FACT OR FICTION: SSO Is the Same as a Password Manager

At Okta, we are highly invested in the latest ideas and practices around authentication and security—and that requires some myth busting. This blog is the first in a series of posts meant to tackle common misunderstandings and myths around Single Sign-On (SSO). See below for our full list of the myths we've seen (and busted!) around SSO.
Single sign-on solutions are often confused with password managers because both use a single login to access information for multiple applications.
If you work at a computer, your day likely involves switching between various applications. It goes without saying that it’s a strain to remember multiple passwords and enter them individually each time. This is why password managers have become so popular.
Password managers are like vaults for passwords—they store your credentials in one consolidated place. Instead of having to juggle different usernames and passwords, users only need to remember the single master password that unlocks the password manager. From there, a password manager automatically enters stored credentials into authorized websites and apps. In theory, this encourages the use of more complex passwords. Since users only need to remember a single login, they’re less likely to repeat passwords across multiple apps, so if one password gets compromised, not all systems are compromised.
But here’s the problem...
With password managers, the focus is on protecting the password. Even if password managers encourage people to use passwords that are harder to guess, passwords themselves are still inherently vulnerable to phishing and brute-force attacks. In fact, passwords are still a main source of security breaches for enterprises—81% of security breaches are from credential theft. Some of the most high profile hacks in recent memory stemmed from phished credentials.
Password managers also pose a problem for IT admins. Each password is a potential entry point for a hacker, and consolidating every password in one place does nothing to reduce your organization’s attack surface. When users leave, they leave their passwords behind—and password managers can’t easily remove the access rights these disparate credentials have.
While password managers make it easier for users to manage their credentials, they still focus on the password. They cannot manage who has access to those credentials or to your system. SSO solves both pain points, creating a convenient experience through strong authentication.
SSO is about trust, not passwords
Modern SSO solutions don’t just help users manage passwords (although SSO does that as well)—they provide a new approach to identity and access management (IAM). They shift the focus from managing passwords to managing access through trust. Instead of relying on a vault full of passwords to keep data secure, SSO leverages existing trust relationships to create a single domain where authentication takes place.
How it works
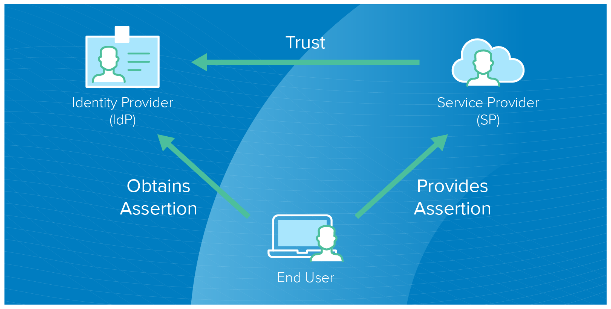
Single sign-on relies on federated identity—the sharing of identity attributes across systems that are trusted, but otherwise autonomous. So, when you’re trusted by one system, you’re allowed access to all other systems that have a trusted relationship with that particular one. This removes the need for shuffling passwords between systems. Modern SSO solutions are built on this, enabled through federation protocols like SAML 2.0 and OpenID Connect. For users, this means they only need one set of credentials to sign in to the SSO solution and gain access to any trusted, interlinked app and system.
These interlinked systems are also not restricted to just cloud apps. Unlike password managers, you can integrate SSO with VPNs, WiFi, firewalls, native mobile apps, on-premises resources, and even other identity providers—basically any tool that supports federation.
SSO and login context
In addition to the potential of removing passwords, SSO gives IT teams a clear view of the context of a login request. Information such as who the user is, where they are logging in from, what their IP is, what device or browser they’re using, and when and where they last logged in.
By understanding the context of the login, IT can create incredibly secure policies to drive proper access decisions. For example, SSO is often combined with multi-factor authentication (MFA) to flag suspicious login attempts—like an unknown device or location—and prompt for another authentication factor. So even if someone enters a stolen password, he or she won’t simply be given access to the data without that second factor.
Administrators can also control user sessions by setting certain policies. This may mean users must re-authenticate every few hours, that only certain teams get access to certain systems, or that users can’t access certain apps from outside the office IP range. For example, you may require all employees on the road to authenticate using MFA on every login attempt, while those in the office need only re-authenticate every 24 hours. It also means admins can cut access if a user changes positions within the company or is terminated.
SSO is not the same as a password manager
Passwords are susceptible to all manner of threats, and it takes more than consolidating them in one place to protect your users. SSO provides the ideal hybrid: the ease of a single login with enterprise-grade security.

Want to learn more about SSO? Listen to the Things You Don’t Know About Single Sign-On webinar, visit our SSO page, and check out our entire myth busting series:
Fact or Fiction: SSO Creates a Single Point of Failure So Less Secure
Fact or Fiction: SSO slows down IT
Fact or Fiction: SSO is Difficult to Deploy

