FACT OR FICTION: SSO Creates a Single Point of Failure, so It’s Less Secure

At Okta, we are highly invested in the latest ideas and practices around authentication and security—and that requires some myth busting. This blog is the second in a series of posts meant to tackle common misunderstandings and myths around single sign-on (SSO). See below for our full list of the myths we've seen (and busted!) around SSO.
Single sign-on solutions are sometimes criticized for introducing a single point of failure into the authentication process. In reality, a single point of failure already exists: the user.
Login credentials exist to keep accounts secure, but they pose a problem in modern companies where users access many applications every day. When forced to constantly juggle different credentials, it’s only natural that people being to suffer from password fatigue. Single sign-on (SSO) simplifies the login experience by giving users access to multiple applications with a single login. However, this also raises an important question: with all your eggs in one basket, isn’t life much easier for a hacker who now needs to steal just a single set of credentials to access all accounts?
The real single point of failure is the user
In theory, having multiple, complex passwords that change often is more secure than having a single password that unlocks everything. But the reality is very different; few people actually make use of different complex passwords. It simply isn’t feasible to remember passwords for each of the average American user’s 150 password-protected accounts. To cope, some store passwords in unencrypted files or leave them on sticky notes in public view. Even worse, many users reuse the same password across systems with one study citing that 73% of all passwords are duplicates.

By reusing passwords across multiple systems and apps, users introduce a single point of failure that gives hackers easy access to data.
Password fatigue leads to poor password hygiene—and as users start to rely on insecure password management practices, they become a single point of failure. Verizon has found that hacks due to stolen credentials are the most common source of data breaches, and it’s fair to say this is largely because users struggle to manage their many credentials. Ultimately, passwords are useless if they can’t safeguard user accounts from unwarranted access, so when it comes to credentials, less really can mean more.
SSO is more than simplified password management
SSO is a great way to enforce strong password practices for your users. With just one password to control, IT can set policies to make sure that one password is as secure as possible:
- Expires after a certain amount of time
- Differs from previous ones to prevent reuse
- Does not match an existing list of hacked credentials
- Lock after a certain number of unsuccessful attempts to protect against brute-force attacks
Password managers can also provide these functionalities, but as I stated in the first post of this series, password managers focus on protecting credentials, when the focus should be instead on access. SSO solutions, on the other hand, does focus on access and can give companies a stronger, more sophisticated approach to security by looking at the user’s context. Modern SSO can analyze:
- Application context: Which application is the user accessing? Does it contain sensitive data? More to the point, should they have access to it?
- User context: What group is the user a member of? Are they a temporary contractor or an employee? Did they recently switch roles within the organization?
- Location context: Do we trust the user’s current location? Have they logged in from that location before?
- Device context: Is the user logging in from a mobile device or a desktop? Is the device managed? Have they used this device before?
- Network context: What is the user’s IP? Have we seen it before, and is it known to be suspicious? Is the user using an anonymizing service such as TOR?
Even if a user enters the correct credentials, users may be asked for additional verification due to the context of their access. For example, an employee who comes in from outside the corporate network using an unknown device trying to gain access to an HR tool might be prompted for a second factor through a multi-factor authentication (MFA) tool. On the other hand, a contractor using a Tor anonymizer trying to gain access to sensitive financial data might simply be refused access altogether. SSO gives administrators more control and granularity over how users are given access to company resources.
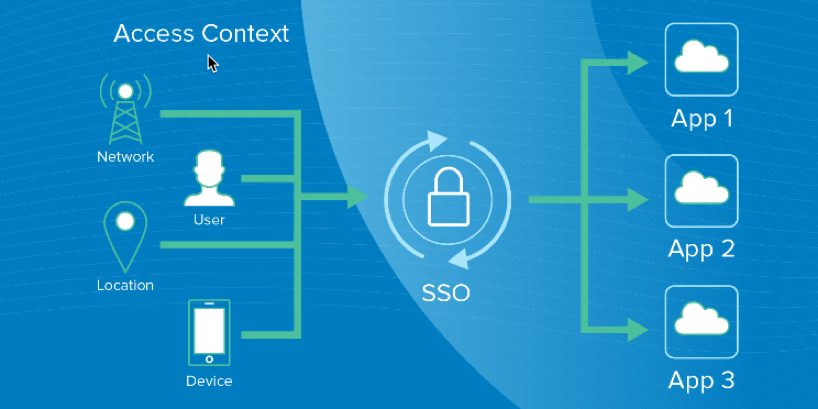
A successful SSO login process where all the contextual factors have been taken into consideration before allowing access.
SSO removes the single point of failure
It would be great if everyone used unique, complex, and continuously changing passwords for each of their apps. The reality is that this unfairly burdens users, who will generally choose convenience over security. Adding SSO to protect passwords behind a strong master password improves the user experience and increases security. However, the real benefit of SSO comes from the ability to enforce strong access policies driven by user context. That master password is now just one of many, hard to compromise inputs that goes into allowing access. With the right SSO solution, organizations can not only ensure better system security, but also reduce the login friction that frustrates so many users.

Want to learn more about SSO? Listen to the Things You Don’t Know About Single Sign-On webinar, visit our SSO page, and check out our entire myth busting series:
Fact or Fiction: SSO is the Same as a Password Manager
Fact or Fiction: SSO Slows Down IT
Fact or Fiction: SSO is Difficult to Deploy

