Navigating your Identity and Access Management Journey
The benefits of implementing identity and access management (IAM) speak for themselves. Having a centralized IAM solution means fewer passwords, a better end user experience, and a centralized solution for managing access to both cloud and on-prem apps and services.
Despite this, investing in identity and access management is not top of mind for many organizations. Worldwide security spending on identity and access management technology is only about 9%.
Perhaps your organization is small enough where managing individual apps and users is not yet getting out of hand. Or maybe you are already using Active Directory, but have yet to adopt many cloud apps. Maybe your executive team just isn’t taking security as seriously as they should.
But securing your organization means more than just implementing multi-factor authentication. Your organization requires a combination of Single Sign-On, Lifecycle Management, Universal Directory, and API Access Management all to stay secure.
All of that said, we know that this can’t all be done overnight. It must be done in phases as you continue to modernize, so let’s take a look at the different methods available to secure your organization based on your current identity and access management adoption, and where you are headed.
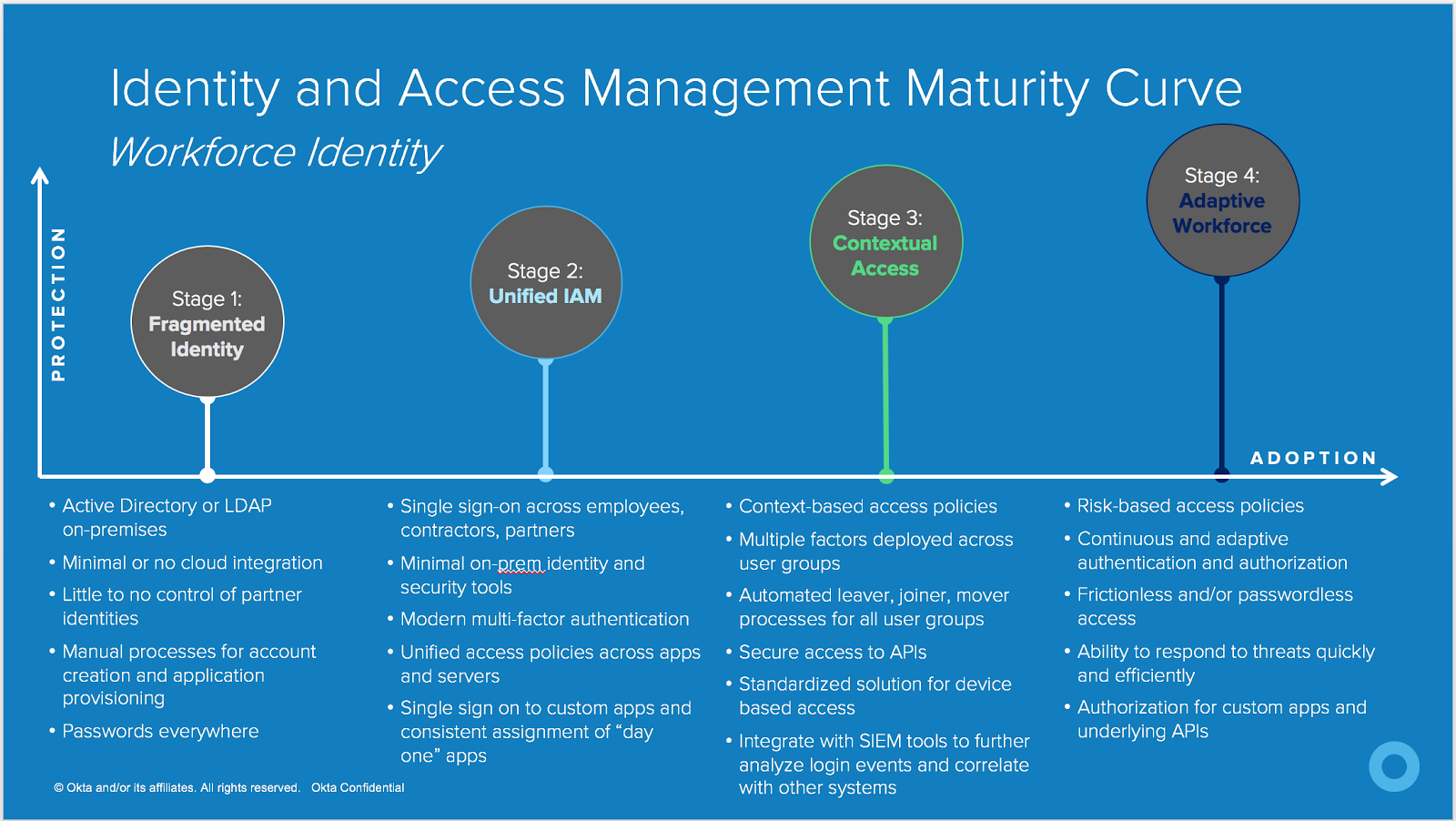
Here, we have our Identity and Access Management maturity curve, a collection of stages based on what we have seen with organizations modernizing their identity and access management technologies. Of course, there is some overlap between these stages, so you can pick and choose what makes the most sense for your organization.
