settings page
Figure 15: VoidProxy admin panel campaigns settings page
This page allows the operator to configure the platform and integrate it with other services for data exfiltration and notifications.
- Account management: includes options to "Change Password" and manage "API Keys."
- Integrations: operators can configure a "Telegram Bot Token" or a generic "Webhook URL" to receive real-time notifications and exfiltrate stolen data automatically.
Linking VoidProxy to underground identities
After analyzing the campaign, Okta Threat Intelligence researched the underground ecosystem for activity that could link this novel PhaaS platform to a specific threat actor.
The research uncovered a Telegram message dated August 2024 posted on the "BIGFATCHAT™" channel - a channel known for harboring scammers where a user under the moniker VOID was offering a service to "bypass all 2FA".
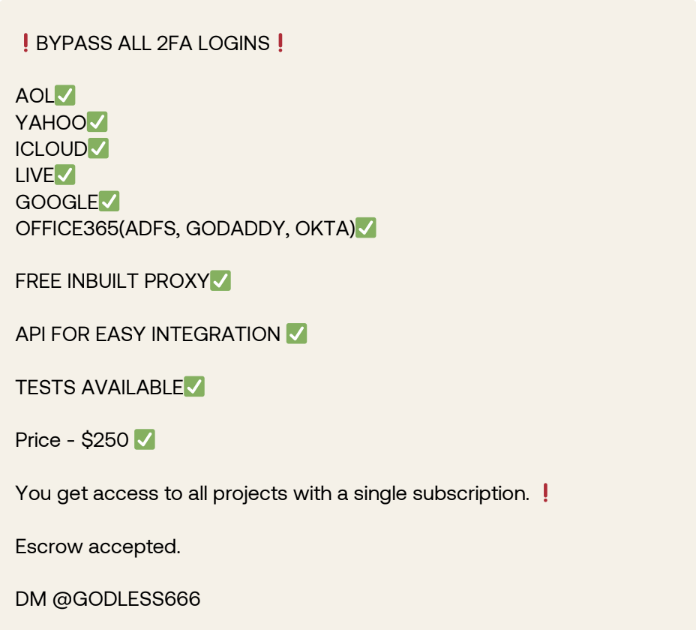 Figure 16: This Telegram channel was inactive at the time of publishing.
Figure 16: This Telegram channel was inactive at the time of publishing.
The service, priced at $250 at the time, promises to bypass 2FA logins from AOL, Yahoo, iCloud, Live, Google and Office 365 (ADFS, GODADDY, OΚΤΑ). Attached to the message was a screenshot showing a service named "voidproxy" running on what appeared to be an AWS server. The screenshot revealed that several components of the service were active, including a "MITMSERVER" (Man-in-the-Middle Server), which was already configured to bypass authentication flows for platforms like Google and Office 365.
Notably, the infrastructure appeared designed to intercept session cookies, which were being exfiltrated via Telegram bots mentioned in the interface. The presence of an AitM server, along with these indicators, strongly suggests that this setup was a fully operational Phaas environment primed for harvesting credentials and hijacking user sessions.
