Oktane19 Closing Keynote
Transcript
Details
Speaker 1: Welcome to our final keynote for Oktane '19. This morning, you heard Pietro Galli talk about the Norwegian Refugee Council, and Aaron announced our fundraising campaign to support this very important nonprofit. I'm very pleased to report that we have raised over $8,000 via the link that you can see here, and also $9,700 via the activation in the expo hall.
But we can still do more. As you heard, we will be matching anything raised over $10,000 via the link right here. And I was just talking to Ryan backstage, and he promised to personally commit to match any amount raised over $10,000 today. And I will also do the same. So, please take a minute to take out your phones and help us get to that $10,000 goal, and help us get over that match. I hope that you join us.
Our mission is to connect everything. Yesterday, you heard Todd unveil our new products to support that mission, and hopefully during your time at Octane, you've been able to connect with each other, as well. And next up during this keynote session, for our first part, you will be hearing more about our product strategy, where we're going to be taking the product in the future, and to do that, please join me in giving a warm welcome to our Vice President of Product Strategy, Alex Salazar.
Alex Salazar: Every organization in this room is going through two major transformations. On one side, you're going through a cloud transformation. You're taking more and more of your applications, your services, your infrastructure and moving it to the cloud.
On the other side, you're going through a digital transformation, taking your products and services and turning them into web and mobile applications. Across both transformations, your organizations are grappling with trust. Trust in the vendors, trust in your processes and your people, your code. But a lot of other people are having to increasingly trust you.
Your employees have to trust that as you're making your environments more secure, that you're not going to get in the way of them just trying to do their jobs. And your customers have to place a lot of trust in you, that you're going to secure their private information and make sure that it's not shared with other parties. And that you're going to give them good digital experiences as they interact with you.
Now, trust is what makes all these transformations work, and at the heart of that trust, we believe, is identity. Now, at Okta, we're excited about identity. It's the only thing we do. And because of that passionate, singular focus, we have the commitment, the time and the resources to build it right. To build it as one identity platform that spans multiple use cases. For workforce identity, customer identity, and beyond.
And we're building it this way because that's what you, our customers, want. You don't want to deal with multiple silos of identity across multiple vendors. You want one identity layer that you can go to for any resources across your organizations. It also gives us tremendous leverage in our R&D investments.
When we build a feature like passwordless authentication for the workforce, we automatically light it up for customer identity. And when we build self-service registration for customer identity, we automatically light it up for our customers using it for workforce. And this strategy of one platform for identity across the org, it's working, and it shows in our continued market leadership.
Now, the thing that's really exciting is that we're just getting started. Over the next 20 minutes, we're going to talk about our near-term roadmap and our long-term product strategy. And my hope is that by the end of this, you're as excited as we are about what we're building for you, and that you'll take time to talk to your account teams about how you can explore the full value of what we're building for you across all of our use cases.
Now, you heard Todd yesterday talk about the interplay across products, integrations, use cases and data. This virtuous cycle is critical to our strategy but we're going to zoom into the product piece of this. And when you look at the investments we're making in product, they really fall into four categories.
The first is we're trying to improve your security outcomes. We're trying to build a more open platform to unlock more use cases for you. We're also helping you connect identity to everything in your organization. And we're trying to leverage our network effects and our scale to deliver unique and innovative solutions for you.
Let's start with security.
The perimeter's gone. There are too many users accessing too many resources outside of your network. You can no longer trust the network and the credential assert trust of a user trying to access a critical resource. The model's changing.
And we're doing our part to help you evolve that model by taking multiple signals about the user to assess risk and determine if you want to give them access to this resource. And if you do want to give them access to the resource, do you want to step up their forms of authentication to ensure it really is them?
Now, we do this today. We already have a great set of products around contextual access management that many of you are already using. But we want to go further.
Over the next 24 months, we're going to deepen our support for the devices as a signal for identity. And what that means is we're going to take device identity, and make that a first-class citizen in a universal directory, and allow you the ability to bind those devices to the users that own them.
