Products
Our platforms secure all types of identity from AI agents to your customers, employees, and partners.
Auth0 Platform
Auth0 is your developer-friendly platform for Customer Identity. It simplifies authentication and authorization so you can build secure apps and experiences that adapt to evolving customer expectations.
Modernize authentication and authorization flows without modifying your app’s code. Use pre-built SDKs, APIs, and customizable UI components — along with security integrations like MFA, bot detection, passkeys, and more.
Address evolving Identity requirements with Auth0’s extensible-by-design architecture. Easily accommodate everything from new regulations to progressive profiling flows to the latest and greatest technology.
Deliver end-to-end protection. By leveraging signals and insights, Auth0 can apply security measures when you need them – before, during, and after login. It also reduces vulnerabilities by authenticating and authorizing AI agents.
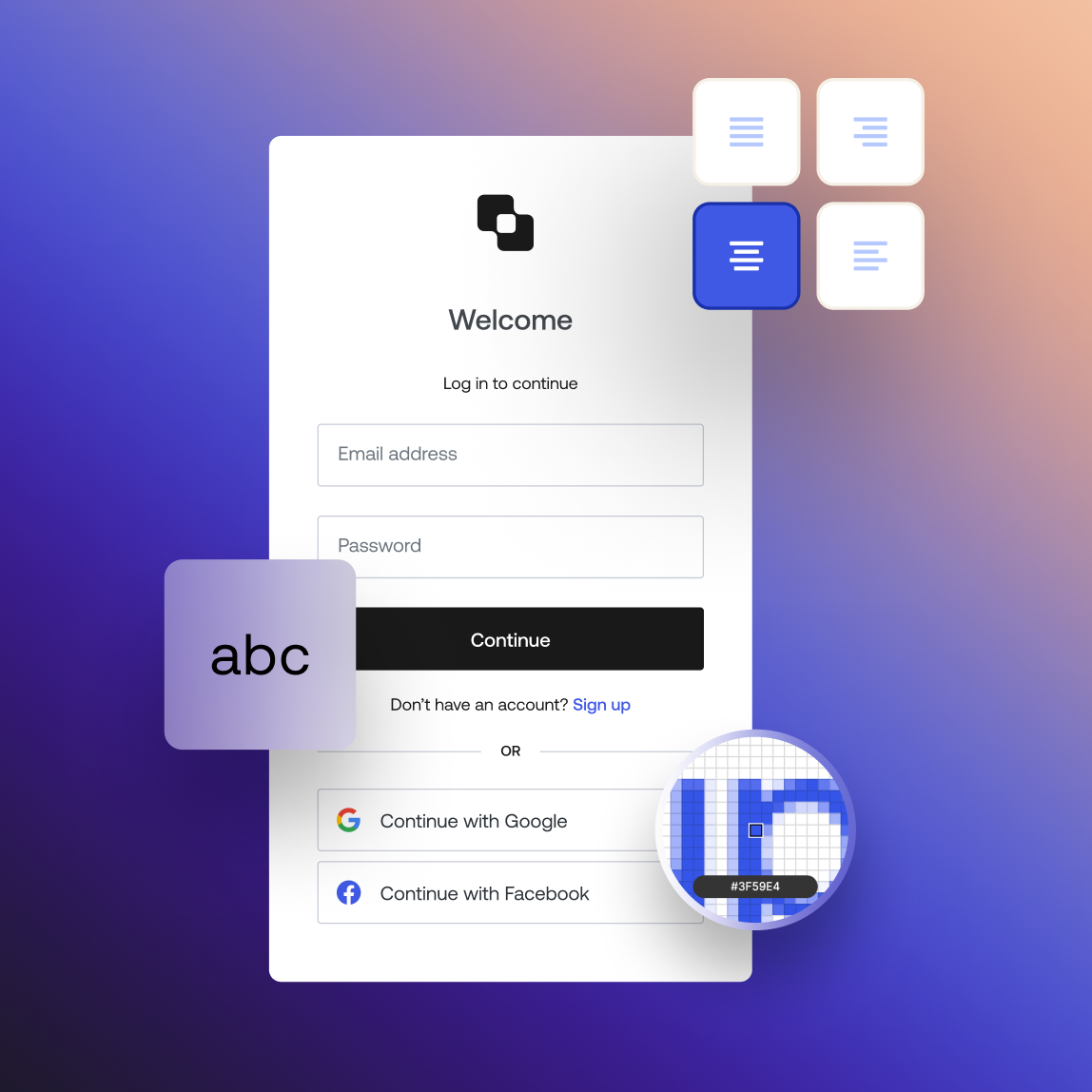
Universal Login
Enable a consistent and secure authentication experience. Customize branding, set up SSO effortlessly, and tailor flows with flexible UI components.