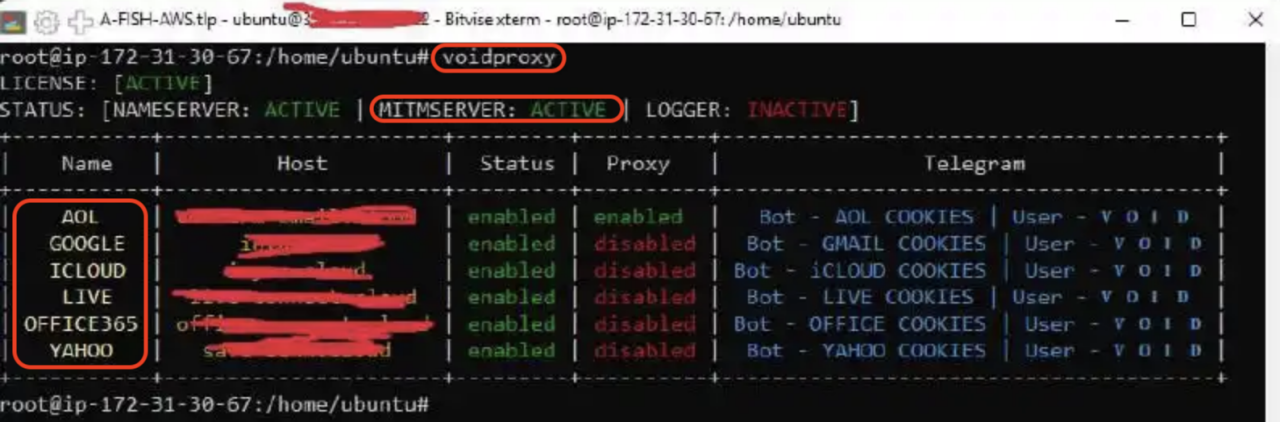 Figure 17: VoidProxy screenshot attached to dark web advertisement
Figure 17: VoidProxy screenshot attached to dark web advertisement
The user behind the service has been active in the cybercrime underground since at least 2022, initially engaging across multiple English-speaking Telegram channels, many of which are associated with scam-related activity.
Operating under aliases VOID and GODLESS666, the individual demonstrated early interest in BEC schemes and sought partners to carry out what they referred to as "SMS phishing" (aka smishing).
In 2023, VOID began to show interest in identity service providers, specifically seeking credentials for Okta and Duo Security. Okta Threat Intelligence team found additional monikers used by VOID, which includes "godlessvoid666", an active user on the well-known English-speaking forum "Breached".
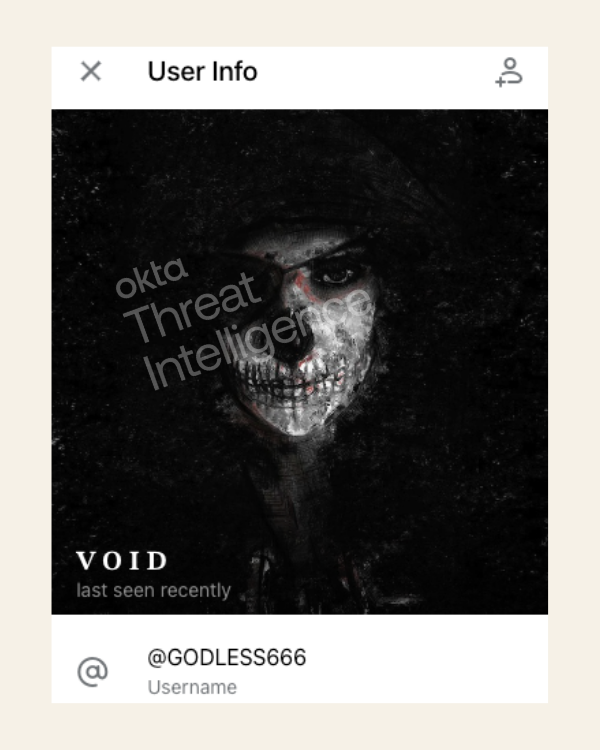 Figure 18: VOID User Profile
Figure 18: VOID User Profile
At the time of this writing, no definitive link has been established to confirm that this user is directly affiliated with VoidProxy Phaas discussed in this threat advisory report. However, based on the contextual indicators and modus operandi outlined above, such an affiliation can be assessed with a moderate level of confidence.
Threat Response
What we're doing:
We're actively engaged in the following activities to mitigate this threat:
- Continuously monitoring for newly registered phishing domains and infrastructure associated with this campaign.
- Proactively filing abuse reports with relevant registrars and hosting providers to initiate takedown requests for identified malicious sites.
- Feeding a continuous stream of relevant threat indicators into Okta Identity Threat Protection with Okta Al.
- Providing guidance and assistance to organizations to enhance the security of their Okta environments and investigate any suspicious activity related to potentially compromised accounts.
Protective Controls
Recommendations for customers
- Enroll users in strong authenticators such as Okta FastPass, FIDO2 WebAuthn and smart cards and enforce phishing resistance in policy. If any exceptions are made for Okta Verify Push notifications, we recommend enforcing number challenges for all sign-in attempts or for high-risk sign-in attempts.