When a user shows up, we can recognize it; we've seen this device before, it's theirs, it's fingerprinted. And we know that we're going to have more comfort with this user, because we recognize this binding. And over time as we expand on these device identities, we can accrue more and more information. Is it managed by Airwatch? Does Crowdstrike believe it's been compromised? And we can take all that information and feed our own risk assessment of this user, and also allow you to build more and more policy around that as you need for your organization.
Now, our contextual access policy's really powerful. But today, they're really focused on assessing risk for an authentication request into a resource. But there are other high-risk transactions that can benefit from a contextual access policy.
How do we extend these capabilities to things like credential enrollment, device enrollment, account reset, and the reset of MFA factors? And over time, as we continue to break apart the Okta identity engine that Todd talked about yesterday, and I'll expand a little bit on in a few slides, how do we make it so that you can apply a contextual access policy to any arbitrary or custom transaction that you might need in your organization beyond what we do?
We're also focusing on our own security, making Okta more secure, making Okta easier to manage. That's a really hard balance. We have to make sure we're giving our customers modern, seamless user experiences, as well. And so we're investing in improving the experience for those of you who are admins, and we're going to do that by helping you have custom admin roles that are going to help with delegated administration.
And we're going to make it easier for you to manage what the onboarding and offboarding process looks like for an admin who's being added to Okta or removed from Okta. And then finally, for those of you who are in larger, complex organizations where you have multiple divisions or subsidiaries, we're going to make it easier for you to manage multiple Okta organizations as an admin.
Now, on the end user side, the people who are logging into Okta every morning, we're going to give them a redesigned dashboard, a more modern experience. We're also going to make it easier for them to do single sign-on on mobile device. And we're going to start creating reports around suspicious activity.
Beyond the next 24 months, we're think bigger. We want to make access management not just more contextual, we want to make it continuous. And that's a really big challenge, because even the best identity system today loses sight of the user once the user successfully authenticated and accessed an application. For us to really close the loop on what the user's doing once they're in the application, we have to leverage our partnerships with our application partners, and start to exchange risk signals.
And what that looks like is, as someone like Box is starting to see anomalous behavior inside their application, how do we exchange that information? How do we get that risk signal out of Box that starts feeding it into our own engine? So that maybe as we combine it with all the signals that we have, we tell Box that we're no longer comfortable, that we think that user's too high-risk.
Turn off the session. Let's create a ticket in service now, and have security investigate. Or even better, if Box decides to turn the user off because they've seen too much anomalous behavior, we're alerted, and then that user tries to go access the CRM, we prevent access.
This is what we believe the future of authentication should look like for workforce. But contextual access management is more powerful even beyond workforce identity. It has a place in customer identity, as well. If we can assess risk on a user, then if we believe that a user's probably who they say they are, and we have a really high assurance that they are the right person accessing the right resource, we can reduce friction. And in customer identity use cases, that's really important.
Think of an e-commerce flow. Every time a user experiences an authentication request, a password reset flow or registration flow, you increase the likelihood that they're going to abandon their shopping cart. If you're identity system can help reduce the risk in a transaction, we could help you increase revenue.
But these customer-facing applications also are under attack. They're seeing an increasing amount of fraud. And so, how do we take all the signals that we're seeing, and all the power we're building in contextual access management, and partner with specialized vendors in fraud? Like Experian, Shape, and Castle, so that together, we can exchange signal and give our customers, you guys, a more end-to-end solution to help protect your application.
We've been making really big investments over the last few years on building an open platform to really unlock unlimited use cases. And yesterday, Todd talked about the Okta Identity Engine. The ability to make Okta more compose-able, and combined with hooks, make it more extensible. This is powerful! It's going to unlock a tremendous number of use cases for you.
But this is really just the beginning. Over the next 24 months, we want to take this major investment we've made in workflow, we want to combine it with the Okta Identity Engine and our Hooks investment so that in a world where Okta generates an event and kicks off a web hook, instead of you having to write the code to process that hook, you can instead go into our visual workflow designer and build any workflow you want.
