In the past, traditional multifactor authentication (MFA) approaches were enough to provide a critical layer of defense against attacks. In today’s landscape, however, standard MFA is not enough.
As attackers and businesses engage in battle, attempts to bypass or circumvent MFA have become an ongoing threat, making it vital that organizations adopt phishing-resistant MFA to curtail credential theft and unauthorized access.
According to Okta’s latest Secure Sign-in Trends Report, the adoption rate of phishing-resistant authenticators increased 63% from 2024. This increase was accompanied by a drop-off in the use of weaker authentication factors like SMS.
“What makes phishing-resistant MFA stronger is that, unlike SMS notifications or emailed one-time passwords, phishing-resistant authenticators are bound to the legitimate URLs. Furthermore, they leverage public key cryptography and are physically tied to the user’s devices,” explains Fei Liu, Principal Emerging Technology Researcher at Okta. “It also uses methods like FIDO2 security keys and biometrics, and requires user interaction.”
Attackers don’t like this. In 2025, Okta Threat Intelligence observed phishing attacks in which threat actors impersonated the CEO of a targeted company and attempted to persuade targeted users to join a malicious Slack workspace. As part of the ruse, they urged them not to log in using Okta FastPass, Okta’s passwordless authenticator, thereby bypassing the company’s security defenses.
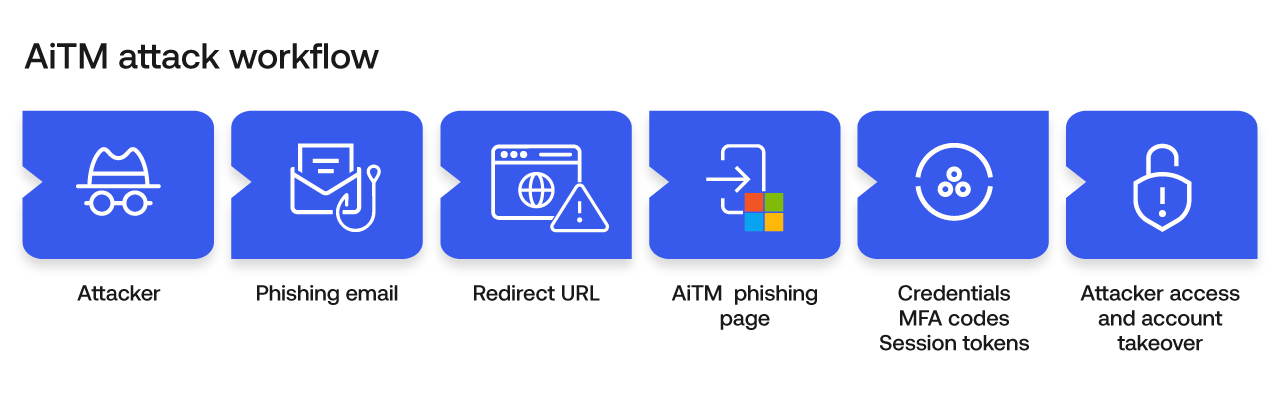
In another example of threat activity from last year, Okta observed a phishing-as-a-service platform known as VoidProxy being used by attackers to target Microsoft and Google accounts. VoidProxy employs adversary-in-the-middle (AiTM) techniques to intercept authentication flows in real-time to capture credentials and MFA codes, as well as steal any session tokens established during the sign-in process.
This capability allowed VoidProxy to bypass several common MFA methods, including SMS codes and one-time passwords (OTPs) issued by authenticator apps. The discovery of VoidProxy began after Okta FastPass stopped a targeted user from signing in via the proxy infrastructure.
“Attackers always seek low-hanging fruit,” Liu says. “The harder you make it, the more secure your networks and users will be.”
There are several ways attackers attempt to bypass MFA.
“For traditional/phishable MFA, the most common way to bypass it is to use an adversary-in-the-middle attack,” she explains. “AiTM is an attack where attackers insert a proxy between a user and a legitimate website to intercept communications and steal credentials such as passwords and OTPs, as well as session tokens.”
Other examples of MFA bypass include:
MFA enrollment attacks: If your authenticator enrollment or account recovery allows weaker credentials or MFA than the ones used at authentication, the attackers can leverage it as an entry point for account takeover.
Phishing-resistant MFA downgrade attacks: Phishing-resistant MFA downgrade attacks are observed in the wild. In general, attackers force a system to abandon phishing-resistant authentication and fall back to a weaker MFA and then use AiTM to eventually bypass MFA protection.
OAuth app consent phishing: In this attack, threat actors trick users into giving third-party apps permission to access their data, which allows them to bypass MFA.
Traditional brute-force attacks still focus primarily on knowledge-based authenticators, says Liu, adding that using authenticators based on possession or biometric factors can dramatically reduce the likelihood of account takeover via brute-force attacks.
As threat actors intensify their social engineering techniques using deepfakes and other AI-powered attacks, it is incumbent on enterprises to layer security into their environments. That means implementing Zero Trust, enforcing least privilege access, and focusing on securing the entire identity lifecycle.
MFA remains a key element of that strategy, says Liu. According to the Secure Sign-in Trends report, user adoption of MFA has more than doubled in Okta commercial workforce environments since 2019.
“Organizations should upgrade to phishing-resistant authenticators, and, to ensure they are actually used as intended, enforce phishing resistance in their application access policy,” she says. “This prevents attackers from forcing a system to fall back to a weaker MFA during a downgrade attack. Block, challenge, or investigate the requests from malicious IPs that have attacked your organization or other organizations. Also, have visibility or control over user consent to third-party applications, and implement policies that require devices to be managed or compliant.”
Learn more about how Okta’s phishing-resistant MFA can protect your environment.