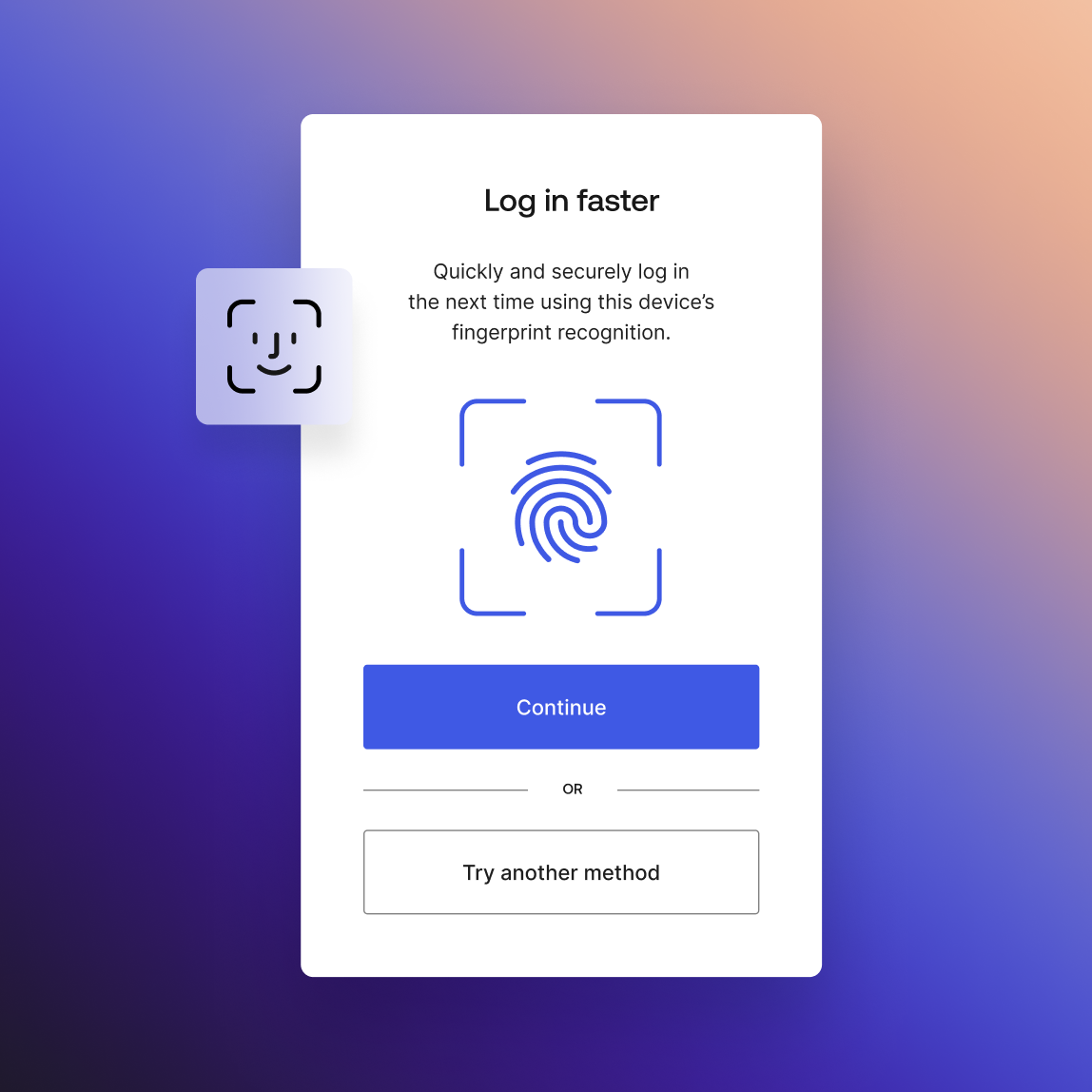
Passwordless
Give customers the choice to go passwordless — for secure experiences that are convenient and completely seamless.