Let’s break down each of these stages.
Stage 1: Fragmented Identity
Many large organizations or organizations that have been around for a number of years are still in this stage. Active Directory is very entrenched in the enterprise with multiple forests and domains. A few business units may even have another type of on-prem LDAP directory. Some apps may support authentication via Active Directory credentials, while others may not.
Additionally, the organization has implemented minimal or very few cloud applications, and the credentials used in those cloud apps could be different than Active Directory credentials. All of this, of course, means that passwords are everywhere.
When we look at how users are assigned to applications, this could be a manual process, or, in some cases, everyone has access to every app in the enterprise. This means that IT does not have a methodical way of tracking who has access to which app, or the permissions they may have within that app.
Stage 2: Unified IAM
In this stage, organizations have a single sign-on solution in place—ideally, a cloud-based single sign-on solution. The organization has taken steps to move away from on-prem identity and security tools (directories, DLP solutions, firewalls etc) and has implemented some cloud-based technologies.
In addition, that identity solution is facilitating access to cloud apps and custom built/homegrown apps, as well as on-prem resources like servers.
At this stage, the organization has identified a method by which access policies are the same across cloud apps and on-prem resources. And lastly, the organization has implemented some form of multi-factor authentication for administrators and end users, regardless of the app or resource they are trying to access.
Stage 3: Contextual Access
Fewer organizations are at this stage. When an organization has heavily invested in contextual access management, they have thought about intelligent and dynamic access policies across cloud apps, on-prem resources, devices, user lifecycle states, and API’s. Ideally, they are using one cloud service to facilitate all of this. If your company is in this category, it means you’ve implemented the following tools:
Multi-factor authentication: Organizations in this category enforce multi-factor authentication, but only when and where it makes sense. Ideally, the organization has implemented strong forms of authentication such as a U2F token or a mobile authenticator app, and has made both of these options available to users.
Lifecycle management: The organization has automated the onboarding and offboarding process, as well as “mover” processes (employees moving roles within a company). Ideally, the organization is automating both app assignment and app entitlement, and this is being done at the group level such that administrators do not need to manually assign individual users to applications.
API’s: Internal developers produce API’s to allow external applications access to limited data. As custom apps become increasingly modern with an API backend, it’s important to secure the methods by which your apps communicate with other 3rd party apps. However, unless fully controlled, the handshake between the external apps and the API can become a critical vulnerability. Therefore, organizations in this stage have implemented a technology which secures access to their APIs via contextual access policies.
Devices: With the influx of device types in the enterprise, administrators need a method by which they can ensure that devices are managed by an Enterprise Mobility Management (EMM) solution (System Center Configuration Manager, BigFix, Jamf etc) or a Mobile Device Management (MDM) solution (Workspace ONE UEM, MobileIron, Msft Intune, etc). Organizations that have implemented a contextual access policy for devices are ensuring that only managed devices have access to corporate applications.
Security detection and remediation: Larger organizations require a method by which they can correlate data and have an all-up view of the login activity in the enterprise. In this case, organizations have integrated their identity solution with a SIEM tool such as Splunk or SumoLogic as a means of advanced detection. Furthermore, the organization may have implemented a Cloud Access Security Broker (CASB) such as Netskope to remediate suspicious activity.
Stage 4: Adaptive Workforce
This stage is the “north star” for many organizations. Implementing an adaptive identity and access management technology means that administrators no longer need to create prescriptive access policies for allowing/denying access, or prompting for MFA.
The identity and access management solution can automate this process by means of risk scoring and automated response when suspicious activity is detected. Organizations in this category have implemented a passwordless access policy, where either a strong auth method (U2f, biometrics etc) or a certificate is used to grant access, with no additional interference required by the end user.
How to get started on your IAM journey
Reading through this, you may be wondering—where do I start? This is just a glimpse into the different methods by which you can secure your enterprise. Gauge where you are by taking our Okta IAM Maturity Curve Survey! And for a more detailed overview of the technologies associated with each of these stages, check out Best Practices for Strengthening Enterprise Security with Okta from the Okta Help Center.

