Empower Employees to Become First Responders with UserInsight
As cybercriminals become more refined in their quest to access workforce credentials, today’s businesses are under ever-increasing pressure to implement systems, tools, and processes that protect their sensitive data. These features need to be able to secure their employees without overburdening IT with excessive monitoring tasks.
This is a tricky balance to get right, but implementing our newly released UserInsight tool—which turns employees into first responders in the face of potential account takeovers—is a step in the right direction.
The current landscape: More users, more locations, more devices
Today’s organizations are made up of remote employees, contractors, and partners — all of whom require access from various locations and devices. While this sprawling workforce can open up new opportunities for productivity, it can also potentially leave organizations vulnerable to cyber threats.
To address this risk, many organizations invest in tools like multi-factor authentication, which add additional layers of security to user accounts.
However, any security expert worth their salt will tell you that there’s no such thing as a fully impenetrable security solution. IT admins must still remain vigilant for anomalous user behaviors, such as a user enrolling a new authentication factor. In these cases, it can be difficult to distinguish whether the uncommon behavior is the work of a legitimate user or a bad actor.
The challenge: Recognizing the malicious from the benign
Signing in from a new device, enrolling new authentication factors, and resetting MFA factors are all necessary—albeit uncommon—activities that users need to easily execute in order to be productive.
It’s IT’s responsibility to monitor this activity, determine whether it’s malicious, and respond accordingly. In some cases, however, IT doesn’t necessarily have the resources to handle these tasks. For large enterprises with millions of logins, tracking every potential issue is a near-impossible task that can lead to users being locked out erroneously. As such, it’s not realistic for IT to manually track all of these activities—but to ignore them completely would leave their organizations vulnerable.