Pull data from this resource. Run this calculation, and then call out to another service to give it an update. And where this combination of extensibility and compose-ability is going to be most impactful in the next 24 months, it's our lifecycle management products. We're going to supercharge it.
Today, this is a great product. Many of you already use it. Today, we can already see when a user's been added to the HR system, we can create that user an identity in Okta, and we then can provision that Okta identity across a variety of downstream SAS applications like Sales Force and Box, et cetera. But with a combination of workflow, we can take it beyond basic provisioning and turn it into true onboarding so that in addition to creating that user in Sales Force, we can also assign their territory based on who their manager is. We can send a notification to the Sales Force admin to request confirmation of the permissions we're about to give this user.
And when the user's been successfully created and provisioned in the application and fully onboarded, we can create a Slack notification to the manager, letting them know that the account's ready to go. But where it gets really exciting is that we can take all of this workflow and make it unique for every single application you want to onboard a user for, and chain it all as needed.
This is going to be really powerful. But beyond the next 24 months, we're going to continue breaking apart the different parts of Okta, making Okta more compose-able, more extensible. And if we do that, the real power of this starts to show up in customer identity.
Today, with identity engine, with hooks and with the variety of API's we already have, it's great! A developer can build anything they need to build with Okta. But it still requires a developer, and there aren't enough of those. If we can apply all this workflow capability to everything Okta has to offer, it means that your developers can do less work. A non-technical admin should be able to go into Okta and create whatever workflow they want off of any event in Okta. That means your developers can go build something else. They can go focus on building the core business logic that makes your application run, or they can move onto another high-priority project.
What it also means is that maintenance goes down. When you want to go change any part of this workflow, a non-technical admin can go in and visually change what's needed as opposed to having to pull another developer off another project to crack open source code and redeploy it.
And with all these unlimited use cases that we can unlock with more customization, more compose-ability, more extensibility, we expect the number of integrations that Okta supports to go from 6,000 to 60,000.
But with that new scale of integration, we're going to need to deliver a new catalog experience to make it easier for you to find the integrations you need and make sense of all the different variety and how to turn them on, and how to plug them together, and how to integrate them.
Now, this is my favorite topic. Integrating identity to everything. And I'm excited about this, 'cause we're seeing our customers doing it already. Many of you are taking Okta and you're finding ways of integrating it to all the resources across your organization.
But today, our products are really only focused on a small set of these. We're mainly been focused historically on SAS applications, custom-built applications, API's, and as of yesterday, we're now expanding support to servers and to on-premise applications.
Over the next 24 months, we're going to take the products that we've announced and we're going to make them better. For the Okta access gateway, it's a great product. It's extending the value of Okta to your traditional legacy on-prem applications.
But we want to make it easier. We want to make it easier to manage, easier to deploy, easier to secure. And to do that, we're going to give customers the option of taking that proxy and moving it to the cloud. Instead of having to deploy and manage and secure this on-premise proxy, you can just reroute DNS to the applications you want.
It won't be for every application, but our hope is that if we make it easier for you, you're going to apply this solution to more than just your most critical applications, more than just [inaudible] business suite. You might apply it to your hosted Jira, your GitHub, or a variety of internal portals, getting more value out of Okta, bringing the identity experience you're already investing in and expanding it to more applications.
I'm really excited about server access. This is really Okta going down stack, and there's a huge opportunity for all of us if we get this right. And today, we're doing it with servers, and the product is awesome. I hope all of you get to play with it soon. But over the next 24 months, we're going to make this product even better. We're going to improve the login capabilities for it. We're going to give it ever finer-grain access. And we're going to build better automation, which means we're going to have deeper integrations to the automation tools you're already using like Puppet and Chef, and a variety of CLI tools that your dev-ops teams and your IT admin teams are using.
And if you look at what made it successful in the SAS world, it was best of breed. We built deep integrations that were vendor-neutral across all the applications that you care about most. We're taking that same perspective to infrastructure, and what that means is that each of you are waking up with the realization that you are multi-cloud whether you wanted to be or not.