- Okta authentication policies can also be used to restrict access to user accounts based on a range of customer-configurable prerequisites. We recommend administrators restrict access to sensitive applications to devices that are managed by Endpoint Management tools and protected by endpoint security tools. For access to less sensitive applications, require registered devices (using Okta FastPass) that exhibit indicators of basic hygiene.
- Deny or require higher assurance for requests from rarely-used networks. With Okta Network Zones, access can be controlled by location, ASN (Autonomous System Number), IP, and IP-Type (which can identify known anonymizing proxies).
- Okta Behavior and Risk evaluations can be used to identify requests for access to applications that deviate from previously established patterns of user activity. Policies can be configured to step-up or deny requests using this context.
- Train users to identify indicators of suspicious emails, phishing sites and common social engineering techniques used by attackers. Make it easy for users to report potential issues by configuring End User Notifications and Suspicious Activity Reporting.
- Document, evangelize and adhere to a standardized process for validating the identity of remote users that contact IT support personnel, and vice versa.
- Take a "Zero Standing Privileges" approach to administrative access. Assign administrators Custom Admin Roles with the least permissions required for daily tasks, and require dual authorization for JIT (just-in-time) access to more privileged roles.
- Apply IP Session Binding to all administrative apps to prevent the replay of stolen administrative sessions.
- Enable Protected Actions to force re-authentication whenever an administrative user attempts to perform sensitive actions.
Observing and responding to phishing infrastructure:
- Review application logs (Okta logs, web proxies, email systems, DNS servers, firewalls) for any evidence of communication with any such suspicious domains.
- Monitor the domains regularly to see if the contents change.
- If content hosted on the domain violates copyright or legal marks, consider providing evidence and issuing a takedown request with the domain registrar and/or web hosting provider.
Appendix A: Indicators of Compromise
This is an ongoing investigation, and additional IOCs may be identified as the campaign evolves. Organizations are advised to remain vigilant and implement the recommended mitigation strategies. Below are the IOCs observed.
| Type | Indicator | Comment | Seen at |
|---|---|---|---|
| Domain | login.<phishing.page>.<tld> | Phishing domain targeting Microsoft | 08.2024 - 08.2025 |
| Domain | accounts.<phishing_domain>.<tld> | Phishing domain targeting | 08.2024 - 08.2025 |
| Domain | newnewdom<random>. <phishing_domain.tld> | Phishing domain from redirect to Okta via Microsoft | 01.2025 - 08.2025 |
| Domain | securedauthxx<random>. <phishing_domain>.tld | Phishing domain from redirect to Okta via Google | 01.2025 - 08.2025 |
| Domain | <alphanumeric>. <firstnamelastname>.workers.dev. | Cloudflare Workers infrastructure | 01.2025 - 08.2025 |
| AS Number | AS36352 - HostPapa | Infrastructure used by the Proxy | 01.2025 - 08.2025 |
| AS Number | AS149440 - Evoxt Enterprise | Infrastructure used by the Proxy | 01.2025 - 08.2025 |
| AS Number | AS210558 - 1337 Services GmbH | Infrastructure used by the Proxy | 01.2025 - 08.2025 |
| AS Number | AS401120- cheapy.host LLC | Infrastructure used by the Proxy | 01.2025 - 08.2025 |
| AS Number | AS23470 - ReliableSite.Net LLC | Infrastructure used by the Proxy | 01.2025 - 08.2025 |
Additional indicators are also available from an unredacted advisory that Okta customers can download at security.okta.com
A note on estimate language
Okta Threat Intelligence teams the following terms to express likelihood or probability as outlined in the US Office of the Director of National Intelligence Community Directive 203 - Analytic Standards.
| Likelihood | Almost no chance | Very unlikely | Unlikely | Roughly even chance | Likely | Very likely | Almost certain(ly) |
|---|---|---|---|---|---|---|---|
| Probability | Remote | Highly improbable | Improbable | Roughly even odds | Probable | Highly Probable | Nearly Certain |
| Percentage | 1-5% | 5-20% | 20-45% | 45-55% | 55-80% | 80-95% | 95-99% |