Shared responsibility: Turning targets into first responders
To address these challenges, we recently announced Userinsight as part of our SecurityInsights family of security tools.
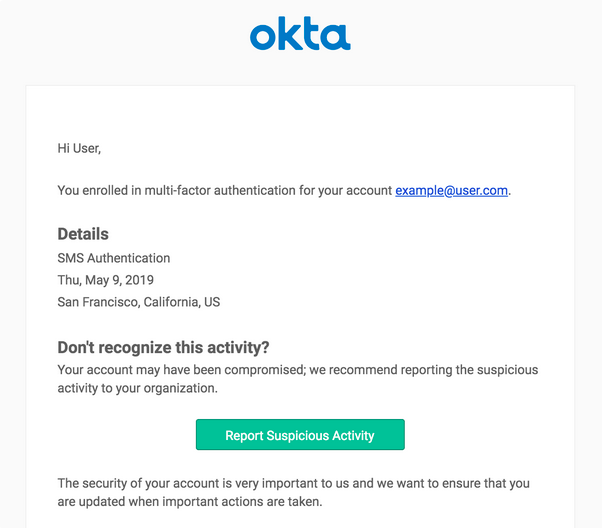
Once enabled, Userinsight alerts users via email when suspicious activities like an MFA factor enrollment or password change is detected on their account. From there, the user has the opportunity to report the activity to their IT admins if they don’t recognize it.
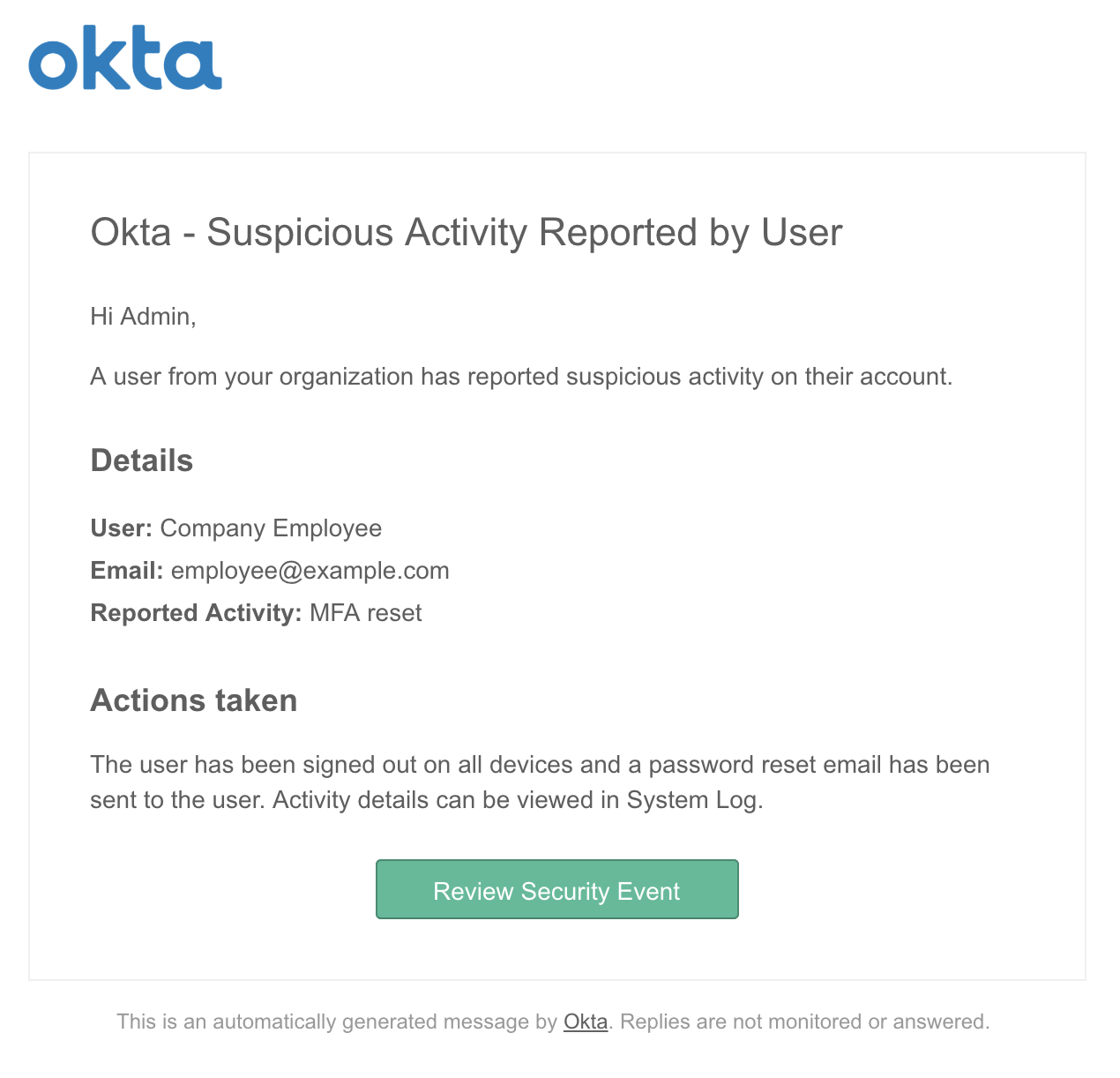
Once reported, the admin team is notified of the activity, and can begin their investigation and response.
By using Okta Hooks or Okta Workflows, admins can also automate certain actions like quarantining a user, thereby preventing access to apps with sensitive data until the user identity can be confirmed through a strong factor like biometrics or a mobile authenticator app.
Admins can even automatically notify SecOps teams of potential account compromises through integrations with digital operations platforms like PagerDuty.

Getting started with UserInsight
Businesses across industries are working hard to protect their workforce and sensitive data from increasingly refined attacks from cybercriminals, without compromising their productivity.
UserInsight supports this mission by empowering users to be first responders on their accounts without compromising their productivity. It minimizes the burden on IT and provides an additional layer of protection against evolving cyberthreats.
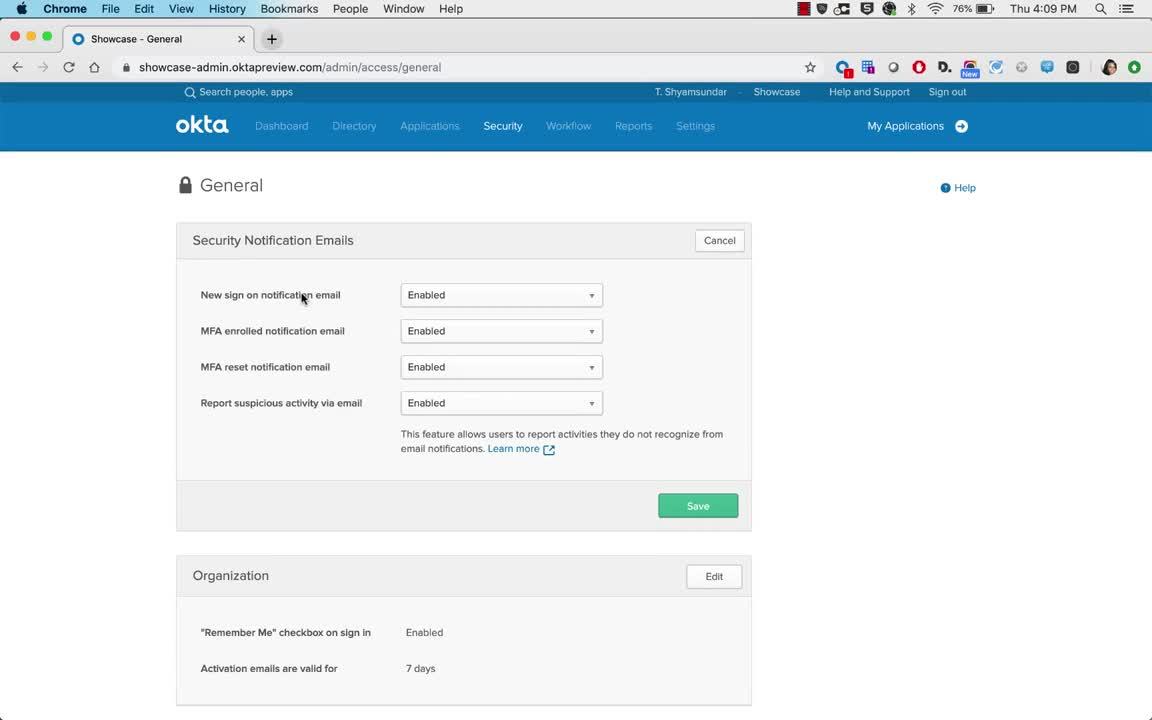
For Okta customers that are interested in implementing the tool, UserInsight is now available as an Early Access feature. Read this post for detailed steps on how to enable UserInsight within Okta.
For more information on the feature and the SecurityInsights family, feel free to contact us or check out the following resources:
- SecurityInsights: Protection at the Admin, User, and Network levels - Blog
- ThreatInsight - Okta help page
- HealthInsight - Okta help page