You could have one identity system that could control identity across all of them without your teams having to learn and manage three different systems whether it's AWS, Azure, or GCP. We think beyond the next 24 months, we want to extend what we're doing in infrastructure beyond just the server. Databases. Containers. Other services. Your whole devops tool chain.
Our goal here is to kill the shared credential in infrastructure the way we did for SAS. And what this means for all of us is a world where if Joe the IT guy leaves your organization for any reason, within moments of them being removed from the HR system, their session's terminated across all the infrastructure, and they've been de-provisioned across all the applications, all the services, all the servers and all the databases.
This is powerful. Most organizations cannot do this today.
You know, this is Todd's favorite topic: network effects.
We're at a unique opportunity in Okta's history. We're reaching a scale where our customers are coming to us because we have so many customers. Sorry, our partners are coming to us because we have so many customers. And the more partners we attract because of our customer base, the more customers we attract because we can deliver more and more solutions with our partners.
And as both of those scale up, we're generating more and more data that we can use to deliver more and more products to you. Over the next 24 months, we're going to leverage this new scale, this network effect, to deliver sign-in with Okta.
And what this means is that when a user and customer, Okta Customer A, attempts to go log in to Okta Customer B's web product or mobile product or partner portal or supplier portal, instead of Customer A having to manually create accounts for all of their employees in Customer B, or instead of Customer B having to go build out and configure and coordinate a whole federation system to hook into Customer A's identity system, they can just click a button and connect both Okta-works.
And the reason this matters is that increasingly, all of your business relationships are becoming digital, and in digital relationships, reducing friction is what makes them more powerful. We're doing our part to help reduce the friction around identifying who the people are you're doing business with. We're really excited.
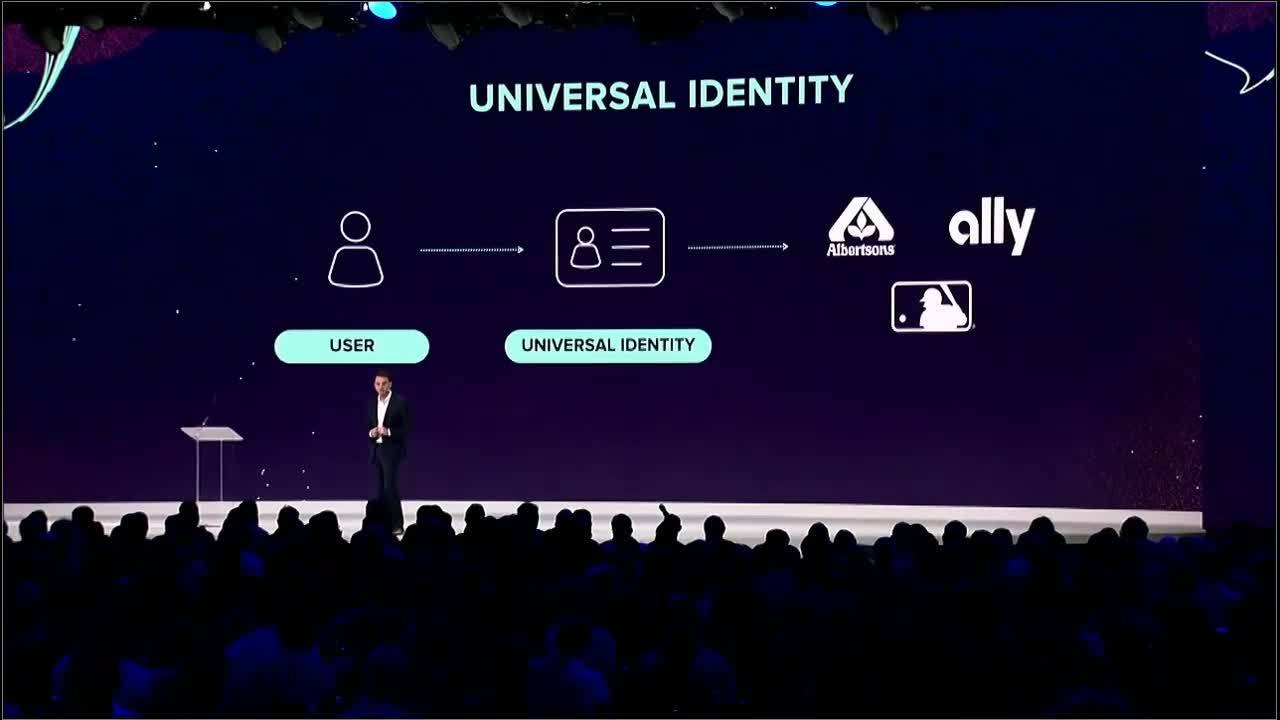
Now, beyond the 24 months, we're thinking very big. We believe that with our customers and our partners, we can deliver universal identity. That we can collect all the data we have, and create truly global, universal identities for every person in the world. And the key to this, though, is to give the end user full control over that identity, so that they're in the driver's seat of their own privacy.