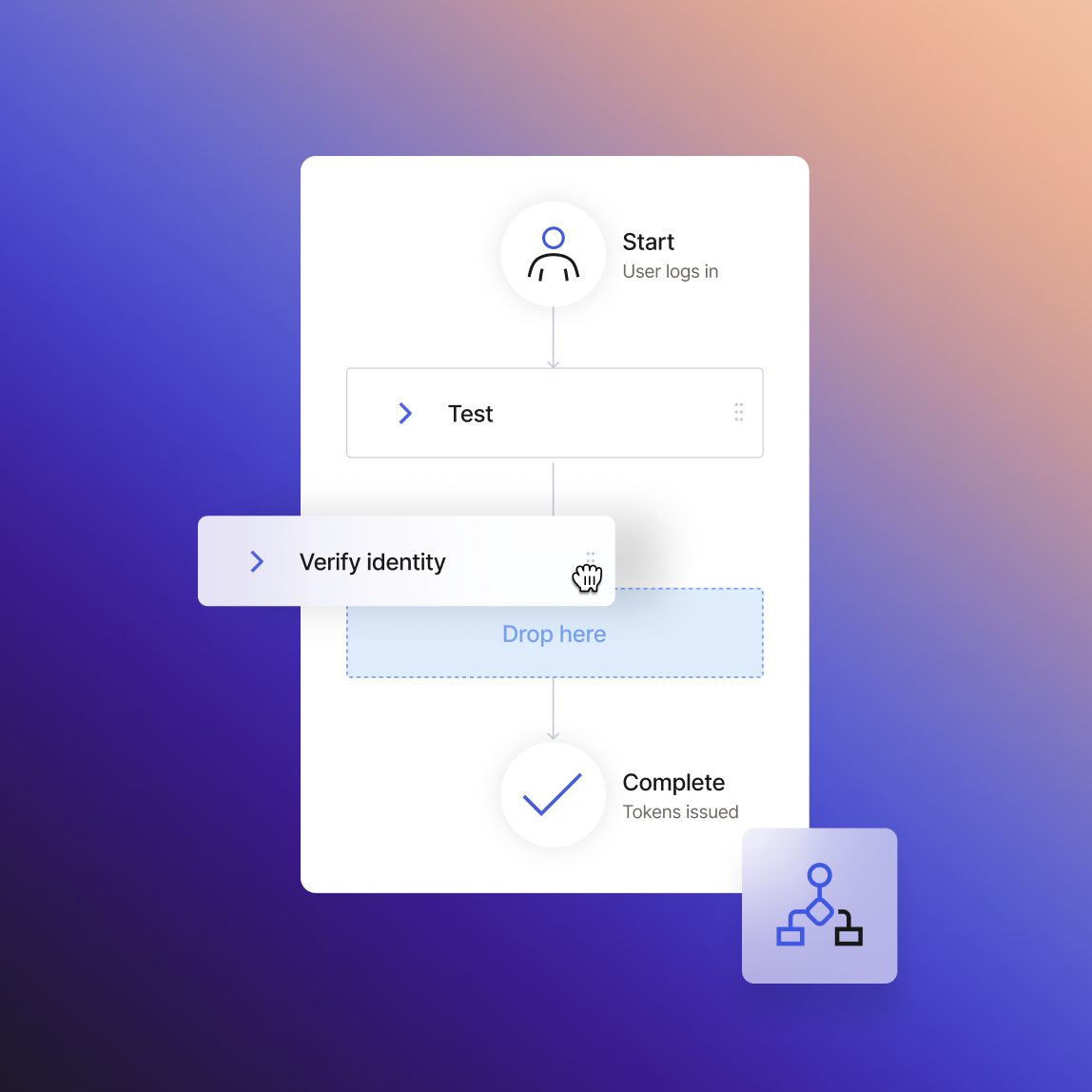
Actions & Forms
Build Identity flows that fit your needs and give you flexibility. Use a drag-and-drop interface for quick customization or dive into pro-code extensibility.