And the value to the end user, it's powerful. They control their privacy. But the value to our customers and our partners is also powerful, because when the user shows up for the first time to Albertson's to go buy their groceries, we can recognize them and say, "Hey, we know you. Do you want to sign in with your universal identity? Do you want to share this information with Albertson's?"
And if they click Yes, we just took a tremendous amount of friction out of that e-commerce transaction. And we've increased their probability that that user is in fact going to transact and buy their groceries in that session with Albertson's.
And if we as an industry can make this work, we can solve a tremendous amount of the problems with internet identity. And this is hard, it's complicated, and it's risky. But we're excited about trying it with our partners and our customers.
Now, we've talked about our roadmap and the investments we're making across four key areas. How we're improving security, how we're building a more open platform, how we're connecting identity to more things, and how we're leveraging our network effects for innovation.
But this whole roadmap doesn't happen in a vacuum. It happens through conversations with you. We're building these products for you, and our vision is informed by what you're telling us, what you're asking us for. And as a proof point to that, we have over 5,000 Okta admins who've registered and have logged in and voted on the Okta help center, about the features they care about most.
And of the top 30 most requested features, we've already delivered 15 and another 13 are currently on a roadmap to be delivered in the next 12 months. If you haven't already, register for the Okta help center. Log in. Look at the features that people are voting on. Create your own, and vote on the ones that matter most to you so that we know, so that we have a sense of where you want us to go.
We're really excited about where we're going and what we're building for you. And my hope is that each of you are also really excited about what we're going to deliver for you over the next few years. And if you are excited, my ask is that you contact your account teams and explore the full value of Okta. Go see all the things we have to offer.
If you're using us for customer identity, thank you! But we can do more than just secure the application. With server access, we could secure the whole stack of that project. Go explore workforce identity. Go extend the value of Okta to your own day-to-day experience in your environment. And if you're using us for workforce, and you're using us for single sign-on and lifecycle management MFA, explore customer identity. Go play with it. Go open up the API. See how easy it is to do this, so you don't have to rebuild this stuff for your next project.
And go explore our infrastructure, our server access products so that you can extend the same value you're already getting at the app tier to your infrastructure.
We're looking forward to being a better partner with you, and we're looking forward to doing more business with you.
Thank you.
Throughout Oktane19, you’ve heard about the exciting new products, services and functionality we’re introducing over the next few months. But what about next year? The next few years? Beyond? Vice President of Product Strategy Alex Salazar will walk Oktane19 attendees through Okta’s long term product vision, providing a glimpse into how Okta is thinking about the future and what the company is building towards for its customers. Alex will go in-depth into strategies around the Okta Identity Cloud, touching on use cases for workforce identity, customer identity, and the Okta Integration Network. Following the Product Roadmap, attendees be kept on the edge of their seats by Frank Abagnale, walking away from his talk with an inspiring and unforgettable life lesson. Mr. Abagnale’s transformation from one of the world’s more notorious con artists to international cybersecurity expert and trusted advisor for over four decades to the FBI will make for a defining experience and a memorable event for Oktane19 attendees.