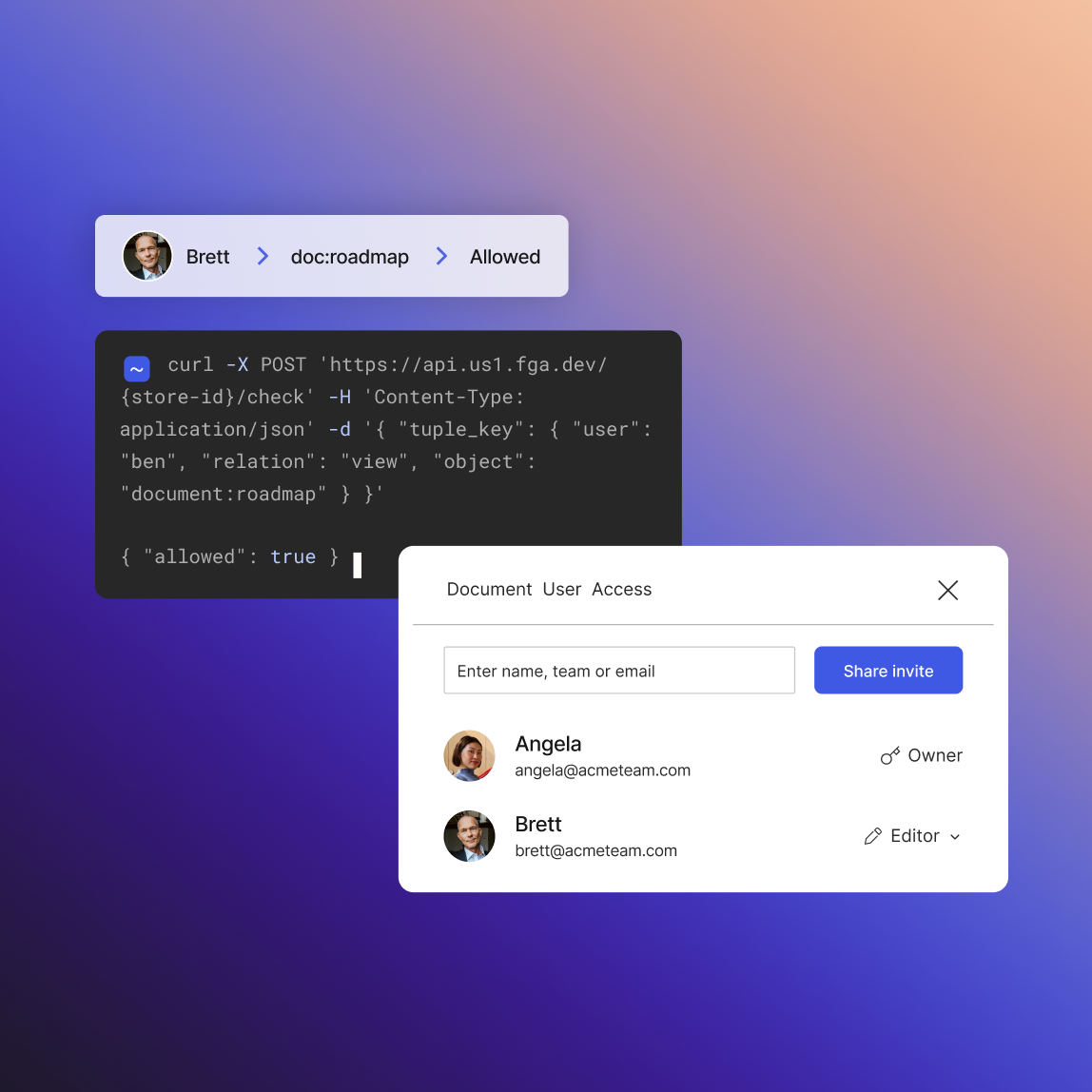
Fine Grained Authorization (FGA)
Enable user collaboration and access control with unmatched granularity and easy-to-use APIs.
Highly Regulated Identity
Secure sensitive customer operations and transactions seamlessly, with support for industry standards like GDPR, HIPAA, and PSD2.
Attack Protection
Protect against a range of attacks with features like Bot Detection, Breached Password Detection, and Suspicious IP Throttling.
Organizations
Customize authentication and authorization workflows for your B2B customers at scale.
Single Sign-On (SSO)
Give your customers, partners, and contractors secure access with one login while streamlining authentication across apps and reducing risks.
Adaptive MFA
Leverage login context to enforce dynamic authentication for risky logins.
From frictionless login experiences to dynamic access management, we have Identity handled. So you can stay focused on growing your business.





